On Oneway and Twoway Classical Post Processing Quantum



- Slides: 22

On One-way and Two-way Classical Post. Processing Quantum Key Distribution Marcos Curty 1, 2 Coauthors: Tobias Moroder 2, 3, and Norbert Lütkenhaus 2, 3 1. 2. 3. Center for Quantum Information and Quantum Control (CQIQC), University of Toronto Institute for Quantum Computing, University of Waterloo Max-Plank-Forschungsgruppe, Institut für Optik, Information und Photonik, Universität Erlangen-Nürnberg

Overview • Quantum Key Distribution (QKD) • Precondition for secure QKD (Two-way & One-way) • Witness Operators (Two-way & One-way QKD) • Semidefinite Programming • Evaluation

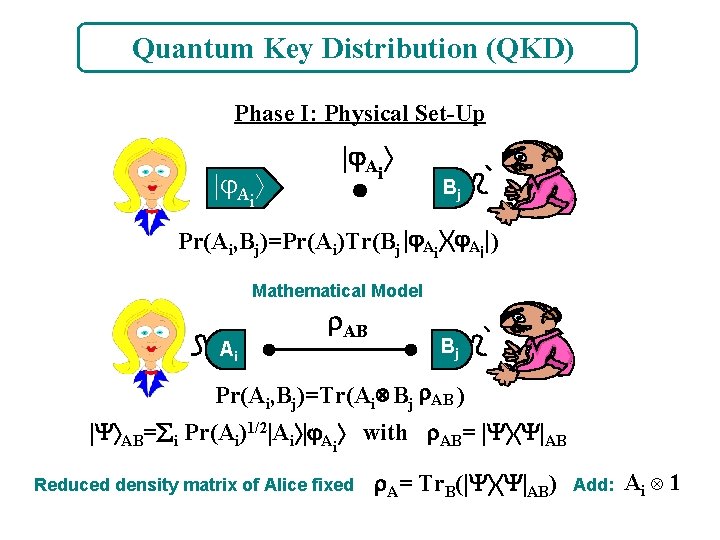
Quantum Key Distribution (QKD) Phase I: Physical Set-Up Ai Ai Bj Pr(Ai, Bj)=Pr(Ai)Tr(Bj Ai ) Mathematical Model Ai AB Bj Pr(Ai, Bj)=Tr(Ai Bj AB ) AB= i Pr(Ai)1/2 Ai A with AB= AB i Reduced density matrix of Alice fixed A= Tr. B( AB) Add: Ai 1

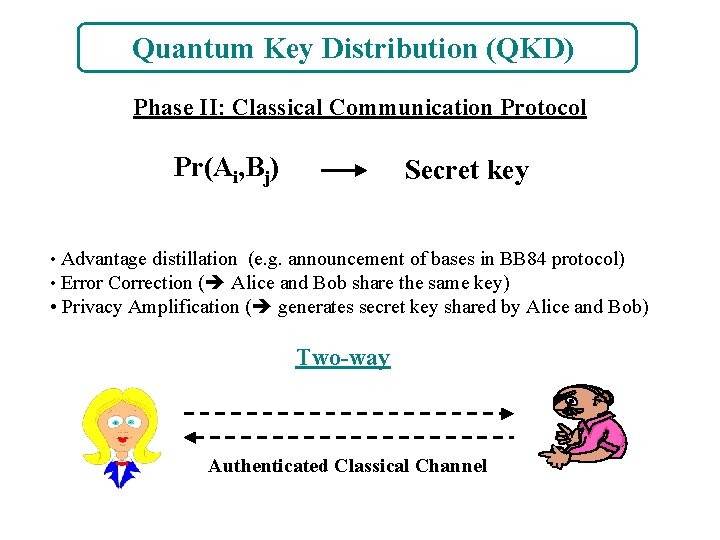
Quantum Key Distribution (QKD) Phase II: Classical Communication Protocol Pr(Ai, Bj) Secret key • Advantage distillation (e. g. announcement of bases in BB 84 protocol) • Error Correction ( Alice and Bob share the same key) • Privacy Amplification ( generates secret key shared by Alice and Bob) Two-way Authenticated Classical Channel

