Managing Operations Outline 1 What Are Operations 2























- Slides: 47

Managing Operations

Outline 1 What Are Operations? 2 Outsourcing IS Functions 3 Information Security

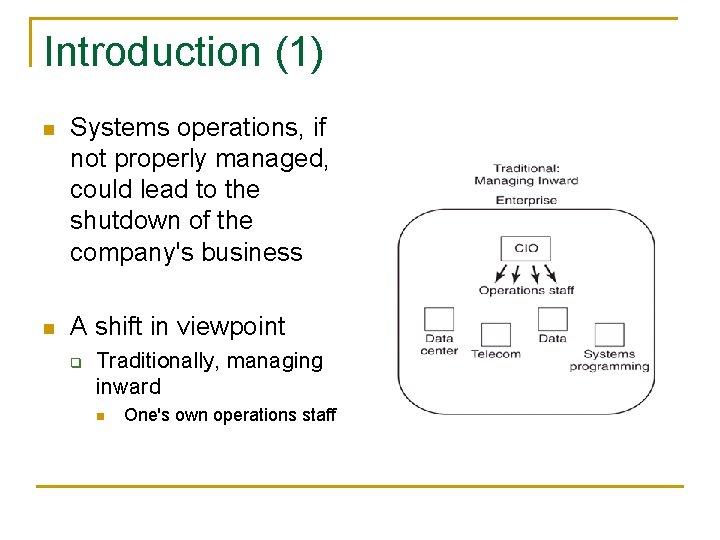
Introduction (1) n Systems operations, if not properly managed, could lead to the shutdown of the company's business n A shift in viewpoint q Traditionally, managing inward n One's own operations staff

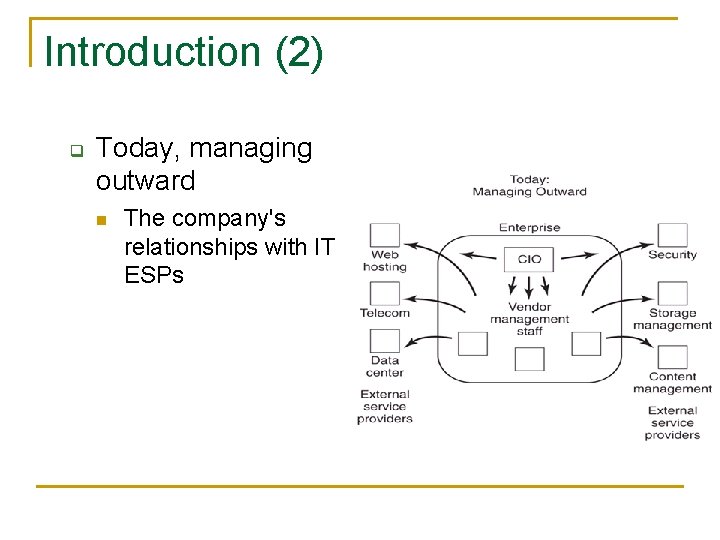
Introduction (2) q Today, managing outward n The company's relationships with IT ESPs

Why Emphasizing Operations? n A Typical MIS Department Budget: q 33% Systems and Programming n n q q 70% Maintenance 30% New Development 10% Administration and Training 57% Operations n n Involve more money than any other part of the IS department Very involved (difficult), challenging and rewarding area

Solving Operational Problems n Three strategies to improve operations: q q q Buy more equipment Continuously fight fires and rearrange priorities Continually document and measure what you are doing n Find out the real problems, not just the apparent ones. Then set standards and manage to them.

Operational Measures n External measures q What the customer sees, relating to customer satisfaction n n Internal measures q Of interest to IS people n n System and network uptime, response time, turnaround time, program failures Computer utilization as percentage of capacity, disk storage used etc. Problems reported by external measures can be explained by deviations in internal measures

The Importance of Good Management n Skills of an operations manager is similar to that needed in e. g. a factory q n Only here the "factory equipment" is the disk drives, DB servers, network gateways etc The key to managing operations is the same as in any management job q q Set standards Then manage to those standards by finding an outstanding operations manager

