Security Services Cloud Security Management monitoring and standards




- Slides: 18


Security Services Cloud Security Management monitoring and standards enforcement for cloud resources. Data Security controls around sensitive data such as data loss prevention and data discovery. Firewall/IPS Preventing malicious activity from entering campus networks. Incident Management Coordinating response and investigation of security incidents to mitigate damage, ensure legal compliance, and expedite remediation. Security Assessment & Consultation Reviewing application data discovery and classification, code reviews, consultation, risk assessment, architecture assessment, and penetration testing. Security Awareness & Training Security training and security awareness programs for end users Security Event Monitoring & Management Aggregation, monitoring, and alerting for security events from application logs, server logs, network logs, firewall logs, or any other log source. System Security System-level monitoring and protection such as web application firewalls, endpoint, security, and database firewalls. Metrics and Reporting Metrics on incidents, vulnerabilities, and tools. Threat & Federated Intelligence Integration of external intelligence feeds to enhance threat detection and internal integrations to enhance context around events. Network Security Monitoring/IDS Logging network traffic within campus (eastwest) and at the border. Vulnerability Management Detection and tracking of security vulnerabilities by system, department, and severity.

CES Information Security Risk & Compliance Making our campus communities better, by providing efficient information security risk management services. Mission Statement: The Church Educational System (CES) Information Security Risk (ISR) team assists in identifying, evaluating, and monitoring information security risk and compliance at BYU, BYU-Idaho, BYU-Hawaii, and Ensign College. As a partner with each campus community, the ISR team provides professional cybersecurity consulting services that help safeguard IT assets, data, and people.

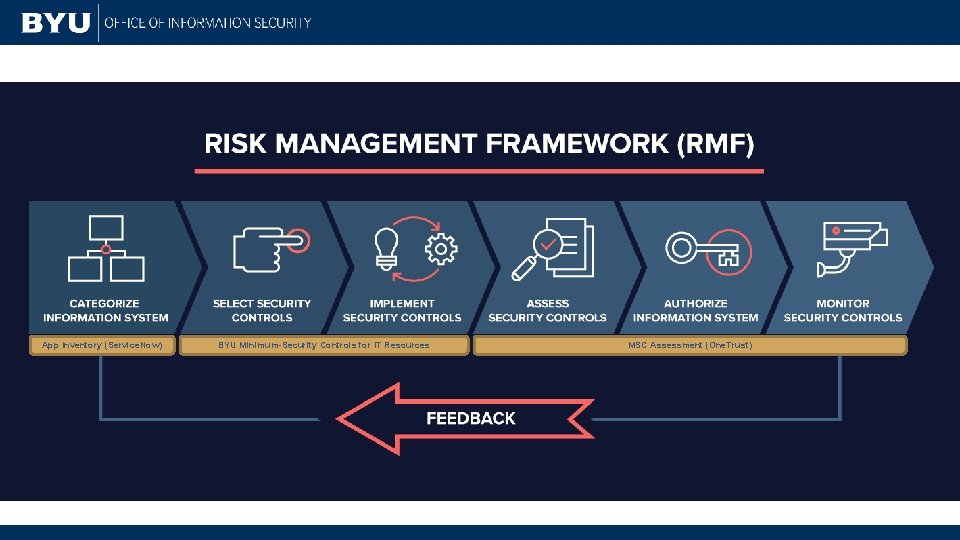
App Inventory (Service. Now) BYU Minimum-Security Controls for IT Resources MSC Assessment (One. Trust)

Information Security Risk Management Risk Assessments • Mitigate new and emerging risks • Risk severity and priority ratings • Security control implementation • Assist with inventory documentation • Validate completed self-assessments • Consult on mitigating risk Examples risk sources: Incidents response, audit findings, risk assessments, management identification, and control monitoring Examples assessment sources: data sharing agreements, control monitoring, new service offerings, department requests, and risk management reviews

