NWEN 243 Networked Applications Lecture 1 Introduction to













![Basic Cryptography: Terminology ◦ Plaintext ◦ Ciphertext [Figure 2. 01 – Plaintext Sample] ◦ Basic Cryptography: Terminology ◦ Plaintext ◦ Ciphertext [Figure 2. 01 – Plaintext Sample] ◦](https://slidetodoc.com/presentation_image_h/21ea09e2829d428f7e339a40a71f3477/image-19.jpg)




- Slides: 23

NWEN 243 Networked Applications Lecture 1: Introduction to Security © 2011 -15, Kris Bubendorfer NWEN 243

Introducing the Course �NWEN 243: Networked Applications �Modern application are rarely standalone. ◦ ◦ They communicate, they coordinate, they authenticate, and users participate (user generated content (web 2. 0) ◦ Networking is everywhere �This course looks at how we build networks, and the applications that use them. �Designed as a first Networking course, with an application focus. © 2011 -15, Kris Bubendorfer NWEN 243

What you will do in NWEN 243 � The Lecture Course: 1. Security, Public Key Cryptography, Authentication and Digital Signatures. 2. Introduction to Networking, Lans, Protocols, the protocol Stack, TCP/IP and the socket API 3. Models of Networked Applications and application layer case studies: Domain Name System (DNS) and Hypertext Transport Protocol (HTTP) 4. XML and Android Application Development, Webservices, SOAP, REST. � NWEN 243 is an introductory course, so we’ll look at the general concepts rather than focus on the finest of details. © 2011 -15, Kris Bubendorfer NWEN 243

Textbook © 2011 -15, Kris Bubendorfer NWEN 243

Some thoughts… �A couple of definitions of a Network: ◦ A network is a number of computers connected together to share information and hardware. ◦ A network is a series of points or nodes interconnected by communication paths. Networks can interconnect with other networks and contain subnetworks. Q: What is the first thing you should consider when designing a networked © 2011 -15, Kris Bubendorfer NWEN 243

About this lecture �Steganography �Cryptography, and a little taste of �Security. The Enigma Machine © 2011 -15, Kris Bubendorfer NWEN 243

Secrecy in Communications: Steganography � Information has always been critical in commerce, warfare and romance. �Steganography: ◦ Steganos (covered) and graphein (to write). � Concealed Messages: ◦ Some of the earliest accounts of secret writing relate to warfare. ◦ In BC 480 the Greek Demaratus hid a message about an impending Persian invasion underneath the wax on a writing tablet. ◦ A little later a message was sent by Histaiaeus to encourage a rebellion in Persia. He tatooted message on a messenger’s scalp, which was then allowed to regrow. On arrival his head was shaved to reveal the message. ◦ The ancient Chinese wrote messages on fine silk, which was then scrunched into a tiny ball, covered with wax, and swallowed. © 2011 -15, Kris Bubendorfer NWEN 243

Secrecy in Communications � Secret Writing: ◦ 100 AD, Pliny the Elder detailed the use of the sap(milk) of the Thithymallus plant as invisible ink. Upon heating the ink turns brown. ◦ In the 16 th Century Giovanni Porta managed to conceal messages within an un-broken hard boiled egg using alum and vineager. ◦ Microdots, WWII © 2011 -15, Kris Bubendorfer NWEN 243

Steganography, but… �The problem with steganography is that if the message is intercepted – then the contents of the message are immediately revealed. �So, ‘cryptography’ was developed in parallel: ◦ Kryptos (hidden) ◦ However, the aim is not to hide the message, but rather to hide its meaning. ◦ The sender scambles a message using a agreed protocol, and then the reciever unscrambles the message with the same protocol. © 2011 -15, Kris Bubendorfer NWEN 243

Cryptography �Two main approaches: ◦ Transposition: create an anagram of the message (the letters retain their identity). ◦ Substitution: replace each letter with an alternative (the letters retain their position). © 2011 -15, Kris Bubendorfer NWEN 243

