Software Group SOA Governance Runtime Tools In Action




- Slides: 42

Software Group SOA Governance Runtime Tools In Action based on the “IBM SOA Governance at Runtime Po. T” (Po. T = Proof of Technology – A free IBM Hands-on Workshop) Bill. Hahn@us. ibm. com Sr. Consulting Developer/Architect IBM Certified SW IT Specialist Web. Sphere Integration Solution Architect SOA, Web 2. 0, Social Software & Development Tools Evangelist Go to http: //Java. SOA. com for presentations, demos, tutorials and other resources Download demo files and place in same directory as presentaion, then use gold demo buttons at top of slides, while in screenshow mode. ftp: //ftp. software. ibm. com/software/websphere/Java. Dev. Tools/Demos/IBMSW/Governance/Big 6 -Gov-at-Runtime-Scenarios/ (Big 6 -Scenario 1. avi thru Big 6 -Scenario 6. avi)

Agenda What is SOA Governance and the “Governance at Runtime Po. T”? SOA Governance at Runtime Scenarios 1. Analysis of Running Services 2. Dynamic Selection: Quality of Service 3. Dynamic Selection: Message Content or Version 4. Federated Identity Management & Credential Propagation 5. Service Level Management 6. Security Gateway Wrap-up 2

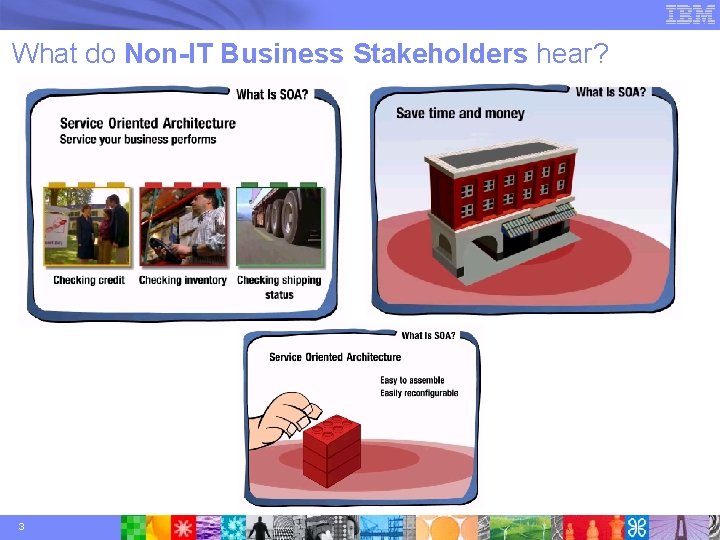
What do Non-IT Business Stakeholders hear? 3

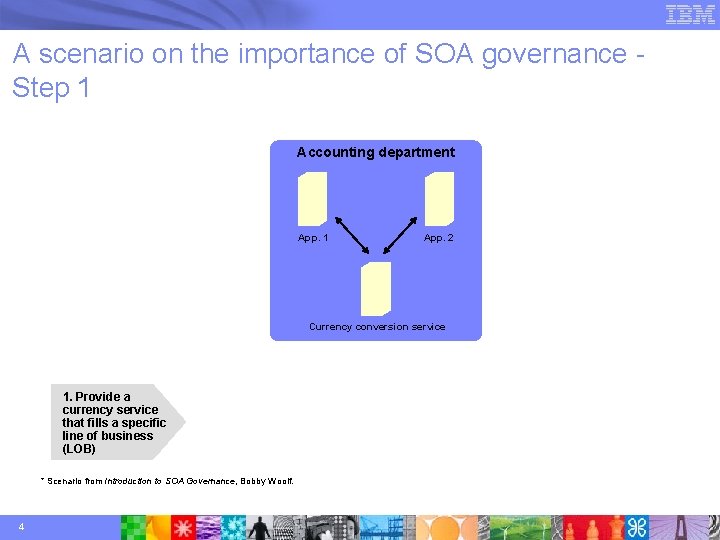
A scenario on the importance of SOA governance Step 1 Accounting department App. 1 App. 2 Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) * Scenario from Introduction to SOA Governance, Bobby Woolf. 4

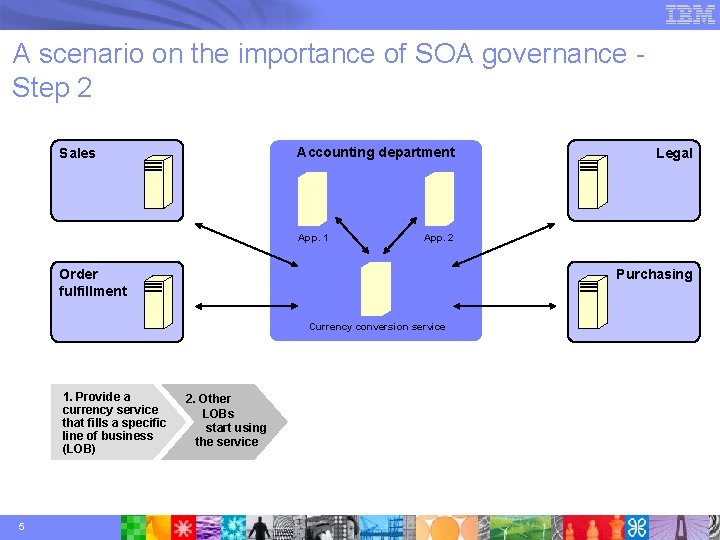
A scenario on the importance of SOA governance Step 2 Accounting department Sales App. 1 App. 2 Order fulfillment Purchasing Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) 5 Legal 2. Other LOBs start using the service

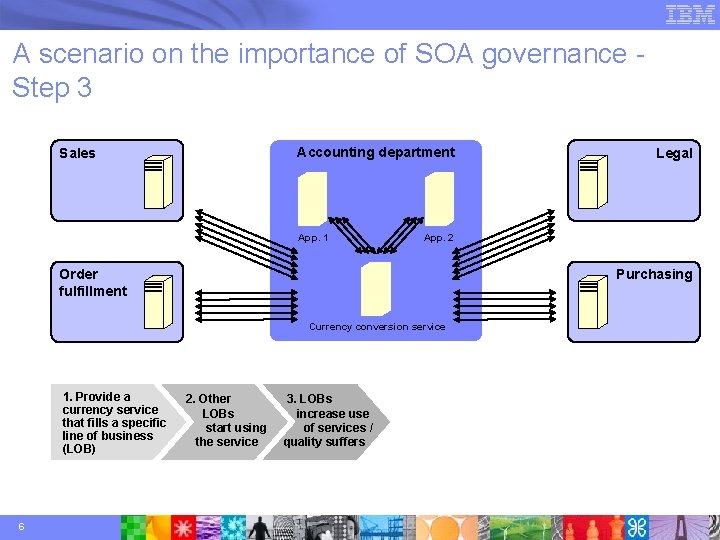
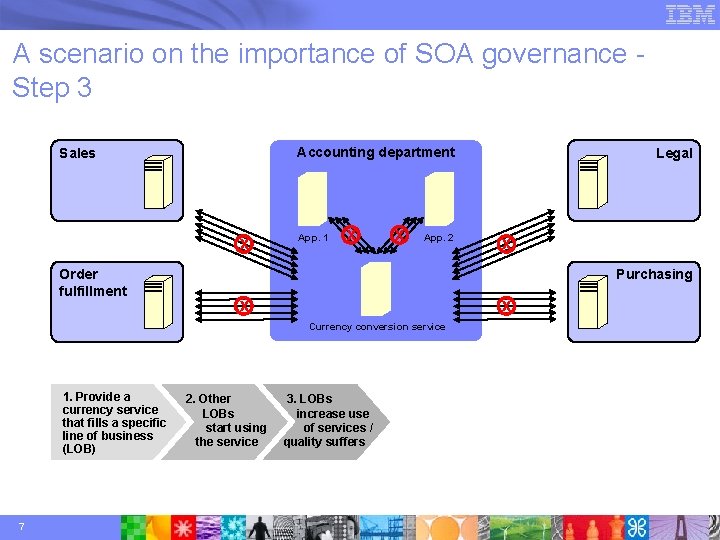
A scenario on the importance of SOA governance Step 3 Accounting department Sales App. 1 App. 2 Order fulfillment Purchasing Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) 6 Legal 2. Other LOBs start using the service 3. LOBs increase use of services / quality suffers