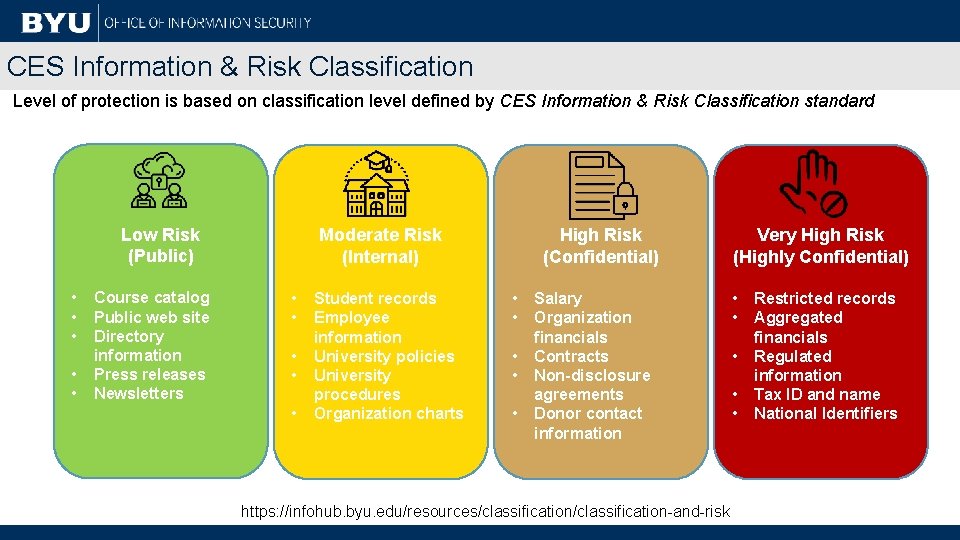
CES Information & Risk Classification Level of protection is based on classification level defined by CES Information & Risk Classification standard Low Risk (Public) • • • Course catalog Public web site Directory information Press releases Newsletters Moderate Risk (Internal) • • • Student records Employee information University policies University procedures Organization charts High Risk (Confidential) • • • Salary Organization financials Contracts Non-disclosure agreements Donor contact information https: //infohub. byu. edu/resources/classification-and-risk Very High Risk (Highly Confidential) • • • Restricted records Aggregated financials Regulated information Tax ID and name National Identifiers