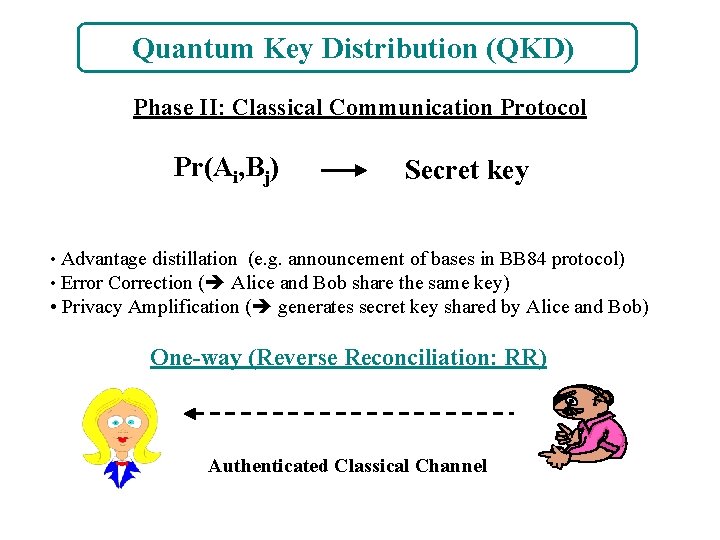
Quantum Key Distribution (QKD) Phase II: Classical Communication Protocol Pr(Ai, Bj) Secret key • Advantage distillation (e. g. announcement of bases in BB 84 protocol) • Error Correction ( Alice and Bob share the same key) • Privacy Amplification ( generates secret key shared by Alice and Bob) One-way (Reverse Reconciliation: RR) Authenticated Classical Channel

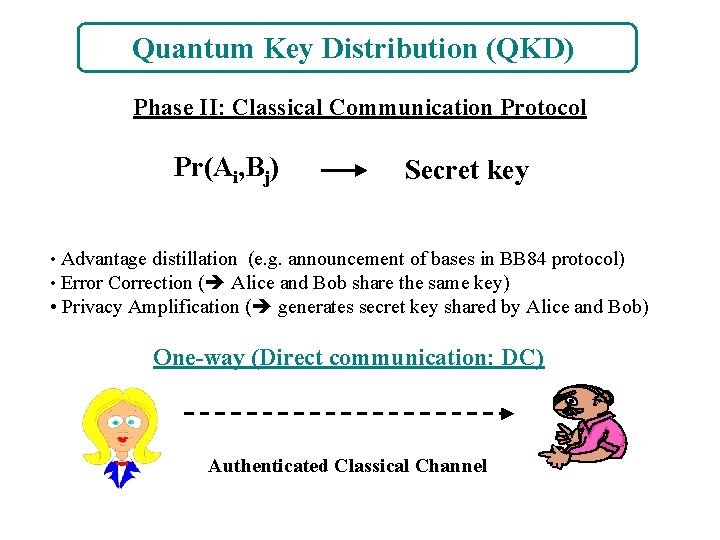
Quantum Key Distribution (QKD) Phase II: Classical Communication Protocol Pr(Ai, Bj) Secret key • Advantage distillation (e. g. announcement of bases in BB 84 protocol) • Error Correction ( Alice and Bob share the same key) • Privacy Amplification ( generates secret key shared by Alice and Bob) One-way (Direct communication: DC) Authenticated Classical Channel

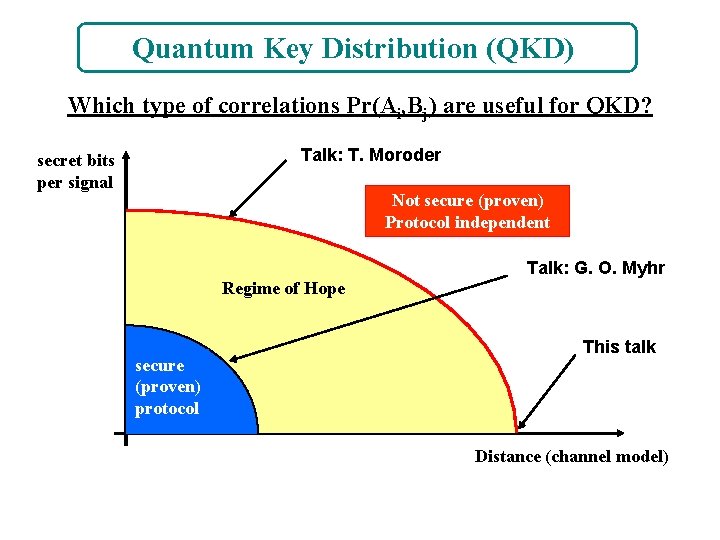
Quantum Key Distribution (QKD) Which type of correlations Pr(Ai, Bj) are useful for QKD? Talk: T. Moroder secret bits per signal Not secure (proven) Protocol independent Talk: G. O. Myhr Regime of Hope secure (proven) protocol This talk Distance (channel model)

