Network Applications Outline File Transfer Protocol Telnet Simple











- Slides: 22

Network Applications Outline File Transfer Protocol Telnet Simple Mail Transfer Protocol Peer-to-peer applications (Napster, Gnutella) CS 640 1

File Transfer Protocol • Most basic file transfer application in the Internet • • – One of the original client/server applications run on the ARPANET Runs on top of TCP Allows for both file transfer and interactive access Requires authentication via user name and password Requires that a host system run an FTP server – Listens for incoming requests on a well known port (21) – Anonymous/Guest logins are common • FTP is a two process model – Control process which communicates with peer control process • These processes communicate commands/responses as well as port information – Data transfer process which actually transfers requested file CS 640 2

File Transfer Protocol contd. • Client control process connects to server control process – ftp mirror 1. cs. wisc. edu • The client also starts a data transfer process which listens on a local port – Communicates this port number to server via control process • If client requests a file transfer, server initiates connection to client’s data transfer port – Server uses well known port for data transfer (20) • Commands used by FTP are actually a subset of TELNET protocol NVT ASCII CS 640 3

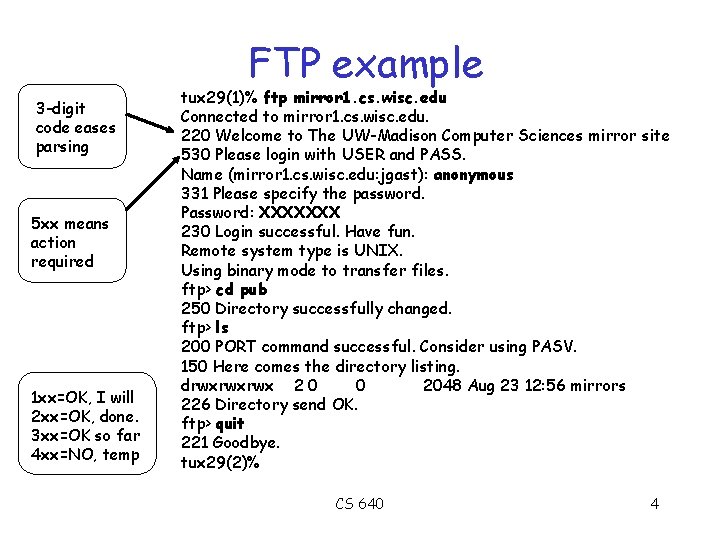
FTP example 3 -digit code eases parsing 5 xx means action required 1 xx=OK, I will 2 xx=OK, done. 3 xx=OK so far 4 xx=NO, temp tux 29(1)% ftp mirror 1. cs. wisc. edu Connected to mirror 1. cs. wisc. edu. 220 Welcome to The UW-Madison Computer Sciences mirror site 530 Please login with USER and PASS. Name (mirror 1. cs. wisc. edu: jgast): anonymous 331 Please specify the password. Password: XXXXXXX 230 Login successful. Have fun. Remote system type is UNIX. Using binary mode to transfer files. ftp> cd pub 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxrwxrwx 2 0 0 2048 Aug 23 12: 56 mirrors 226 Directory send OK. ftp> quit 221 Goodbye. tux 29(2)% CS 640 4

