SIA 206 Keep Your Information Safe Josh Heller











- Slides: 25

SIA 206 Keep Your Information Safe! Josh Heller Sr. Product Manager Microsoft Corporation

Consumerization of IT Advanced Persistent Threat Expanding Importance of Identity Cloud Computing Government Interests

Information Privacy is the most important security concern in the enterprise, outranking malware for the first time

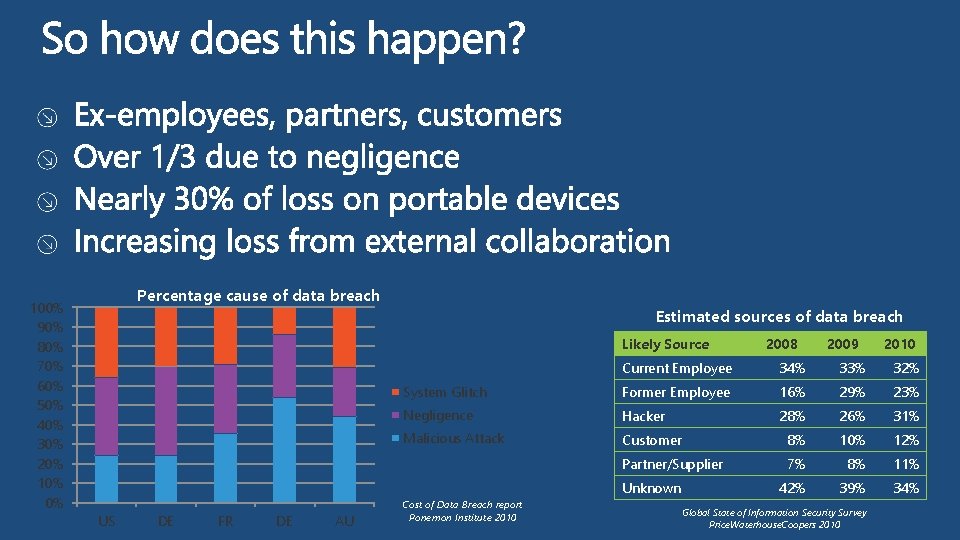
100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0% Percentage cause of data breach Estimated sources of data breach Likely Source DE FR DE AU 2009 2010 Current Employee 34% 33% 32% System Glitch Former Employee 16% 29% 23% Negligence Hacker 28% 26% 31% Malicious Attack Customer 8% 10% 12% Partner/Supplier 7% 8% 11% 42% 39% 34% Unknown US 2008 Cost of Data Breach report Ponemon Institute 2010 Global State of Information Security Survey Price. Waterhouse. Coopers 2010

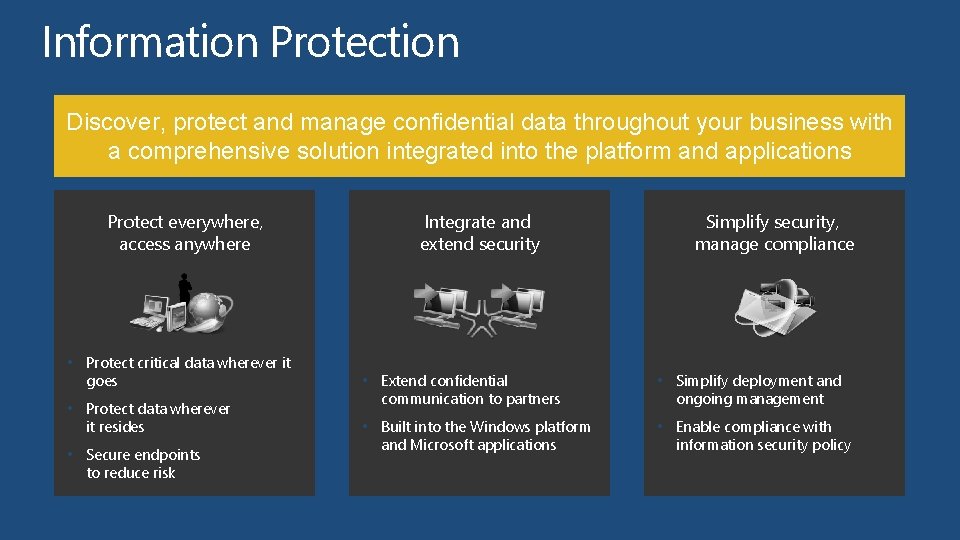
Information Protection Discover, protect and manage confidential data throughout your business with a comprehensive solution integrated into the platform and applications Protect everywhere, access anywhere • Protect critical data wherever it goes • Protect data wherever it resides • Secure endpoints to reduce risk Integrate and extend security Simplify security, manage compliance • Extend confidential • Simplify deployment and • Built into the Windows platform • Enable compliance with communication to partners and Microsoft applications ongoing management information security policy