A scenario on the importance of SOA governance Step 3 Accounting department Sales x Order fulfillment App. 1 x x App. 2 7 x Purchasing x x Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) Legal 2. Other LOBs start using the service 3. LOBs increase use of services / quality suffers

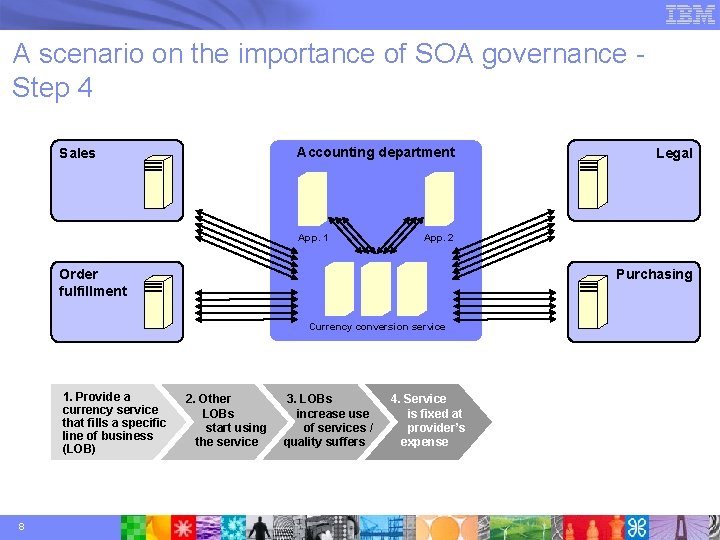
A scenario on the importance of SOA governance Step 4 Accounting department Sales App. 1 App. 2 Order fulfillment Purchasing Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) 8 Legal 2. Other LOBs start using the service 3. LOBs increase use of services / quality suffers 4. Service is fixed at provider’s expense

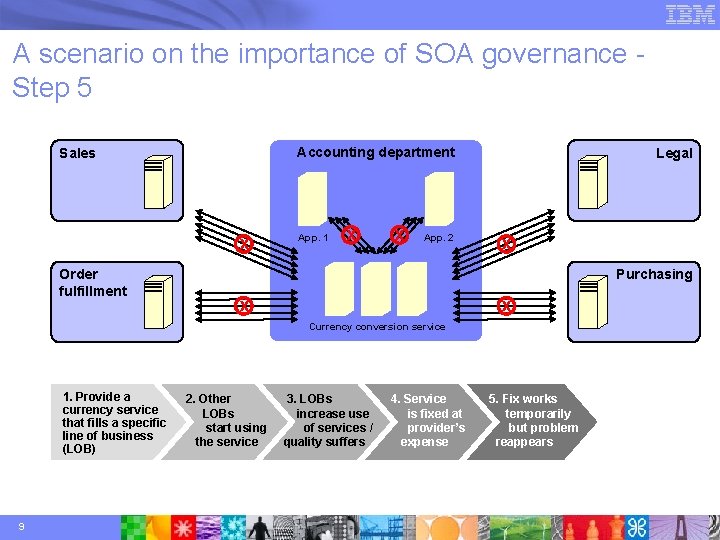
A scenario on the importance of SOA governance Step 5 Accounting department Sales x Order fulfillment App. 1 x x App. 2 Legal x Purchasing x x Currency conversion service 1. Provide a currency service that fills a specific line of business (LOB) 9 2. Other LOBs start using the service 3. LOBs increase use of services / quality suffers 4. Service is fixed at provider’s expense 5. Fix works temporarily but problem reappears

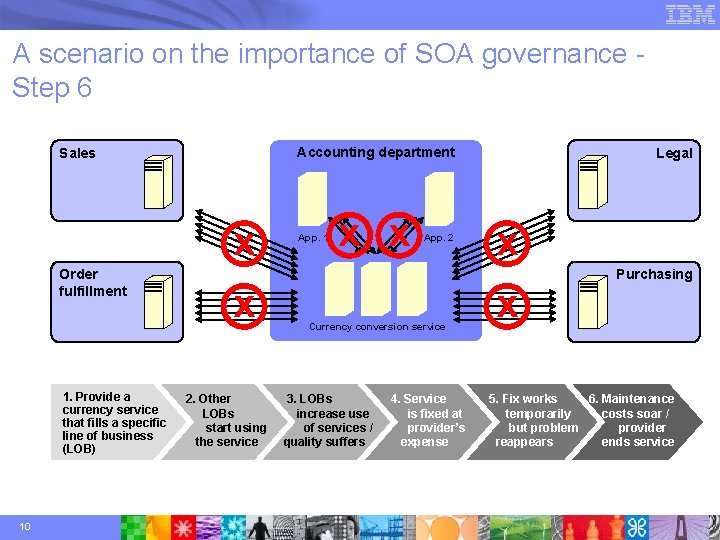
A scenario on the importance of SOA governance Step 6 Accounting department Sales x Order fulfillment 1. Provide a currency service that fills a specific line of business (LOB) 10 x 2. Other LOBs start using the service App. 1 x x App. 2 Currency conversion service 3. LOBs increase use of services / quality suffers 4. Service is fixed at provider’s expense Legal x x Purchasing 5. Fix works 6. Maintenance temporarily costs soar / but problem provider reappears ends service

What Business AND IT Stakeholders need to make SOA Work Well? 11

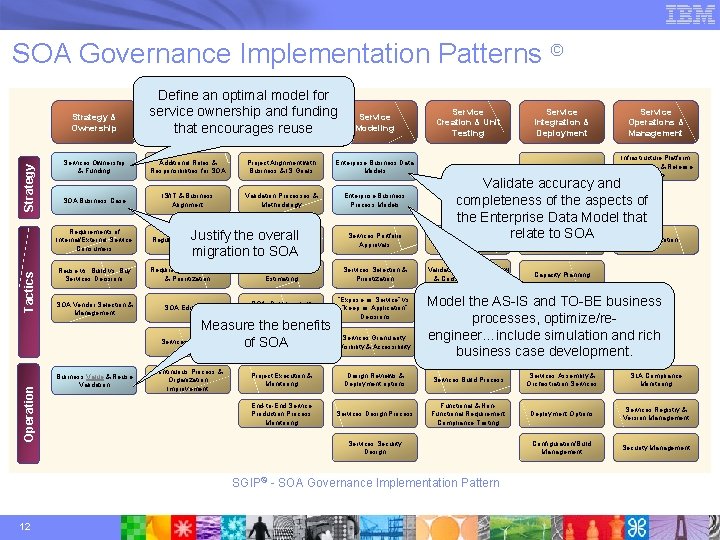
SOA Governance Implementation Patterns © Tactics Strategy & Ownership Define an optimal model for service ownership and funding Organization & SOA Project Planning Management that encourages reuse Services Ownership & Funding Additional Roles & Responsibilities for SOA Project Alignment with Business & IS Goals Enterprise Business Data Models SOA Business Case IS/IT & Business Alignment Validation Processes & Methodology Enterprise Business Process Models Requirements of Internal/External Service Consumers Regulatory Compliance Reuse vs. Build vs. Buy Services Decisions Requirements Gathering & Prioritization Project Planning & Estimating Services Selection & Prioritization SOA Vendor Selection & Management SOA Education SOA Development Approach “Expose as Service” vs. “keep as Application” Decisions Justify the overall Project Business Case migration to SOA Measure the benefits Services Registry of SOA Operation Service Modeling Business Value & Reuse Validation Continuous Process & Organization Improvement Services Portfolio Approvals Services Granularity, Visibility & Accessibility Service Creation & Unit Testing Service Operations & Management SOA Service Certification Infrastructure Platform Components & Release Cycle Validate accuracy and completeness of the aspects of the Enterprise Data Model that SOA Development Tools relate to SOA SLA Definition Acceptance & Training Validation, Design Review & Code Walkthroughs Capacity Planning Model the AS-IS and TO-BE business Services Architectural Options processes, optimize/reengineer…include simulation and rich business case development. Project Execution & Monitoring Design Reviews & Deployment options Services Build Process Services Assembly & Orchestration Services SLA Compliance Monitoring End-to-End Service Production Process Monitoring Services Design Process Functional & Non. Functional Requirement Compliance Testing Deployment Options Services Registry & Version Management Configuration/Build Management Security Management Services Security Design SGIP© - SOA Governance Implementation Pattern 12 Service Integration & Deployment