What’s New in Operations? n Companies have "cleaned their operational house" q n More operations managers are managing outward q q n Y 2 K problem moved company from a survival mode to a planning mode CIOs does not relinquish responsibility for operations Ensure their people are properly managing relationships Operations are being "simplified" q Centralizing applications in one place rather than distribute them on PCs n n Server based computing Certain operations are being offloaded q e. g. Microsoft offloaded webcasts to Netpodium

Outline 1 What Are Operations? 2 Outsourcing IS Functions 3 Information Security

Outsourcing IS Function n Outsourcing means turning over a firm's computer operations, network operations, or other IT function to a vendor for a specified time n The focus of CIOs in operations is changing q q In the past, ensuring they had the in-house expertise to keep systems and networks up and tuning Now, determining where best to perform the various kinds of operations n In house or with a third party and manage it accordingly

The Driving Forces Behind Outsourcing n 70% of US economy had global competition in 1970 s q q n Companies had to focus on core business, which led to huge amount of merger and acquisition activity Companies were priced based on their shareholder value Focus and value q Management must stress value, they must consider outsourcing in all their nonstrategic functions

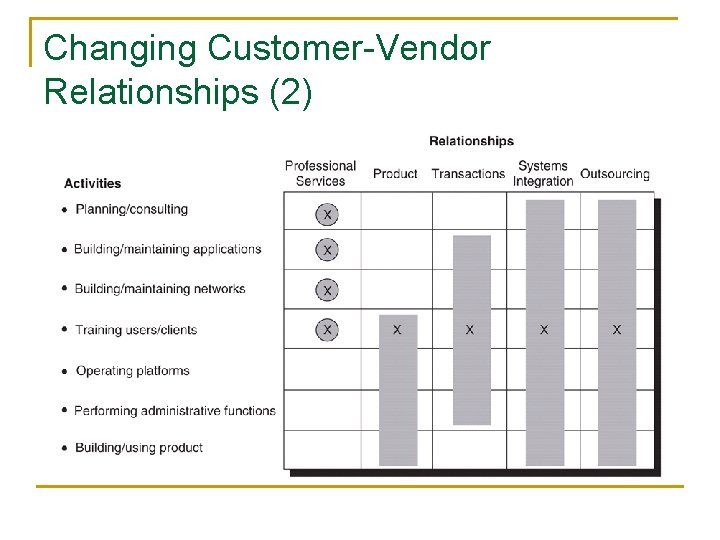
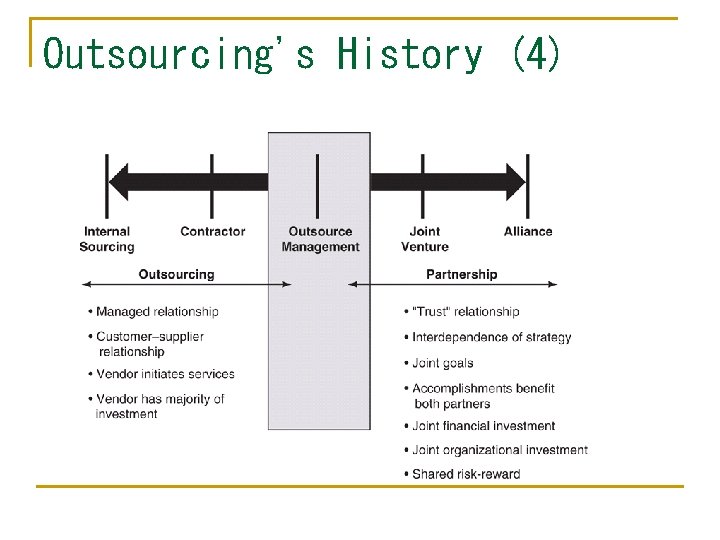
Changing Customer-Vendor Relationships (1) n n Relationships have expanded from buying professional services, to buying products and transactions, to integrating systems, to outsourcing In this evolution: q q IS management has increasingly lost control Providers take on more risks Provider's margins increase Choosing the right provider becomes more important

Changing Customer-Vendor Relationships (2)

Outsourcing's History (1) n In 1989 only full IT outsourcing was available q q q Essentially began with "big-bang" deals. The goal was purely financial. Problems occurred n n q Us VS them Culture clash Until that time, companies only outsourced poorly run IS operations n Kodak outsourced its well-run IS operations in 1989 to become a more competitive company

