Outsourcing Private RAM Computation Daniel Wichs Northeastern University


![Garbled Computation Garbled Circuits [Yao 82] Reusable Garbled Circuits [GKPVZ 13 a, b] Can Garbled Computation Garbled Circuits [Yao 82] Reusable Garbled Circuits [GKPVZ 13 a, b] Can](https://slidetodoc.com/presentation_image_h2/043791b75860c8d7d4cd333f95fb6cc2/image-8.jpg)




- Slides: 27

Outsourcing Private RAM Computation Daniel Wichs Northeastern University with: Craig Gentry, Shai Halevi, Mariana Raykova

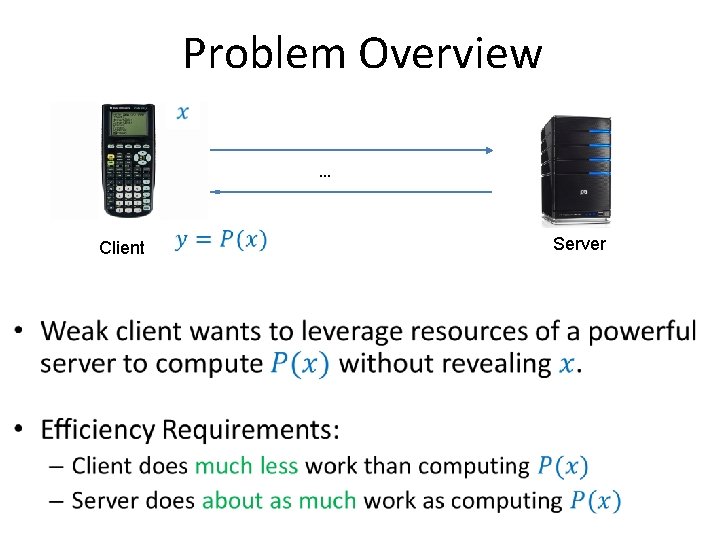
Problem Overview • … Client Server

Use FHE! Done? • Private outsourcing is possible using Fully Homomorphic Encryption (FHE). [RAD 78, Gen 09, …] • But FHE works over circuits rather than RAM programs. I’m very efficient!