Active Directory Rights Management Services

+ Persistent Protection Encryption Policy: Access Permissions Use Right Permissions

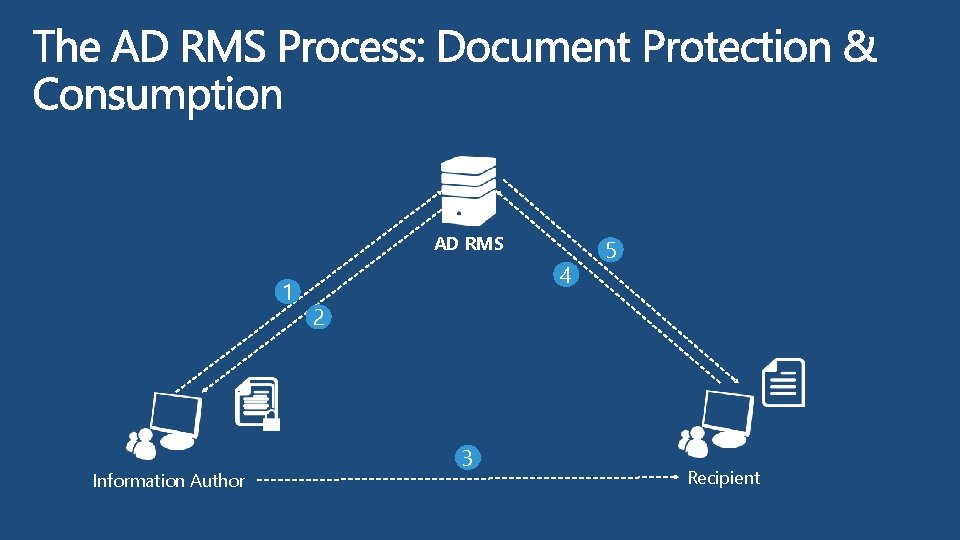
AD RMS 1 Information Author 4 5 2 3 Recipient

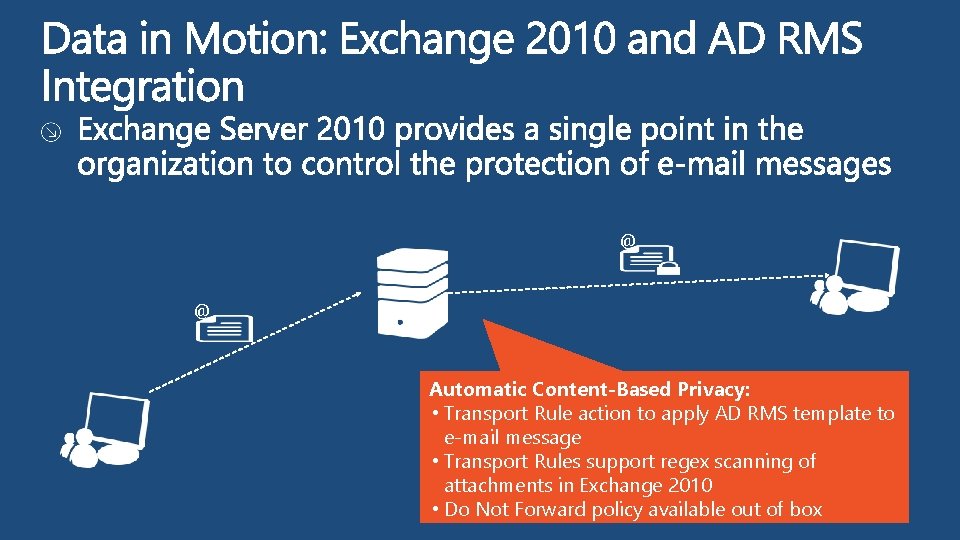
@ @ Automatic Content-Based Privacy: • Transport Rule action to apply AD RMS template to e-mail message • Transport Rules support regex scanning of attachments in Exchange 2010 • Do Not Forward policy available out of box