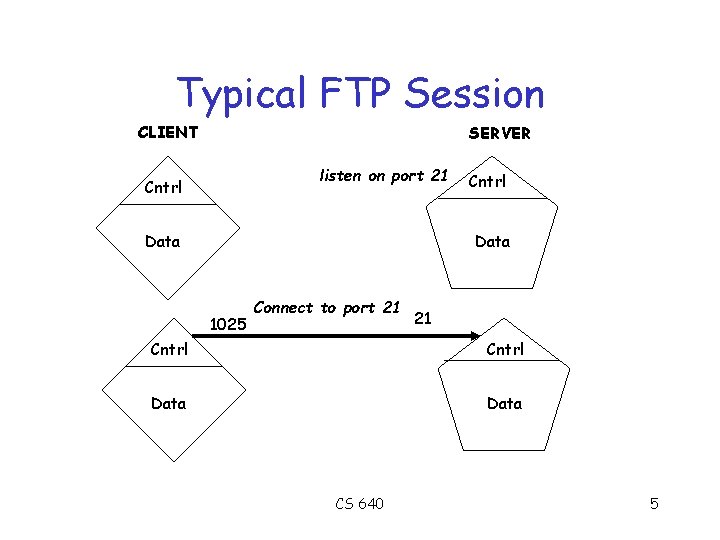
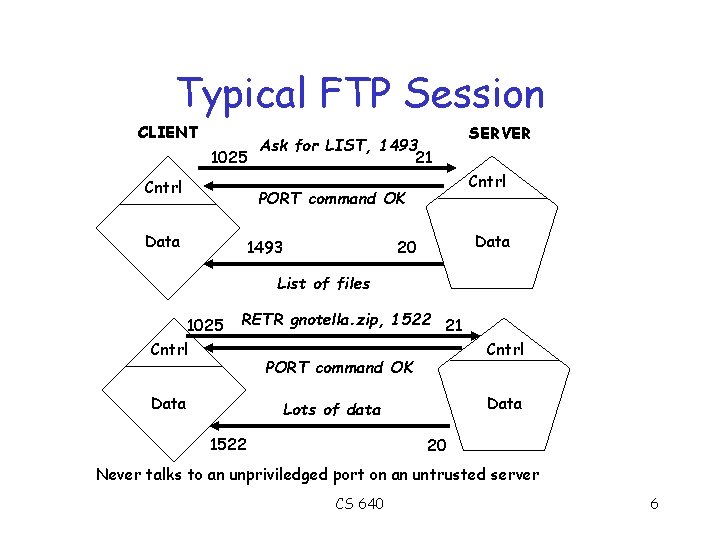
Typical FTP Session CLIENT SERVER listen on port 21 Cntrl Data 1025 Connect to port 21 21 Cntrl Data CS 640 5

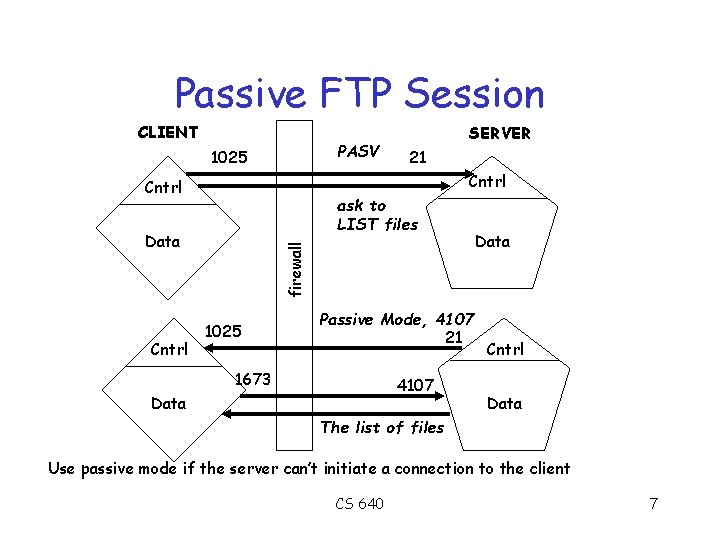
Typical FTP Session CLIENT Ask for LIST, 1493 1025 21 Cntrl PORT command OK Data 1493 SERVER Data 20 List of files 1025 Cntrl RETR gnotella. zip, 1522 21 Data Cntrl PORT command OK Data Lots of data 1522 20 Never talks to an unpriviledged port on an untrusted server CS 640 6

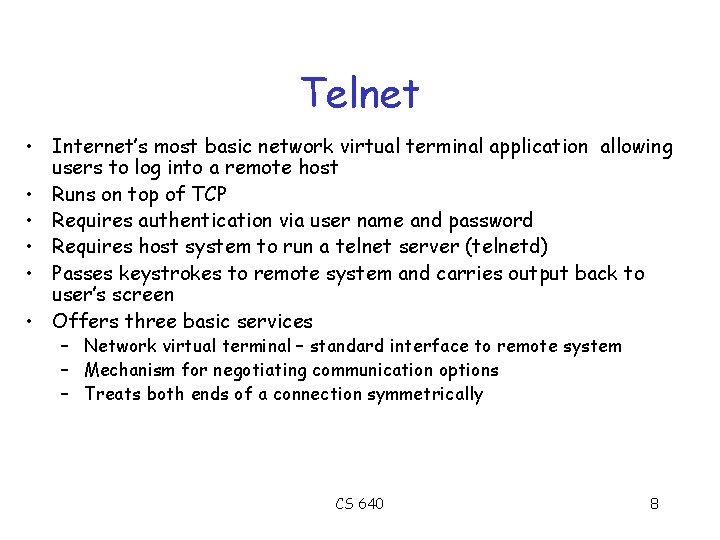
Passive FTP Session CLIENT PASV 1025 21 Cntrl ask to LIST files firewall Data Cntrl SERVER 1025 Passive Mode, 4107 21 1673 4107 Data Cntrl Data The list of files Use passive mode if the server can’t initiate a connection to the client CS 640 7

