PRESENTATION ON WIFI TECHNOLOGY Contents Need of WIFI















- Slides: 30

PRESENTATION ON WI-FI TECHNOLOGY

Contents • • • Need of WIFI Introduction Wi-Fi Technologies Wi-Fi Network Elements Wi-Fi Architecture How a Wi-Fi Network Works Wi-Fi Network Topologies Wi-Fi Security Post Implementation Advantages/ Disadvantages of Wi-Fi Applications

NEED ? ? Higher authorities do not want wiring When guest/auditor comes then installation of new LAN is not possible Employees seat is not fixed Handling of cables(wires) is difficult

Introduction • Wireless Technology is an alternative to Wired Technology, • Wi-Fi Network connect computers to each other, to the internet and to the wired network.

The Wi-Fi Technology Wi-Fi Networks use Radio Technologies to transmit & receive data at high speed: • IEEE 802. 11 b • IEEE 802. 11 a • IEEE 802. 11 g

IEEE 802. 11 b • Operates at 2. 4 GHz radio spectrum • 100 -150 feet range • Most popular, Least Expensive IEEE 802. 11 a Operates at 5 GHz (less popular) 50 -75 feet range More expensive, Not compatible with 802. 11 b

IEEE 802. 11 g Combine the feature of both standards (a, b) 100 -150 feet range 2. 4 GHz radio frequencies, Compatible with ‘b’

Elements of a WI-FI Network 1. Switch --- Nortel WLAN 2360 2. Access point --- NORTEL WLAN 2330 3. Devices --- Mobiles, Laptop, Personal computers 4. WIFI Cards--- PCMCIA Cards, PCI Cards 5. Safeguards--- Antivirus & Firewalls

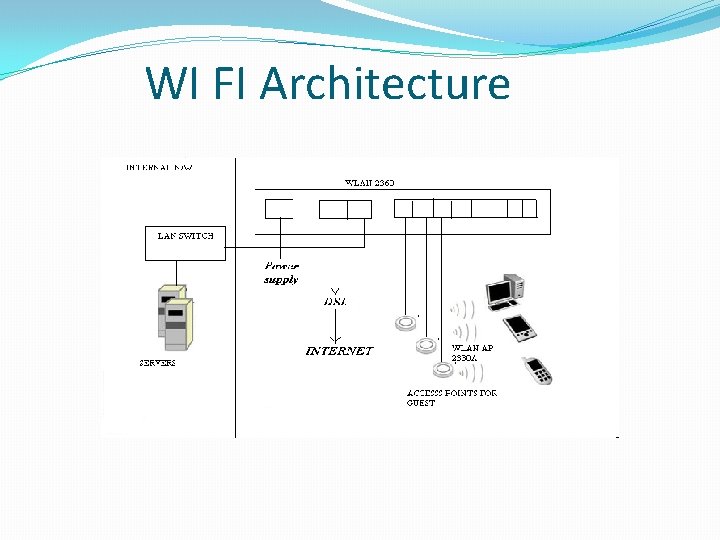
WI FI Architecture

How a Wi-Fi Network Works • Basic concept is same as Walkie talkies. • A Wi-Fi hotspot is created by installing an access point to an internet connection. • An access point acts as a base station. • When Wi-Fi enabled device encounters a hotspot the device can then connect to that network wirelessly. • A single access point can support up to 30 users and can function within a range of 100 – 150 feet indoors and up to 300 feet outdoors. • Many access points can be connected to each other via Ethernet cables to create a single large network.

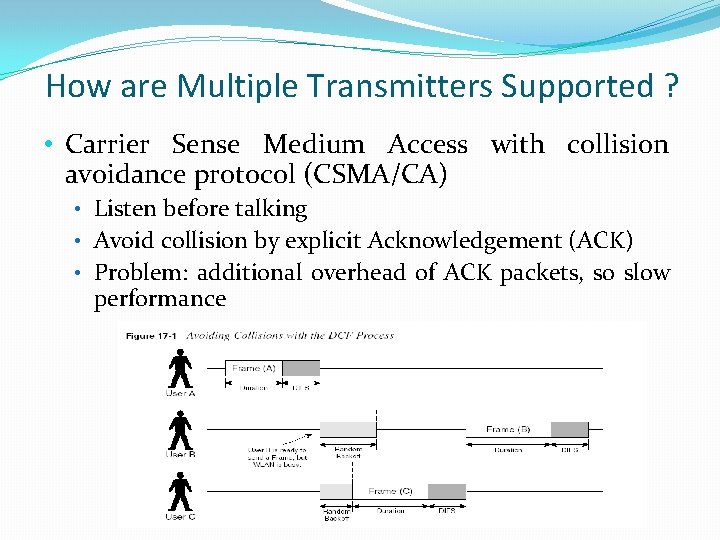
How are Multiple Transmitters Supported ? • Carrier Sense Medium Access with collision avoidance protocol (CSMA/CA) • Listen before talking • Avoid collision by explicit Acknowledgement (ACK) • Problem: additional overhead of ACK packets, so slow performance