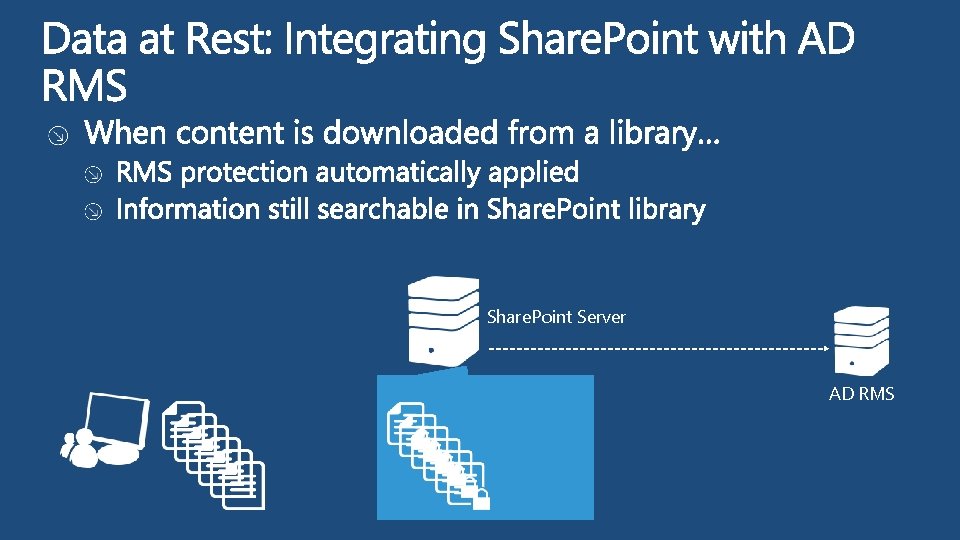
Share. Point Server AD RMS


Demo AD Rights Management Services

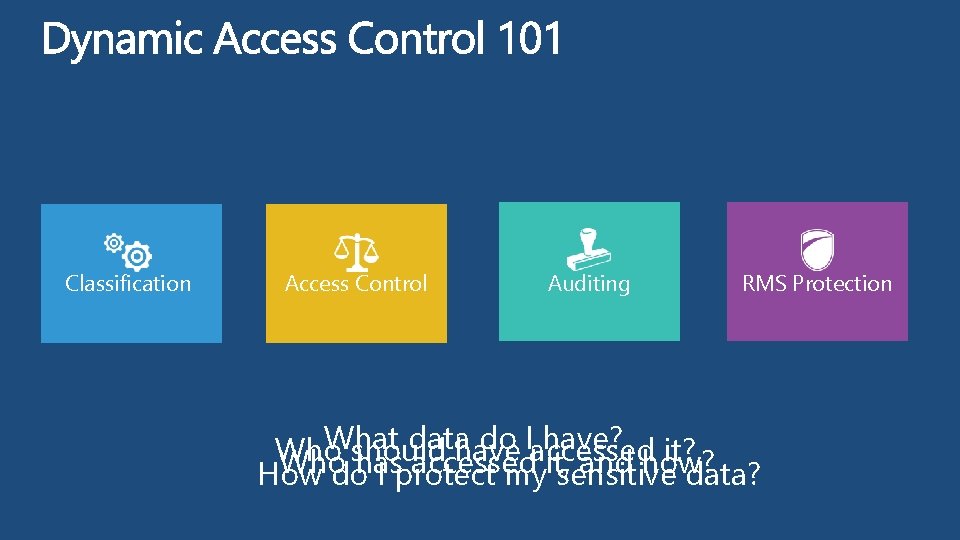
Classification Access Control Auditing RMS Protection What datahave do Iaccessed have? it? Who should Whodohas accessed and how? How I protect myit, sensitive data?

