PTC India Foundation 23 rd Annual Conference Friday













- Slides: 23

PTC India Foundation 23 rd Annual Conference Friday, 24 th March 2017 ‘Security of Digital Payment and Trust Issues’ (Cyber Security threats and audit; Home-grown Cyber security Networks) M. K. Gupta, C-DOT

Agenda • • • Security Framework & building Trust Holistic View of Digital Infrastructure Security in Enterprise Network Cyber Security from a National perspective Questions & Discussions

Security Framework & building Trust

Cyber Attacks Custom Infection Vectors ØSpear-Phishing (A phishing Email having a malicious link or a weaponized payload attached) ØWatering hole attacks (Redirecting victim to a site hosting exploit code through a compromised Website) ØPoisoning Search Results (Using SEO, SEP, SEM techniques) ØPushing Malware through Networks (Embedding Malicious code in image, PDF or any other file) ØDrive-By-Download Attack (By clicking on a deceptive pop-up window/message Leading to Download and install an unknown or counterfeit code)

Security Framework for Digital Infrastructure 1. Holistic View of Digital Infrastructure 2. Dimensions to protect against major threats 3. Ensure that each dimension is applicable to complete landscape of Digital Infrastructure. 4. Build the security infrastructure for each dimension. 5. Monitoring & Follow up measures.

Remember that New age of attacks are Ø Organized, Ø Targeted, Ø Purposeful Ø Ever-changing & Ø Difficult to detect!!!

Motive can be Ø Ø Financial Frauds, Espionage, Political, Gaining control of Strategic operations

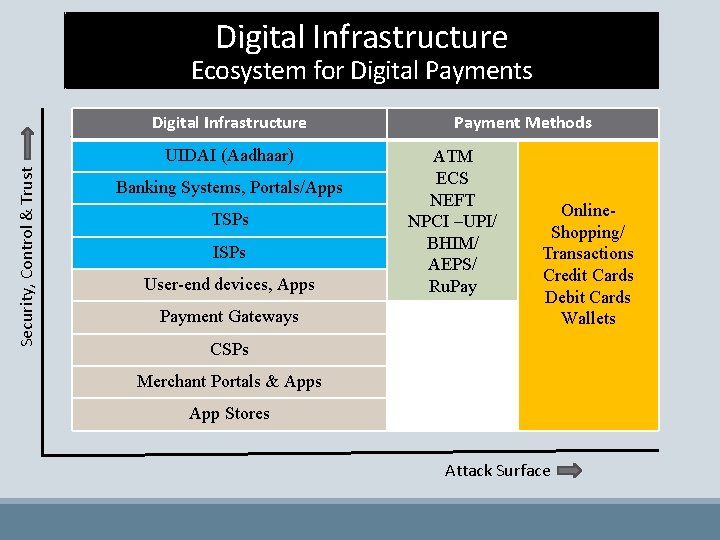
Digital Infrastructure Ecosystem for Digital Payments Digital Infrastructure Security, Control & Trust UIDAI (Aadhaar) Banking Systems, Portals/Apps TSPs ISPs User-end devices, Apps Payment Gateways Payment Methods ATM ECS NEFT NPCI –UPI/ BHIM/ AEPS/ Ru. Pay Online. Shopping/ Transactions Credit Cards Debit Cards Wallets CSPs Merchant Portals & Apps App Stores Attack Surface

