STEGANOGRAPHY The Art of Message Hiding Cryptography Securing






















- Slides: 25

STEGANOGRAPHY The Art of Message Hiding

Cryptography: Securing Information in the Digital Age Part 1: Introduction to Steganography Part 2: Hands-on activity: Exchange of Steganographic Messages Part 3: Research and Practice on Steganalysis


STEGANOGRAPHY Steganography is an ancient technique (known from the Antiquity) for hiding information. The hidden information can be additionally encrypted (in the digital age). A Digital Message (the secret) can be hidden within - digital images - audio files - video files - … or even other text messages by storing the secret information within inessential lines of code (bytes) that don't alter the look or sound of the original file.

Modern Use of Steganography http: //usatoday 30. usatoday. com/life/cyber/tech/2001 -02 -05 binladen. htm Terror groups hide behind Web encryption by Jack Kelley, USA TODAY 02/05/2001 … (Islamist groups) are hiding maps and photographs of terrorist targets and posting instructions for terrorist activities on sports chat rooms, pornographic bulletin boards and other Web sites, U. S. and foreign officials say.

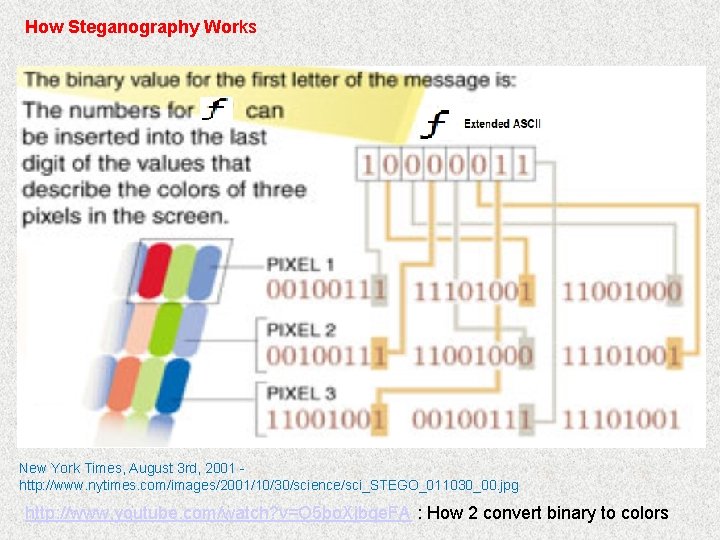
How Steganography Works New York Times, August 3 rd, 2001 - http: //www. nytimes. com/images/2001/10/30/science/sci_STEGO_011030_00. jpg http: //www. youtube. com/watch? v=O 5 bo. Xjbqe. FA : How 2 convert binary to colors

Steganography versus Cryptography 1/2 Although Steganography and Cryptography seem to be practically closely related they are technically different Steganography hides the existence of a secrete message, whereas Cryptography only scrambles the original message (plain text) so it cannot be understood

Steganography versus Cryptography 2/2 Steganography cannot replace cryptography, because the containers must have a much larger size than the embedded “secret” message Steganography necessitates the transmission of the encoding key, and possibly more information to decode the message. The transmission of this vital information must be accomplished using a different communication channel Note: Asymmetric Encryption (e. g. PGP), does not require the transmission of a secret key.

Terminology of Steganography Cover data (a. k. a: Carrier, Container) – The original, innocent message, be it audio, video, text or an image Embedded data (a. k. a: Secret) – The data that is to be hidden with the ccarrier Stego data – A message that includes both the cover and embedded data


Historical Forms of Steganography - Tattoos ( Herodotus) - Invisible Inks (lemon juice, milk, urine, …) - Microdots in paper - Text – Can one man pace up to empty rooms? – Can One Man Pace Up To Empty Rooms?

http: //blog 2 life. com/steganography-the-secret-tool/

http: //ladyastridslaboratory. com/tag/invisible-ink/

http: //www. pinewswire. net/article/new-steganography-technique-relies-on-letter-shapes/

Modern Steganography Types of covers (carriers) include – Text – Images – Audio files – Video files Details and Examples

Steganography in TEXT Examples of Encoding Algorithms • Line-shift coding – Moving lines of text up and down by 1/300 th of an inch • Word-shift coding – Moving words left and right • Feature coding – Changing the heights of letters • Other methods

Steganography in Images • Least significant bit insertion (GIF, BMP) – Changing the least significant bit in order to store other data • Discreet Cosine Transform (JPG) – Applying a Cosine function to approximate hidden data Examples



Injected Data Extracted Data Previous slide’s image from Hawaiipictures. com and this slide’s images fom spacedaily. com

Steganography in Audio Examples of Encoding Algorithms • Low bit encoding – Similar to Least Significant bit insertion • Phase encoding – Similar to Discreet Cosine Transform function • Spread Spectrum – Using entire bandwidth to encrypt data. Number of jumps determines amount of data able to hide. • Echo Data Hiding – Next slide

Several Free Steganography Programs are available on the Internet - S-tools - Open. Puff (Free, Open-Source and Portable) -. . .

Exercise 1 in class: Open. PUFF You work in team Use Open. Puff to hide a secret e. Mail your partner and attach the file with the secret Give your partner the password and the algorithm used for the encoding (“by phone”) Decode the message sent by your partner

Exercise 2: Steganalysis Detection of Hidden Information You work individually Use a Hash generator to detect the existence of hidden informatin inside a file Use your favorite Hash Generator or this one: ( Free Portable: http: //www. paehl. de/dp_hash. 7 z )

Exercise 3: Research on Steganalysis Extracting Hidden Information without knowing the Key On the following pages, you will find collections of tools for detecting the existence of a secret. 1) Get a Steganographic message for which you do not know the key 2) Try to extract the secret http: //www. guillermito 2. net/stegano/index. html http: //www. spy-hunter. com/stegspydownload. htm
 Public key cryptography and message authentication
Public key cryptography and message authentication Message integrity
Message integrity Hide text in image steganography
Hide text in image steganography Steganography
Steganography Steganography examples
Steganography examples Echo hiding
Echo hiding Steganography nedir
Steganography nedir Bmpsecrets
Bmpsecrets Image steganography abstract
Image steganography abstract Hydan steganography
Hydan steganography Steganography
Steganography Pin punctures steganography
Pin punctures steganography Niels provos
Niels provos Hydan steganography
Hydan steganography ㅠㅁㄴㄷ64
ㅠㅁㄴㄷ64 Hiderman steganography
Hiderman steganography Steganography
Steganography Steganography
Steganography Cmd ile rar şifresi kırma
Cmd ile rar şifresi kırma Examples of steganography
Examples of steganography Cheddad abbas
Cheddad abbas Gargoyle steganography
Gargoyle steganography Steganography
Steganography Steganography
Steganography Appalex
Appalex Securingthehuman sans org
Securingthehuman sans org