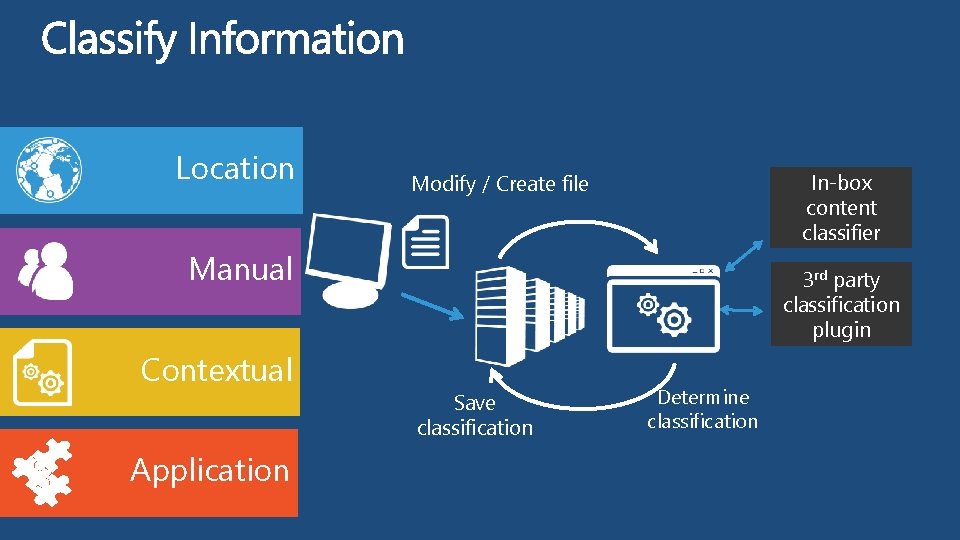
Location In-box content classifier Modify / Create file Manual Contextual Application 3 rd party classification plugin Save classification Determine classification

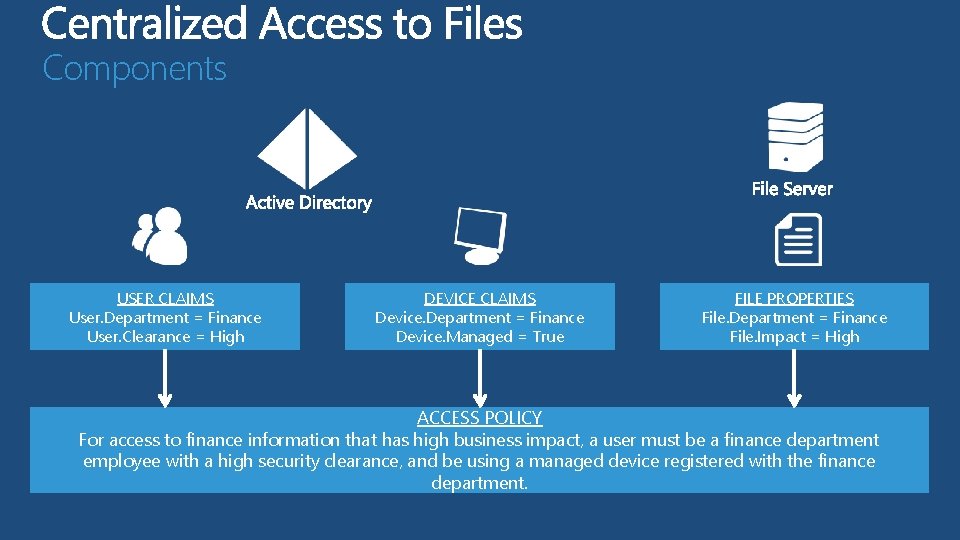
Components USER CLAIMS User. Department = Finance User. Clearance = High DEVICE CLAIMS Device. Department = Finance Device. Managed = True FILE PROPERTIES File. Department = Finance File. Impact = High ACCESS POLICY For access to finance information that has high business impact, a user must be a finance department employee with a high security clearance, and be using a managed device registered with the finance department.

