HIPAA Training Privacy Protection for Patients Privacy Training






































- Slides: 40

HIPAA Training: Privacy Protection for Patients Privacy Training for TUSM students and Visiting Students Overview by Steve Pauker, M. D. Sara Murray Jordan Professor of Medicine

Goals for this Program • Understand basic principles of the new Privacy Rule • Understand your role in protecting patient information • Know where to go for help if you have a question or have incidentally violated rules

What is the HIPPA/ Privacy Compliance Law? • HIPPA: stands for Health Insurance Portability and Accountability Act. Passed by Congress in 1996; implemented April 14, 2003 • Ensures that personal medical information that patients share with health care providers remains private and is protected

Why Is the HIPAA Privacy Regulation Needed? • When it comes to personal information that moves across hospitals, doctors’ offices, insurers or third party payers, and state lines, the United States has relied on a patchwork of federal and state laws. • Up to now, personal health information could be distributed – without either notice or consent – for reasons that have nothing to do with a patient’s medical treatment or a provider’s health care reimbursement. • The Privacy Regulation establishes a federal floor of safeguards to protect the confidentiality of medical information. State laws that provide stronger privacy protections will continue to apply over and above the new federal privacy standards. • Although health care providers have a strong tradition of safeguarding private health information, in today’s world, the old system of paper records in locked filing cabinets is not enough. • With information broadly held and transmitted electronically, the Privacy Regulation provides clear standards for all parties regarding protection of personal health information.

HIPAA Provides Benefits to Patients • Portability of health insurance • Protects patient privacy • Ensures that everyone who handles personally identifiable health information(including medical students) is responsible and accountable for protecting the patients’ privacy

What does the Privacy Regulation Do? -1 • The Privacy Regulation for the first time creates national standards to protect individuals’ medical records and other personal health information. • It gives patients more control over their health information. • It sets boundaries on the use and release of health records. • It establishes appropriate safeguards that health care providers and others must achieve to protect the privacy of health information. • It holds violators accountable, with civil and criminal penalties that can be imposed if they violate patients’ privacy rights. • And it strikes a balance when public responsibility requires disclosure of some forms of data - for example, to protect public health.

What Does the Privacy Regulation Do? - 2 For patients, • It means being able to make informed choices when seeking care and reimbursement for care based on how personal health information may be used. • It enables patients to find out how their information may be used and what disclosures of their information have been made. • It generally limits release of information to the minimum reasonably needed for the purpose of the disclosure. • It gives patients the right to examine and obtain a copy of their own health records and request amendments.

What Does the Privacy Regulation Do? -3 For the average health care provider, HIPAA requires activities, such as: • Providing information to patients about their privacy rights and how their information can be used. • Adopting clear privacy procedures for the particular practice or facility. • Training employees so that they understand the privacy procedures. • Designating an individual to be responsible for seeing that the privacy procedures are adopted and followed. • Securing patient records containing individually identifiable health information so that they are not readily available to those who do not need them. • Responsible health care providers and businesses already take many of the kinds of steps required by the regulation to protect patients’ privacy.

The Privacy Law • Protects all health information created by a healthcare provider, health plan or healthcare clearinghouse • Protects this information no matter how it is transmitted (verbally, electronically or in writing) • Defines who is allowed to use patients’ protected health information

Common HIPAA Jargon for Students • • IIHI- Individually Identifiable Health Info PHI- Protected Health Information CE- Covered entity TPO – TREATMENT – Payment – Operations (healthcare) • NPP- Notice of Privacy Practices

To Whom Does HIPPA Apply? • Covered Entity: under HIPAA, this means health plans, healthcare clearinghouses, healthcare providers who transmit any health information – Healthcare providers include all workforce members of hospitals and clinics including medical students

Who Must Comply With the HIPAA? • Tufts University is a “hybrid entity. ” This means that some, but not all, of its functions fall under HIPAA. • Since medical students see patients and clinical data at covered entities (affiliated clinics and hospitals), medical students are required to comply with the Privacy Regulation.