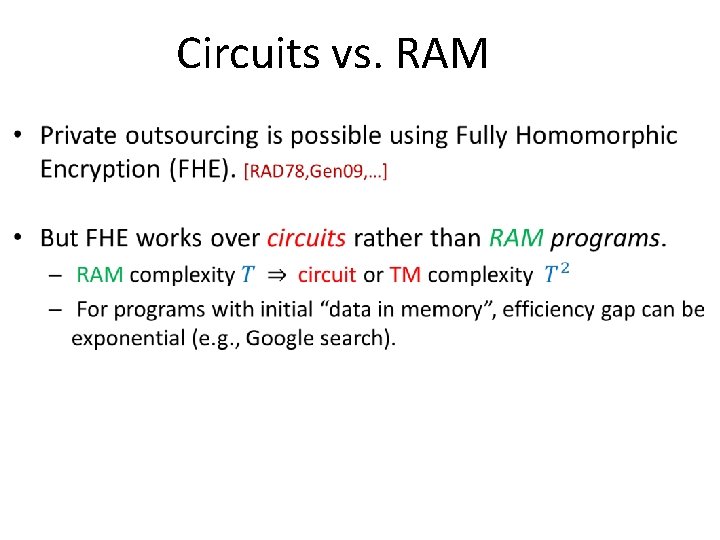
Circuits vs. RAM •

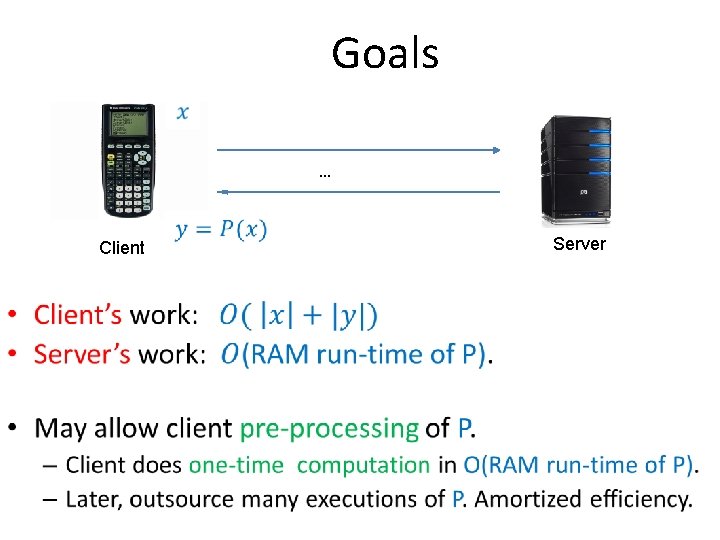
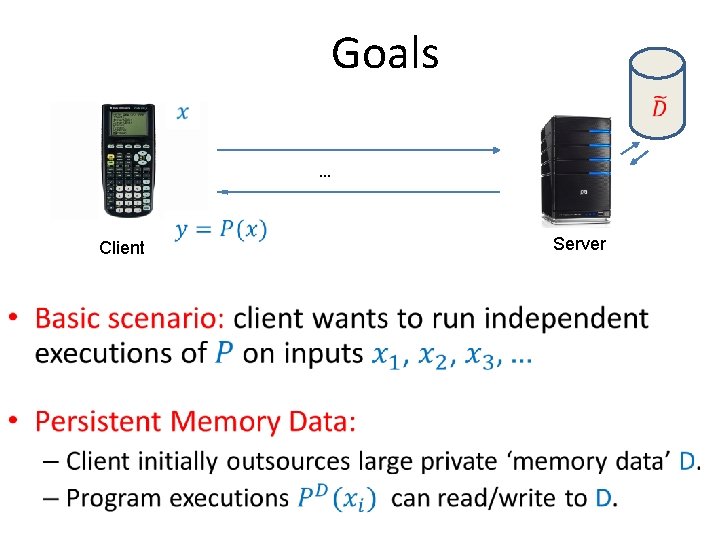
Goals … Client • Server

Goals … Client • Server

Goals Client Server • Non-interactive solution: “reusable garbled RAM”.
![Garbled Computation Garbled Circuits Yao 82 Reusable Garbled Circuits GKPVZ 13 a b Can Garbled Computation Garbled Circuits [Yao 82] Reusable Garbled Circuits [GKPVZ 13 a, b] Can](https://slidetodoc.com/presentation_image_h2/043791b75860c8d7d4cd333f95fb6cc2/image-8.jpg)
Garbled Computation Garbled Circuits [Yao 82] Reusable Garbled Circuits [GKPVZ 13 a, b] Can garble many inputs per circuit. Efficiently outsource circuit comp. Extension to TM. Garbled RAM [LO 13, GHLORW 14] Reusable Garbled RAM This Talk! Can garble many inputs per program. Efficiently outsource RAM comp.

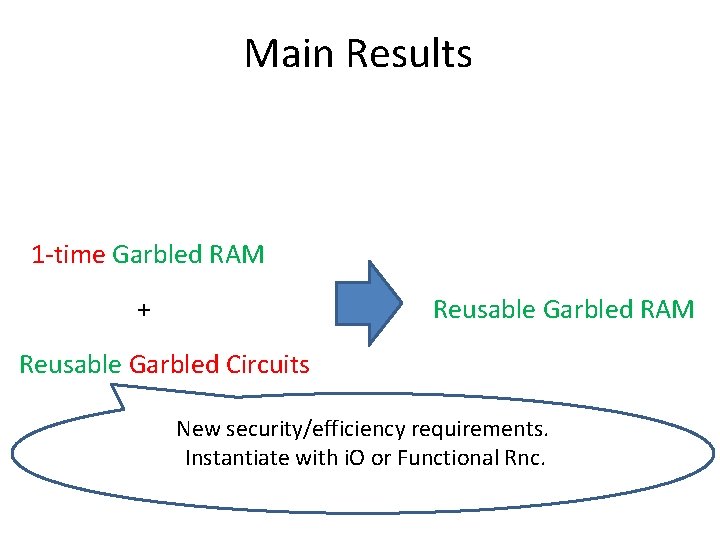
Main Results 1 -time Garbled RAM + Reusable Garbled RAM Reusable Garbled Circuits New security/efficiency requirements. Instantiate with i. O or Functional Rnc.

