PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 Office of




















- Slides: 22

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 Office of Management Privacy, Information and Records Management Services Privacy Safeguards Division previou s next

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Instructions § This training is intended for U. S. Department of Education contractors. If you are an employee, you must take the Mandatory Privacy Training through the Talent Management System (TMS). The link to TMS is on the home page of connect. ED. gov § After you have reviewed the training slides, read and print the certificate found on the last page. Sign and date the certificate, then give it to your immediate supervisor and keep a copy for your own records. 2

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next WELCOME Annual privacy awareness training emphasizes the importance of privacy safeguards at ED, explains privacy protection requirements, and details your responsibilities for protecting privacy information, regardless of format. Upon completion of this training you should be able to: § define privacy protection terms; § protect the personal privacy rights of individuals whose personal information ED maintains, including your own; § identify potential threats to privacy protected data; and § identify and report suspected or actual loss of privacy data. ED’s Privacy Safeguards Program is carried out by the Privacy Safeguards Division of the Office of Management’s (OM) Privacy, Information and Records Management Services (PIRMS). 3

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Who Must Take This Training? As part of ED’s orientation process, all new employees, including career, contractors, non career, interns, stay-in-school and detailees, must complete this training within 30 days of reporting to duty at ED and annually thereafter. 4

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Why You Need This Training This training will help you to: 1. Protect the personal privacy rights of individuals whose personal information ED maintains, including your own. 2. Comply with laws, regulations, and policies that protect privacy data. 3. Understand your privacy responsibilities before being permitted access to agency information and information systems. 4. Understand your personal responsibility for protecting against the unauthorized disclosure of privacy protected information and preventing privacy breaches. 5. Maintain the public’s trust. 5

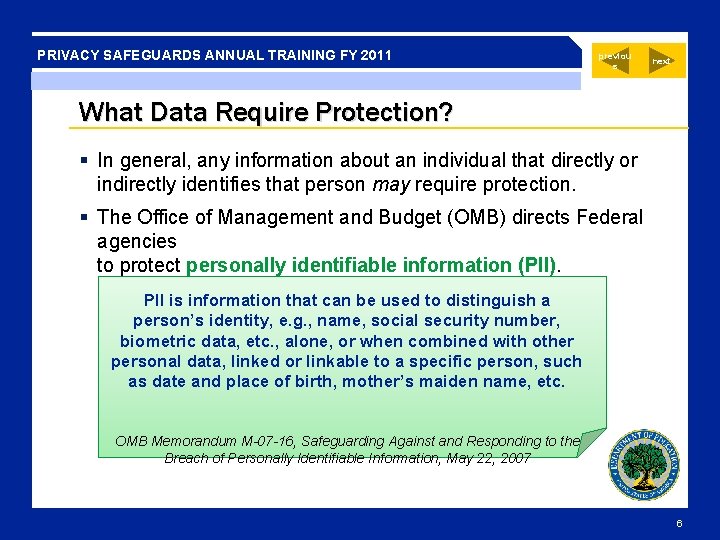
PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next What Data Require Protection? § In general, any information about an individual that directly or indirectly identifies that person may require protection. § The Office of Management and Budget (OMB) directs Federal agencies to protect personally identifiable information (PII). PII is information that can be used to distinguish a person’s identity, e. g. , name, social security number, biometric data, etc. , alone, or when combined with other personal data, linked or linkable to a specific person, such as date and place of birth, mother’s maiden name, etc. OMB Memorandum M-07 -16, Safeguarding Against and Responding to the Breach of Personally Identifiable Information, May 22, 2007 6

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Sensitive PII (SPII) § Some PII is always sensitive and requires a high level of protection because of the substantial harm to an individual that could occur if it were wrongfully disclosed. § The level of protection should reflect the sensitivity of the data – data that is determined by the owner to be of high value or that represents a high risk to the individual if it were wrongfully disclosed requires increased protection. 7

