Module 1 Server Management in Windows Server 2012










- Slides: 25

Module 1 Server Management in Windows Server 2012

Module Overview • What's New in Server Manager • Windows Power. Shell and Server Core Enhancements • What’s New in Active Directory • Dynamic Access Control • Introducing IP Address Management

Lesson 1: What's New in Server Manager • Administering Servers with Server Manager • Adding Roles and Features

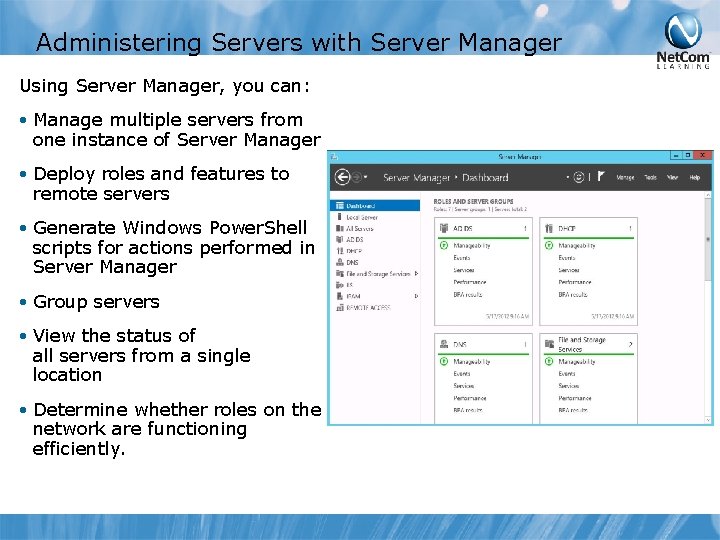
Administering Servers with Server Manager Using Server Manager, you can: • Manage multiple servers from one instance of Server Manager • Deploy roles and features to remote servers • Generate Windows Power. Shell scripts for actions performed in Server Manager • Group servers • View the status of all servers from a single location • Determine whether roles on the network are functioning efficiently.

Adding Roles and Features • Remotely deploy roles and features • Add roles and features to virtual hard disks even if the virtual machine is turned off.

Demonstration: Exploring Server Management in Windows Server 2012 In this demonstration you will: • Start the Server Manager console. • Add a server role or feature. • View role related events. • Run the Best Practice Analyzer for a role. • List the tools available from Server Manager. • Open the Start Menu. • Log off the currently logged on user. • Restart Windows Server 2012. Recorded Demo - Configuring Server Manager. wmv

POLLS

Lesson 2: Windows Power. Shell and Server Core Enhancements • Using Windows Power. Shell in Windows Server 2012 • Removing the Graphical Interface

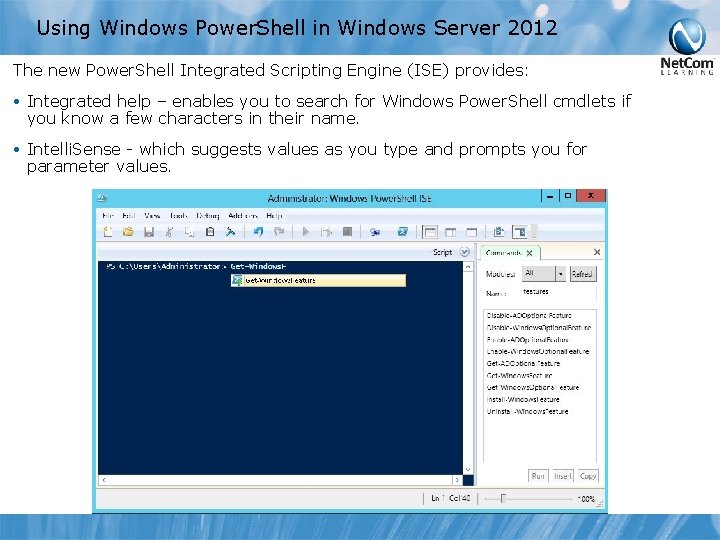
Using Windows Power. Shell in Windows Server 2012 The new Power. Shell Integrated Scripting Engine (ISE) provides: • Integrated help – enables you to search for Windows Power. Shell cmdlets if you know a few characters in their name. • Intelli. Sense - which suggests values as you type and prompts you for parameter values.