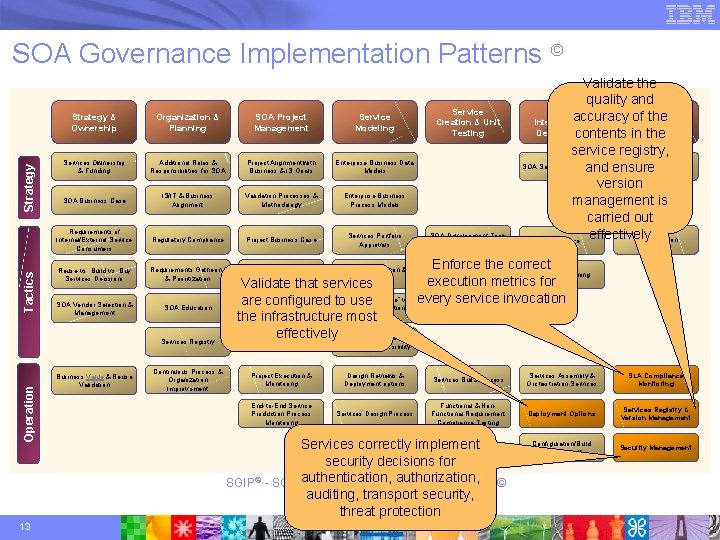
Tactics Strategy SOA Governance Implementation Patterns © Strategy & Ownership Organization & Planning SOA Project Management Service Modeling Services Ownership & Funding Additional Roles & Responsibilities for SOA Project Alignment with Business & IS Goals Enterprise Business Data Models SOA Business Case IS/IT & Business Alignment Validation Processes & Methodology Enterprise Business Process Models Requirements of Internal/External Service Consumers Regulatory Compliance Project Business Case Services Portfolio Approvals Reuse vs. Build vs. Buy Services Decisions Requirements Gathering & Prioritization Project Planning & Estimating Services Selection & Prioritization SOA Vendor Selection & Management SOA Education Operation Services Registry 13 Business Value & Reuse Validation Continuous Process & Organization Improvement Validate that services “Expose as Service” vs. are to use SOAconfigured Development “keep as Application” Approach Decisions the infrastructure most effectively Services Granularity, Service Creation & Unit Testing SOA Development Tools & Training Validate the quality and Service accuracy of. Service the & Integration & Operations Deployment contents Management in the service registry, Infrastructure Platform Components & Release SOA Service Certification and ensure Cycle version management is carried out effectively SLA Definition Acceptance Enforce the correct Capacity Planning execution metrics for every service invocation Services Architectural Validation, Design Review & Code Walkthroughs Options Visibility & Accessibility Project Execution & Monitoring Design Reviews & Deployment options Services Build Process Services Assembly & Orchestration Services SLA Compliance Monitoring End-to-End Service Production Process Monitoring Services Design Process Functional & Non. Functional Requirement Compliance Testing Deployment Options Services Registry & Version Management Configuration/Build Management Security Services correctly implement Design security decisions for authorization, SGIP© - SOA authentication, Governance Implementation Pattern © auditing, transport security, threat protection

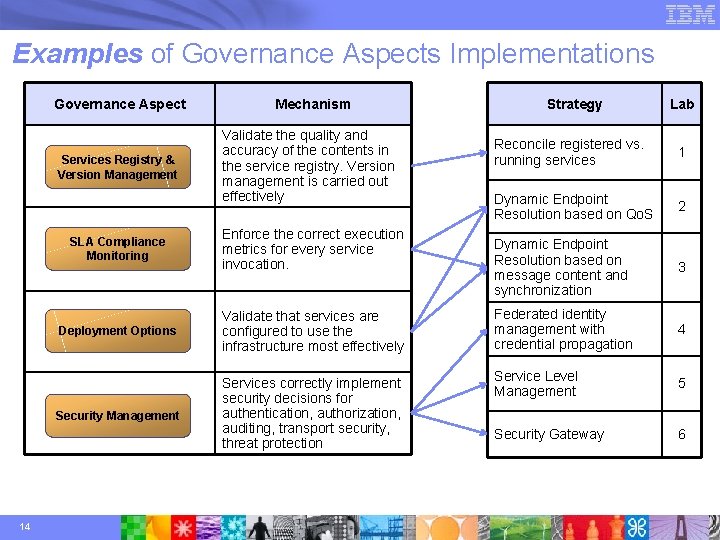
Examples of Governance Aspects Implementations Governance Aspect Services Registry & Version Management 14 Mechanism Validate the quality and accuracy of the contents in the service registry. Version management is carried out effectively SLA Compliance Monitoring Enforce the correct execution metrics for every service invocation. Deployment Options Validate that services are configured to use the infrastructure most effectively Security Management Services correctly implement security decisions for authentication, authorization, auditing, transport security, threat protection Strategy Lab Reconcile registered vs. running services 1 Dynamic Endpoint Resolution based on Qo. S 2 Dynamic Endpoint Resolution based on message content and synchronization 3 Federated identity management with credential propagation 4 Service Level Management 5 Security Gateway 6

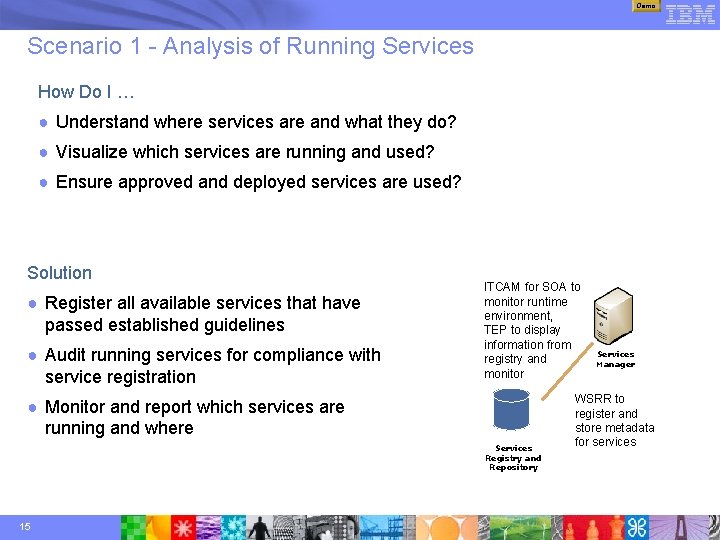
Demo Scenario 1 - Analysis of Running Services How Do I … ● Understand where services are and what they do? ● Visualize which services are running and used? ● Ensure approved and deployed services are used? Solution ● Register all available services that have passed established guidelines ● Audit running services for compliance with service registration ITCAM for SOA to monitor runtime environment, TEP to display information from registry and monitor ● Monitor and report which services are running and where Services Registry and Repository 15 Services Manager WSRR to register and store metadata for services