Telnet • Internet’s most basic network virtual terminal application allowing users to log into a remote host • Runs on top of TCP • Requires authentication via user name and password • Requires host system to run a telnet server (telnetd) • Passes keystrokes to remote system and carries output back to user’s screen • Offers three basic services – Network virtual terminal – standard interface to remote system – Mechanism for negotiating communication options – Treats both ends of a connection symmetrically CS 640 8

Telnet • Client’s TELNET process connects to server’s TELNET – telnet foo. cs. wisc. edu • Server listens on well known port (23) for incoming connections – forks new slave process to handle connection • Much of the hard work in telnet is to accommodate heterogeneity of systems – Control characters, etc. – Accomplished via network virtual terminal (NVT) specification for ASCII • It’s not very secure! • It can cause a lot of traffic - tinygrams – Nagle’s algorithm (RFC 896, ‘ 84) • Collects and sends groups of data based on ACK process CS 640 9

Simple Mail Transfer Protocol • Basic protocol for email exchange over the Internet • Runs on top of TCP • Fundamental difference between SMTP and FTP/TELNET is that it is NOT an interactive protocol – Messages are queued and spooled by SMTP agent • Users interact with email application – Lots! • Application interfaces with Message Transfer Agent – Sendmail on UNIX – Setup and configured by admins. • SMTP specifies how MTA’s pass email across the Internet – Also uses NVT commands CS 640 10

Simple Mail Transfer Protocol • Client uses email application to construct and send messages – Addresses consist of machine name and mailbox address • Mailbox is usually the same as one’s login but you can have aliases • Destination machine can also be an alias@cs. wisc. edu • Message is passed to mail spooler which is part of MTA – Application communicates with MTA via email transfer protocol • Post Office Protocol (POP 3) is common, but not very secure • Our department uses IMAP • MTA’s on remote systems listen for incoming mail on well known port (25) • Messages are delivered in two parts – header and body – Header format has exact specification = RFC 822 – Body content types are specified by MIME CS 640 11

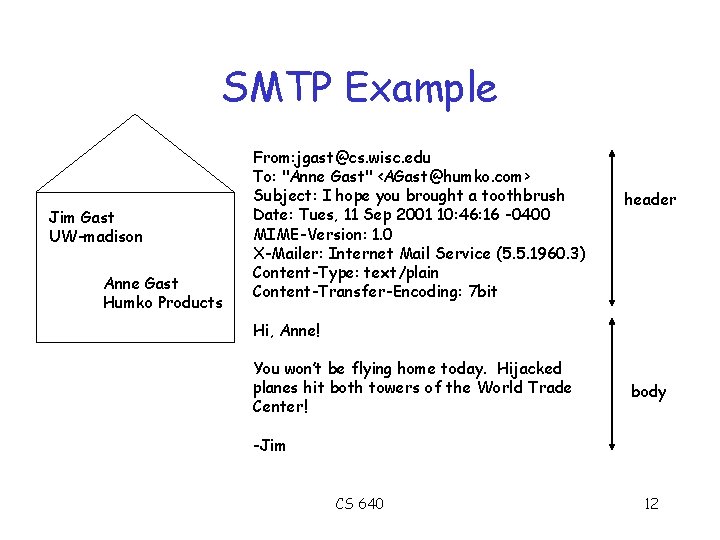
SMTP Example Jim Gast UW-madison Anne Gast Humko Products From: jgast@cs. wisc. edu To: "Anne Gast" <AGast@humko. com> Subject: I hope you brought a toothbrush Date: Tues, 11 Sep 2001 10: 46: 16 -0400 MIME-Version: 1. 0 X-Mailer: Internet Mail Service (5. 5. 1960. 3) Content-Type: text/plain Content-Transfer-Encoding: 7 bit header Hi, Anne! You won’t be flying home today. Hijacked planes hit both towers of the World Trade Center! body -Jim CS 640 12