Removing the Graphical Interface • Benefits of Using Server Core § Reduced update requirements. § Reduced hardware footprint. • Graphical shell is now a feature. Can be turned off and back on again • Server Core Installation Options § Server Core. The standard deployment of Server Core. It is possible to convert to the full version of Windows Server 2012. § Server Core with Management. This works the same as a deployment of Windows Server 2012 with the graphical component, except that the graphical components are not installed

Lesson 3: What’s New in Active Directory • Key New Features • Deploying Domain Controllers • Virtualization-Safe Technology • Group Managed Service Accounts

Key New Features New features of AD DS: • New deployment methods • Simplified administration • Virtualized domain controllers • Clone a Domain Controller • Active Directory Administration Center • Active Directory module for Power. Shell • Windows Power. Shell History Viewer • Active Directory Federated Services • Active Directory Based Activation

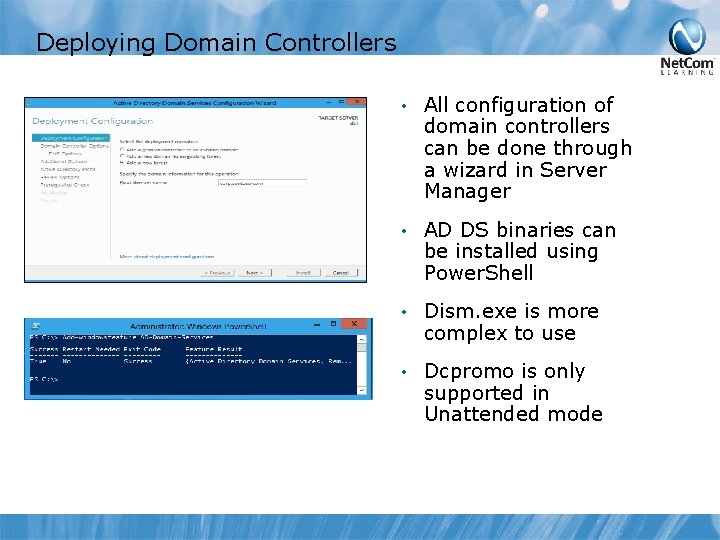
Deploying Domain Controllers • All configuration of domain controllers can be done through a wizard in Server Manager • AD DS binaries can be installed using Power. Shell • Dism. exe is more complex to use • Dcpromo is only supported in Unattended mode

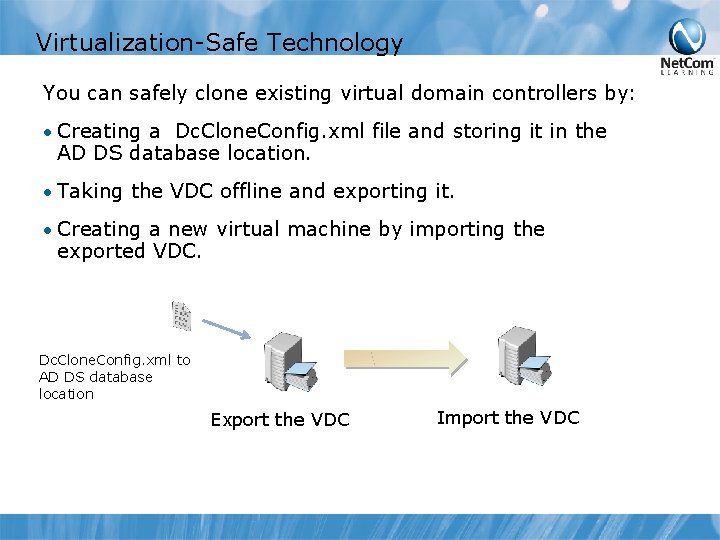
Virtualization-Safe Technology You can safely clone existing virtual domain controllers by: • Creating a Dc. Clone. Config. xml file and storing it in the AD DS database location. • Taking the VDC offline and exporting it. • Creating a new virtual machine by importing the exported VDC. Dc. Clone. Config. xml to AD DS database location Export the VDC Import the VDC