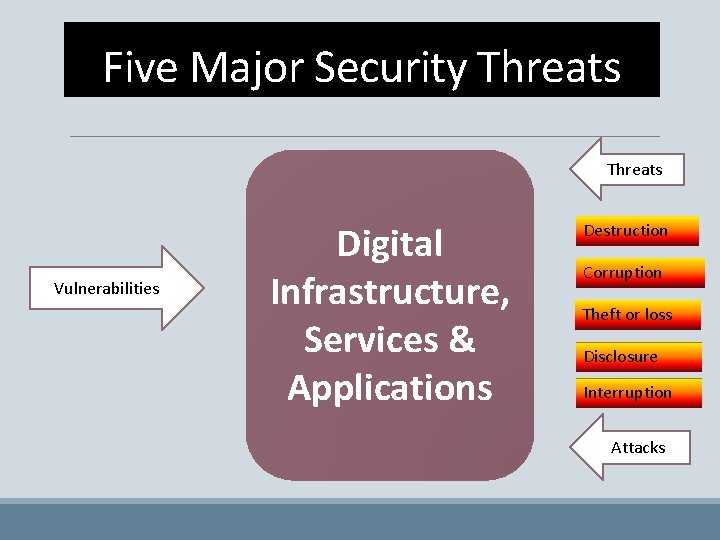
Five Major Security Threats Vulnerabilities Digital Infrastructure, Services & Applications Destruction Corruption Theft or loss Disclosure Interruption Attacks

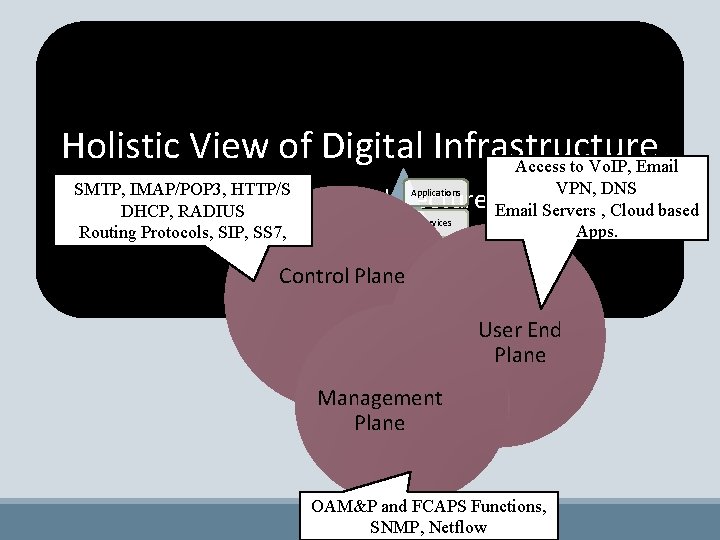
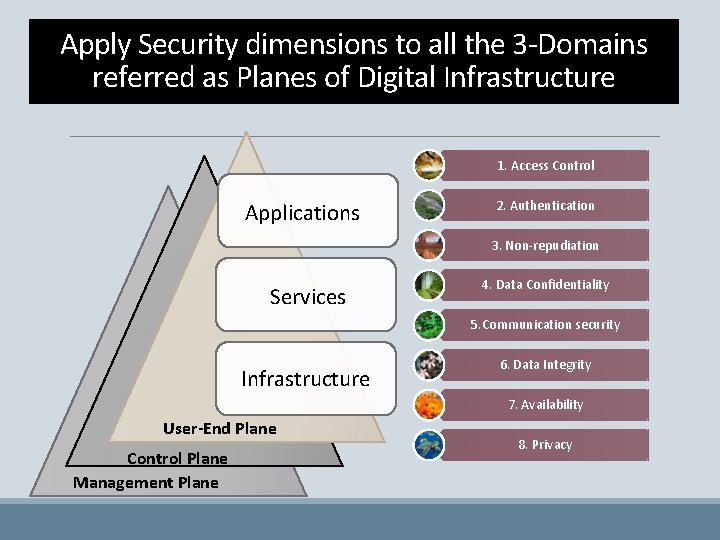
Holistic View of Digital Infrastructure Access to Vo. IP, Email SMTP, IMAP/POP 3, HTTP/S A 3 -Plane DHCP, RADIUS Routing Protocols, SIP, SS 7, Architecture Applications Services VPN, DNS Email Servers , Cloud based Apps. Infrastructure Control Plane User End Plane Management Plane OAM&P and FCAPS Functions, SNMP, Netflow