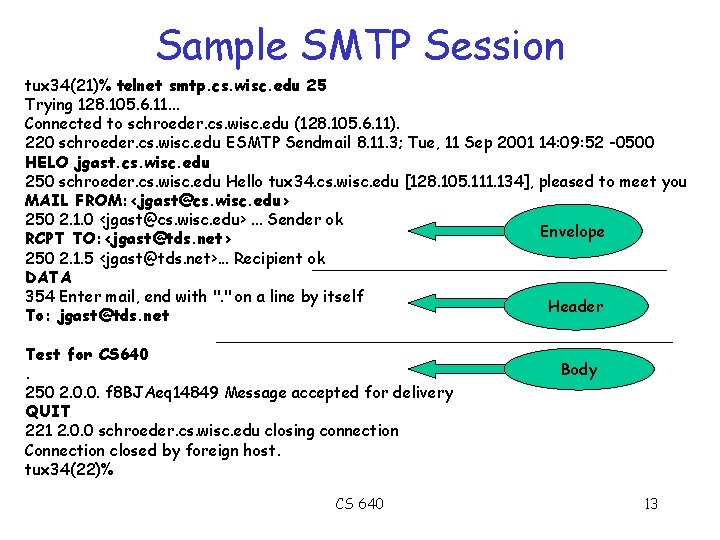
Sample SMTP Session tux 34(21)% telnet smtp. cs. wisc. edu 25 Trying 128. 105. 6. 11. . . Connected to schroeder. cs. wisc. edu (128. 105. 6. 11). 220 schroeder. cs. wisc. edu ESMTP Sendmail 8. 11. 3; Tue, 11 Sep 2001 14: 09: 52 -0500 HELO jgast. cs. wisc. edu 250 schroeder. cs. wisc. edu Hello tux 34. cs. wisc. edu [128. 105. 111. 134], pleased to meet you MAIL FROM: <jgast@cs. wisc. edu> 250 2. 1. 0 <jgast@cs. wisc. edu>. . . Sender ok Envelope RCPT TO: <jgast@tds. net> 250 2. 1. 5 <jgast@tds. net>. . . Recipient ok DATA 354 Enter mail, end with ". " on a line by itself Header To: jgast@tds. net Test for CS 640. 250 2. 0. 0. f 8 BJAeq 14849 Message accepted for delivery QUIT 221 2. 0. 0 schroeder. cs. wisc. edu closing connection Connection closed by foreign host. tux 34(22)% CS 640 Body 13

Peer to Peer Applications • Applications which facilitate the sharing of data between widely distributed users – Clearly the new “killer app” on the Internet – Napster model • One central source of meta data – Gnutella model • Distributed source of meta data • This is the way things will go… • Napster – Invented by Shawn Fanning at Northeastern U. in 1998 -9 – Founded as a company in May, 1999 – Indexes millions of songs on millions of systems world wide • Well known servers at Abovenet and globalcenter – Sued by Recording Industry Association of America in Dec. 1999 – Currently in limbo… CS 640 14

Napster Protocol • There are three basic entities in Napster – Client – browses, requests files – Server – end host system which shares/serves files – Metaserver/Redirector – file index repository • Protocol is “private” – has been reverse engineered • Messages are passed between entities – Form: <length><type><data> • Length and type are two bytes • Length specifies the number of bytes of data • Data is ASCII string often enclosed in quotes – There a large number of possible messages defined for the protocol • Information – errors, versions, status… • Control – login, upgrades, add/delete accounts… • Operation – search, listings, transfer requests, etc. CS 640 15

Napster Protocol contd. • “Official” software runs on Windows – Many other clients available eg. Gnapster – All you need to access Napster is a client • Runs on TCP – Servers (typically) use ports 7777, 8888 – Metaservers run on port 8875 • Protocol – Connect to a well known metaserver and login – Can join chat session or search for files (our focus) – Clients send “search query” request - results in locations of matching files – Downloading files happen directly between hosts • Metaserver is not involved CS 640 16