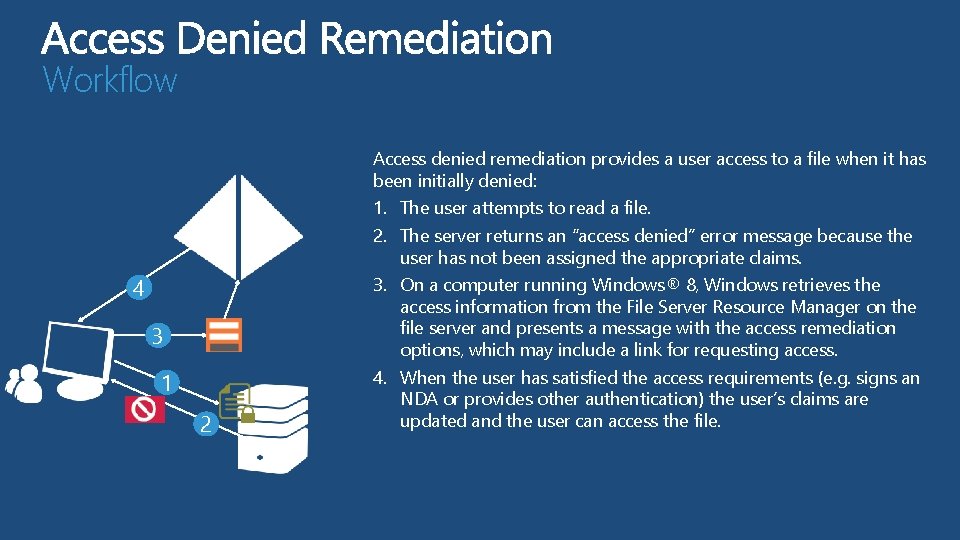
Workflow Access denied remediation provides a user access to a file when it has been initially denied: 4 3 1 2 1. The user attempts to read a file. 2. The server returns an “access denied” error message because the user has not been assigned the appropriate claims. 3. On a computer running Windows® 8, Windows retrieves the access information from the File Server Resource Manager on the file server and presents a message with the access remediation options, which may include a link for requesting access. 4. When the user has satisfied the access requirements (e. g. signs an NDA or provides other authentication) the user’s claims are updated and the user can access the file.

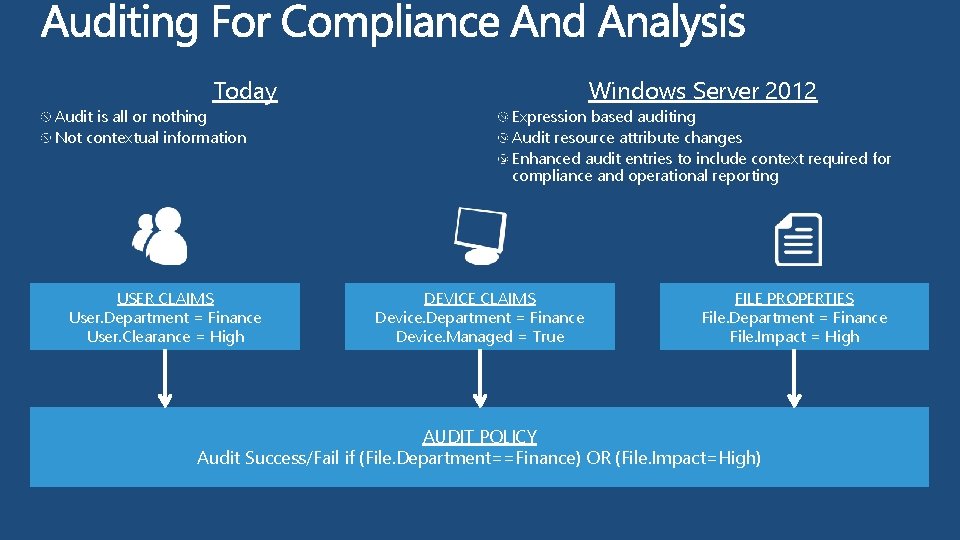
Today Audit is all or nothing Not contextual information USER CLAIMS User. Department = Finance User. Clearance = High Windows Server 2012 Expression based auditing Audit resource attribute changes Enhanced audit entries to include context required for compliance and operational reporting DEVICE CLAIMS Device. Department = Finance Device. Managed = True FILE PROPERTIES File. Department = Finance File. Impact = High AUDIT POLICY Audit Success/Fail if (File. Department==Finance) OR (File. Impact=High)