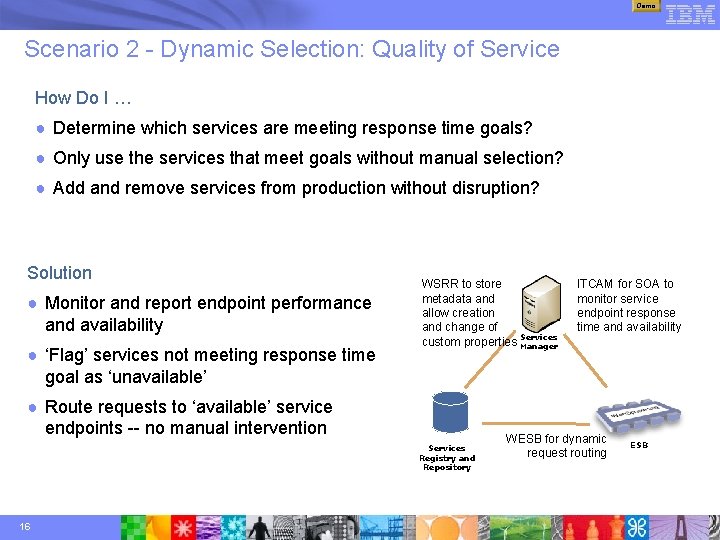
Demo Scenario 2 - Dynamic Selection: Quality of Service How Do I … ● Determine which services are meeting response time goals? ● Only use the services that meet goals without manual selection? ● Add and remove services from production without disruption? Solution ● Monitor and report endpoint performance and availability ● ‘Flag’ services not meeting response time goal as ‘unavailable’ WSRR to store metadata and allow creation and change of Services custom properties Manager ● Route requests to ‘available’ service endpoints -- no manual intervention Services Registry and Repository 16 ITCAM for SOA to monitor service endpoint response time and availability WESB for dynamic request routing ESB

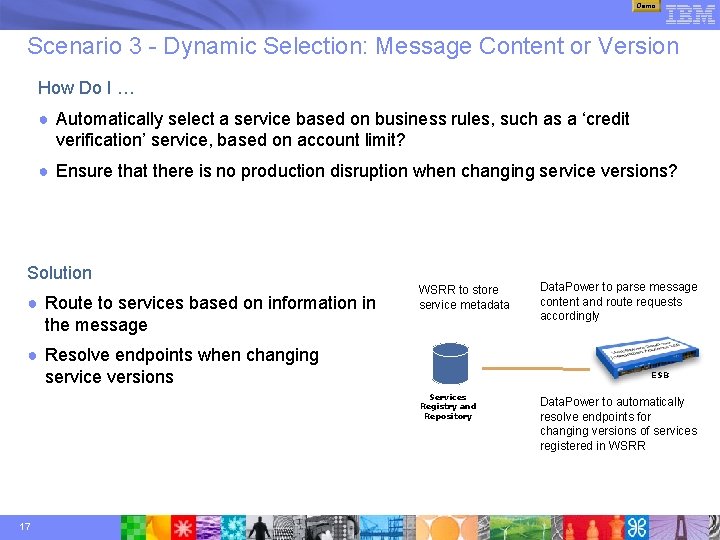
Demo Scenario 3 - Dynamic Selection: Message Content or Version How Do I … ● Automatically select a service based on business rules, such as a ‘credit verification’ service, based on account limit? ● Ensure that there is no production disruption when changing service versions? Solution ● Route to services based on information in the message WSRR to store service metadata ● Resolve endpoints when changing service versions ESB Services Registry and Repository 17 Data. Power to parse message content and route requests accordingly Data. Power to automatically resolve endpoints for changing versions of services registered in WSRR

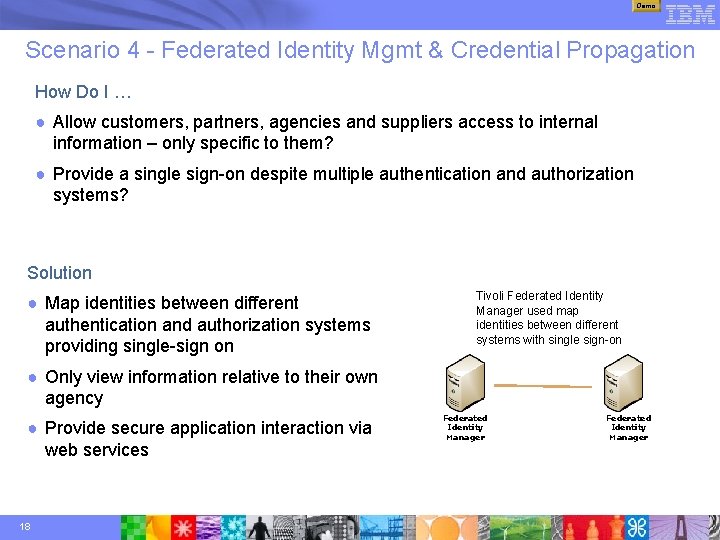
Demo Scenario 4 - Federated Identity Mgmt & Credential Propagation How Do I … ● Allow customers, partners, agencies and suppliers access to internal information – only specific to them? ● Provide a single sign-on despite multiple authentication and authorization systems? Solution ● Map identities between different authentication and authorization systems providing single-sign on Tivoli Federated Identity Manager used map identities between different systems with single sign-on ● Only view information relative to their own agency ● Provide secure application interaction via web services 18 Federated Identity Manager

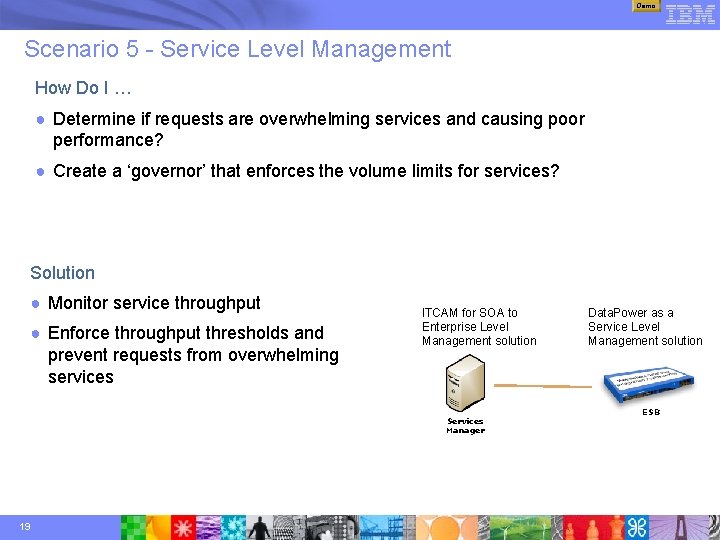
Demo Scenario 5 - Service Level Management How Do I … ● Determine if requests are overwhelming services and causing poor performance? ● Create a ‘governor’ that enforces the volume limits for services? Solution ● Monitor service throughput ● Enforce throughput thresholds and prevent requests from overwhelming services ITCAM for SOA to Enterprise Level Management solution Services Manager 19 Data. Power as a Service Level Management solution ESB

Demo Scenario 6 - Security Gateway How Do I … ● Prevent security threats from external access? ● How do I authenticate, authorize, and audit requests for call center requests of customer information? Solution ● Enforce security policies at runtime ● Inspect requests for denial-of-service attacks and SQL injection Tivoli Federated Identify Manager for authentication, authorization, and token negotiation ● Ensure response integrity, confidentiality and non-repudiation Services Manager 20 Data. Power as a security gateway Security Gateway