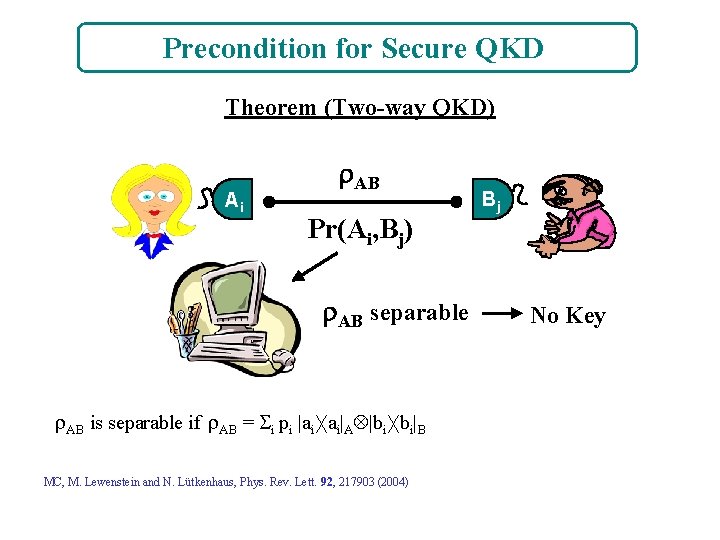
Precondition for Secure QKD Theorem (Two-way QKD) Ai AB Pr(Ai, Bj) AB separable AB is separable if AB = i pi |ai ai|A |bi bi|B MC, M. Lewenstein and N. Lütkenhaus, Phys. Rev. Lett. 92, 217903 (2004) Bj No Key

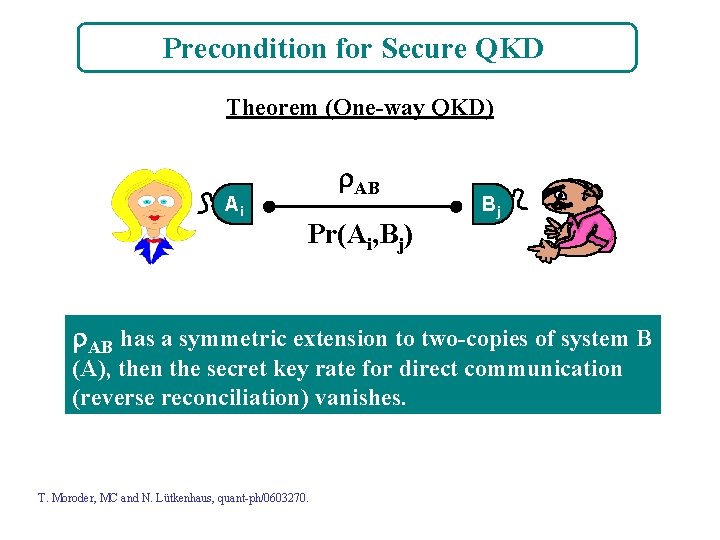
Precondition for Secure QKD Theorem (One-way QKD) Ai AB Pr(Ai, Bj) Bj AB has a symmetric extension to two-copies of system B (A), then the secret key rate for direct communication (reverse reconciliation) vanishes. T. Moroder, MC and N. Lütkenhaus, quant-ph/0603270.