Protected Health Information (PHI) • PHI is any health information that is created by or received by a covered entity; and • relates to the past, present or future (e. g. genetic predisposition) physical or mental health or condition of an individual; or the past, present or future payment for the provision of health care to an individual • The standards apply to information, not to specific records; therefore, the protections apply to the information in any form (verbal, written, etc. )

IIHI: Individually Identifiable Health Information • All information which may potentially identify the individual or with respect to which there is a reasonable basis to believe that the information can be used to identify the individual • Individually identifiable health information is protected under the law

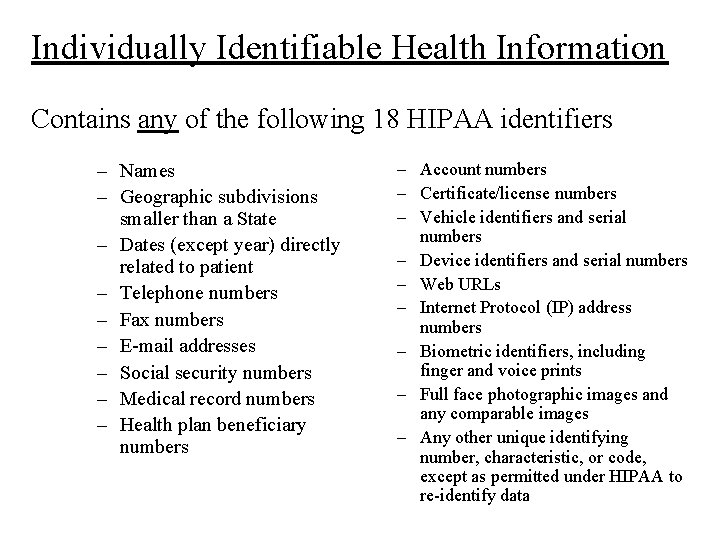
Individually Identifiable Health Information Contains any of the following 18 HIPAA identifiers – Names – Geographic subdivisions smaller than a State – Dates (except year) directly related to patient – Telephone numbers – Fax numbers – E-mail addresses – Social security numbers – Medical record numbers – Health plan beneficiary numbers – Account numbers – Certificate/license numbers – Vehicle identifiers and serial numbers – Device identifiers and serial numbers – Web URLs – Internet Protocol (IP) address numbers – Biometric identifiers, including finger and voice prints – Full face photographic images and any comparable images – Any other unique identifying number, characteristic, or code, except as permitted under HIPAA to re-identify data

Patient Rights • To have their privacy protected and respected. • To receive a notice of our privacy practices at first contact aft April 14, 2003 (and acknowledge receiving that notice). • To request/authorize disclosure of their PHI, although some disclosures do not require the patient’s authorization. • To receive a copy of their records, within a specified time frame, if they ask. • To request their records be amended (we do not have to comply, but we must respond in a specified time frame). • To request that PHI be communicated to the patient at alternative locations or by alternative means if possible (e. g. , different address).

Patient Rights (cont) • To request that our use or disclosure of their PHI be restricted (but we do not have to comply). • To receive an accounting of disclosures of their PHI generally within 60 days, except for disclosures for treatment, payment, our operations, disclosures the patients authorize, and certain other disclosures. • To complain about alleged violations of their rights to DHHS.

Notice of Privacy Practices • Each patient must receive such a notice at least once. • Such receipt must be documented by an acknowledgment receipt form, which must be signed, dated, and kept on record. • At most hospitals, this process will be handled by registration, the clinics, admitting, etc • Private offices must provide a separate notice specific to the practice’s privacy practices. The practice must handle this process and record keeping.