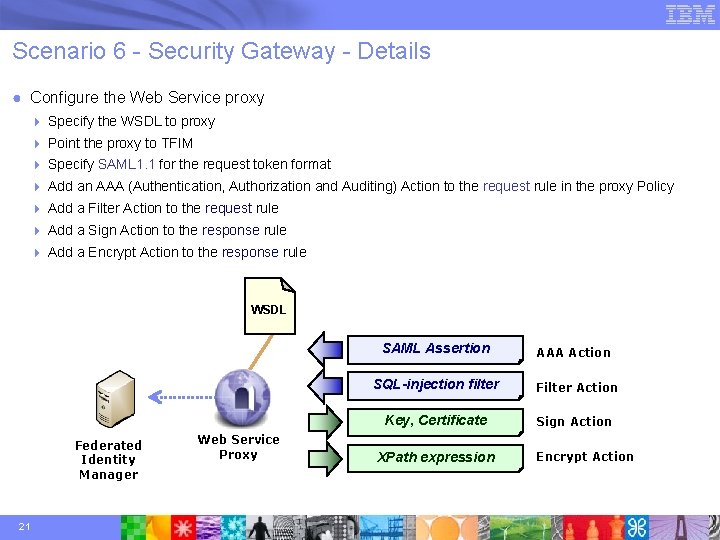
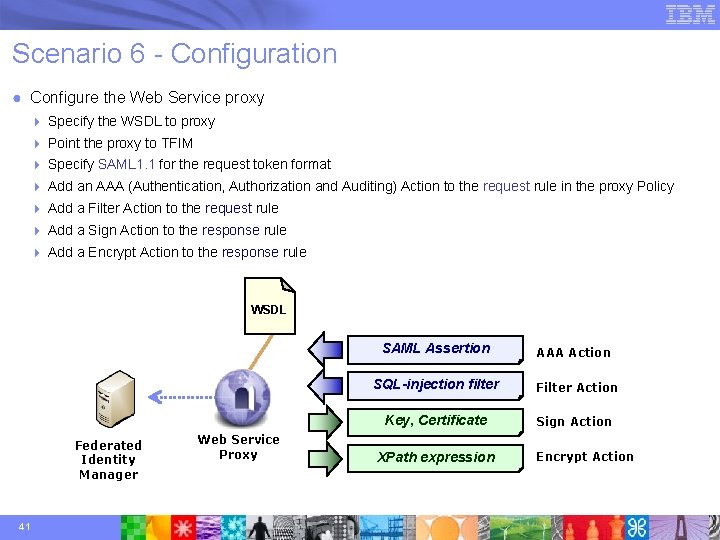
Scenario 6 - Security Gateway - Details ● Configure the Web Service proxy 4 Specify the WSDL to proxy 4 Point the proxy to TFIM 4 Specify SAML 1. 1 for the request token format 4 Add an AAA (Authentication, Authorization and Auditing) Action to the request rule in the proxy Policy 4 Add a Filter Action to the request rule 4 Add a Sign Action to the response rule 4 Add a Encrypt Action to the response rule WSDL SAML Assertion Federated Identity Manager 21 Web Service Proxy AAA Action SQL-injection filter Filter Action Key, Certificate Sign Action XPath expression Encrypt Action

Resources http: //ibm. com/developer (IBM developer. Works for technologies and/or products) Java, J 2 EE, Web Services and other technology zones are on the left hand side Web. Sphere Zone: http: //ibm. com/developer/websphere Rational Zone: http: //ibm. com/developer/rational Free Education Portal: http: //ibm. com/developer/training http: //www. redbooks. ibm. com (How-To Step-by-step Practical Implementation Books) http: //ibmsoasoftware. com/ (a. k. a. Java. SOA. com, Web. Sphere. Central. com) (Tutorials, Links, Presentations, White Papers, Articles, etc. ) 22

BACKUP SLIDES and “Governance at Runtime Po. T” Scenario Details 23

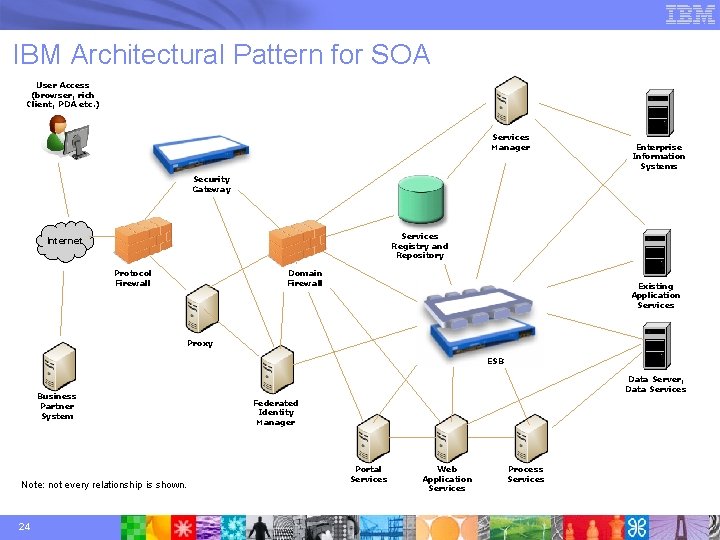
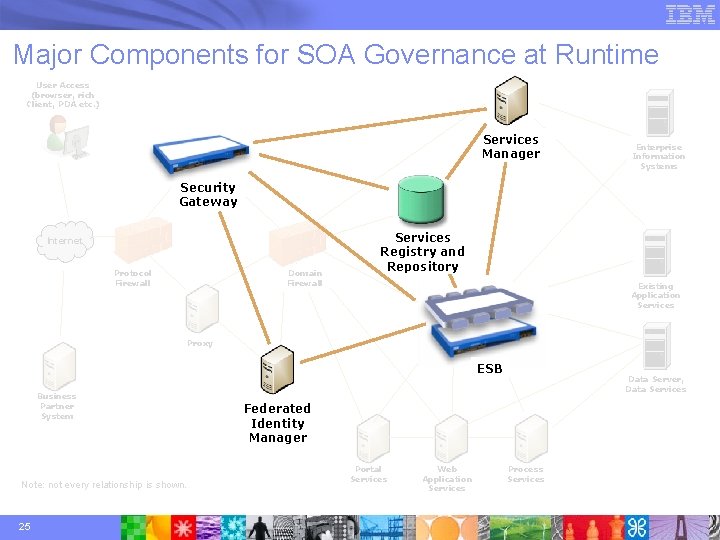
IBM Architectural Pattern for SOA User Access (browser, rich Client, PDA etc. ) Services Manager Enterprise Information Systems Security Gateway Services Registry and Repository Internet Protocol Firewall Domain Firewall Existing Application Services Proxy ESB Business Partner System Note: not every relationship is shown. 24 Data Server, Data Services Federated Identity Manager Portal Services Web Application Services Process Services

Major Components for SOA Governance at Runtime User Access (browser, rich Client, PDA etc. ) Services Manager Enterprise Information Systems Security Gateway Services Registry and Registry Repositoryand Internet Protocol Firewall Domain Firewall Repository Existing Application Services Proxy ESB Business Partner System Note: not every relationship is shown. 25 Data Server, Data Services Federated Identity Manager Portal Services Web Application Services Process Services