Outsourcing's History (2) n Early 1990 s: transitional outsourcing q One of two routes in outsourcing n n n Maintenance of their legacy systems, hence staff concentrated on building new client server systems C/S development to specialists & kept maintenance of legacy systems in-house Mid to late '90 s: best-of-breed outsourcing q q Selective outsourcing began "Collaborative outsourcing": one prime contractor and some secondary external service providers

Outsourcing's History (3) n Shared services q q n "In-sourcing" to an internal shared service group Improved efficiencies & saved money (scale of economy) Business Process Outsourcing (BPO) q q q As IT outsourcing matured it became a commodity service, profit margins dropped and competitors rose ESPs moved to specific functional areas with higher margins Handling specific business processes as well as their IT underpinnings: BPO

Outsourcing's History (4)

Outsourcing's History (5) n E-business outsourcing q q With the arrival of business use of the Internet, outsourcing has been one way that companies can quickly get Websites up and handling business In dot-coms and Internet-based operations, outsourcing all or most of the IS function has been preferred mode of operation n Allows a company to move faster Companies can remain flexible Do not tie up a firm's funds in computer and networking equipment

Outsourcing's History (6) n Utility Computing q q Also known as on-demand computing, virtual data centers and grid computing The idea is computing power can be treated like electricity: You plug in and only pay for what you use n n Numerous vendors, especially IBM, HP and Sun are promoting access rather than ownership Turning clients' fixed IT costs into variable costs

Managing Outsourcing n Numerous aspects to managing outsourcing need to be handled well to create a successful working relationship q q Organizational structures Governance Day-to-day working Supplier development

Organizational Structure n Managing outsourcing is different from managing internal staff q n It is a joint effort between parties that may not have the same goals Typically, parties establish layers of joint teams q q q Top-level team: final word in conflict resolution Operational team: oversees day-to-day functioning Joint special purpose teams: created from time to solve pressing issues Standing committees: oversee the use of formal change management procedures Relationship managers: look after the "relationship"

Governance n The foundations of governing an outsourcing relationship are laid in the (LARGE) contract(s) q Service Level Agreement (SLA) n n n Responsibilities, performance requirements, penalties, bonuses Another important component of SLAs is metrics. An SLA needs to be measurable to be of use Most parties in strong relationships put the contract in the drawer and work from trust and agreed-upon rules q It is only when trust in one another breaks down that they turn to the contract

Day-to-day Working n Recommendations to manage day-to-day interactions: q Manage expectations, not staff n q q Facilitation becomes the mode of working Realize that informal ways of working may disappear Loss of informal ways of working may add rigor Integration of the two staffs requires explicit actions The best way to manage day-to-day is communicate frequently n Preferably "face to face"

Supplier Development n A topic that is receiving increased attention q q Buying parts and services that go into one's own products and services Assisting one's suppliers to improve their product and services by generally improving their processes

Offshoring n Offshore outsourcers became a desirable choice in late 1990 s q q A tight labor market due to Y 2 K Lower cost and an ample supply of educated people n n India, Ireland, Philippines, China White-collar work going offshore q Application maintenance and development, call centers, customer service, back office processing, BPO, claims processing etc.

Outline 1 What Are Operations? 2 Outsourcing IS Functions 3 Information Security

Information Security Management --- A Definition n Information security management defines the controls we must implement to ensure we sensibly manage computer related risks q q Not just technology, but people and processes too An ongoing, continuous activity, you don't just "do" security as a one-off event

Information Security Management ---A Growing Concern n Today even CEOs need to know something about information security q n Need to understand Internet-based threats and countermeasures and continuously fund security work to protect their businesses Since 1996 the Computer Security Institute (CSI) and FBI have conducted an annual survey of US security managers