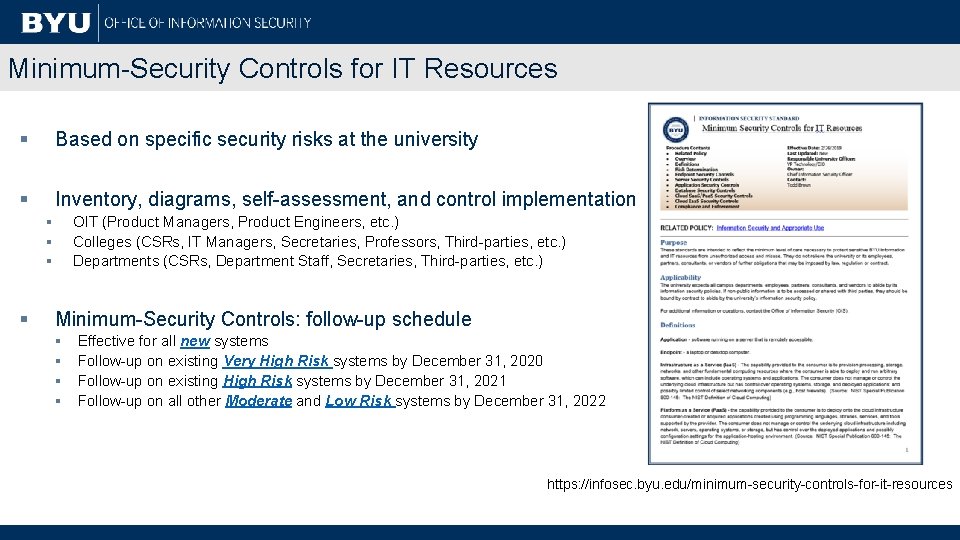
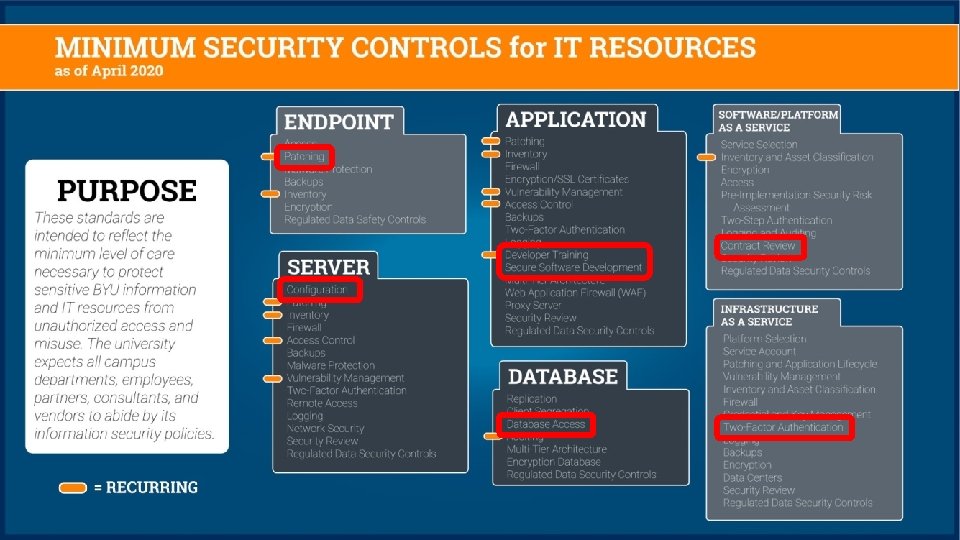
Minimum-Security Controls for IT Resources § Based on specific security risks at the university § Inventory, diagrams, self-assessment, and control implementation § § OIT (Product Managers, Product Engineers, etc. ) Colleges (CSRs, IT Managers, Secretaries, Professors, Third-parties, etc. ) Departments (CSRs, Department Staff, Secretaries, Third-parties, etc. ) Minimum-Security Controls: follow-up schedule § § Effective for all new systems Follow-up on existing Very High Risk systems by December 31, 2020 Follow-up on existing High Risk systems by December 31, 2021 Follow-up on all other Moderate and Low Risk systems by December 31, 2022 https: //infosec. byu. edu/minimum-security-controls-for-it-resources

8

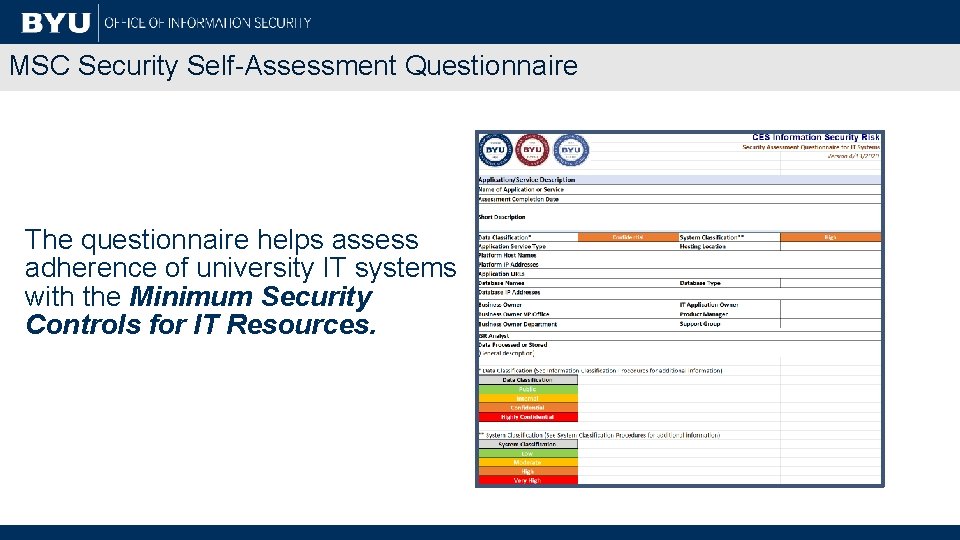
MSC Security Self-Assessment Questionnaire The questionnaire helps assess adherence of university IT systems with the Minimum Security Controls for IT Resources.