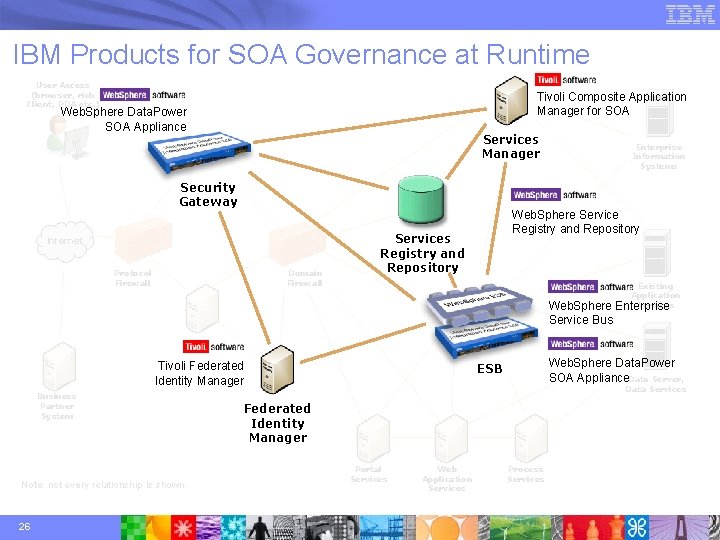
IBM Products for SOA Governance at Runtime User Access (browser, rich Client, PDA etc. ) Tivoli Composite Application Manager for SOA Web. Sphere Data. Power SOA Appliance Services Manager Enterprise Information Systems Security Gateway Web. Sphere Service Registry and Repository Services Registry and Registry Repositoryand Internet Protocol Firewall Domain Firewall Repository Web. Sphere Service Bus Existing Application Services Enterprise Proxy ESB Tivoli Federated Identity Manager Business Partner System Web. Sphere Data. Power SOA Appliance. Data Server, ESB Data Services Federated Identity Manager Note: not every relationship is shown. 26 Portal Services Web Application Services Process Services

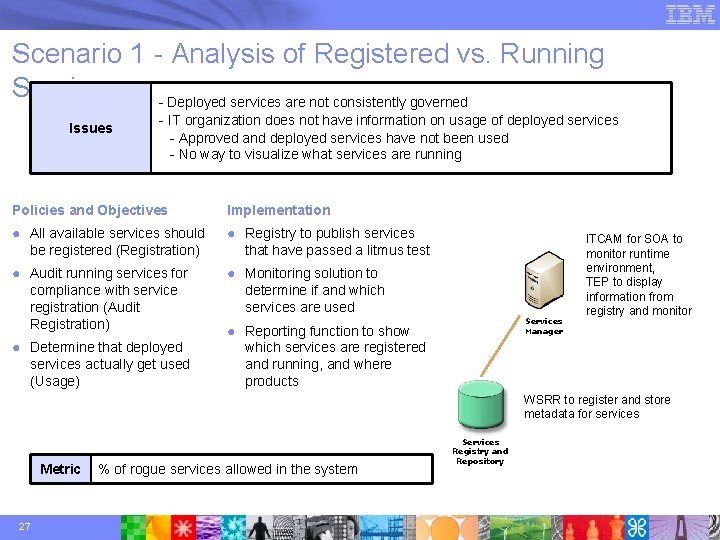
Scenario 1 - Analysis of Registered vs. Running Services - Deployed services are not consistently governed Issues - IT organization does not have information on usage of deployed services - Approved and deployed services have not been used - No way to visualize what services are running Policies and Objectives Implementation ● All available services should be registered (Registration) ● Registry to publish services that have passed a litmus test ● Audit running services for compliance with service registration (Audit Registration) ● Monitoring solution to determine if and which services are used ● Determine that deployed services actually get used (Usage) Services Manager ● Reporting function to show which services are registered and running, and where products ITCAM for SOA to monitor runtime environment, TEP to display information from registry and monitor WSRR to register and store metadata for services Metric 27 % of rogue services allowed in the system Services Registry and Repository

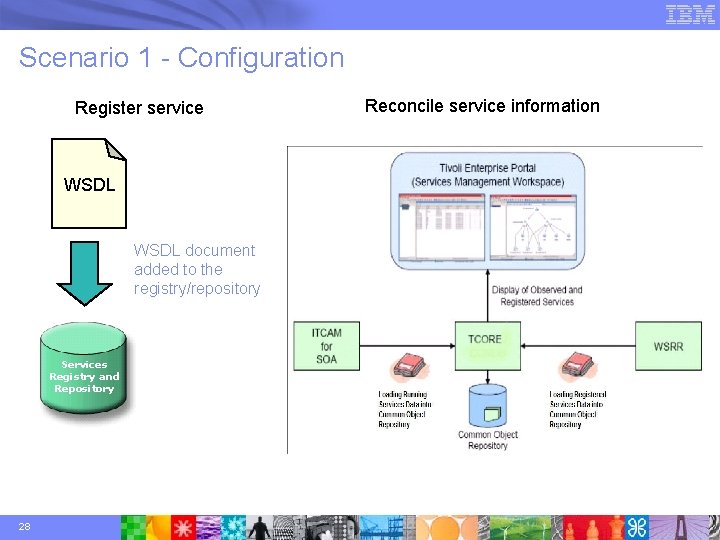
Scenario 1 - Configuration Register service WSDL document added to the registry/repository Services Registry and Repository 28 Reconcile service information

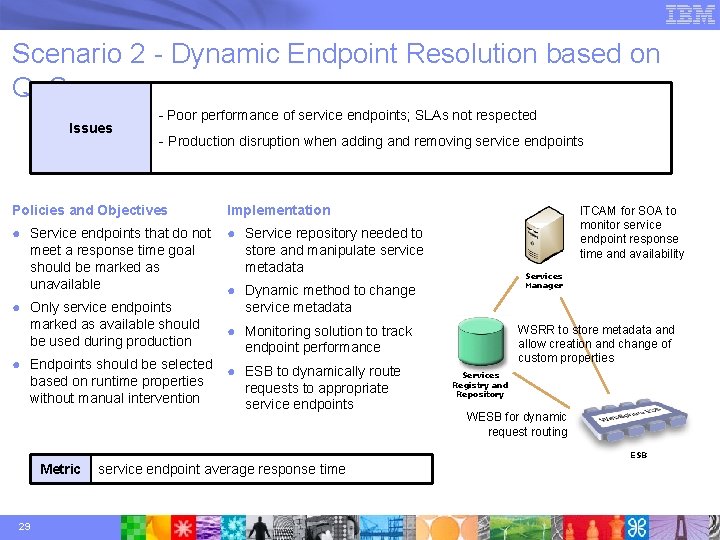
Scenario 2 - Dynamic Endpoint Resolution based on Qo. S Issues - Poor performance of service endpoints; SLAs not respected - Production disruption when adding and removing service endpoints Policies and Objectives Implementation ● Service endpoints that do not meet a response time goal should be marked as unavailable ● Service repository needed to store and manipulate service metadata ● Only service endpoints marked as available should be used during production ITCAM for SOA to monitor service endpoint response time and availability Services Manager ● Dynamic method to change service metadata ● Monitoring solution to track endpoint performance ● Endpoints should be selected ● ESB to dynamically route based on runtime properties requests to appropriate without manual intervention service endpoints WSRR to store metadata and allow creation and change of custom properties Services Registry and Repository WESB for dynamic request routing ESB Metric 29 service endpoint average response time

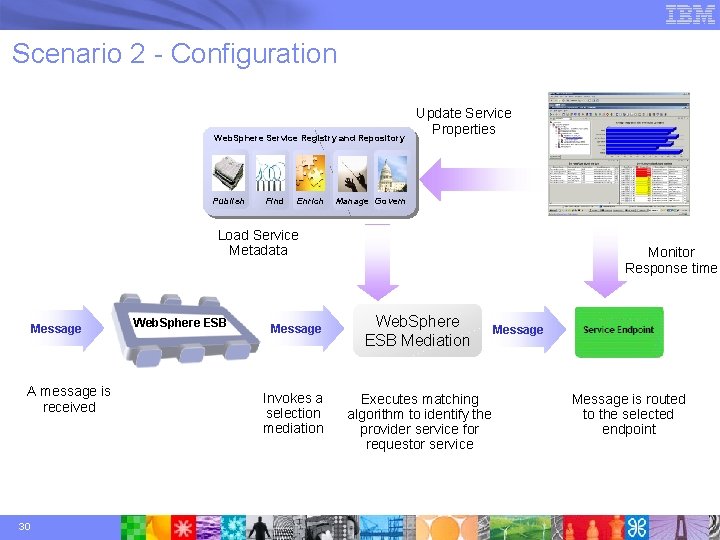
Scenario 2 - Configuration Web. Sphere Service Registry and Repository Publish Find Enrich Update Service Properties Manage Govern Load Service Metadata Message A message is received 30 Web. Sphere ESB Message Invokes a selection mediation Monitor Response time Web. Sphere ESB Mediation Executes matching algorithm to identify the provider service for requestor service Message is routed to the selected endpoint

