Remote Login TELNET SSH Chapter 24 Remote Interactive







- Slides: 15

Remote Login (TELNET, SSH) Chapter 24

Remote Interactive Computing TCP can be used for interactive use of remote machines n n User establish remote login session Then executes commands Remote login may not be simple n Most systems designed to expect direct login May have to modify the machine’s OS n Building interactive client may be difficult, too Passing on Control-C commands

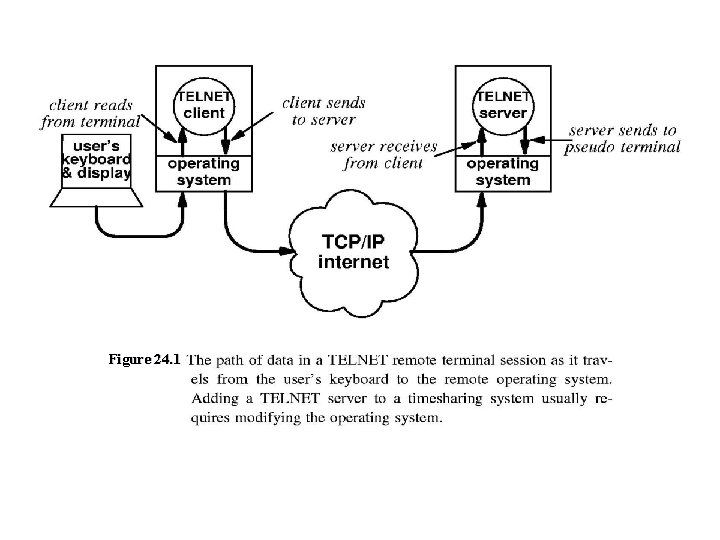
TELNET Protocol TCP/IP suite includes TELNET n n Simple remote terminal protocol Allows user to log into computer over internet Establishes TCP connection Passes keystrokes to remote machine Carries output back to user’s screen n Transparent Gives appearance that user keyboard and display is directly connected to the remote machine

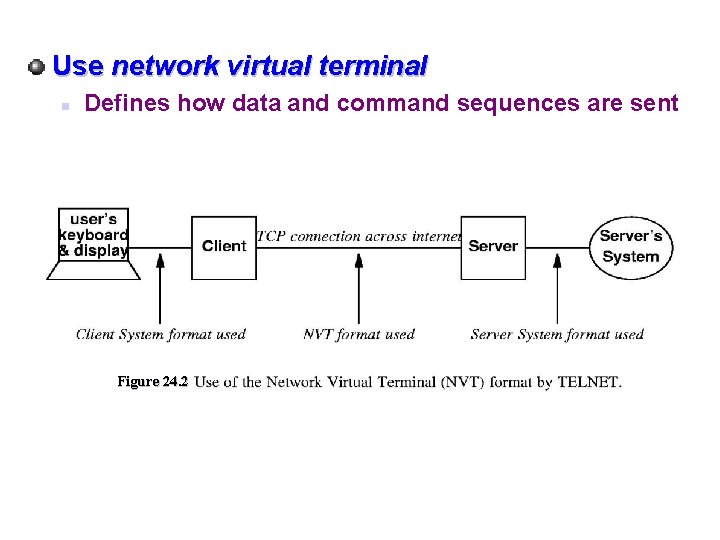
TELNET is not sophisticated as some n Is widely available ID remote machine by domain name or IP address Offers three basic services n Defines network virtual terminal Clients only have to build to the standard interface n n Allows negotiation of some standard options Treats both ends of connection symmetrically Does not force keyboard input or screen output

Figure 24. 1

Server is more complex than shown n n Must handle multiple, concurrent connections TELNET server consists of: Master server that listens for new requests Slave that handles one particular connection Pseudo terminal n n n OS entry point Allows application to transfer characters to OS as if they came from a keyboard Cannot build TELNET server without it

Adv of TELNET server as application pgm n Modification & control of server easier Since code is not part of OS Disadv n Inefficiency Each keystroke n n User keyboard OS Client program OS Across internet Then, Server’s OS Application Program Output comes back over same path Each keystroke requires several context switches n Expensive; practical due to slow typing speeds

Accommodating Heterogeneity Computers and OSs are different n Ending lines of text Some require termination by CR Others require LF Other require two characters: CR-LF n Key to interrupt running program Most interactive systems provide a way Specific keystroke is different (Control-C or ESC)

Use network virtual terminal n Defines how data and command sequences are sent Figure 24. 2

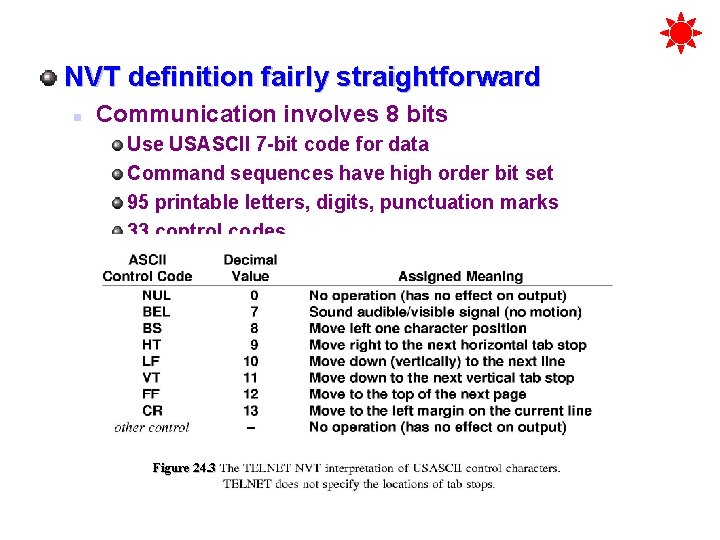
NVT definition fairly straightforward n Communication involves 8 bits Use USASCII 7 -bit code for data Command sequences have high order bit set 95 printable letters, digits, punctuation marks 33 control codes Figure 24. 3

Secure Shell (SSH) Popular alternative to TELNET n n Uses TCP to connect remotely, like TELNET Two significant enhancements over TELNET Provides secure communications Can perform additional, independent data transfers over same connection used for remote login n n Uses public key cryptography Really a general purpose secure connection Versus just a secure remote login service

Rlogin (BSD UNIX) BSD UNIX operating systems include remote login service called rlogin n n Not a general purpose protocol like TELNET Protocol understands computing environments Exports part of user’s environment to remote machine n Supports trusted hosts Administrator can choose set of machines over which login names & file access protections are shared

Virtual Network Computing (VNC) Provides remote desktop capability n n n See exact copy of desktop on another computer Use keyboard, mouse to interact with remote machine Runs across multiple platforms Linux, Windows, etc.

Remote Desktop Protocol (RDP) Defined by Microsoft for their OS n Similar to other remote desktop systems See exact copy of remote desktop Can be used across software platforms

Summary Application level protocols can be built on TCP/IP services & client-server model TELNET n n TCP/IP internet standard Widely available remote access system Secure Shell n n Authenticated, confidential remote login Multiple applications can share SSH connection Other remote access systems n rlogin, VNC, and RDP