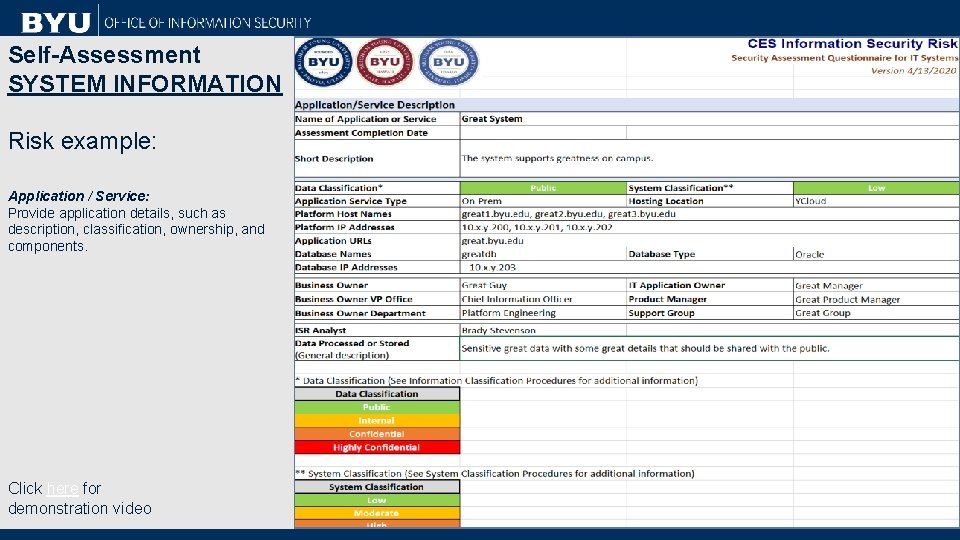
Self-Assessment SYSTEM INFORMATION Risk example: Application / Service: Provide application details, such as description, classification, ownership, and components. Click here for demonstration video

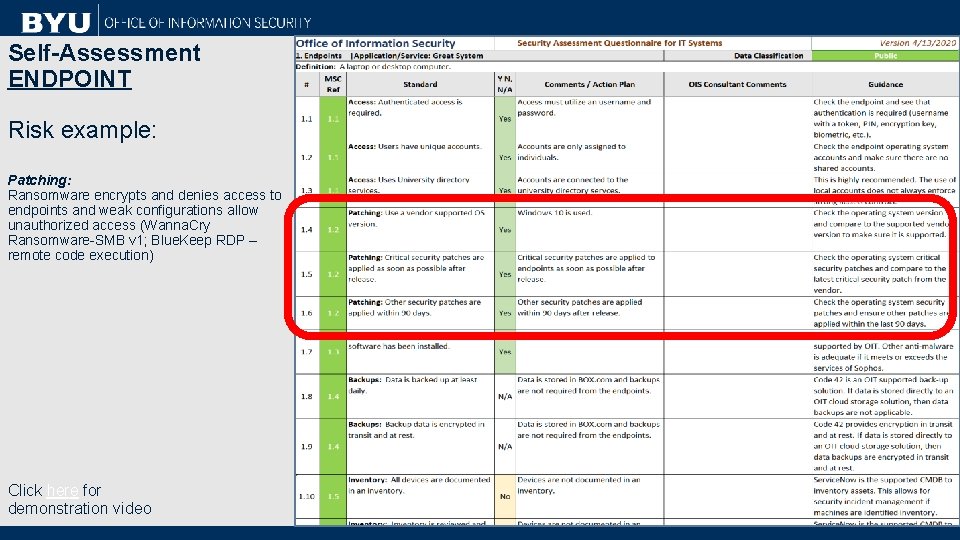
Self-Assessment ENDPOINT Risk example: Patching: Ransomware encrypts and denies access to endpoints and weak configurations allow unauthorized access (Wanna. Cry Ransomware-SMB v 1; Blue. Keep RDP – remote code execution) Click here for demonstration video