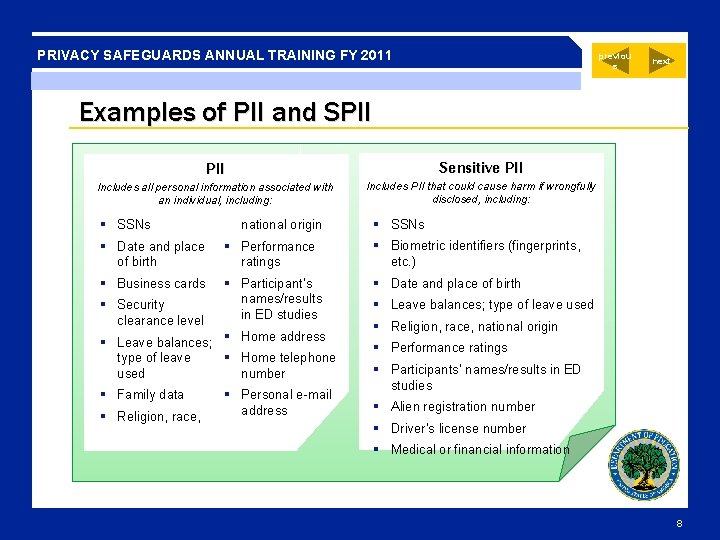
PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Examples of PII and SPII Sensitive PII Includes all personal information associated with an individual, including: Includes PII that could cause harm if wrongfully disclosed, including: § SSNs national origin § SSNs § Date and place of birth § Performance ratings § Biometric identifiers (fingerprints, etc. ) § Business cards § Participant’s names/results in ED studies § Date and place of birth § Security clearance level § Leave balances; § Home address § Home telephone type of leave number used § Family data § Religion, race, § Personal e-mail address § Leave balances; type of leave used § Religion, race, national origin § Performance ratings § Participants’ names/results in ED studies § Alien registration number § Driver’s license number § Medical or financial information 8

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next What Is The Privacy Act? § The Privacy Act (the Act) regulates how Federal agencies collect, maintain, use, and disclose an individual’s information. § The Act protects “records”, i. e. , any information about a person, such as education, financial, medical, criminal or work history, that contains one’s name or other personal identifier. The Act – Ø requires Federal agencies to publish system of records notices (SORNs) so that the public is aware of what personal information is being maintained and how it will be used; Ø requires that records about individuals are accurate, relevant, timely, and complete; and Ø generally allows individuals to access and request corrections to records maintained on them. The Privacy Act of 1974, as amended. 5 U. S. C. § 552 a. 9

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Privacy Act Systems of Records § A system of records is a group of records that an agency maintains that: Ø contains a personal identifier, such as a name, Social Security Number (SSN), etc. , about a specific person; Ø contains one other item of personal data (such as home address, performance rating, blood type, etc. ); and Ø is retrieved by a personal identifier. § If you are the project lead or system owner, you must prepare a System of Records Notice (SORN) that will be published in the Federal Register. § If you think this applies to your project, contact the Privacy Safeguards Division for assistance as soon as possible. The SORN process can take as long as 6 -9 months. 10

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Consequences for Violating The Privacy Act Criminal penalties may result in misdemeanor criminal charges and fines of up to $5, 000 for each offense per violation for: § knowingly and willfully disclosing Privacy Act data to any person(s) not entitled to access it; § knowingly and willfully requesting or obtaining records under false pretenses; and § willfully maintaining a system of records without meeting the Act’s public notice requirements. NOTE: The Privacy Act authorizes criminal remedies against Federal employees and contractors. 11

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Consequences for Violating The Privacy Act (cont. ) Civil remedies may result in payments of actual damages and payments of reasonable attorney’s fees when an agency fails to: § comply with any provision of the Act, or agency rule, that results in an adverse effect on an individual, including – Ø refusing to amend an individual’s record in a system of records in accordance with the individual’s request; Ø refusing to comply with a person’s request for access to the information pertaining to them in a system of records; and Ø failing to maintain accurate, relevant, timely and NOTE: The Privacy Act only authorizes civil remedies against Federal agencies, not Federal employees. complete systems of records.

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Determining Privacy Risks § The initial review of the privacy risks of ED Information Technology (IT) systems and data collections is conducted at the beginning of the system lifecycle. This review is a Privacy Threshold Analysis (PTA). § The PTA process helps determine what privacy documentation is required and what privacy issues should be addressed when a system is being developed or modified. § System owners and/or project managers complete the brief PTA form by providing basic information about the system in order to determine if additional documentation is required. 13

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Determining Privacy Risks § The E-Government Act of 2002, requires Federal agencies to conduct Privacy Impact Assessments (PIAs) for IT systems that contain information in identifiable form in order to identify and address privacy risks. § A completed PIA details how the information is collected, stored, protected, shared and managed electronically by a Federal agency. A PIA must be conducted: Ø before developing or procuring IT systems that collect or maintain PII about the public; or Ø when initiating a new electronic collection of information in identifiable form for 10 or more people. § A PIA must be updated when changes to the system, collection, or process create new or altered privacy risks. § PIAs must be made available at www. ed. gov. 14

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Special Consideration For SSNs Collect only as a last resort! § SSNs may not be collected or used unless: Ø authorized by law, regulation, or presidential order, and/or necessary for a documented agency purpose; Ø there is approved documentation that no reasonable alternative exists; or Ø these requirements must be met before developing or modifying a system, or implementing a program that collects, uses, maintains, or discloses SSNs. 15