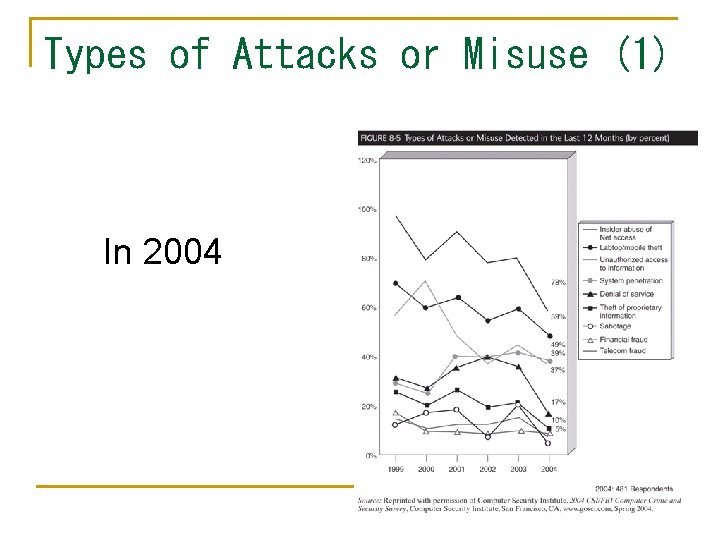
Types of Attacks or Misuse (1) In 2004

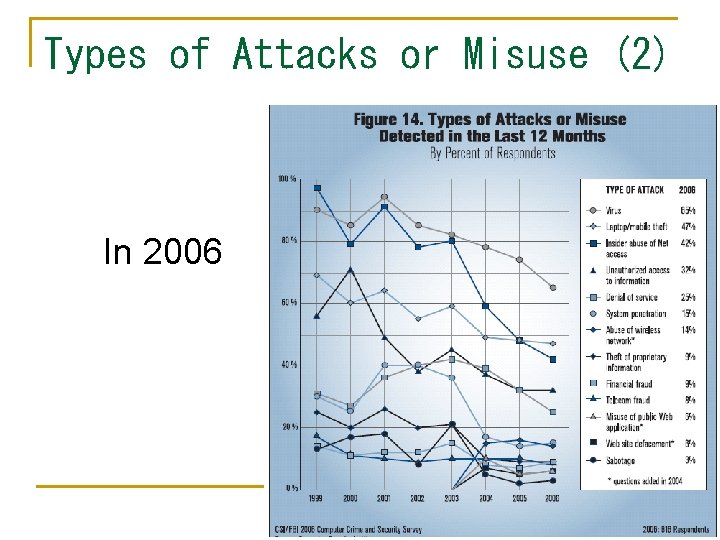
Types of Attacks or Misuse (2) In 2006

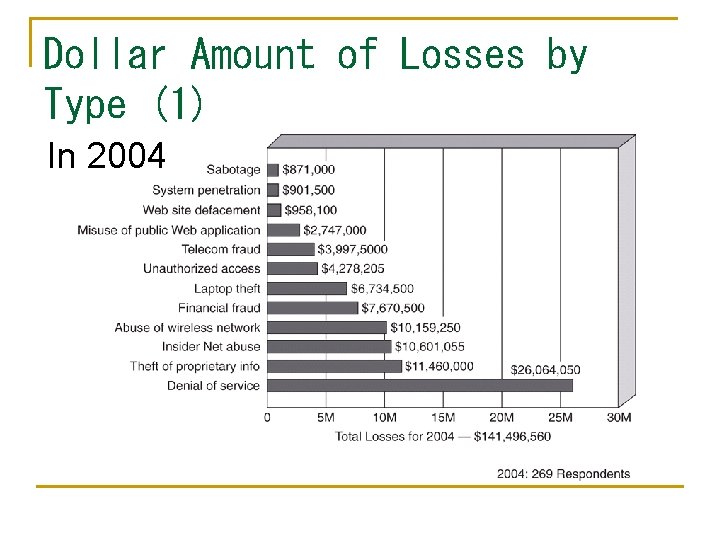
Dollar Amount of Losses by Type (1) In 2004