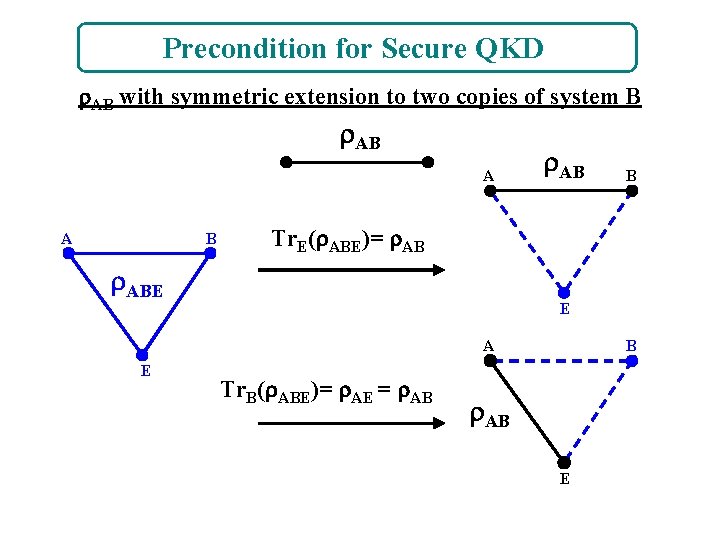
Precondition for Secure QKD AB with symmetric extension to two copies of system B AB A A B AB Tr. E( ABE)= AB ABE E A E B Tr. B( ABE)= AE = AB B AB E

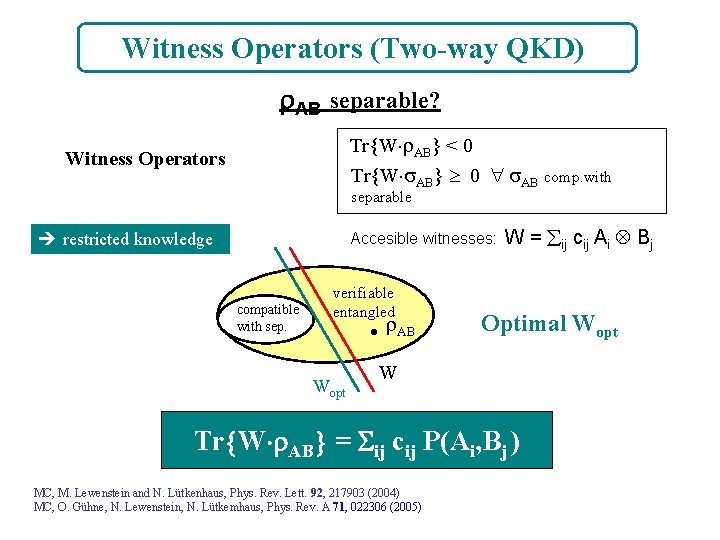
Witness Operators (Two-way QKD) AB separable? Tr W AB < 0 Tr W AB 0 AB comp. with Witness Operators separable restricted knowledge Accesible witnesses: compatible with sep. verifiable entangled • AB Wopt W = ij cij Ai Bj Optimal Wopt W Tr W AB = ij cij P(Ai, Bj ) MC, M. Lewenstein and N. Lütkenhaus, Phys. Rev. Lett. 92, 217903 (2004) MC, O. Gühne, N. Lewenstein, N. Lütkemhaus, Phys. Rev. A 71, 022306 (2005)

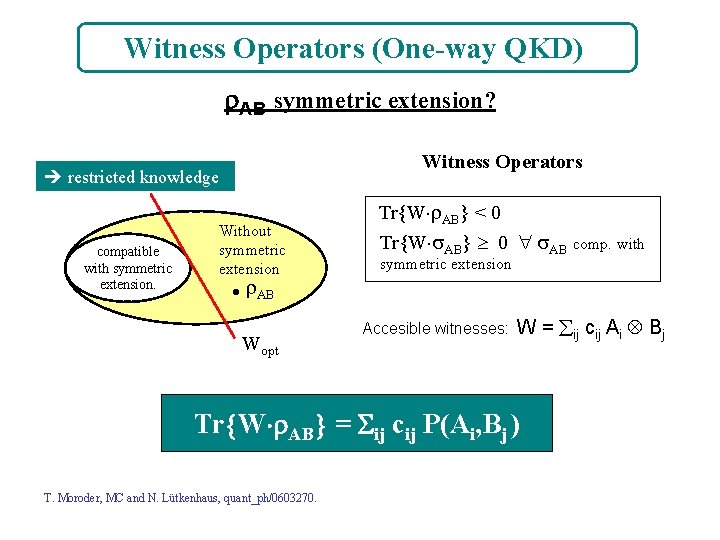
Witness Operators (One-way QKD) AB symmetric extension? Witness Operators restricted knowledge compatible with symmetric extension. Without symmetric extension Tr W AB < 0 Tr W AB 0 AB comp. with symmetric extension • AB Wopt Accesible witnesses: W = ij cij Ai Bj Tr W AB = ij cij P(Ai, Bj ) T. Moroder, MC and N. Lütkenhaus, quant_ph/0603270.