Eight Dimensions to build the trust & protect against major threats 1. Access Control 2. Authentication 3. Non-repudiation 4. Data Confidentiality 5. Communication security 6. Data Integrity 7. Availability 8. Privacy

Apply Security dimensions to all the 3 -Domains referred as Planes of Digital Infrastructure 1. Access Control Applications 2. Authentication 3. Non-repudiation Services 4. Data Confidentiality 5. Communication security Infrastructure 6. Data Integrity 7. Availability User-End Plane Control Plane Management Plane 8. Privacy

Challenges ahead § What about the security assurance of user end-points (Vulnerable or already compromised), connecting to digital Infrastructure for services & applications? § Credentials of hacked Email accounts, credit cards are already on sale. § Cost of security Infrastructure and issue of fast obsolescence, zeroday/unknown attacks? § Skilled resources for Monitoring and Analytics of huge data for quicker response? § Skilled resources for Mitigation (Network, applications, Data) – How, where, who? § At times the magnitude of certain attacks like DDOS are even beyond the control?

CYBER SECURITY NATIONAL PERSPECTIVE

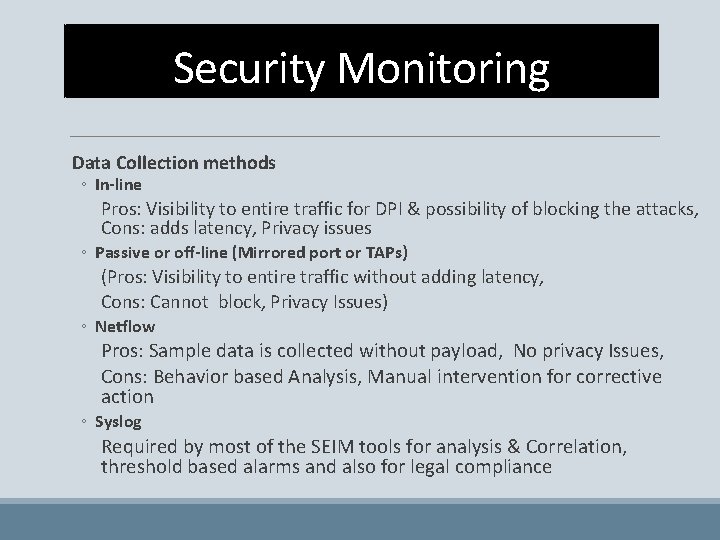
Security Monitoring Data Collection methods ◦ In-line Pros: Visibility to entire traffic for DPI & possibility of blocking the attacks, Cons: adds latency, Privacy issues ◦ Passive or off-line (Mirrored port or TAPs) (Pros: Visibility to entire traffic without adding latency, Cons: Cannot block, Privacy Issues) ◦ Netflow Pros: Sample data is collected without payload, No privacy Issues, Cons: Behavior based Analysis, Manual intervention for corrective action ◦ Syslog Required by most of the SEIM tools for analysis & Correlation, threshold based alarms and also for legal compliance