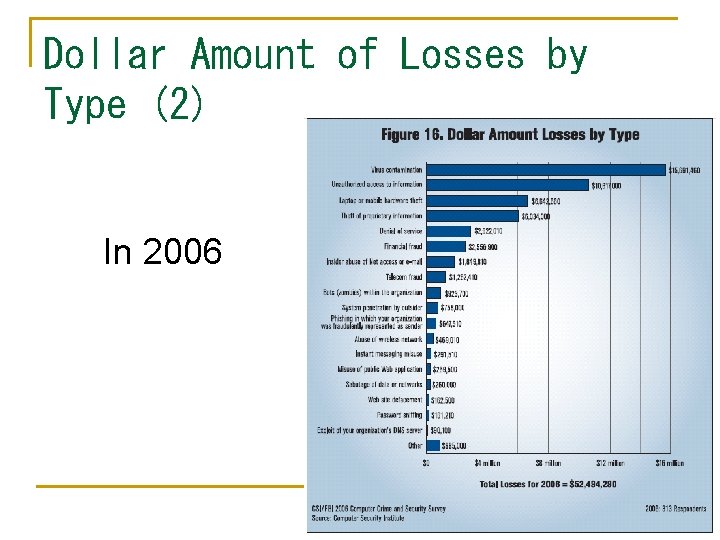
Dollar Amount of Losses by Type (2) In 2006

The Threats---Hackers n n The 'hacker community' has become a 'public club' Approaches hackers use: q q q q q Cracking the password Tricking someone Network sniffing Misusing administrative tools Playing middleman Denial of service Trojan horse Viruses Spoofing

Security's Six Pillars n A secure system should provide: q q q Nonrepudiation – a transaction cannot be denied by any of the parties to it Confidentiality – data or services are protected from unauthorized access Integrity – data or services are delivered as intended Assurance – (authentication) the parties to the transaction are who they say they are Availability - the system will be available for legitimate use; no DOS. Auditing – the system tracks activities within it at levels sufficient to reconstruct them

Security---Technical Countermeasures n Security tactics can be divided into three groups q Resisting attacks n q Detecting attacks n q (locking your doors) (having a motion detector) Recovering from attacks n (having homeowner's insurance)

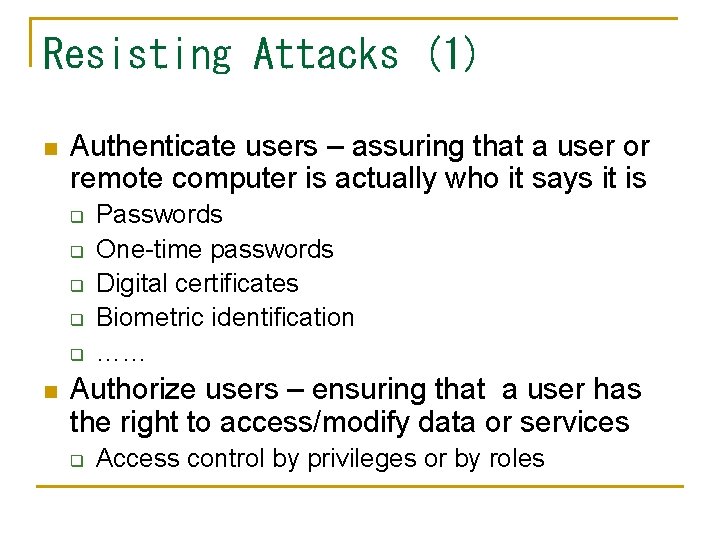
Resisting Attacks (1) n Authenticate users – assuring that a user or remote computer is actually who it says it is q q q n Passwords One-time passwords Digital certificates Biometric identification …… Authorize users – ensuring that a user has the right to access/modify data or services q Access control by privileges or by roles

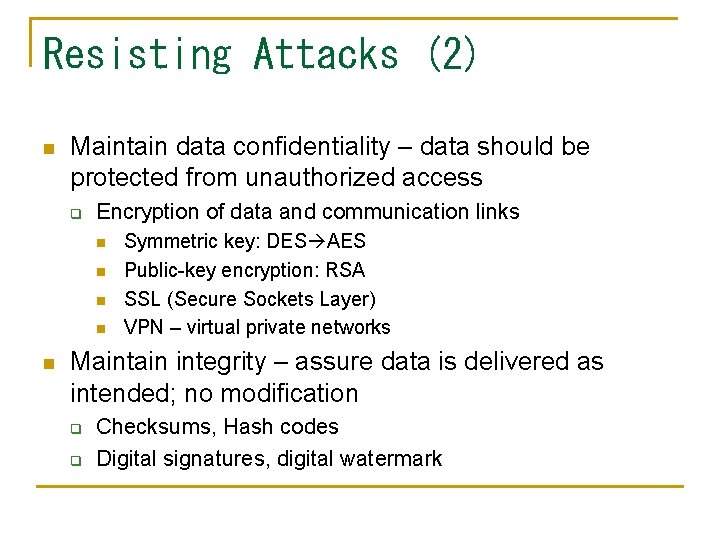
Resisting Attacks (2) n Maintain data confidentiality – data should be protected from unauthorized access q Encryption of data and communication links n n n Symmetric key: DES AES Public-key encryption: RSA SSL (Secure Sockets Layer) VPN – virtual private networks Maintain integrity – assure data is delivered as intended; no modification q q Checksums, Hash codes Digital signatures, digital watermark