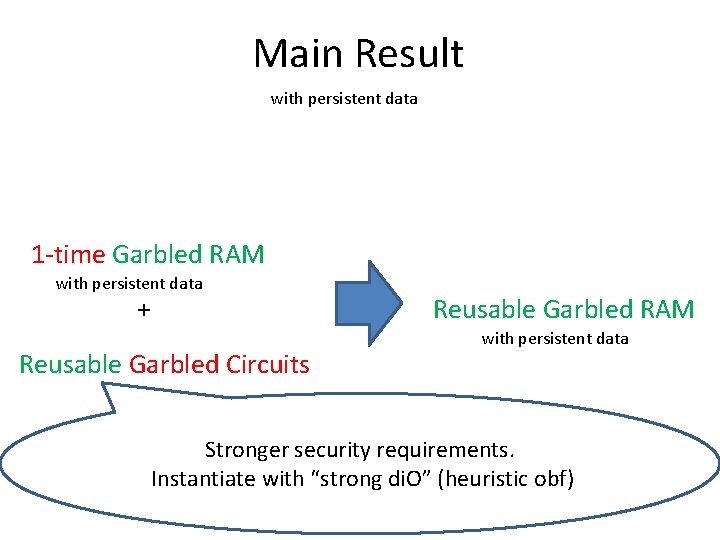
Main Result with persistent data 1 -time Garbled RAM with persistent data + Reusable Garbled Circuits Reusable Garbled RAM with persistent data Stronger security requirements. Instantiate with “strong di. O” (heuristic obf)

Without Persistent Data

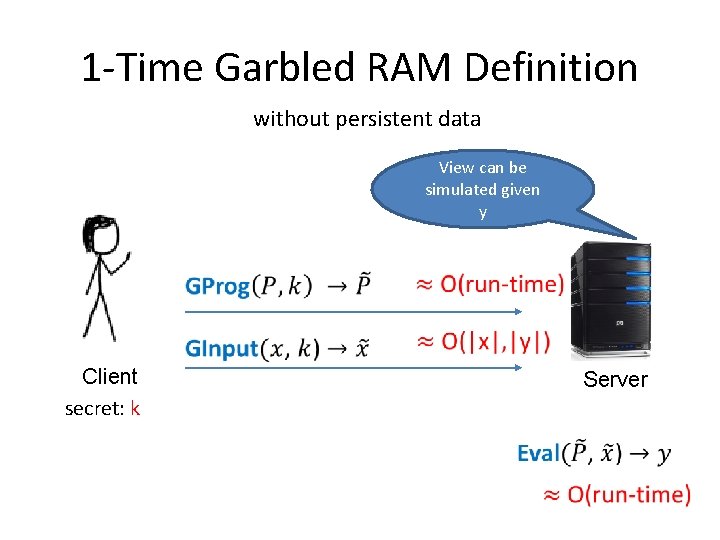
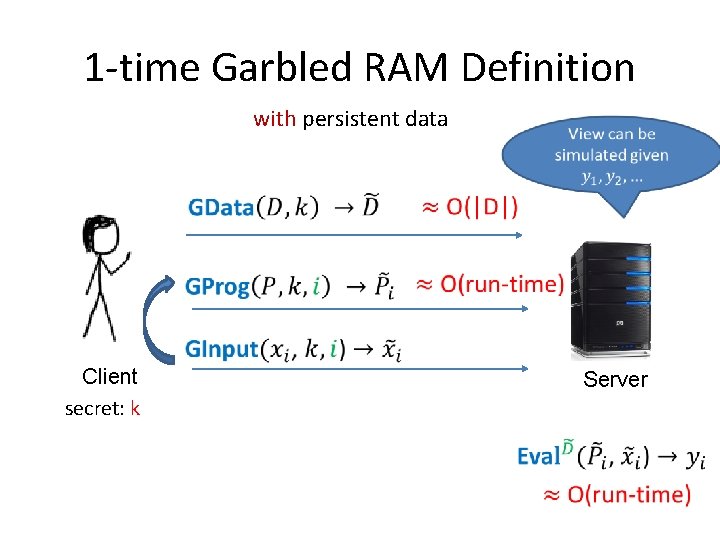
1 -Time Garbled RAM Definition without persistent data View can be simulated given y Client secret: k Server