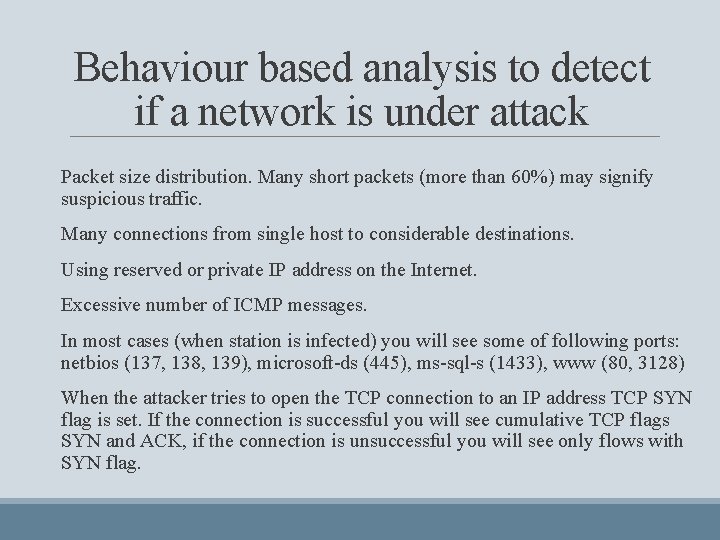
Behaviour based analysis to detect if a network is under attack Packet size distribution. Many short packets (more than 60%) may signify suspicious traffic. Many connections from single host to considerable destinations. Using reserved or private IP address on the Internet. Excessive number of ICMP messages. In most cases (when station is infected) you will see some of following ports: netbios (137, 138, 139), microsoft-ds (445), ms-sql-s (1433), www (80, 3128) When the attacker tries to open the TCP connection to an IP address TCP SYN flag is set. If the connection is successful you will see cumulative TCP flags SYN and ACK, if the connection is unsuccessful you will see only flows with SYN flag.

Solution Infrastructure There are basically two types of sensor solutions Signature based sensors (IDS/IPS systems) ◦ Conduct real-time full packet inspection and threat-based decision-making on network traffic. ◦ More suitable at edge of critical organizations/ departments. ◦ Can block the attacks and malicious traffic in real-time. Netflow based analyzers ◦ ◦ Standard based flows generated and exported by routers Analysis of behavior of traffic for generating alerts and decision making only. Low cost infrastructure More suitable for top level monitoring of large volume of traffic at international gateways.

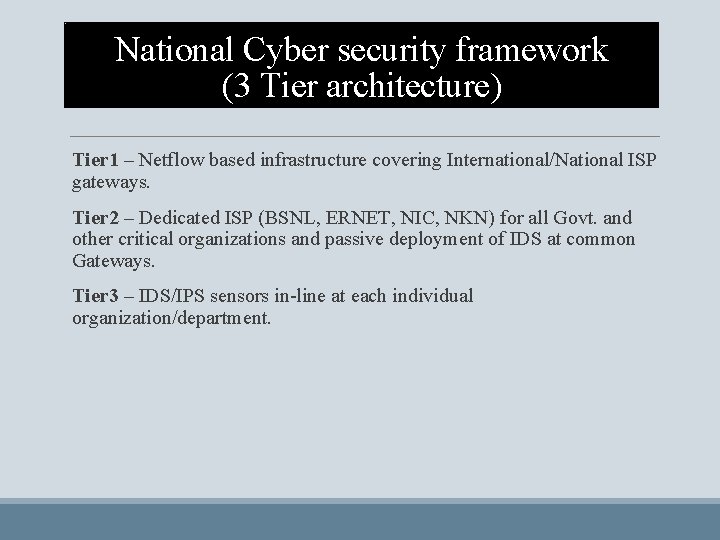
National Cyber security framework (3 Tier architecture) Tier 1 – Netflow based infrastructure covering International/National ISP gateways. Tier 2 – Dedicated ISP (BSNL, ERNET, NIC, NKN) for all Govt. and other critical organizations and passive deployment of IDS at common Gateways. Tier 3 – IDS/IPS sensors in-line at each individual organization/department.

