Measuring Relative Attack Surfaces Michael Howard Jon Pincus



























- Slides: 29

Measuring Relative Attack Surfaces Michael Howard, Jon Pincus & Jeannette Wing Presented by Bert Bruce

Abstract • Propose metric for measuring relative level of security of 2 systems • Base measurement is “attack opportunities” • Measured along 3 dimensions to generate an attack surface • Larger surface=>more attack opportunities => more likely a target

Limitations • Metric is relative, not absolute – Can compare 2 systems • Restrictions – Same environment – same capabilities – i. e. 2 releases of same system

Goal • Measure if a new release of a system has improved its security

Motivation • Building on previous work of one of the authors – He defined 17 attack vectors – Defined Relative Attack Surface Quotient (RASC) • Current paper adds 3 attack vectors • Compute RASQ for 5 versions of Windows • Claim relative security levels agree with anecdotal evidence

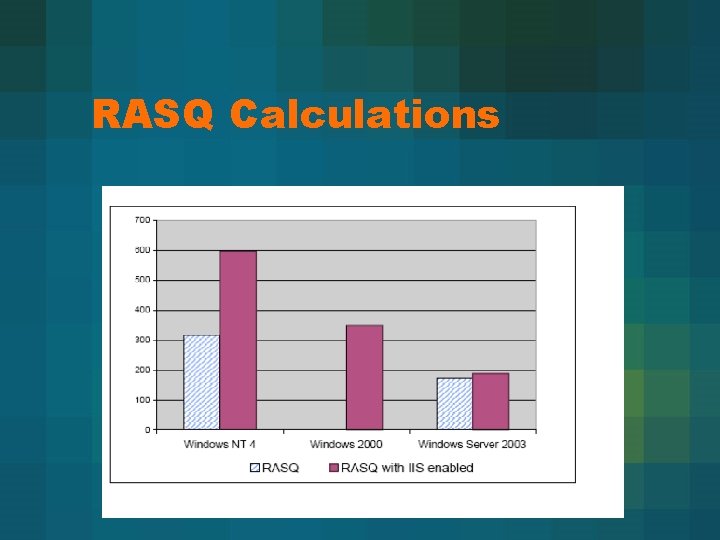
RASQ Calculations

Attackability • Proposed unit of measurement for security • Higher level than bug count • Lower level than count of system vulnerabilities reported in bulletins and advisories

Attackability • Define 3 dimensions to measure – Targets and Enablers – Channels and Protocols – Access Rights • From these create system’s Attack Surface

System Model • System to be measured and environment modeled as Finite State Machines • 3 Key terms – Vulnerability – weakness in design, implementation or operation – Attack – exploit the vulnerability – Threat – the adversary doing the attack

State Models • Think of System as FSM with states, initial states and transitions • Threat modeled the same way • Create new FSM out of union of System and Threat

State Models • The attacker has Goal States of the System he wants to obtain • We want to defines the system FSM so Goal States can’t be reached

Vulnerabilities • Look at 2 System FSMs – Intended machine (I) & Actual machine (A) • Behaviors = set of execution sequences of an FSM • Vulnerabilities = Behavior(A) – Behavior(I) – Note: Set difference

Vulnerabilities • (States of A – States of I) not empty => unintended states • (Initial states of A - Initial states of I) not empty => we can start actual system where we shouldn’t

Vulnerabilities • (Action set of A – Action set of I) not empty => A can have unexpected behavior • (Transition set of A – Transition set of I) not empty => A can have unintended transitions

Attack • A sequence of action executions which include vulnerabilities and which leads to attacker’s Goal State

Dimension #1 Targets and Enablers • Target – part of system to be controlled • Enabler – part of system providing means for attack – Evaluator – runs attacking code – Carrier – embeds attacking code

Dimension #2 Channels and Protocols • How attacker gets into the system • Channel – Message passing – Shared memory • Protocol – rules for message passing

Dimension #3 Access Rights • Accounts – How many individual, admin, guest • Trust Relationships – Among users and processes • Privilege Level • Reducing the dimension = Principal of Least Privilege

Example • Use actual MS Security Bulletin • Provide template for describing Vulnerabilities and Attacks – Vulnerabilities: describe intended and actual pre and post conditions – Attacks: describe goal, resources, preconditions, attack sequence, postconditions

Example • Use of the preceding model: – Some use of FSM transitions in Vulnerability description – Resources described in terms of the three dimensions

Attack Surface • Some complex function of the 5 components of the dimensions • Authors punt on specific function • Instead they suggest reducing it by: – Reducing values of dimensions – Reducing vulnerabilities (Intended - Actual) – Reduce types of attacks (better technology)

Attack Surface Metric • List 20 attack vectors • Examples: – Open port – Services running as SYSTEM – Active. X enabled

Attack Surface Metric Calculation • Each vector given a weight • “Surfaces” are calculated for 4 vector types – Channels – Process Targets – Data Targets – Process Enablers

Attack Surface Metric Calculation • Each surface is sum of weights of each type of vector • Total surface is sum of these 4 • I assume this is the RASQ (they don’t make an explicit connection) • Values of weights are not explained

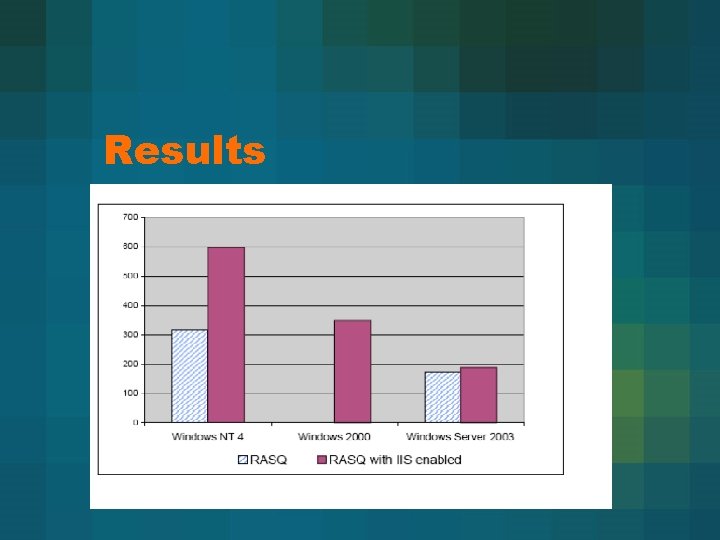
Results

Results • Win NT with IIS is much less secure than without it • Win Server 2003 doesn’t lose much security with IIS on • Relative security of 3 seems to match the order shown

Analysis of RASQ • Can’t apply if systems are different – RASQ isn’t absolute metric – Doesn’t measure over time as features or configurations change – Certainly doesn’t apply to different operating systems • Should focus more on individual attack vectors than a single number

Presenter’s Comments • A relatively simple idea dressed up in elegant mathematical clothing • Formalizes stuff we already know – Formalization can obfuscate the obvious • Confusing point: start with 3 dimensions based on 5 factors and end up with 4 surface categories

Presenter’s Comments • “Surface” => area => product of dimensions – Not done here • More like each term adds a “pixel”, a small patch, to a surface to form total area • Or each term pokes hole in surface dimension to increase porosity