CH 25 Remote Login TELNET Rlogin Xiaoying Cheng













- Slides: 17

CH 25 -Remote Login (TELNET, Rlogin) Xiaoying Cheng Yinghsuan Huang Chunli Yu Cheng Zhang Yi Zhang

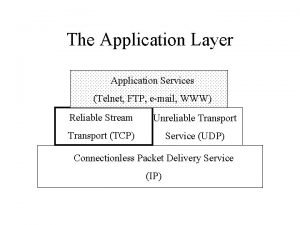
Introduction l Remote login: – Login to one host and then remote login across the network to any other host l Telnet: – A standard application. It works between hosts that use different operating systems.

TELNET Protocol Allow a user to log into a computer across an internet. l – – – l Establish a TCP connection. Pass keystrokes from the user’s keyboard directly to the remote computer. Carry output from the remote machine back to the user’s screen. Transparent: user’s keyboard and display attach directly to the remote machine.

TELNET Three Services 1 It defines a network virtual terminal that provides a standard interface to remote systems. 2 Telnet includes a mechanism that allows the client and server to negotiate options, and it provides a set of standard options. 3 Telnet treats both ends of the connection symmetrically. Thus , telnet allows an arbitrary program to become a client, either end can negotiate options.

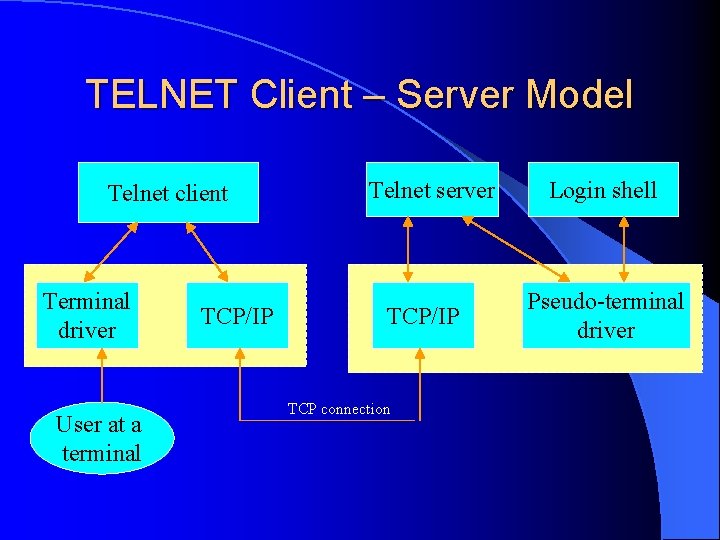
TELNET Client – Server Model Telnet client Terminal driver User at a terminal TCP/IP Telnet server TCP/IP TCP connection Login shell Pseudo-terminal driver

How application programs implement a TELNET client and server Client reads From terminal User’s keyboard & display Client sends To server TELNET client Operating system Server receives From client Server sends to pseudo terminal TCP/IP internet TELNET server Operating system

Pseudo terminal describe the OS entry point that allows a running program like the TELNET server to transfer characters to the operating system as if they came from a keyboard. l Each slave server connects a TCP stream from one client to a particular pseudo terminal. l

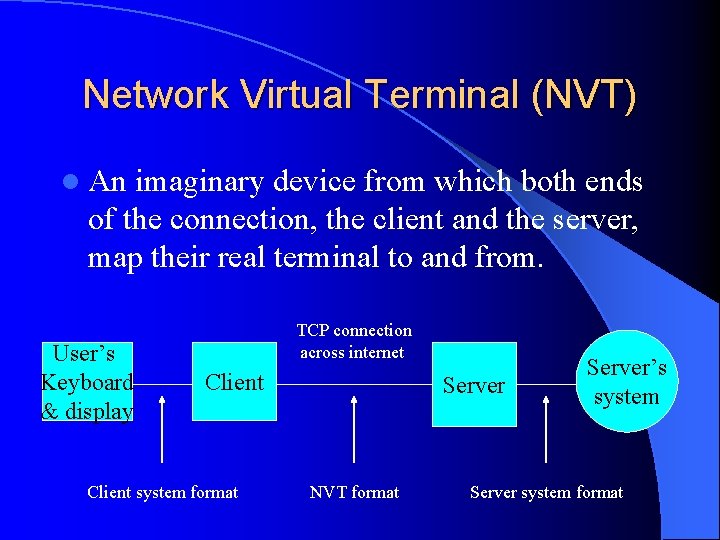
Network Virtual Terminal (NVT) l An imaginary device from which both ends of the connection, the client and the server, map their real terminal to and from. User’s Keyboard & display TCP connection across internet Client system format Server NVT format Server’s system Server system format

NVT Format l 7 – bit USASCII: – Each 7 – bit character is sent as an 8 -bit byte with the high-order bit set to 0. l An end-of-line is transmitted as 2 -character sequence CR followed by a LF. Such as rn l A carriage return is transmitted as 2 character sequence CR followed by a NUL (byte of 0). Such as r�

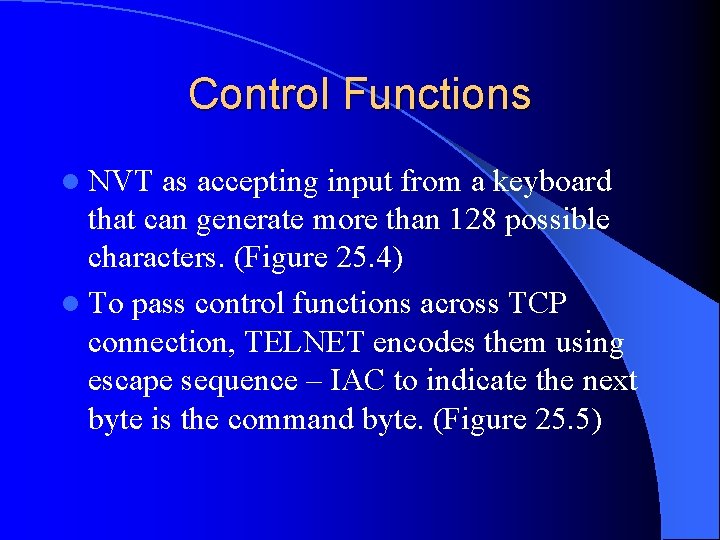
Control Functions l NVT as accepting input from a keyboard that can generate more than 128 possible characters. (Figure 25. 4) l To pass control functions across TCP connection, TELNET encodes them using escape sequence – IAC to indicate the next byte is the command byte. (Figure 25. 5)

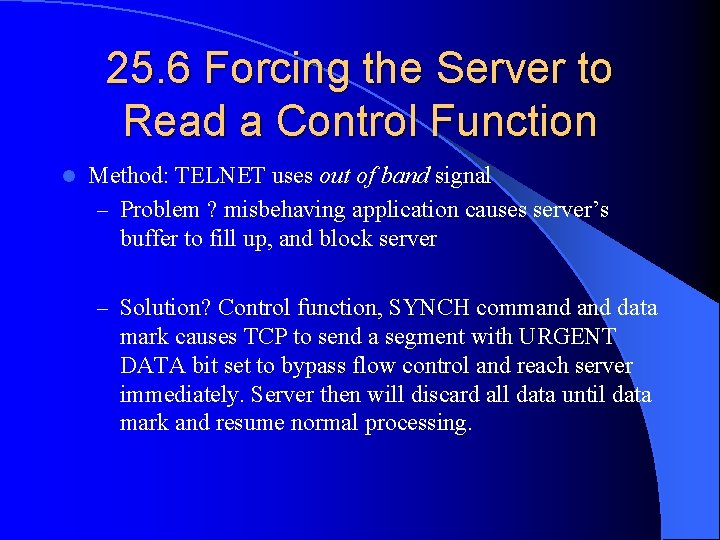
25. 6 Forcing the Server to Read a Control Function l Method: TELNET uses out of band signal – Problem ? misbehaving application causes server’s buffer to fill up, and block server – Solution? Control function, SYNCH command data mark causes TCP to send a segment with URGENT DATA bit set to bypass flow control and reach server immediately. Server then will discard all data until data mark and resume normal processing.

25. 7 TELNET options l In TELNET , options are negotiable, the client and server can reconfigure their connection. – i. e. 7 -bit or 8 -bit data l The range of TELNET options is wide: some extend the capabilities in major ways while others deal minor details. – P. 493, list of Telnet option.

25. 8 TELNET Option Negotiation l Symmetric: both of sides – Will X? Do/Don’t X. l Different version communication – If don’t understand request, decline!

25. 9 Rlogin (BSD UNIX) l Trusted Hosts – administrators may choose a set of “trusted” machines which are shared and establish equivalences among user logins. l One user, different login names in different machines without password. l rsh – One variant rlogin. rsh diamond ls

25. 9 Rlogin (BSD UNIX) cont. l Advantage – rlogin understand both local and remote computing environments, they communicate better than TELNET. l Unix stdin, stdout. l Re-direction l exports user’s environment to remote machine.

Demo l rlogin and rsh – Sun lab doesn’t fully support rsh. – Neither rlogin l Telnet: is not Telnet only – telnet different port/protocol – Knowledge of TCP/IP l Being a hacker?

 Telnet rlogin
Telnet rlogin Remote login telnet
Remote login telnet Remote login telnet
Remote login telnet Rlogin
Rlogin Rlogin ダウンロード 窓の杜
Rlogin ダウンロード 窓の杜 File transfer telnet
File transfer telnet Rfc 854
Rfc 854 Telnet protocol
Telnet protocol Telnet sql
Telnet sql Telnet application layer
Telnet application layer Protocolos telnet
Protocolos telnet Telnet gaia.cs.umass.edu 80
Telnet gaia.cs.umass.edu 80 Telnet imap
Telnet imap Telnet enumeration
Telnet enumeration Bbs server software
Bbs server software Telnet adalah
Telnet adalah Reverse telnet cisco aux to console
Reverse telnet cisco aux to console Telnet cis.poly.edu 80
Telnet cis.poly.edu 80