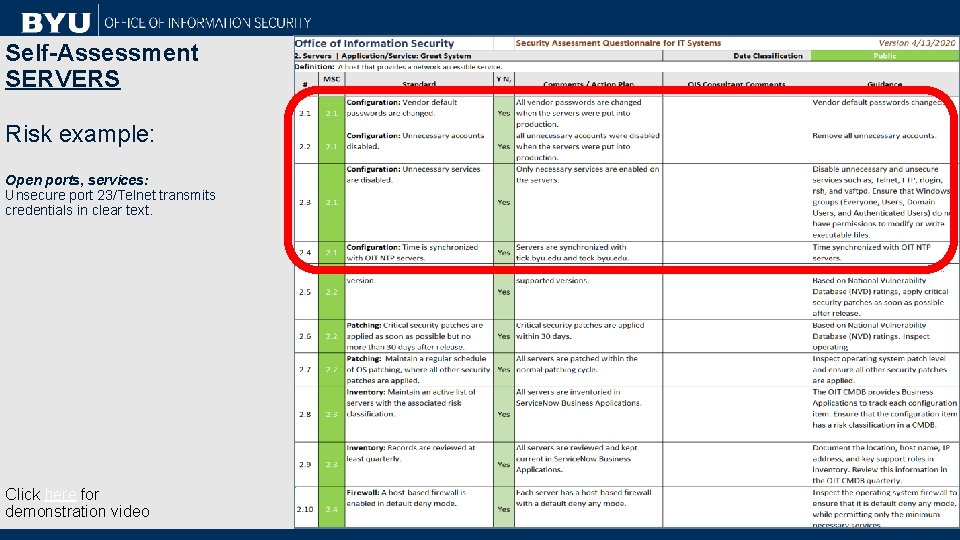
Self-Assessment SERVERS Risk example: Open ports, services: Unsecure port 23/Telnet transmits credentials in clear text. Click here for demonstration video

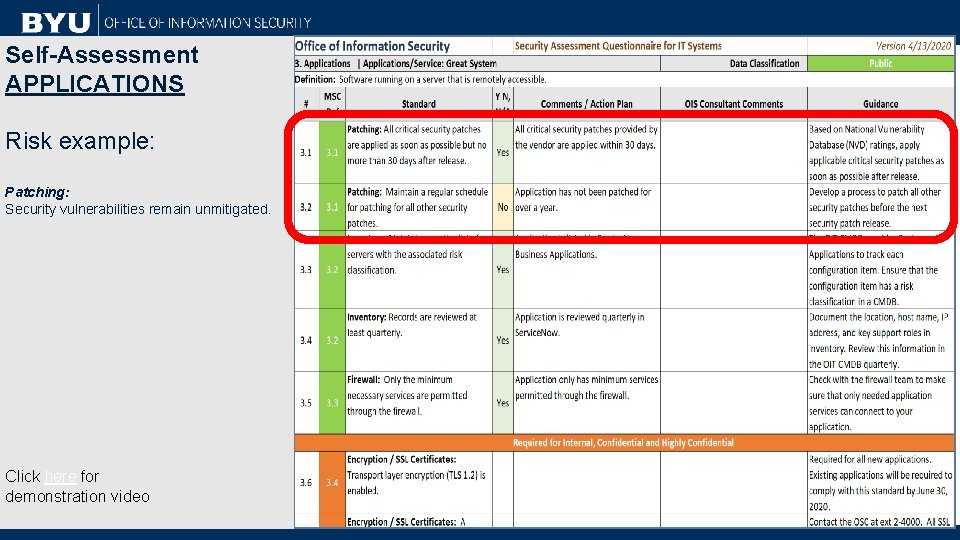
Self-Assessment APPLICATIONS Risk example: Patching: Security vulnerabilities remain unmitigated. Click here for demonstration video