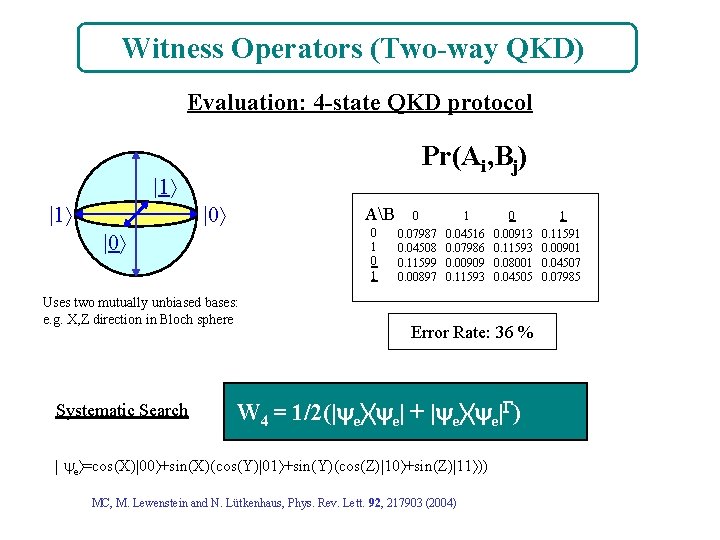
Witness Operators (Two-way QKD) Evaluation: 4 -state QKD protocol Pr(Ai, Bj) |1 |1 |0 AB 0 1 |0 Uses two mutually unbiased bases: e. g. X, Z direction in Bloch sphere Systematic Search 0 0. 07987 0. 04508 0. 11599 0. 00897 1 0. 04516 0. 07986 0. 00909 0. 11593 0 0. 00913 0. 11593 0. 08001 0. 04505 Error Rate: 36 % W 4 = 1/2(| e e| + | e e| ) | e =cos(X)|00 +sin(X)(cos(Y)|01 +sin(Y)(cos(Z)|10 +sin(Z)|11 )) MC, M. Lewenstein and N. Lütkenhaus, Phys. Rev. Lett. 92, 217903 (2004) 1 0. 11591 0. 00901 0. 04507 0. 07985

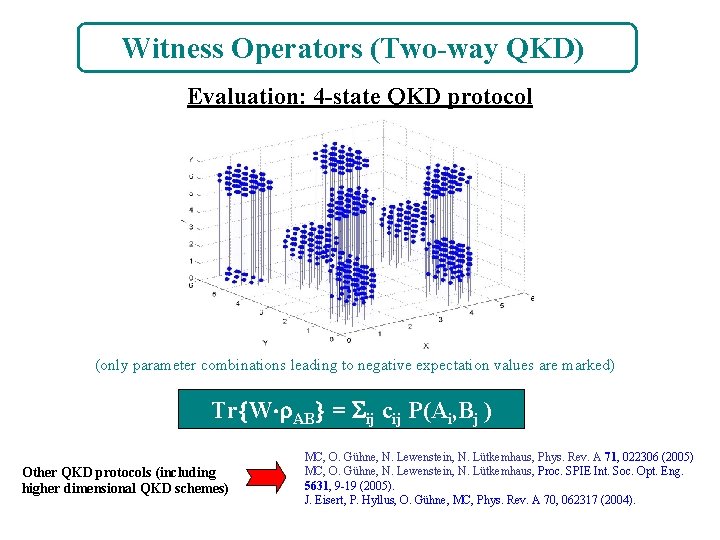
Witness Operators (Two-way QKD) Evaluation: 4 -state QKD protocol (only parameter combinations leading to negative expectation values are marked) Tr W AB = ij cij P(Ai, Bj ) Other QKD protocols (including higher dimensional QKD schemes) MC, O. Gühne, N. Lewenstein, N. Lütkemhaus, Phys. Rev. A 71, 022306 (2005) MC, O. Gühne, N. Lewenstein, N. Lütkemhaus, Proc. SPIE Int. Soc. Opt. Eng. 5631, 9 -19 (2005). J. Eisert, P. Hyllus, O. Gühne, MC, Phys. Rev. A 70, 062317 (2004).