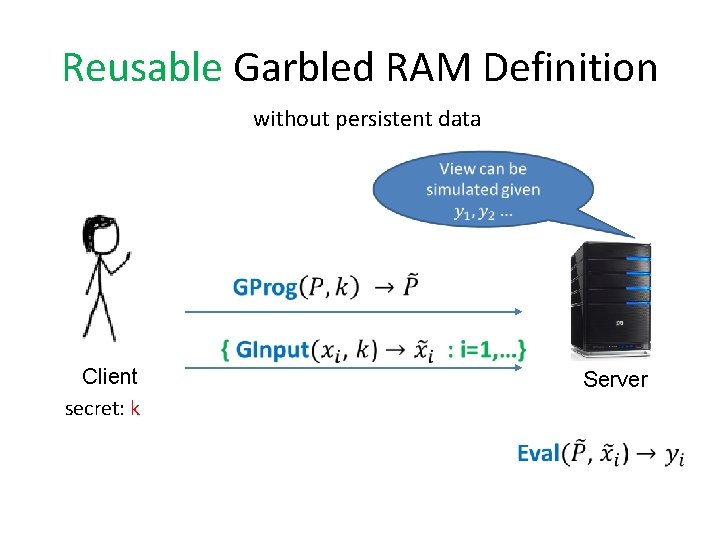
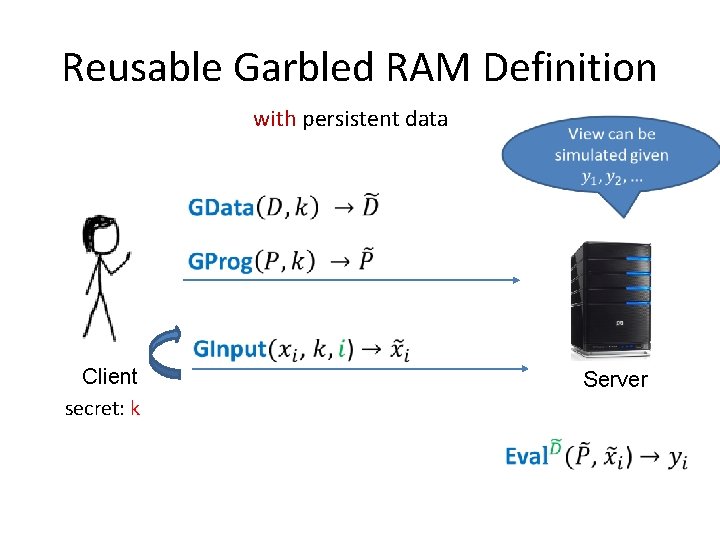
Reusable Garbled RAM Definition without persistent data Client secret: k Server