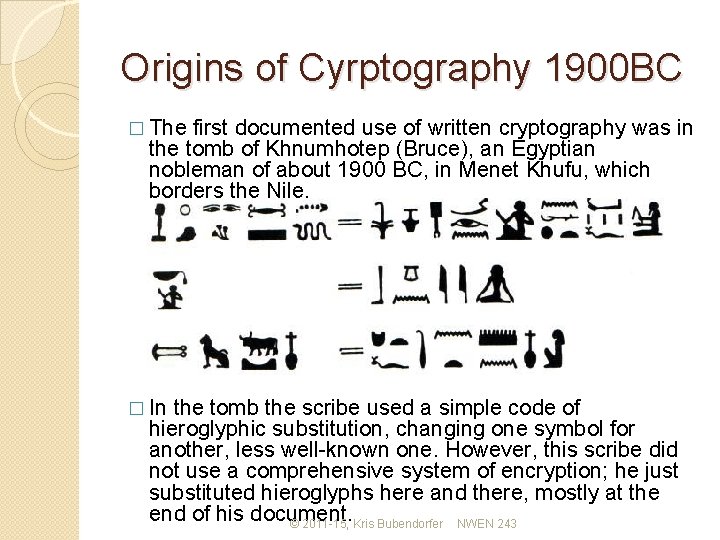
Origins of Cyrptography 1900 BC � The first documented use of written cryptography was in the tomb of Khnumhotep (Bruce), an Egyptian nobleman of about 1900 BC, in Menet Khufu, which borders the Nile. � In the tomb the scribe used a simple code of hieroglyphic substitution, changing one symbol for another, less well-known one. However, this scribe did not use a comprehensive system of encryption; he just substituted hieroglyphs here and there, mostly at the end of his document. © 2011 -15, Kris Bubendorfer NWEN 243

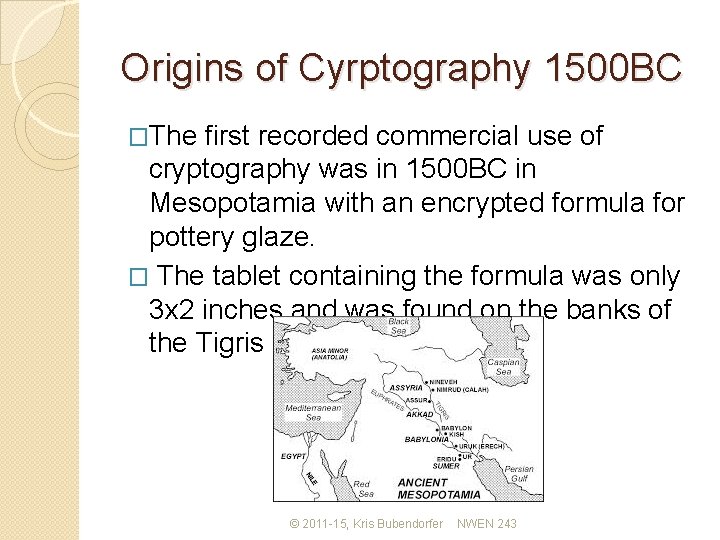
Origins of Cyrptography 1500 BC �The first recorded commercial use of cryptography was in 1500 BC in Mesopotamia with an encrypted formula for pottery glaze. � The tablet containing the formula was only 3 x 2 inches and was found on the banks of the Tigris river. © 2011 -15, Kris Bubendorfer NWEN 243

Tablet in cuneiform* � Earliest known formula for pottery glazes. � Uses cuneiform signs in their least common syllabic values to attempt to hide the secrets of the formulae. � Like George Bernard Shaw's rewriting of fish as "ghoti" � *cuneiform 1 : having the shape of a wedge 2 : composed of or written in wedge-shaped characters <cuneiform syllabary> © 2011 -15, Kris Bubendorfer NWEN 243

The Cyphers - 500 BC �The Spartans developed the first military cryptograpic device around 487 BC �A strip of papyrus or leather or parchment is wrapped around a staff of wood. ◦ The secret message is written on the parchment down the length of the staff; the parchment is then unwound and sent on its way (often hidden inside a belt steganography). ◦ To decode the message, a staff of the same size is required. ◦ This is a transposition Cypher. ◦ Called a Skytale or Scytale. © 2011 -15, Kris Bubendorfer NWEN 243