Disclosures • As covered entities need to track and account for certain disclosures, requests for copies of medical records or parts thereof should go through the Medical Records Department or some other central mechanism. • An exception is when a clinician sends a letter or a copy of a routine discharge summary to a referring clinician or a referral form to another facility or the VNA (or other homecare agency), as such communication is explicitly for treatment purposes. • Similarly the reporting of a test or a procedure result to a referring clinician for treatment purposes is not an accountable disclosure and can be sent as usual to the referring or receiving clinician.

Minimum Necessary Standard • For treatment purposes (actually T, P or O) PHI can be used without seeking authorization (unless the patient has requested and we have agreed to restriction to such use). • However, even when providing treatment, HIPAA requires us to use the minimum amount of information required to accomplish the intended purpose. • But, the rule of thumb should always be Safety and Patient Care Comes First • However please distinguish between need to know and right to know. • Only access PHI based on your need to know.

Minimum Necessary Standard (cont) • The minimum necessary standard does not apply when requesting PHI from or disclosing PHI to another health care provider for treatment purposes. • When disclosing information for non-TPO purposes, HIPAA asks we disclose the minimum amount of PHI needed to comply with the need. • The minimum necessary standard does not apply to disclosures to the patient or authorized by the patient.

Teaching • In an academic institution, teaching is a key part of operations. • Bedside rounds, teaching rounds, conferences, clerkships, etc are all permissible. • On the wards or in the clinics, take measures to minimize incidental disclosures, such as speaking softly. • At conferences, minimize disclosure of patient identifiers as much as possible without compromising the educational goals. Tufts attempts to “de‑identify” patient information used in lectures and other teaching activities. • Any student must complete this HIPAA training before having access to any PHI. In some circumstances, our affiliated covered entities, may require more training than completion of this module from the medical school.

Research • Special rules apply. • See information provided the Institutional Review Board. • Can use “De-Identified Data” – All 18 HIPAA identifiers removed • Can Use With Patient’s Authorization – Research Authorization Form: Signed, Time and Use Limited • Can Use Limited Data Set • Contains Date and Geographic Region But No Other Identifiers • Requires Data Use Agreement • Can Use If Waiver Given By Institutional Privacy Board but not for inconvenience to investigator • Can Use If Patient Is Deceased • Can Use If Chart Review in preparation for research, but individually identifiable data may NOT be extracted from the charts.

Research (cont) • Research sponsors are not usually Business Associates (BAs) and their seeing the data constitute a disclosure about which the patient must be informed. • Coded data Are De-Identified but code sheets/files are PHI

Incidental Disclosures • Incidental disclosures cannot all be avoided and HIPAA recognizes that, but the risk of such disclosures should be minimized. • Do not discuss PHI in public places, e. g. , elevators, hallways, restaurants, etc. • Do not use your cell phone to discuss PHI in public places. • Speak softly when another patient is nearby (e. g. , double rooms, ICUs, etc).

Incidental Disclosures (cont) • In clinics, speak to your patients in private rooms, not in the waiting room. • It is OK to call a patient by name from a waiting room or keep a patient list containing only their names. • Keep charts, mail, test results, etc in protected areas. • If necessary for patient care and safety, limited disclosure may be made (e. g. , identifying a patient as being on precautions).

Important Measures to Comply with Privacy Rule • • • Environmental safeguards Suggestions for use of PCs and PDAs Use of shredders Suggestions for phone calls and faxes Students may not take PHI out of the hospital or office • Patient Logs and Notes • E-mail

The Physical Environment • Keep PHI in protected areas, as much as possible. • Some hospitals and practices white boards or bulletin boards. In general, such boards should not contain diagnoses or clinical information. Most will list patient name, nurse and house officer, but not the attending clinician (which more likely implies the diagnosis). • White boards that have any more information should be in protected, non-public areas. • Use shredders or secure disposal containers for PHI. • In clinics, keep appointment schedules in a protected area. • If charts are put in holders on a clinic or patient door, they should be turned so as not to display the patient’s name and medical record number.