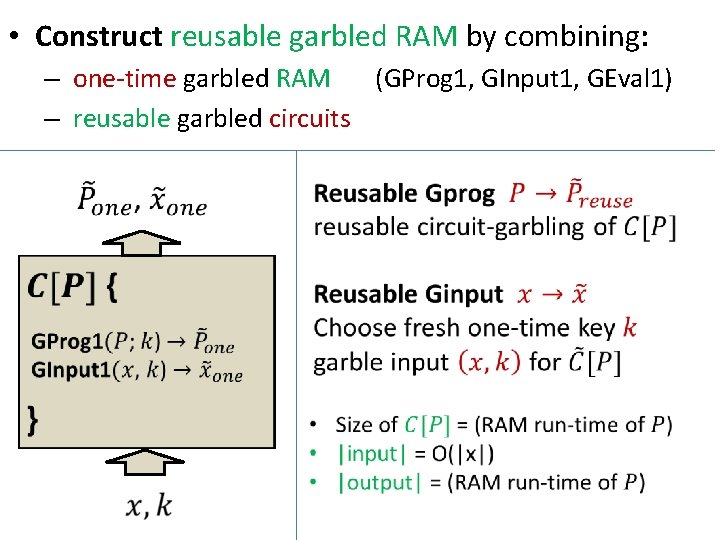
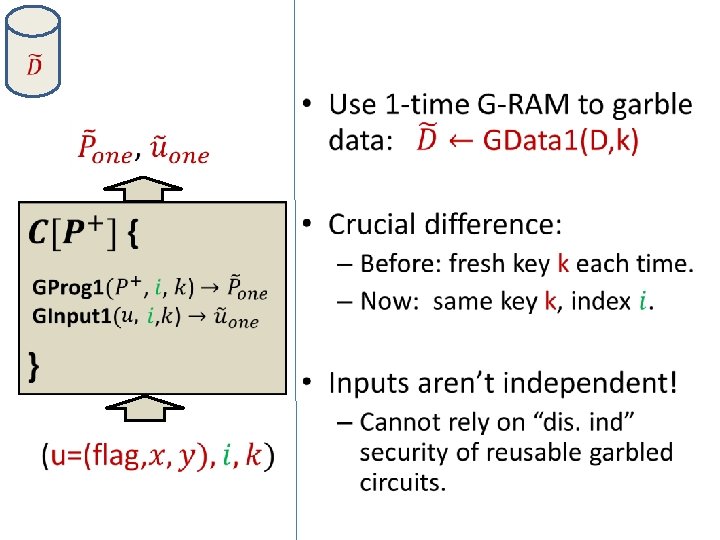
• Construct reusable garbled RAM by combining: – one-time garbled RAM (GProg 1, GInput 1, GEval 1) – reusable garbled circuits

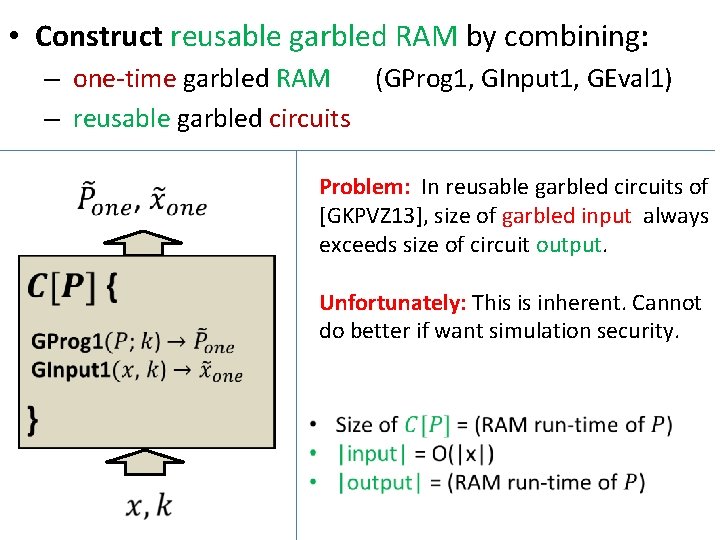
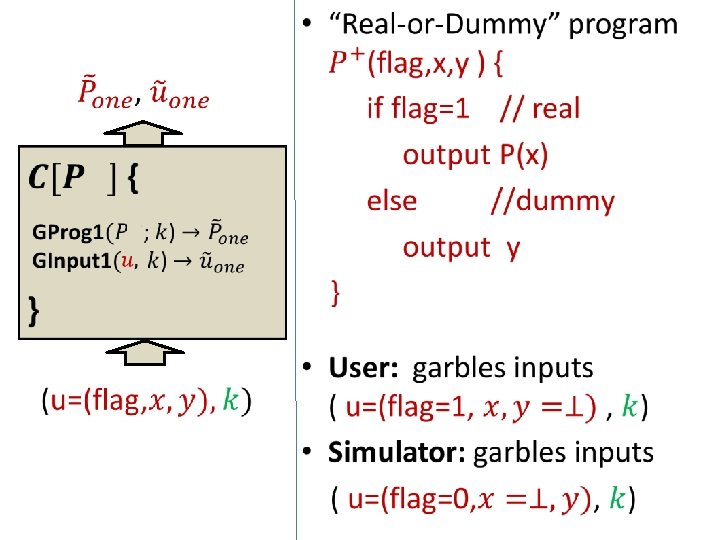
• Construct reusable garbled RAM by combining: – one-time garbled RAM (GProg 1, GInput 1, GEval 1) – reusable garbled circuits Problem: In reusable garbled circuits of [GKPVZ 13], size of garbled input always exceeds size of circuit output. Unfortunately: This is inherent. Cannot do better if want simulation security.