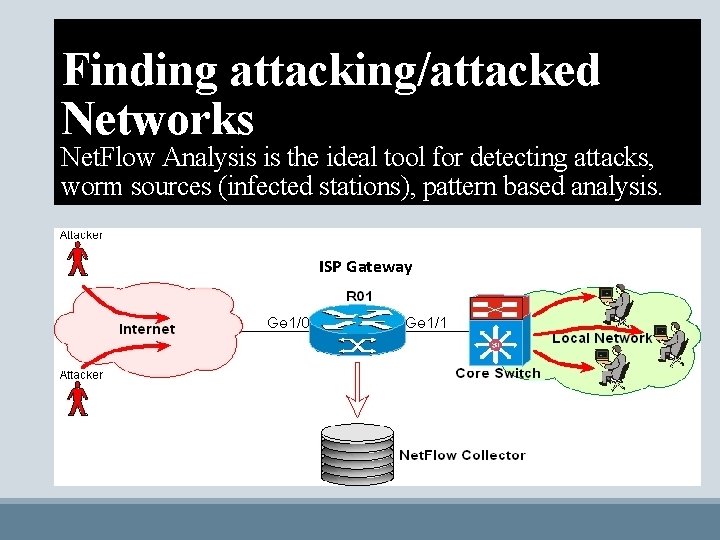
Finding attacking/attacked Networks Net. Flow Analysis is the ideal tool for detecting attacks, worm sources (infected stations), pattern based analysis. ISP Gateway

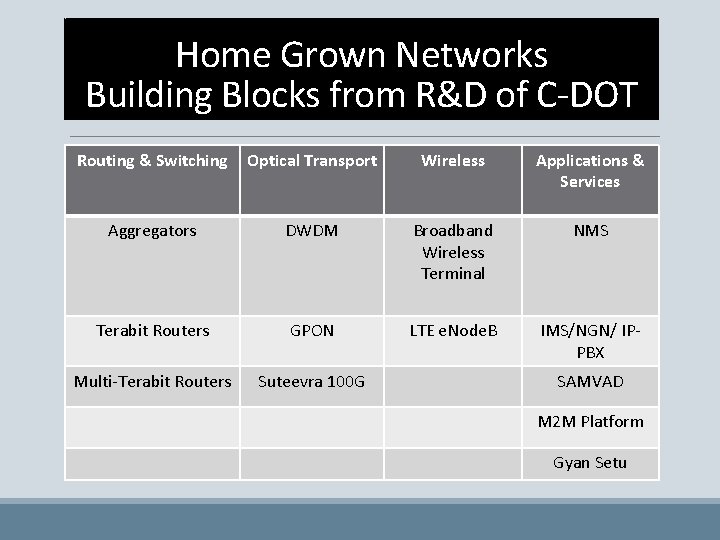
Home Grown Networks Building Blocks from R&D of C-DOT Routing & Switching Optical Transport Wireless Applications & Services Aggregators DWDM Broadband Wireless Terminal NMS Terabit Routers GPON LTE e. Node. B IMS/NGN/ IPPBX Multi-Terabit Routers Suteevra 100 G SAMVAD M 2 M Platform Gyan Setu



Thank you M. K. Gupta, Group Leader (Networks & Security) Centre For Development of Telematics Mandi Road, Chattarpur, Mehrauli New Delhi - 110030
 Ptc india office
Ptc india office Hepi conference
Hepi conference Pbfeam
Pbfeam Afp annual conference 2020
Afp annual conference 2020 Iowa league of cities annual conference
Iowa league of cities annual conference Nmls annual conference 2019
Nmls annual conference 2019 Travel health insurance association annual conference
Travel health insurance association annual conference Organization development network annual conference
Organization development network annual conference Stfm conference
Stfm conference Gie annual conference
Gie annual conference Gcyf 2011 annual conference
Gcyf 2011 annual conference Problemitize
Problemitize Stfm conference
Stfm conference Fuze conference 2018
Fuze conference 2018 Njdv
Njdv Composition of urine slideshare
Composition of urine slideshare Pad foundation section
Pad foundation section Agencies related to welfare services to the children
Agencies related to welfare services to the children India trade & export finance conference
India trade & export finance conference India trade & export finance conference
India trade & export finance conference Asme ptc 4
Asme ptc 4 Ascending pyelography
Ascending pyelography Ptc wizard windham nh
Ptc wizard windham nh Ptc university
Ptc university