Using PCs • Protect your password. Do not share it. Change it if it may be compromised. • Log off your computer or the application when your are done with your task. If that is inconvenient, use a screen saver. • Position the monitor screen so it can not be easily viewed by casual passers-by as you are working.

Shredding • Many covered entities, such as NEMC, have placed shredding receptacles or other disposal receptacles for PHI in clinical spaces. • Utilize shredders for any PHI no longer needed.

Phone Calls and Faxes • Be certain you know to whom and to where you are phoning or faxing before disclosing PHI. • Fax cover sheets should contain a confidentiality notice such as: Note: The information contained in this facsimile may be privileged and confidential and protected from disclosure. If the reader of this facsimile is not the intended recipient, you are hereby notified that any reading, dissemination, distribution, copying, or other use of this facsimile is strictly prohibited. If you have received this facsimile in error, please notify the sender immediately by telephone at _________ and destroy this facsimile. Thank you. • Be wary of making calls in public areas. Speak as softly as possible. • Be aware that cell phone conversations on non-digital phones can be intercepted. • Receiving fax machines should be in a secure location.

Taking PHI Outside of a Clinical Setting • Great care must be exercised if PHI that is taken from any clinical setting physically or outside its firewall electronically. In general, DO NOT DO IT. • Such exposures include notes you are editing or writing, rounding card decks, signout sheets or cards, and information contained in your PDAs, laptops, on disks, on CDs, etc. • Destroy or erase such data when its use outside of that clinical setting is no longer absolutely necessary. • DO NOT DISCARD PHI IN UNSHREDDED TRASH. • However, if access to such PHI is necessary for safe patient care, be extremely careful and protect our patients’ privacy. • As a medical student, you would ordinarily NOT require such access to PHI outside the clinical setting for patient care.

Taking PHI Outside of a Clinical Setting (Cont) • Before you remove any PHI from a clinical setting ask permission. • If you do take any PHI outside of the clinical setting, you are personally accountable for any disclosures, even incidental disclosures. • Violation of this policy could preclude your returning to that setting, and may subject you to disciplinary action at the school.

PDAs, Laptops • Password protect your PDA and laptop, in case they are lost or stolen. • If any PHI is present on the hard disk of a computer you use, delete and purge (overwrite) those sectors of your hard disk. • If that computer requires repair, consult the Student Affairs Office, because PHI could be recovered from the hard disk on the computer and that would constitute a disclosure of PHI. • To repeat, violation of this policy could preclude your returning to that clinical setting and may subject you to disciplinary action at the school.

Patient Logs and Notes • Some students have the habit of keeping personal copies of their notes and other PHI for their own records. – This is an extremely dangerous practice and could subject you to disciplinary action and personal legal consequences if that PHI were to be disclosed, even inadvertently or incidentally. – At the very least, be certain that EVERY one of the 18 HIPAA identifiers has been removed from any such notes. • Some rotations require students to keep patient logs. Such logs should NOT contain any of the 18 HIPAA identifiers, unless approved by the privacy officer of the clinical setting.

• Using e-mail (cont) Unlike E-mail sent within a covered entity that remains within its firewall, any e-mail sent outside of the covered entity (including email sent to Tufts, the HNRC or other hospitals travels over the internet and may therefore cause a disclosure (unless it is specially encrypted). – If you are given an e-mail account at a hospital, Do NOT forward that e-mail outside of that hospital, even manually, if it MIGHT contain any PHI. • There is no easy, standard way to encrypt e-mail at this time. • Because of the nature of unencrypted e-mail transmission and the risk of privacy breaches, the use of e-mail that contains PHI (any of the 18 identifiers, one of which is the patient’s email address) outside of a covered entity’s network firewall may either be prohibited by that institution or may require the patient’s explicit written consent, even e-mail among clinicians. • Your Tufts e-mail account is NOT behind a HIPAA-safe firewall and cannot be e-mailed to from another institution without the message traversing the internet. THEREFORE, YOUR TUFTS EMAIL ACCOUNT CANNOT CONTAIN ANY PHI OR PATIENT IDENTIFIERS.

