Networked Systems Security Systems Solutions Features Learning Outcomes













- Slides: 32

Networked Systems Security Systems Solutions & Features

Learning Outcomes 1. Identify different security related hardware and software 2. Generalise different operations in security their solutions and features 3. Evaluate different based IDS & devices

Recap- Physical security measures Locks. Passes. Sign in/out systems. Guards. Biometrics.

Security Systems IDS – Intrusion Detection System Email Systems Wireless Systems Networked Devices

How do they relate to Network Security?

IDS - Intrusion Detection Systems An intrusion detection system (IDS) is an active process or device that analyses system and network activity for unauthorised entry and/or malicious activity. The ultimate aim of any IDS is to catch perpetrators in the act before they do real damage to resources.

Email Systems Security As email becomes more prolific in an organisation, the importance of email security becomes more significant. In particular, the security implications associated with the management of email storage, policy enforcement, auditing, archiving and data recovery. Another key aspect of the management of mail flow security is the protection of the business from malicious or unlawful attacks

Wireless Systems Wireless security is the prevention of unauthorised access or damage to computers using wireless networks.

Networked Devices Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorised access, misuse, modification, or denial of a computer network and network-accessible resources.

Security Features

Email Systems - Security Features Secure MIME DHCP Relay agents Wireless Systems - Security Features Site Surveys WEP/WPA TKIP

Networked Devices - Security Features Router Switch Wireless Access Points

Email Security From the time an email composed to the time it is read, an email travels through an unprotected Internet, exposed to various electronic dangers. The protection of email from unauthorised access and inspection is known as electronic privacy.

S/MIME - Secure/Multipurpose Internet Mail Extensions It is a security enhancement to the MIME Internet e-mail format standard, based on technology from RSA Data Security (RSA Security is a United States-based organization that creates encryption, network and computer security products. ) Functionality Enveloped Data: This consist of encrypted content of any type and encrypted content encryption keys for one or more recipients Signed Data: A digital signature is formed by taking the message digest of the content to be signed and then encrypting that with the private key of the signer.

DHCP Relay Agents DHCP (Dynamic Host Configuration Protocol) is a communications protocol that network administrators use to centrally manage and automate the network configuration of devices attaching to an Internet Protocol (IP) network. Relay Agent Software : - Routers block broadcasts to outer network which means responses from the DHCP servers must come from same network - DHCP relay agents intercepts IP address requests - repackages the requests - rebroadcasts them as unicast messages to DHCP servers with known addresses of other network - DHCP servers sends its reply to relay agent which in turn forwards them to client requesting the IP address


Wireless Systems Wireless networks can be applied in transportation systems, process industry, smart grids, smart buildings, personal communication and health systems.

Site Surveys Is the first step in the deployment of a Wireless network and the most important step to ensure desired operation. A task-by-task process by which the surveyor studies the facility to understand the RF behavior, discovers RF coverage areas, checks for RF interference and determines the appropriate placement of Wireless devices.

WEP/WPA WEP stands for Wired Equivalent Privacy, and WPA stands for Wireless Protected Access. WPA 2 is the second version of the WPA standard. Encryption Tools used to secure wireless connection. WEP provides security by encrypting data over radio waves so that it is protected as it is transmitted from one end point to another. WPA an improved data encryption method through the temporal key integrity protocol (TKIP). TKIP scrambles the keys using a hashing algorithm and, by adding an integrity -checking feature, ensures that the keys haven't been tampered with. http: //www. dummies. com/how-to/content/wireless-network-administration-wep-and -wpa. html

TKIP - Temporal Key Integrity Protocol Used in the encryption method WPA To increase key strength, TKIP includes four additional algorithms: A cryptographic message integrity check to protect packets A sequencing mechanism that includes hashing, as opposed to WEP's plain text transmission A per-packet key-mixing function to increase cryptographic strength A re-keying mechanism to provide key generation every 10, 000 packets.

Networked Device Security Features - Router - the first line of defense against hackers trying to access all the internetconnected devices on the network Change the default administrator password—and username, if possible Change the SSID (or name of the wireless network) so devices don't always accept connections to similarly named networks (e. g. "linksys") and also so it doesn’t give hackers more of a clue to the router model Set the wireless security mode to WPA 2 and a good, long password is needed