Witness Operators (Two-way and One-way QKD) Advantages: Witnesses operators • One witness: Sufficient condition as a first step towards the demonstration of the feasibility of a particular experimental implementation of QKD. This criterion is independent of any chosen communication protocol in Phase II. • All witnesses: Systematic search for quantum correlations (or symmetric extensions) for a given QKD setup. Ideally the main goal is to obtain a compact description of a minimal verification set of witnesses (Necessary-and Sufficient). Disadvantages: Witnesses operators • How to find them? : To find a minimal verification set of EWs, even for qubit-based QKD schemes, is not always an easy task, and it seems to require a whole independent analysis for each protocol. • Too many tests: To guarantee that no secret key can be obtained from the observed data it is necessary to test all the members of the minimal verification set.

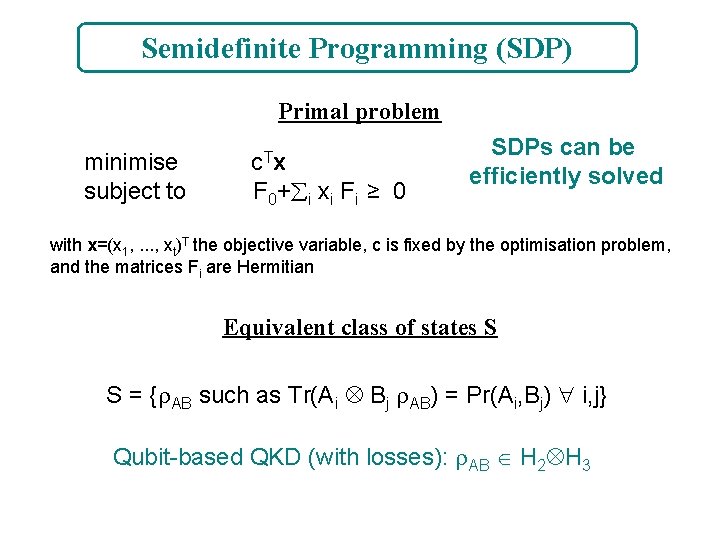
Semidefinite Programming (SDP) Primal problem minimise subject to c Tx F 0+ i xi Fi ≥ 0 SDPs can be efficiently solved with x=(x 1, . . . , xt)T the objective variable, c is fixed by the optimisation problem, and the matrices Fi are Hermitian Equivalent class of states S S = { AB such as Tr(Ai Bj AB) = Pr(Ai, Bj) i, j} Qubit-based QKD (with losses): AB H 2 H 3

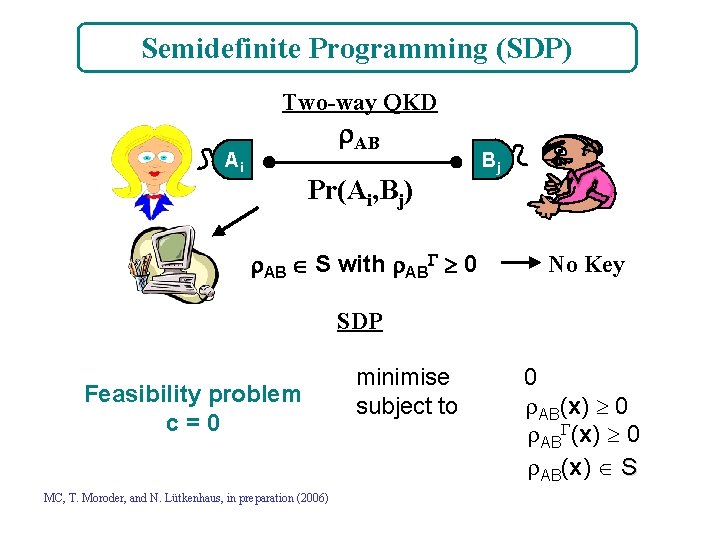
Semidefinite Programming (SDP) Two-way QKD AB Ai Pr(Ai, Bj) AB S with AB 0 Bj No Key SDP Feasibility problem c=0 MC, T. Moroder, and N. Lütkenhaus, in preparation (2006) minimise subject to 0 AB(x) 0 AB(x) S