What if I am unsure whether I can disclose protected health information, or whether information is, in fact, protected health information? • If in doubt, do not give out information without first checking with your attending, clerkship, course director, or other person responsible for the confidentiality of health information in the practice setting, usually the “Privacy Officer”. • Remember that HIPAA is a new law and the faculty, providers, and the public are just now working through its implications for practice, teaching, and research.

Basic Rule No Use or Disclosure of PHI without patient authorization Except: • For treatment, payment and health care operations Remember: Patient care and safety come first! – In a teaching hospital, teaching is a part of treatment and a part of our health care operations. • Or When a specific regulatory exception under HIPAA applies, e. g. , public health reporting, in emergencies/ disasters, to identify patients or locate family members; and as required by law. Keep in mind, there are special requirements under state law for the use and disclosure of certain categories of highly confidential information (e. g. , HIV information, genetic testing information, alcohol and drug abuse treatment information, and mental health treatment information).

Basic Principles • • • Only use PHI that you need Ask yourself: “Do I really need this? ” Only disclose PHI to meet a legitimate need Ask yourself: “Do I need to disclose this? ” The golden rule: – Ask yourself: “What would you wish done if you or a close family member were the patient? ”

HIPAA Review Certification This is a required component of your application to the TUSM Visiting Student Program. I certify that I have reviewed the TUSM HIPAA Guidelines: Printed Name: ___________________ Signature: ____________________Date: ______ Print ONLY this page of this document and mail along with your application and other supporting materials to: TUSM Visiting Student Program Registrar’s Office 145 Harrison Ave. Boston, MA 02111
 Privacy awareness and hipaa privacy training cvs answers
Privacy awareness and hipaa privacy training cvs answers Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Air force hipaa training
Air force hipaa training Hipaa training georgia
Hipaa training georgia Accountable hipaa training
Accountable hipaa training Hipaa training strategies
Hipaa training strategies Hipaa training for nurses
Hipaa training for nurses Ibp training
Ibp training Personal information lifecycle
Personal information lifecycle Who trains employees that work on scaffolds
Who trains employees that work on scaffolds Ladder outline
Ladder outline Child protection training materials
Child protection training materials Child protection awareness training
Child protection awareness training Patient portals and hipaa
Patient portals and hipaa Hippa secure now
Hippa secure now Joint commission accreditation standards
Joint commission accreditation standards Hipaa pre-existing condition protections
Hipaa pre-existing condition protections Gillman hipaa progress note
Gillman hipaa progress note Hipaa cow
Hipaa cow Jira hipaa
Jira hipaa Hipaa security rule self assessment toolkit
Hipaa security rule self assessment toolkit Gillman hipaa progress note
Gillman hipaa progress note Certified hipaa administrator
Certified hipaa administrator Hipaa summit
Hipaa summit What does tpo stand for in hipaa
What does tpo stand for in hipaa When should you promote hipaa awareness
When should you promote hipaa awareness Jcaho standards
Jcaho standards Hipaa security rule objectives
Hipaa security rule objectives What is hipaa
What is hipaa What is hipaa
What is hipaa Ada hipaa compliance kit
Ada hipaa compliance kit Hippocratic oath
Hippocratic oath Hippa
Hippa Louisiana hipaa laws
Louisiana hipaa laws Hipaa summit
Hipaa summit Hipaa frequently asked questions
Hipaa frequently asked questions Hipaa breach notification decision tree
Hipaa breach notification decision tree Hipaa principles
Hipaa principles Family educational rights and privacy act
Family educational rights and privacy act Gremote.geisinger
Gremote.geisinger Becoming hipaa compliant
Becoming hipaa compliant































