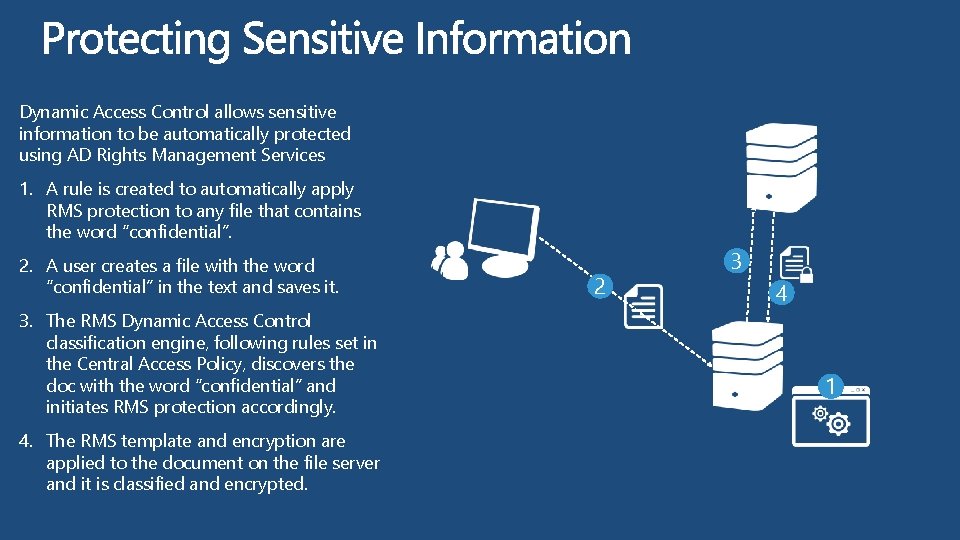
Dynamic Access Control allows sensitive information to be automatically protected using AD Rights Management Services 1. A rule is created to automatically apply RMS protection to any file that contains the word “confidential”. 2. A user creates a file with the word “confidential” in the text and saves it. 3. The RMS Dynamic Access Control classification engine, following rules set in the Central Access Policy, discovers the doc with the word “confidential” and initiates RMS protection accordingly. 4. The RMS template and encryption are applied to the document on the file server and it is classified and encrypted. 2 3 4 1

Dynamic Access Control

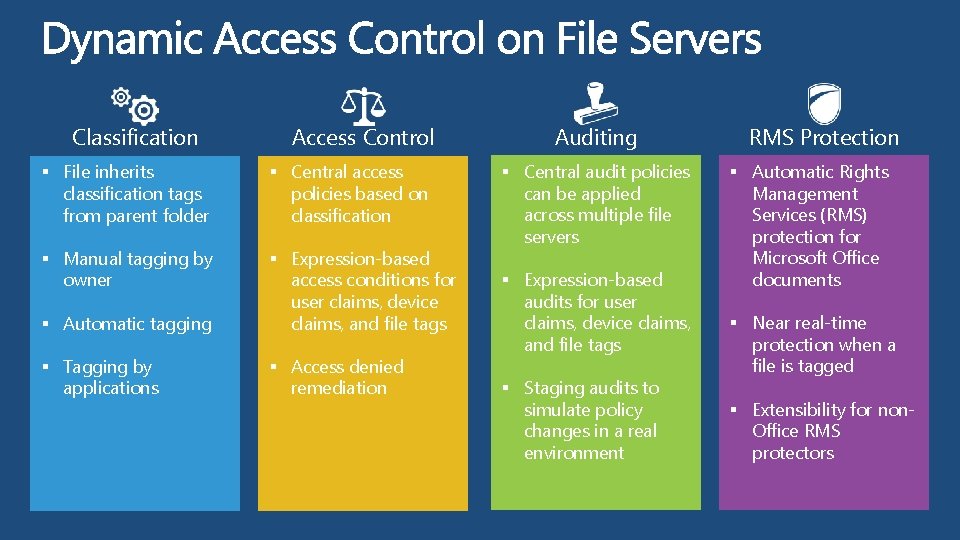
Classification Access Control § File inherits classification tags from parent folder § Central access policies based on classification § Manual tagging by owner § Automatic tagging § Expression-based access conditions for user claims, device claims, and file tags § Tagging by applications § Access denied remediation Auditing § Central audit policies can be applied across multiple file servers § Expression-based audits for user claims, device claims, and file tags § Staging audits to simulate policy changes in a real environment RMS Protection § Automatic Rights Management Services (RMS) protection for Microsoft Office documents § Near real-time protection when a file is tagged § Extensibility for non. Office RMS protectors

#TESIA 206 Hands-On Labs Talk to our Experts at the TLC DOWNLOAD Windows Server 2012 Release Candidate DOWNLOAD Microsoft System Center 2012 Evaluation microsoft. com/windowsserver microsoft. com/systemcenter

Learning Connect. Share. Discuss. Microsoft Certification & Training Resources http: //europe. msteched. com www. microsoft. com/learning Tech. Net Resources for IT Professionals Resources for Developers http: //microsoft. com/technet http: //microsoft. com/msdn

Evaluations Submit your evals online http: //europe. msteched. com/sessions