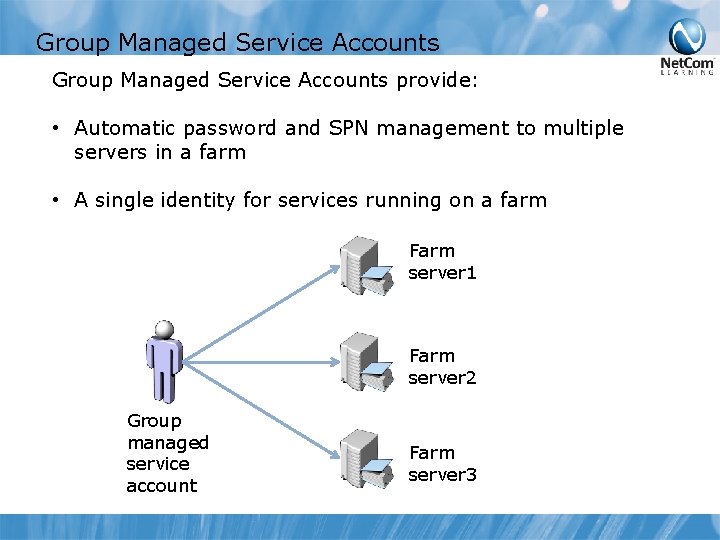
Group Managed Service Accounts provide: • Automatic password and SPN management to multiple servers in a farm • A single identity for services running on a farm Farm server 1 Farm server 2 Group managed service account Farm server 3

Lesson 4: Dynamic Access Control • Introduction to Dynamic Access Control • What are Claims? • Using Central Access Policies and Rules • Classifying Objects Using Resource Properties

Introduction to Dynamic Access Control • Dynamic Access Control provides : § Data Identification § Access Control to files § Auditing of access to files § RMS protection integration • Give users access to file system objects based on their attributes in Active Directory and the Classification of the file system object Finance

What are Claims? • Claims are statements made by AD DS about specific user or object in AD DS • AD DS in Windows Server 2012 supports : § User claims § Device claims • Can be based on existing Active Directory attributes • Typical implementation might use Department • • Department: Sales Level: 5 Site: Berlin Role: Manager

Using Central Access Policies and Rules • Central Access Rules define access based on user attributes (claims) and resource properties • Central Access Rules are grouped into Central Access Policies • Central Access Policies are pushed to file servers using group policies • A Central Access Policy has three configurable parts : § Applicability. § Access conditions. § Exception.

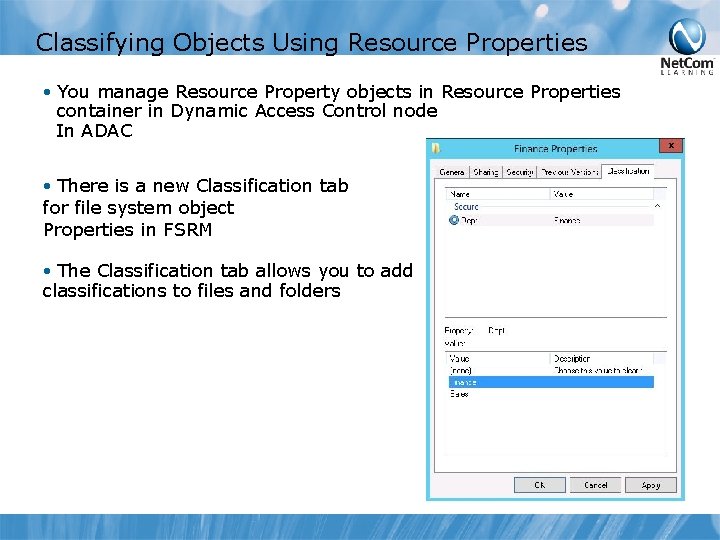
Classifying Objects Using Resource Properties • You manage Resource Property objects in Resource Properties container in Dynamic Access Control node In ADAC • There is a new Classification tab for file system object Properties in FSRM • The Classification tab allows you to add classifications to files and folders

Lesson 5: Introducing IP Address Management • Server Discovery • Address Space Management