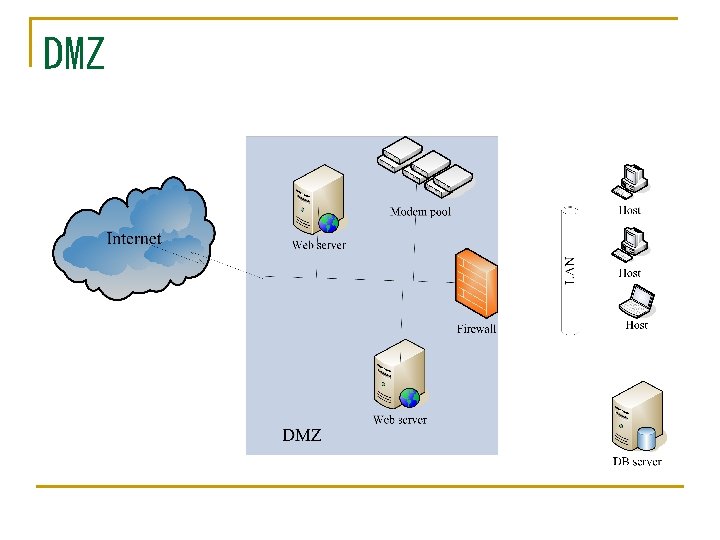
Resisting Attacks (3) n Limit exposure q Attacks typically exploit a single weakness on a host to get access to all of its data n n The architecture can minimize risk by allocation of services/data to hosts to limit exposure on each host Limit Access q Firewalls (source, destination port) n But it is not always possible to limit access to known sources. q q e. g. a public Web site. DMZ – demilitarized zone; access to web but not to the rest of the LAN

DMZ

Virtual Private Networks (VPN) n Maintains data security as it is transmitted by using: q q Tunneling: creates a temporary connection between a remote computer and the CLEC's or ISP's local data center. Blocks access to anyone trying to intercept messages sent over that link Encryption: scrambles the message before it is sent and decodes it at the receiving end

Detecting Attacks n Detection of attacks typically either done manually or with the help of an intrusion detection system (IDS) q Typically compare the patterns of network traffic to historical patterns to identify problems n q E. g. Denial of Service attacks (DOS) The packets must be filtered to make comparison: on IP addresses and ports, TCP flags, packet sizes

Recovering from Attacks n Tactics to restore data and system: q Restoring data n n n q Backups Passive redundancy (from availability) Checkpoints (again) Attacker identification n Audit trails for q q q Rolling back to checkpoint Help identify intruder and support non-repudiation Should be protected/hidden

The Balance Between Security and Risk n n Information Security is a balancing act between ease of access to information and protecting that information from increasing threats The Information Security Manager must q q q Constantly bear in mind the organization's appetite for risk Assess where the "appropriate" balance lies Be prepared to press their case "strenuously" when they believe the risk is not within acceptable bounds.

Planning for Business Continuity n Business continuity is broader than disaster recovery, it includes q q q n Safeguarding people during a disaster Documenting business procedures Giving employees the tools and space to handle personal issues first so that they can then concentrate on work In short, it is a business issue and IT disaster recovery is just one component

Using Internal Resources n Organizations that rely on internal resources for IT disaster recovery generally see this planning as a normal part of systems planning and development q Multiple data centers n q q q Do not have all computing in one location Distributed processing Backup telecommunication facilities Local area networks n Servers on one LAN can be used to backup servers for other networks

Using External Resource n Cost Vs. risk may not justify permanent resources so companies use the services of a disaster recovery firm q q q Integrated disaster recovery services Specialized disaster recovery services Online and off-line data storage facilities