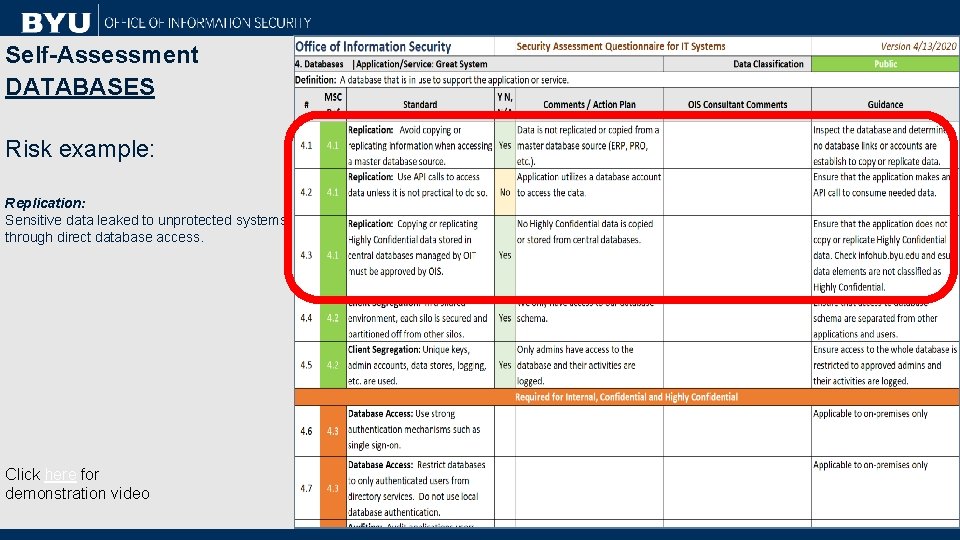
Self-Assessment DATABASES Risk example: Replication: Sensitive data leaked to unprotected systems through direct database access. Click here for demonstration video

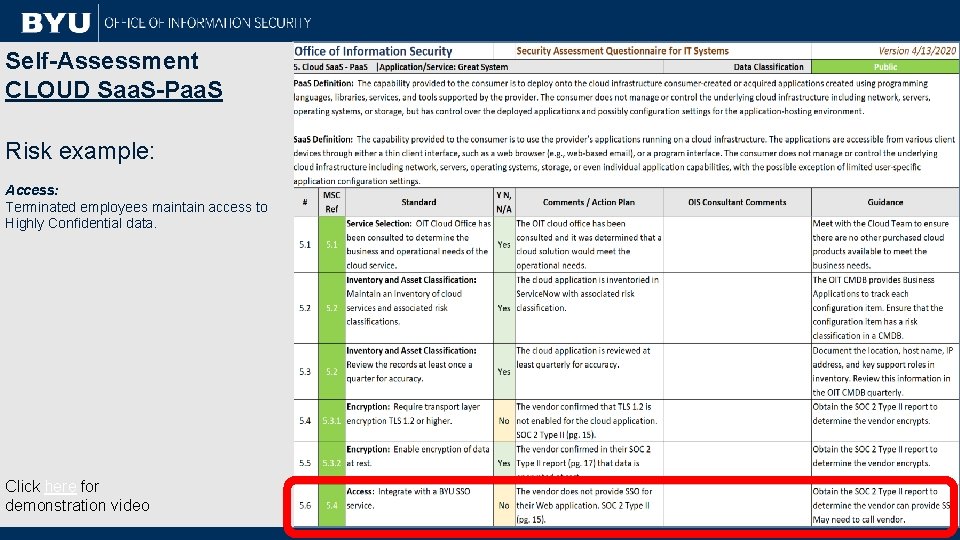
Self-Assessment CLOUD Saa. S-Paa. S Risk example: Access: Terminated employees maintain access to Highly Confidential data. Click here for demonstration video