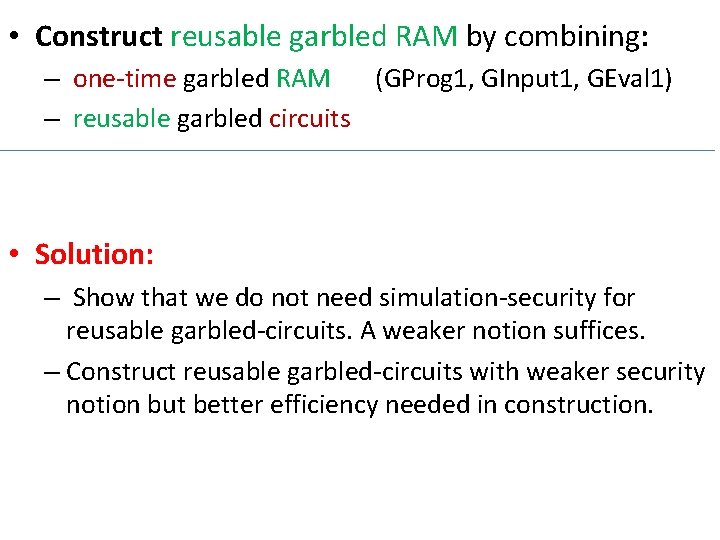
• Construct reusable garbled RAM by combining: – one-time garbled RAM (GProg 1, GInput 1, GEval 1) – reusable garbled circuits • Solution: – Show that we do not need simulation-security for reusable garbled-circuits. A weaker notion suffices. – Construct reusable garbled-circuits with weaker security notion but better efficiency needed in construction.