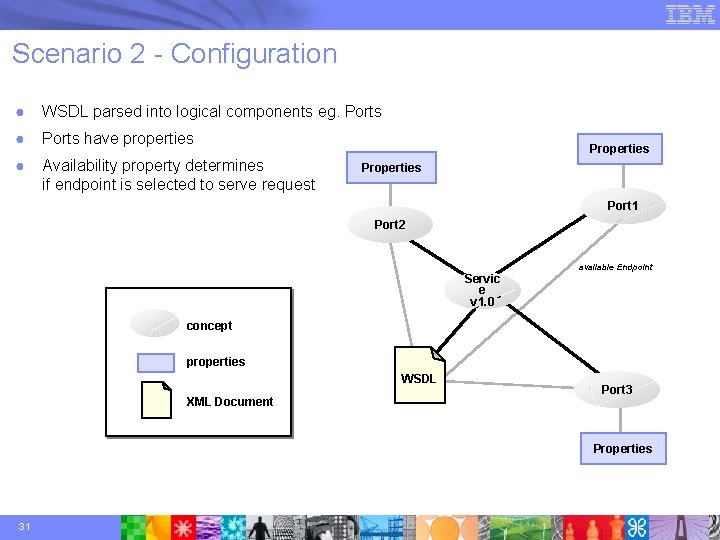
Scenario 2 - Configuration ● WSDL parsed into logical components eg. Ports ● Ports have properties ● Availability property determines if endpoint is selected to serve request Properties Port 1 Port 2 Servic e v 1. 0 available Endpoint concept properties WSDL XML Document Port 3 Properties 31

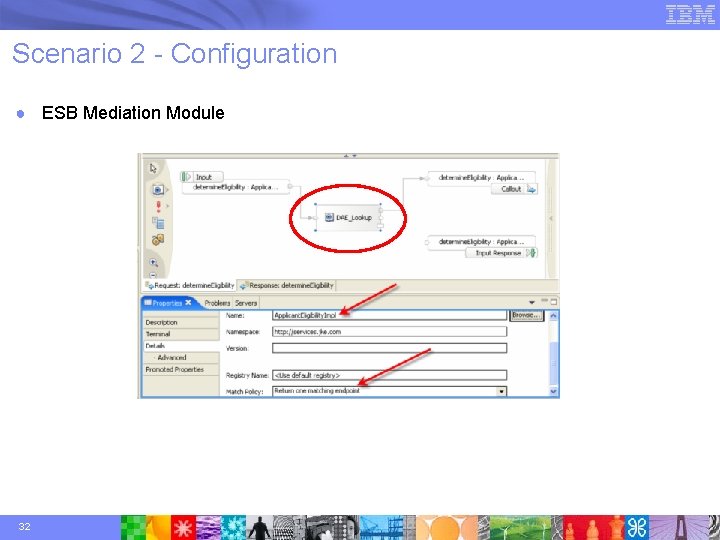
Scenario 2 - Configuration ● ESB Mediation Module 32

Scenario 3 - Dynamic Endpoint Resolution based on Content and Subscription Issues No automatic selection of service providers based on rules Production disruption when changing service versions Policies and Objectives Implementation ● Service provider (credit verification) should be automatically selected based on the account limit ● Service Registry to store service template ● Endpoints should be automatically selected based on specified version Metric 33 ● ESB with ability to make decisions based on message content ● ESB to make routing decisions based on information obtained from subscription to service registry WSRR to store service metadata Services Registry and Repository Data. Power to parse message content and route requests accordingly Data. Power to automatically resolve endpoints for changing versions of services registered in time needed to change version for service in production WSRR ESB

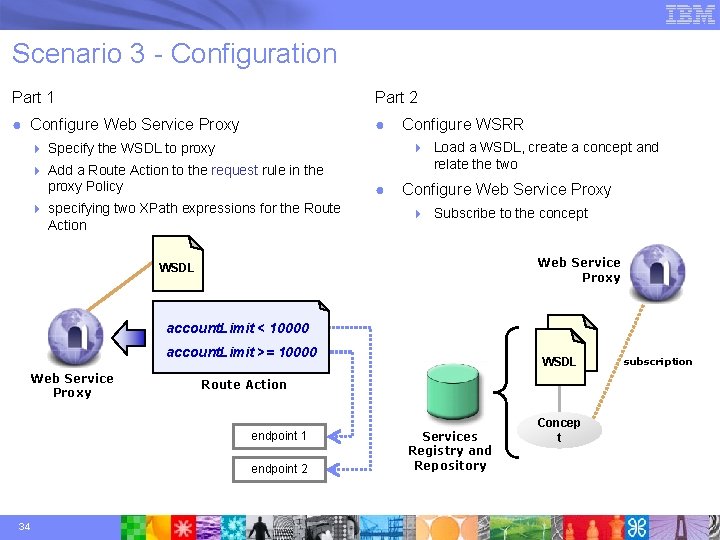
Scenario 3 - Configuration Part 1 Part 2 ● Configure Web Service Proxy ● 4 Load a WSDL, create a concept and relate the two 4 Specify the WSDL to proxy 4 Add a Route Action to the request rule in the proxy Policy 4 specifying two XPath expressions for the Route Action Configure WSRR ● Configure Web Service Proxy 4 Subscribe to the concept Web Service Proxy WSDL account. Limit < 10000 account. Limit >= 10000 Web Service Proxy Route Action endpoint 1 endpoint 2 34 WSDL Services Registry and Repository Concep t subscription

Scenario 4 - Federated Identity Management and Credential Propagation Issues Multiple Authentication and Authorization systems to give partners access to JK portal Policies and Objectives Implementation ● Agencies can sign in and be authenticated once to gain access to resources in JK ● Federated identity solution to map identities between different authentication and authorization systems ● Only Agency managers are allowed to run View Profiles application ● Single sign-on ● Agency managers can only view information about employees in their own agencies Metric 35 TFIM used as the Identity Provider (Agency) # of unauthorized entries TFIM used as the Service Provider (JKE) Federated Identity Manager

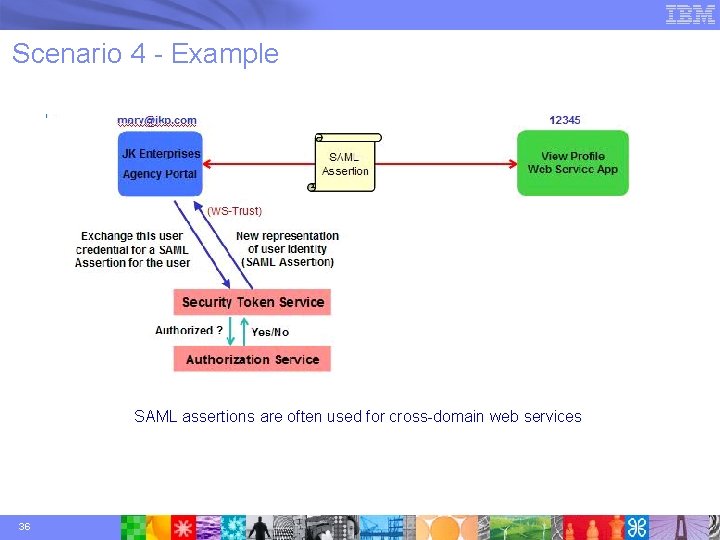
Scenario 4 - Example SAML assertions are often used for cross-domain web services 36