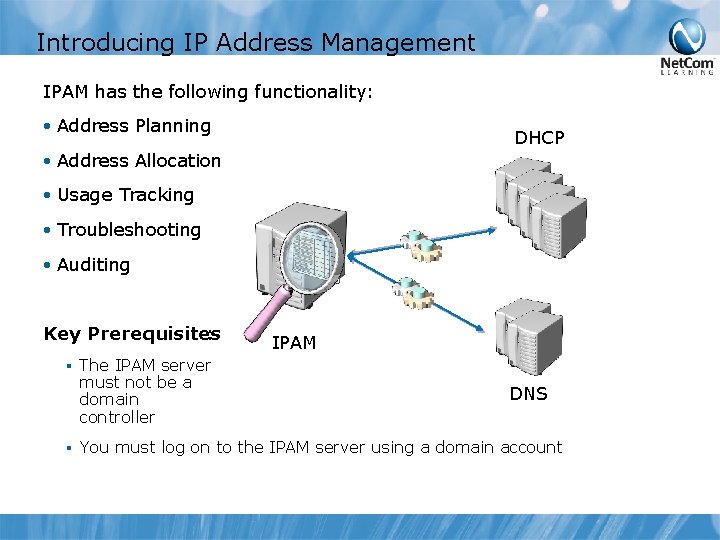
Introducing IP Address Management IPAM has the following functionality: • Address Planning DHCP • Address Allocation • Usage Tracking • Troubleshooting • Auditing Key Prerequisites : § § The IPAM server must not be a domain controller IPAM DNS You must log on to the IPAM server using a domain account

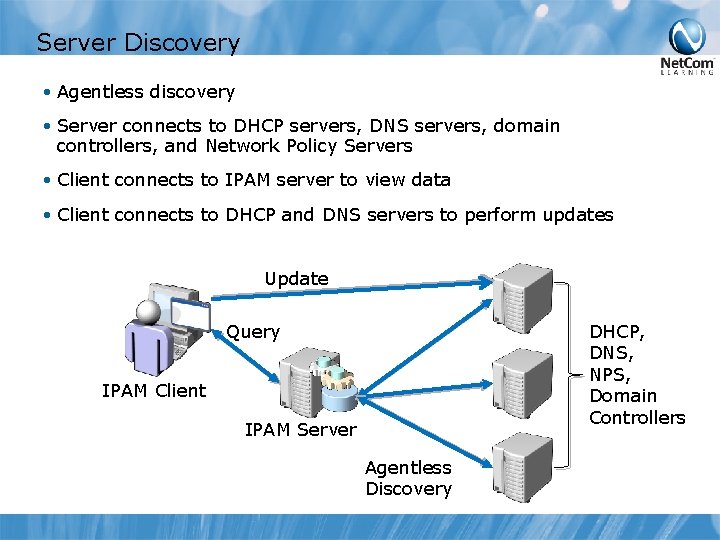
Server Discovery • Agentless discovery • Server connects to DHCP servers, DNS servers, domain controllers, and Network Policy Servers • Client connects to IPAM server to view data • Client connects to DHCP and DNS servers to perform updates Update Query DHCP, DNS, NPS, Domain Controllers IPAM Client IPAM Server Agentless Discovery

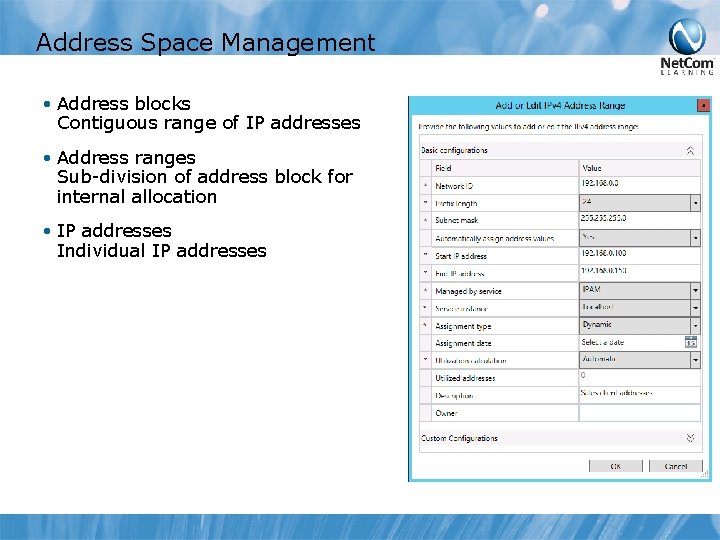
Address Space Management • Address blocks Contiguous range of IP addresses • Address ranges Sub-division of address block for internal allocation • IP addresses Individual IP addresses