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next Safeguarding PII Minimize PII § Collect only PII that you are authorized to collect, and at the minimum level necessary to accomplish a required purpose. Safeguard the transfer of PII § Do not e-mail PII unless it is encrypted or in a § Limit number of copies containing PII to the minimum needed. § Alert FAX recipients of incoming transmission. Secure PII § When not in use, store PII in an appropriate § Use services that provide tracking and confirmation of delivery when mailing or shipping PII offsite. access-controlled environment. § Use fictional personal data for presentations or training. § Review documents for PII prior to posting on ED web pages. § Safeguard PII in any format around your work area. password protected attachment. Dispose of PII Properly § Delete/dispose of PII at the end of its retention period or transfer it to the custody of the National Archives, as specified by its applicable records retention schedule. § Disclose PII only to those authorized to see it. 16

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next What Is A Privacy Breach? A privacy breach occurs when PII is lost or stolen, or is disclosed or otherwise exposed to unauthorized people and/or for unauthorized purposes. § This includes PII in any format, and whether or not it is a suspected or confirmed loss. § Examples of PII breaches: Ø Ø Ø PII left on the printer or scanner; PII e-mailed without encryption or other protection; PII mailed to the wrong recipient; PII stored on a stolen laptop or thumb drive; and PII posted to a public-facing website, etc.

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next If You Suspect a Privacy Breach § If you lose or suspect a loss of PII, it is your responsibility to notify your immediate supervisor and your computer security officer (CSO) or Information Systems Security Manager (ISSM) at once. § Be ready to provide the facts of the incident, including the number of records exposed, the type of PII lost (name, SSN, addresses), if the data is still at risk, etc. § Immediate action is important because agencies must report a breach involving PII within one hour of discovering the breach or potential breach. § Once your report is made, ED will determine appropriate next steps.

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s next There are Risks if PII is Lost or Stolen Risks to the Victim § Identity theft, including financial loss and impact on job, credit, and reputation; § Embarrassment; § Emotional distress; and § Loss of confidence in the government. Risks to the ED Employee § Disciplinary action, loss of clearance, employment, or access to PII; § Penalties under the Privacy Act; and § Diminished reputation. Risks to ED § § Diminished reputation; Costs of mitigation; Litigation and associated costs; Impact on agency processes; and § Loss of the public trust.

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s ED Penalties for Unauthorized Disclosure of PII ED employees may be subject to disciplinary action for failure to safeguard PII, including: § reprimand; § suspension; § demotion; or § removal from employment. Personnel Manual Instruction 751 -1 (Appendix A) next

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 previou s Questions about Safeguarding PII? § Consult your Supervisor § Contact your Principal Office Computer Security Officer or Information System Security Manager § Contact ED’s Privacy Safeguards Program: § Privacy Service Line at 202 -401 -1269, or § E-mail: privacysafeguards@ed. gov § Visit ED’s Privacy Safeguards Division webpage on connect. ED. gov: http: //connected. gov/index. cfm? office=om&cid=be 9 ae 700 -b 2 b 4 -e 2 e 1 -fcbeb 2 d 9 beb 90 b 93 next

PRIVACY SAFEGUARDS ANNUAL TRAINING FY 2011 Certificate of Completion I have completed the Privacy Safeguards Annual Training for ED Employees and Contractors, FY 2011. I am aware of my responsibilities to safeguard privacy information and that there may be consequences for not doing so. PRINT NAME SIGNATURE DATE
 Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Gcyf 2011 annual conference
Gcyf 2011 annual conference General aseptic fields are managed critically
General aseptic fields are managed critically Liberty protection safeguards flowchart
Liberty protection safeguards flowchart Legal safeguards for nurses
Legal safeguards for nurses Objectivity safeguards in research process
Objectivity safeguards in research process Due process safeguards
Due process safeguards Army privacy office
Army privacy office Microsoft office privacy settings popup
Microsoft office privacy settings popup Vanderbilt privacy office
Vanderbilt privacy office Ibp training
Ibp training Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Personal information lifecycle
Personal information lifecycle Information security program refresher training
Information security program refresher training Difference between office location and office layout
Difference between office location and office layout Ms office 2007 training
Ms office 2007 training Privacy loss budget
Privacy loss budget What are the 13 australian privacy principles?
What are the 13 australian privacy principles? Cynthia dwork differential privacy
Cynthia dwork differential privacy The complexity of differential privacy
The complexity of differential privacy Care certificate 7
Care certificate 7 Contingent contract in business law
Contingent contract in business law Mail
Mail