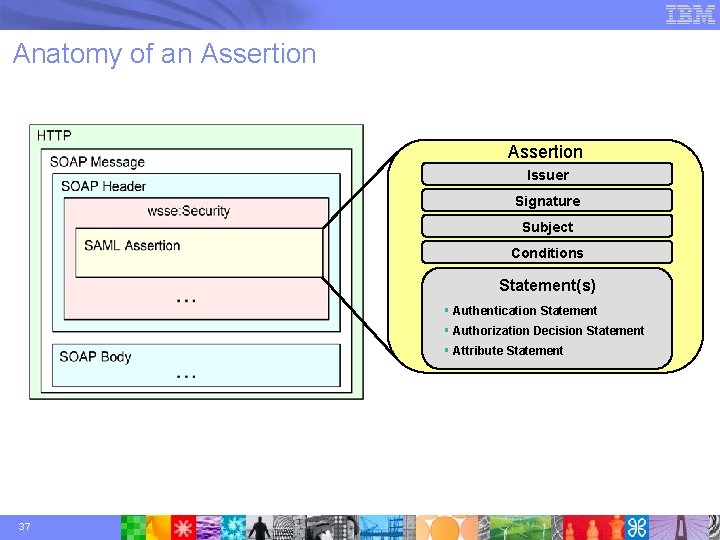
Anatomy of an Assertion Issuer Signature Subject Conditions Statement(s) § Authentication Statement § Authorization Decision Statement § Attribute Statement 37

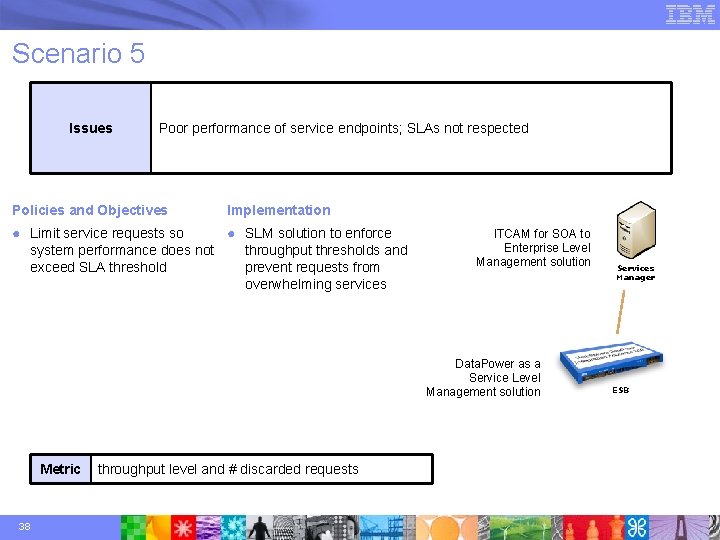
Scenario 5 Issues Poor performance of service endpoints; SLAs not respected Policies and Objectives Implementation ● Limit service requests so ● SLM solution to enforce system performance does not throughput thresholds and exceed SLA threshold prevent requests from overwhelming services ITCAM for SOA to Enterprise Level Management solution Data. Power as a Service Level Management solution Metric 38 throughput level and # discarded requests Services Manager ESB

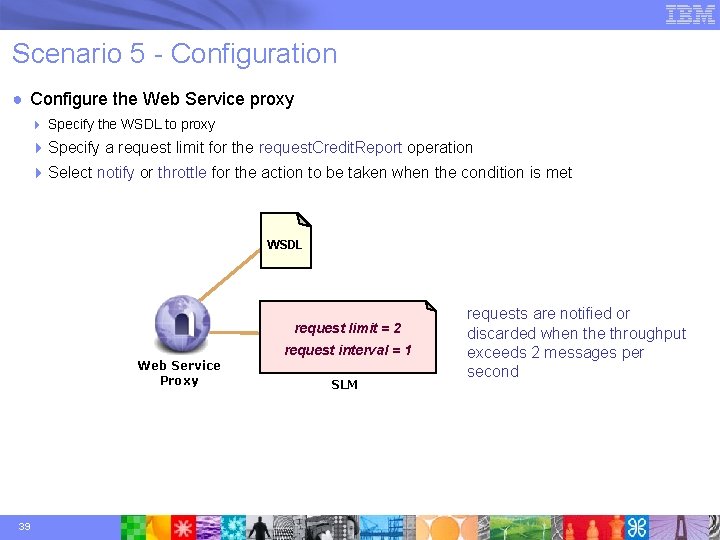
Scenario 5 - Configuration ● Configure the Web Service proxy 4 Specify the WSDL to proxy 4 Specify a request limit for the request. Credit. Report operation 4 Select notify or throttle for the action to be taken when the condition is met WSDL request limit = 2 request interval = 1 Web Service Proxy 39 SLM requests are notified or discarded when the throughput exceeds 2 messages per second

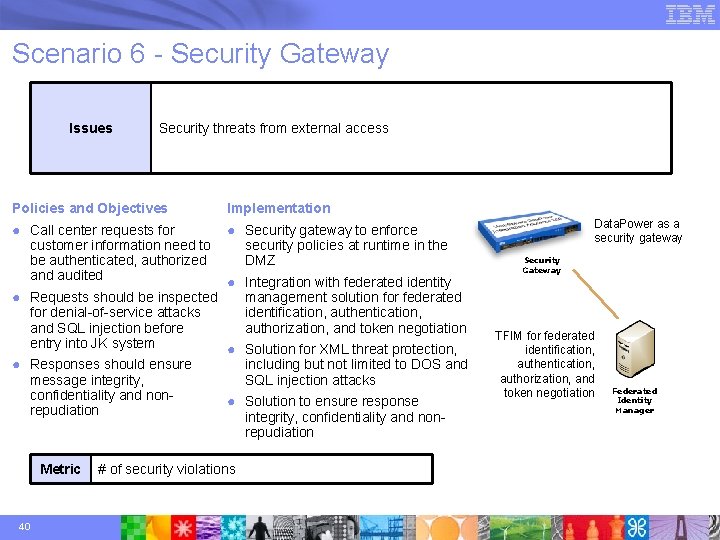
Scenario 6 - Security Gateway Issues Security threats from external access Policies and Objectives Implementation ● Call center requests for customer information need to be authenticated, authorized and audited ● Security gateway to enforce security policies at runtime in the DMZ ● Integration with federated identity ● Requests should be inspected management solution for federated for denial-of-service attacks identification, authentication, and SQL injection before authorization, and token negotiation entry into JK system ● Solution for XML threat protection, ● Responses should ensure message integrity, confidentiality and nonrepudiation Metric 40 including but not limited to DOS and SQL injection attacks ● Solution to ensure response integrity, confidentiality and nonrepudiation # of security violations Data. Power as a security gateway Security Gateway TFIM for federated identification, authentication, authorization, and token negotiation Federated Identity Manager

Scenario 6 - Configuration ● Configure the Web Service proxy 4 Specify the WSDL to proxy 4 Point the proxy to TFIM 4 Specify SAML 1. 1 for the request token format 4 Add an AAA (Authentication, Authorization and Auditing) Action to the request rule in the proxy Policy 4 Add a Filter Action to the request rule 4 Add a Sign Action to the response rule 4 Add a Encrypt Action to the response rule WSDL SAML Assertion Federated Identity Manager 41 Web Service Proxy AAA Action SQL-injection filter Filter Action Key, Certificate Sign Action XPath expression Encrypt Action

Resources http: //ibm. com/developer (IBM developer. Works for technologies and/or products) Java, J 2 EE, Web Services and other technology zones are on the left hand side Web. Sphere Zone: http: //ibm. com/developer/websphere Rational Zone: http: //ibm. com/developer/rational Free Education Portal: http: //ibm. com/developer/training http: //www. redbooks. ibm. com (How-To Step-by-step Practical Implementation Books) http: //Rational. Central. com (a. k. a. Java. SOA. com, SOAWeb 20. com, Web. Sphere. Central. com) (Tutorials, Links, Presentations, White Papers, Articles, etc. ) 42