Napster Protocol contd. • File transfers use one of four modes – Up/download – Firewall up/download • Non-firewalled download – Client sends download (203) request to metaserver – Metaserver responds with download ack (204) that contains user, IP address, port … of requested file – Client makes TCP connection to server • Server responds with ASCII “ 1” immediately – Client sends GET in one packet then username, filename • Also include byte offset to resume interrupted transfer CS 640 17

Napster Protocol contd. • Remote client returns filesize followed by datastream • Client notifies metaserver transfer has begun (218) and ended (219) • Firewalled download – 204 ack from metaserver has port number 0 indicating server is behind a firewall – Client sends firewall download request (500) to metaserver requesting that server upload file to client • Client then waits for server to upload requested file – Metaserver then contacts server requesting upload to client • Done by HTTP tunneling: send message which looks like HTTP request – Upload continues just like download • Each upload is tracked CS 640 18

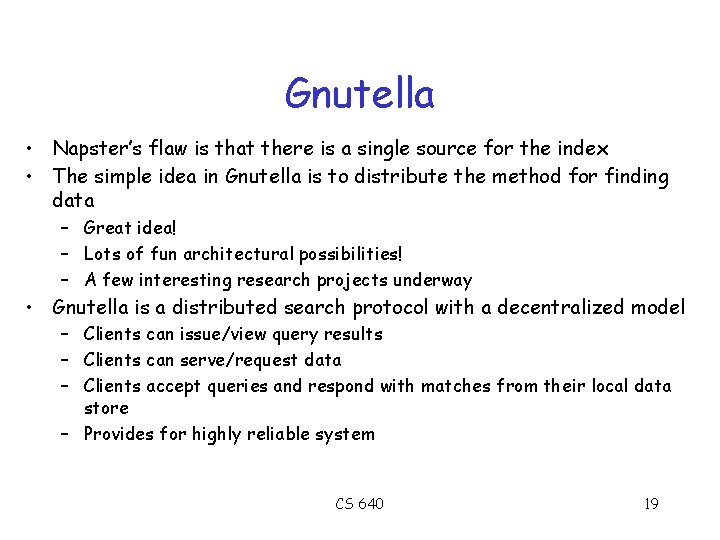
Gnutella • Napster’s flaw is that there is a single source for the index • The simple idea in Gnutella is to distribute the method for finding data – Great idea! – Lots of fun architectural possibilities! – A few interesting research projects underway • Gnutella is a distributed search protocol with a decentralized model – Clients can issue/view query results – Clients can serve/request data – Clients accept queries and respond with matches from their local data store – Provides for highly reliable system CS 640 19

Gnutella Protocol • Protocol defines method of client communication – Set of descriptors used for communicating data – Setof rules governing inter-client exchange of descriptors • Descriptors – – – Ping: active discovery of hosts on a network Pong: response to Ping includes client address and metadata Query: search mechanism Query. Hit: response to Query includes info necessary to get data Push: mechanism enabling firewalled clients to be part of network • A Gnutella client (servent) connects to network by establishing a connection with another client on the network – Finding another client is not part of Gnutella spec. • Host cache services are the typical way this is done CS 640 20

Gnutella Protocol • New client then creates connection to the Gnutella client and thereby becomes part of the network – Gnutella client can reject the connect request – Successful new client can then send/receive descriptors • Pings/pongs are then sent to establish network – No specification as to how much/often to probe – Network data can/is cached • Message routing should be well behaved – Ping/Query descriptors should be sent to all directly connected clients – Pong/Query. Hit descriptors should be sent back along same path – TTL is mechanism to limit distance • File downloads via HTTP/1. 0 protocol via direct connect CS 640 21

Other features • http: //www. Ka. Za. A. com – – “Distributed, self-organizing” Only supernodes are search hubs Intelligent download (Any of several identical items) Simultaneous download of chunks • http: //www. napigator. com – Finds and organizes open napster servers • http: //www. filetopia. org – Adds encryption • http: //www. audiogalaxy. com • http: //www. cubicmetercrystal. com/alpine CS 640 22