Wi-Fi Network Topologies • AP-based topology • Peer-to-peer topology • Point-to-multipoint bridge topology

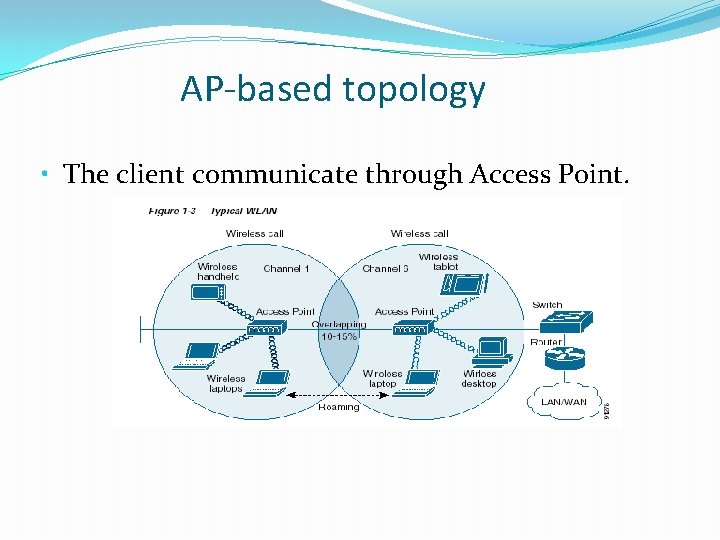
AP-based topology • The client communicate through Access Point.

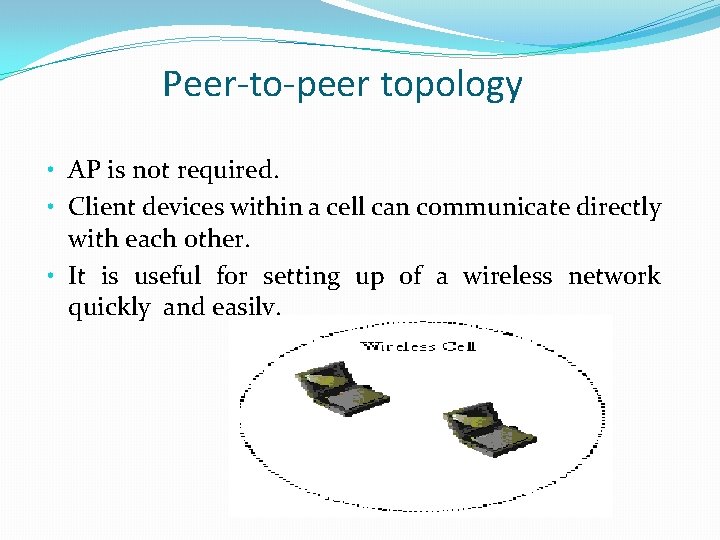
Peer-to-peer topology • AP is not required. • Client devices within a cell can communicate directly with each other. • It is useful for setting up of a wireless network quickly and easily.

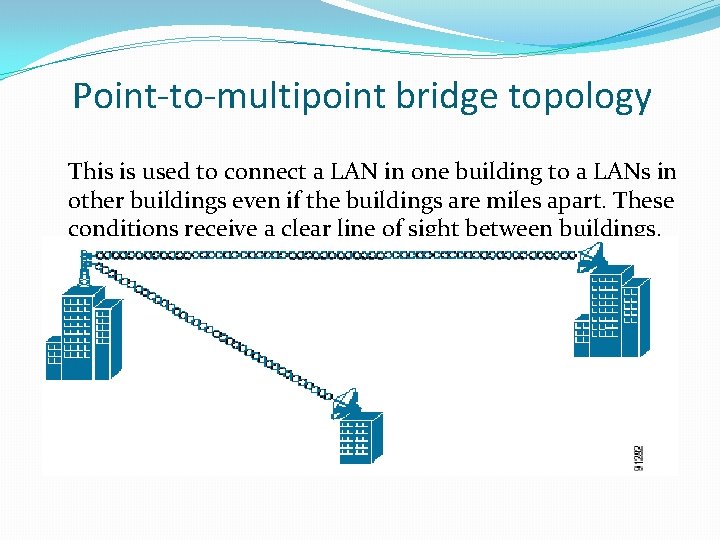
Point-to-multipoint bridge topology This is used to connect a LAN in one building to a LANs in other buildings even if the buildings are miles apart. These conditions receive a clear line of sight between buildings.