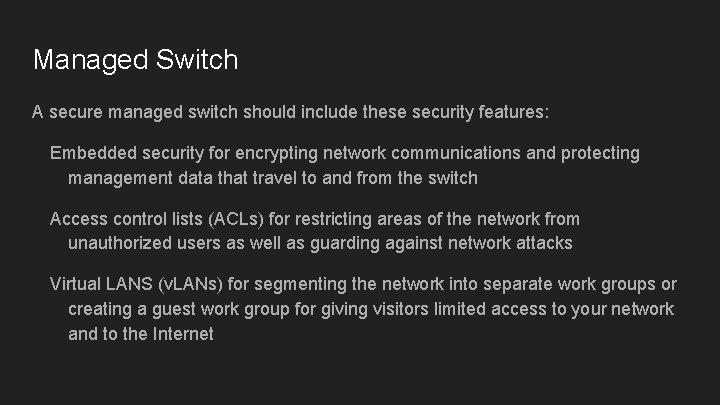
Networked Device Security Features - Switches are the foundation of a network, connecting computers, servers, printers, and other peripheral devices. There are three types of switches—unmanaged, smart, and managed. Smart and managed switches both include security features, but managed switches give you the most control over network traffic with more advanced security and features.

Managed Switch A secure managed switch should include these security features: Embedded security for encrypting network communications and protecting management data that travel to and from the switch Access control lists (ACLs) for restricting areas of the network from unauthorized users as well as guarding against network attacks Virtual LANS (v. LANs) for segmenting the network into separate work groups or creating a guest work group for giving visitors limited access to your network and to the Internet

Wireless Access Points The wireless access point connects to a wired router and then relays the data between the wireless and wired devices through the network. Access points are particularly useful to large businesses and organisations that need to connect additional desktop PCs or laptops to a network without the need for additional cabling. http: //www. practicallynetworked. com/support/wireless_secure. htm Rogue Access Points http: //www. computerweekly. com/feature/Securing-yournetworks-against-the-risk-of-rogue-wireless-access-is-no-longer-optional

Task In groups of 3 choose each choose one of the following: Email Systems Wireless Systems Networked Devices You need to explain how each one can protect a networked system.

IDS - Intrusion Detection System

Definition An intrusion can be defined as a subversion of security to gain access to a system. This intrusion can use multiple attack methods and can span long periods of time. These unauthorized accesses to computer or network systems are often designed to study the system’s weaknesses for future attacks. Other forms of intrusions are aimed at limiting access or even preventing access to computer systems or networks.

What is an IDS? Basically, intrusion detection systems do exactly as the name implies: they detect possible intrusions. More specifically, IDS tools aim to detect computer attacks and/or computer misuse and alert the proper individuals upon detection. An IDS provides much of the same functionality as a burglar alarm installed in a house. That is, both the IDS and the burglar alarm use various methods to detect when an intruder/burglar is present, and both subsequently issue some type of warning or alert

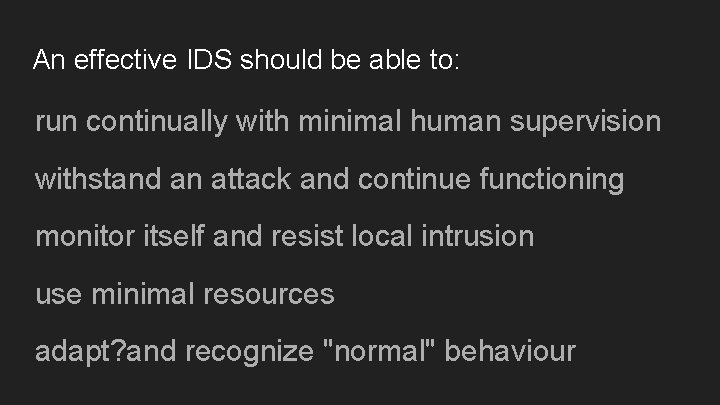
An effective IDS should be able to: run continually with minimal human supervision withstand an attack and continue functioning monitor itself and resist local intrusion use minimal resources adapt? and recognize "normal" behaviour

IDS To protect your network, your IDS must generate alarms when it detects intrusive activity on your network. Different IDSs trigger alarms based on different types of network activity. The two most common triggering mechanisms are the following: Anomaly detection Misuse detection Besides implementing a triggering mechanism, your IDS must somehow watch for intrusive activity at specific points within your network. Monitoring intrusive activity normally occurs at the following two locations: Host-based Network-based http: //www. ciscopress. com/articles/article. asp? p=25334

IDS - Similar Devices Firewalls Virus Protection Spyware protection File monitoring Folder monitoring Use of honeypots Alarms

Task - How does IDS and its different devices protect a networked system? Explain IDS and the different/similar devices, how do they secure a network? Evaluate each one and summarise the differences. Firewalls Virus Protection Spyware protection File monitoring Folder monitoring ● ● Anomaly-Based Misuse-Based Host-Based Network-Based