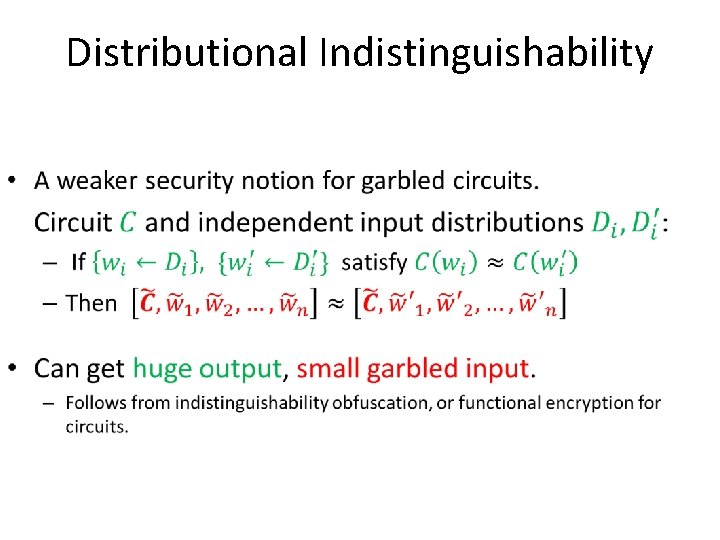
• Distributional Indistinguishability


With Persistent Memory

1 -time Garbled RAM Definition with persistent data Client secret: k Server

Reusable Garbled RAM Definition with persistent data Client secret: k Server


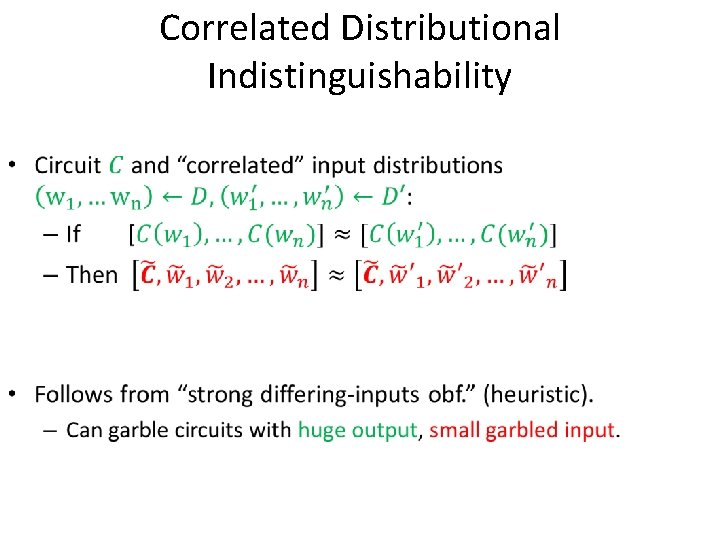
• Correlated Distributional Indistinguishability

• Theorem: Get reusable garbled RAM where: – Garble, evaluate program: O(RAM run-time P). – Garble input = O( input + output size). assuming “ind. obfuscation” + stat. sound NIZK. • Theorem: Get reusable garbled RAM with persistent memory where: – garble data = O( data size) – garble program = O( description size P ) – garble input = O( input + output size) – evaluate = O( RAM run-time P) assuming “strong differing-inputs obfuscation” (heuristic).

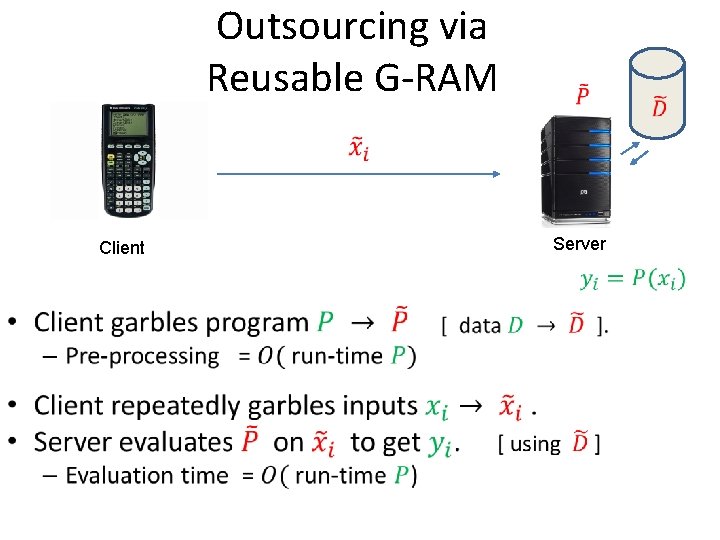
Outsourcing via Reusable G-RAM Client • Server

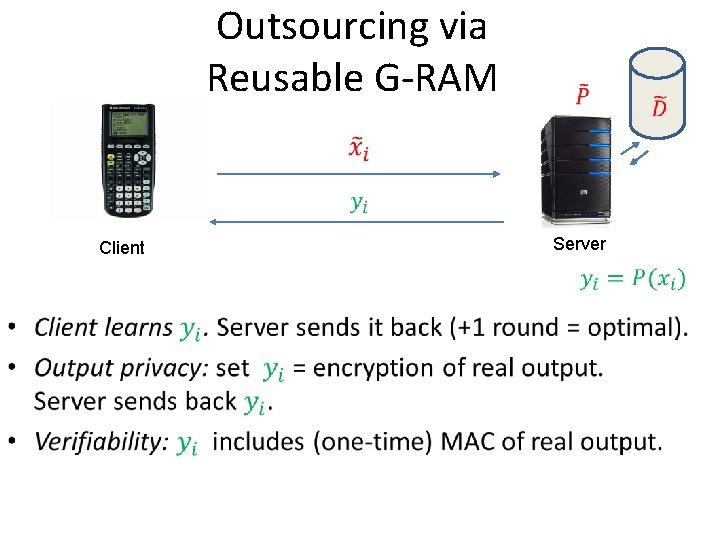
Outsourcing via Reusable G-RAM Client • Server

Thank You! Don’t turn me into a circuit!