WI-FI Security The requirements for Wi-Fi network security can be broken down into two primary components: Authentication User Authentication Server Authentication Privacy

WI-FI Security Techniques • Service Set Identifier (SSID) • Wired Equivalent Privacy (WEP) • 802. 1 X Access Control • Wireless Protected Access (WPA) • IEEE 802. 11 i

Post Implementation Test There are basically two types of testing to be done 1. QTR-WEB Testing 2. QTR-GUEST Testing

QTR-WEB Testing Step 1: Ø Click on Wireless icon on the Taskbar

Step 2: Below shown window will appear, click on Refresh network list.

Step 3: Double click on QTR-Web WI-FI Connection .

Step 4: Insert the Authentication Key Step 5: Wait for few moments, while it is accruing the IP address

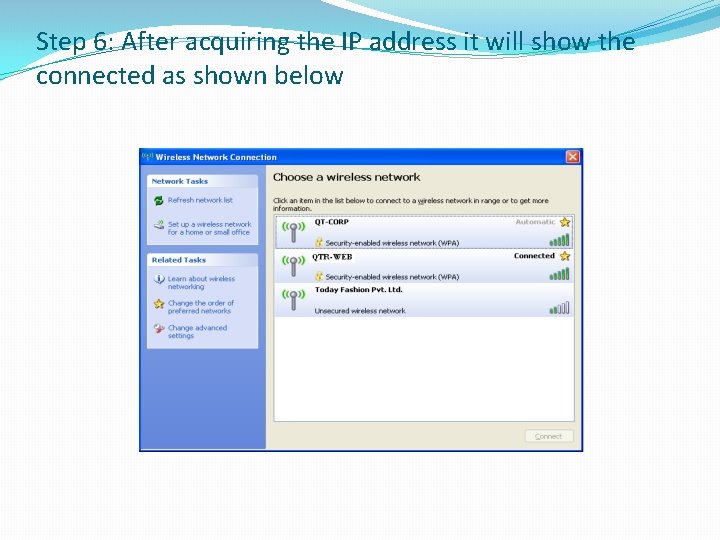
Step 6: After acquiring the IP address it will show the connected as shown below

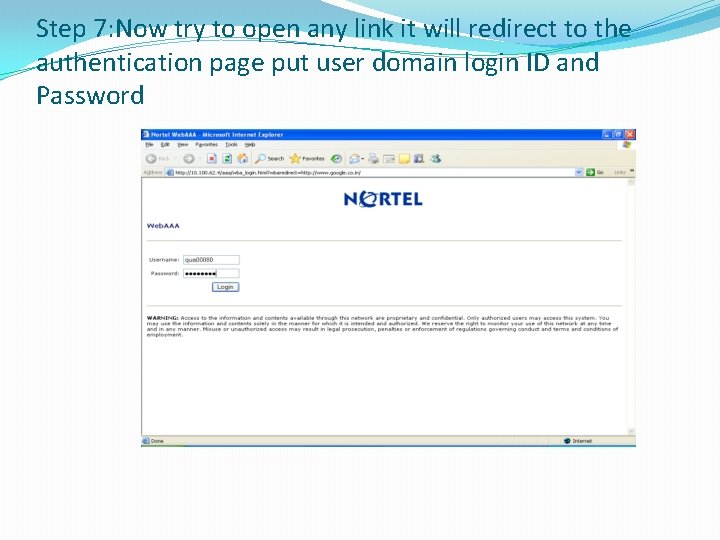
Step 7: Now try to open any link it will redirect to the authentication page put user domain login ID and Password