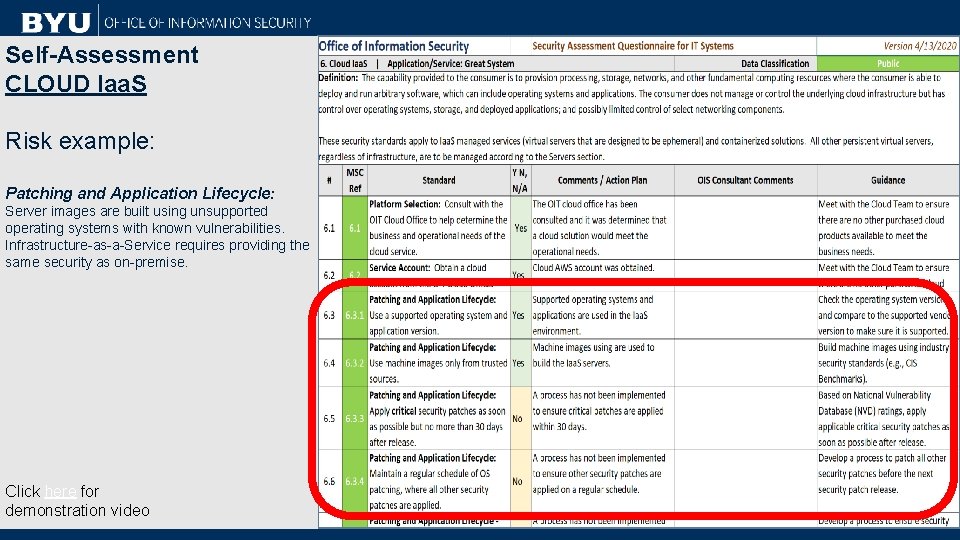
Self-Assessment CLOUD Iaa. S Risk example: Patching and Application Lifecycle: Server images are built using unsupported operating systems with known vulnerabilities. Infrastructure-as-a-Service requires providing the same security as on-premise. Click here for demonstration video

MSC Self Assessment Resources Minimum Security Controls (MSC): https: //infosec. byu. edu/mini mum-security-controls-for-it -resources MSC Self Assessment: https: //infosec. byu. edu/sec urity-standardsassessment-questionnaire MSC Self Assessment Videos: https: //infosec. byu. edu/stan dards-and-proceduressection

Contact Brady R. Stevenson Senior Manager, Information Security Risk CES SOC – Office of Information Security brady_stevenson@byu. edu Slack: @Brady. Stevenson 801 -422 -9906
 Web services security standards
Web services security standards Web services security standards
Web services security standards Dmtf cloud management standards
Dmtf cloud management standards Private secruity
Private secruity Cloud interoperability and standards
Cloud interoperability and standards Hard customer defined standards
Hard customer defined standards Aka.ms/geneva
Aka.ms/geneva Vodafone dedicated cloud
Vodafone dedicated cloud The cloud in cloud computing refers to
The cloud in cloud computing refers to Cloud integration patterns
Cloud integration patterns Public cloud vs private cloud cost analysis
Public cloud vs private cloud cost analysis Snapcloud
Snapcloud Code standards and practices 1 lesson 3
Code standards and practices 1 lesson 3 Measurement units standards and services department
Measurement units standards and services department Online brand monitoring services
Online brand monitoring services Security compliance monitoring
Security compliance monitoring Trafd
Trafd Knowledge management monitoring and evaluation
Knowledge management monitoring and evaluation Project management monitoring and controlling
Project management monitoring and controlling