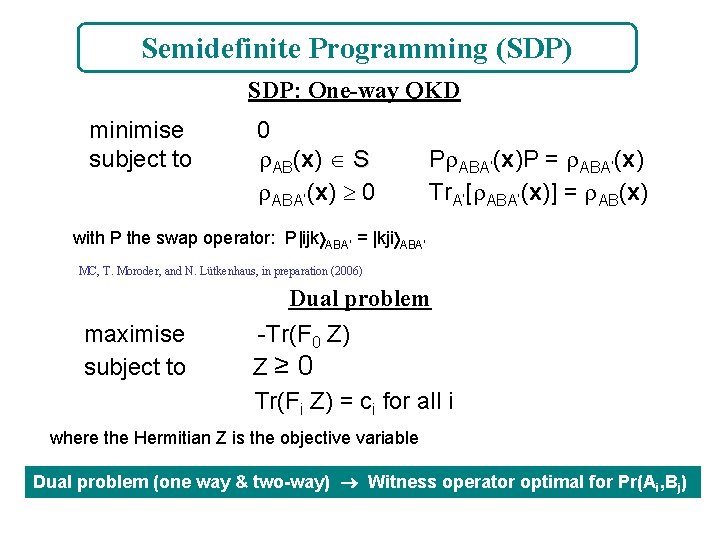
Semidefinite Programming (SDP) SDP: One-way QKD minimise subject to 0 AB(x) S ABA’(x) 0 P ABA’(x)P = ABA’(x) Tr. A’[ ABA’(x)] = AB(x) with P the swap operator: P|ijk ABA’ = |kji ABA’ MC, T. Moroder, and N. Lütkenhaus, in preparation (2006) maximise subject to Dual problem -Tr(F 0 Z) Z≥ 0 Tr(Fi Z) = ci for all i where the Hermitian Z is the objective variable Dual problem (one way & two-way) Witness operator optimal for Pr(Ai, Bj)

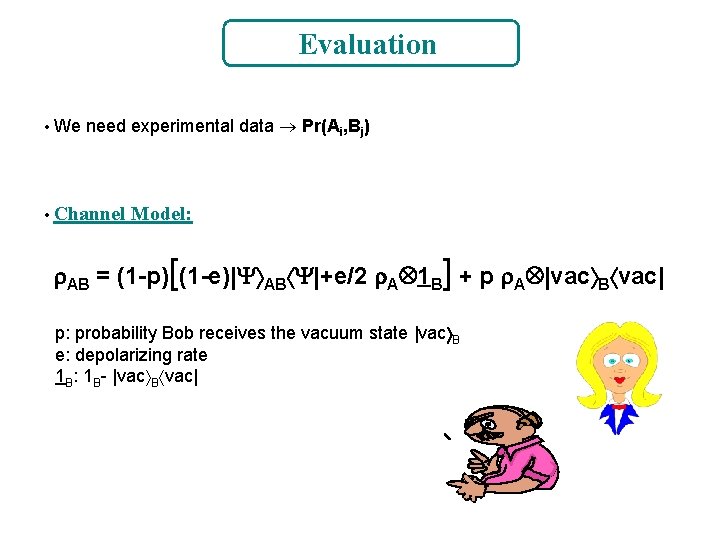
Evaluation • We need experimental data Pr(Ai, Bj) • Channel Model: AB = (1 -p)[(1 -e)| AB |+e/2 A 1 B] + p A |vac B vac| p: probability Bob receives the vacuum state |vac B e: depolarizing rate 1 B: 1 B- |vac B vac|