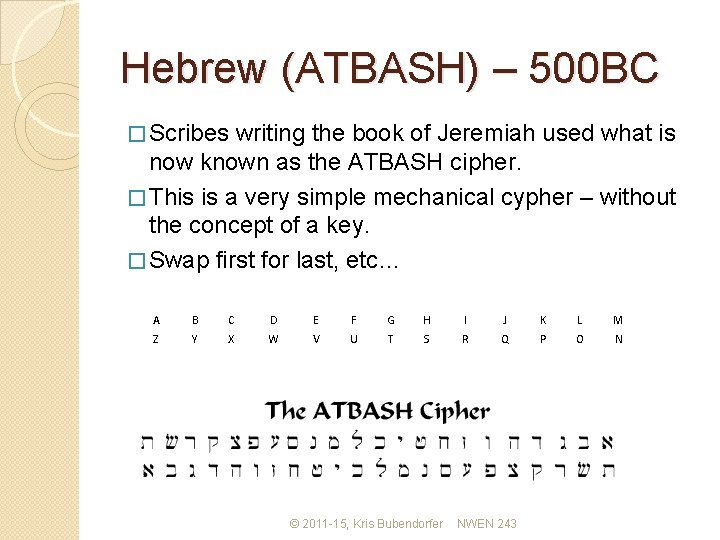
Hebrew (ATBASH) – 500 BC � Scribes writing the book of Jeremiah used what is now known as the ATBASH cipher. � This is a very simple mechanical cypher – without the concept of a key. � Swap first for last, etc… A B C D E F G H I J K L M Z Y X W V U T S R Q P O N © 2011 -15, Kris Bubendorfer NWEN 243


The Kama-Sutra The sophisticated substitution cypher (with a key) appears in the Karma-Sutra, which was in-turn based on manuscripts from BC 400. � The Karma-Sutra is much maligned – it is not a sex manual. � It is a relationship text, and recommends that women should study 64 arts – including, cooking, dressing, languages, conjuring, chess, carpentry, book binding, and secret-writing (number 45). � One of the techniques described is to construct pairs of letters at random, and then substitute each letter with its partner. � ADHIKMORSUWYZ VXBGJCQLNEFPT alice, meet you at midnight, bob vrgmu, cuuz pqe vz cgxsgibz © 2011 -15, Kris Bubendorfer NWEN 243

Caesar Cypher The first documented use of a substitution cypher for military purposes was by Julius Caesar in the Gallic wars (BC 58). � In a caesar cypher the substitution key is formed by cyclically displacing an alphabet with respect to itself (i. e, 9). � A message, called plaintext, is enciphered by substituting for each letter the corresponding letter from the shifted alphabet. � The substitution produces a new string of letters called cyphertext. � a b c d e f g h i j k l m n o p q r s t u v w x y z j k l mn o pq r s t u v w x y z a bc d e f g h i alice, meet you at the pub, bob jurln, vnnc hxd jc cqn ydk, kxk © 2011 -15, Kris Bubendorfer NWEN 243
![Basic Cryptography Terminology Plaintext Ciphertext Figure 2 01 Plaintext Sample Basic Cryptography: Terminology ◦ Plaintext ◦ Ciphertext [Figure 2. 01 – Plaintext Sample] ◦](https://slidetodoc.com/presentation_image_h/21ea09e2829d428f7e339a40a71f3477/image-19.jpg)
Basic Cryptography: Terminology ◦ Plaintext ◦ Ciphertext [Figure 2. 01 – Plaintext Sample] ◦ Key [Figure 2. 02 – Ciphertext Sample]

Basic Cryptography: Terminology ◦ Cryptosystem ◦ Cryptographer ◦ Cryptanalyst

Basic Cryptography: Services ◦ Confidentiality ◦ Integrity ◦ Authenticity ◦ Nonrepudiation ◦ Access Control

Caesar Cypher II � The Caesar cypher outlined is relatively weak, as there are only 25 possible alphabetic shifts. � This was refined to use a more sophisticated keyword or key phrase. � The advantage over a random substation (like the Kama-Sutra pairs) is that the encoding does not need to be written down and consequently subject to capture. a b c d e f g h i j k l m n o p q r s t u v w x y z j u l i s c a e r t v w x y z b d fg h km n op q alice, meet you at the park, bob jwrls, xssh pzk jh hes bjfv, uzu © 2011 -15, Kris Bubendorfer NWEN 243

What is Security? �Concealment of information ◦ existence of data is as confidential as content ◦ the existence of the file “layoffs. doc”, still imparts information – even without reading it. �Integrity ◦ Data Integrity (Data is OK) ◦ Origin Integrity (We know who did what) � Availability © 2011 -15, Kris Bubendorfer ◦ Denial of Service NWEN 243