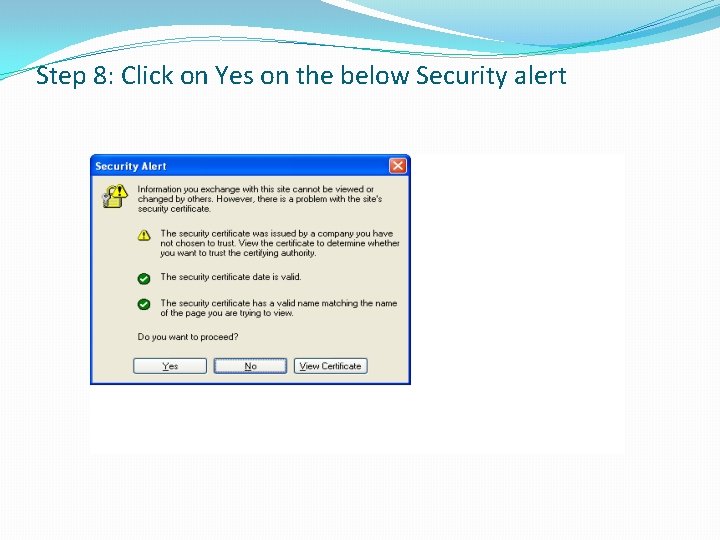
Step 8: Click on Yes on the below Security alert

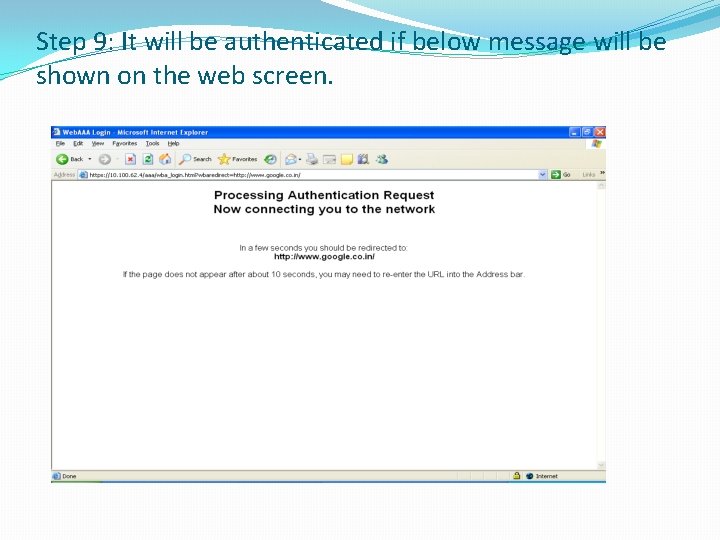
Step 9: It will be authenticated if below message will be shown on the web screen.

Advantages Mobility Ease of Installation Flexibility Cost Reliability Security Use unlicensed part of the radio spectrum Roaming Speed

LIMITATIONS Interference Degradation in performance High power consumption Limited range

Wi-Fi Applications Home Small Businesses Large Corporations & Campuses Health Care Travellers

 Formula sales presentation method
Formula sales presentation method Formula sales presentation
Formula sales presentation Smallest anteroposterior diameter of the pelvic inlet
Smallest anteroposterior diameter of the pelvic inlet Vertex presentation
Vertex presentation Define career portfolio
Define career portfolio Deep perineal pouch contents
Deep perineal pouch contents Febrile non hemolytic transfusion reaction
Febrile non hemolytic transfusion reaction Fresh frozen plasma contents
Fresh frozen plasma contents Superior mediastinum contents
Superior mediastinum contents Femoral triangle
Femoral triangle Superior mediastinum
Superior mediastinum The immortal life of henrietta lacks table of contents
The immortal life of henrietta lacks table of contents Medial lemniscus
Medial lemniscus Site:slidetodoc.com
Site:slidetodoc.com Ark of the covenant lampstand
Ark of the covenant lampstand Comic book table of contents
Comic book table of contents Falciform ligament
Falciform ligament Mla table of contents
Mla table of contents Stylistic lexicology
Stylistic lexicology Front cover page for school magazine
Front cover page for school magazine Continuous variable
Continuous variable Appendix in report
Appendix in report Ffp vs platelets
Ffp vs platelets Superior mediastinum contents
Superior mediastinum contents Middle mediastinum: contents mnemonic
Middle mediastinum: contents mnemonic Abstract and introduction
Abstract and introduction Persepolis table of contents
Persepolis table of contents Persepolis table of contents
Persepolis table of contents Interactive notebook table of contents
Interactive notebook table of contents Cryoprecipitate contains
Cryoprecipitate contains Peduncles anatomy
Peduncles anatomy