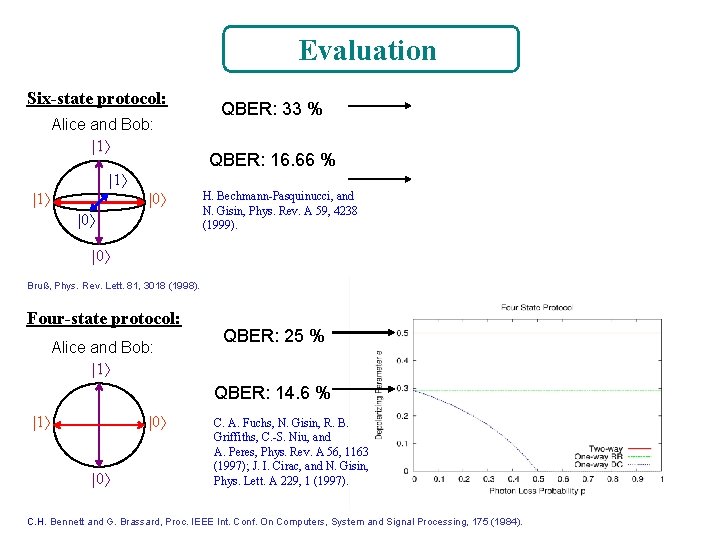
Evaluation Six-state protocol: Alice and Bob: |1 QBER: 33 % QBER: 16. 66 % |1 |1 |0 |0 H. Bechmann-Pasquinucci, and N. Gisin, Phys. Rev. A 59, 4238 (1999). |0 Bruß, Phys. Rev. Lett. 81, 3018 (1998). Four-state protocol: Alice and Bob: |1 QBER: 25 % QBER: 14. 6 % |1 |0 |0 C. A. Fuchs, N. Gisin, R. B. Griffiths, C. -S. Niu, and A. Peres, Phys. Rev. A 56, 1163 (1997); J. I. Cirac, and N. Gisin, Phys. Lett. A 229, 1 (1997). C. H. Bennett and G. Brassard, Proc. IEEE Int. Conf. On Computers, System and Signal Processing, 175 (1984).

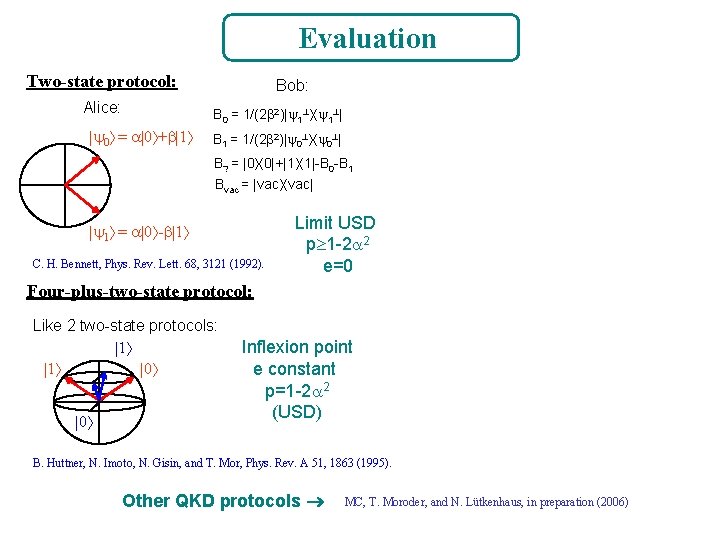
Evaluation Two-state protocol: Alice: | 0 = |0 + |1 Bob: B 0 = 1/(2 2)| 1 1 | B 1 = 1/(2 2)| 0 0 | B? = |0 0|+|1 1|-B 0 -B 1 Bvac = |vac vac| | 1 = |0 - |1 C. H. Bennett, Phys. Rev. Lett. 68, 3121 (1992). Limit USD p 1 -2 2 e=0 Four-plus-two-state protocol: Like 2 two-state protocols: |1 |1 |0 |0 Inflexion point e constant p=1 -2 2 (USD) B. Huttner, N. Imoto, N. Gisin, and T. Mor, Phys. Rev. A 51, 1863 (1995). Other QKD protocols MC, T. Moroder, and N. Lütkenhaus, in preparation (2006)

Summary Interface Physics – Computer Science: Classical Correlated Data with a Promise Necessary condition for secure QKD (Two-way & One-way). Relevance for experiments: show the presence of entanglement (states without symmetric extension) • No need to enter details of classical communication protocols • Prevent oversights in preliminary analysis • One properly constructed proof suffices Evaluation: Semidefinite programming (qubit-based QKD protocols in the presence of loss). Task for Theory: Develop practical tools for realistic experiments ( for given measurements).