Janus Optimizing Memory and Storage Support for Non






- Slides: 26

Janus Optimizing Memory and Storage Support for Non -Volatile Memory Systems Sihang Liu Korakit Seemakhupt, Gennady Pekhimenko, Aasheesh Kolli, and Samira Khan

BACKGROUND • The new non-volatile memory (NVM) is • High-speed • Persistent • Byte-addressable Intel 3 D XPoint • NVM allows program to manipulate persistent data in memory through a load/store interface • Different from conventional DRAM, NVM is both Memory and Storage A practical NVM system requires both memory and storage support

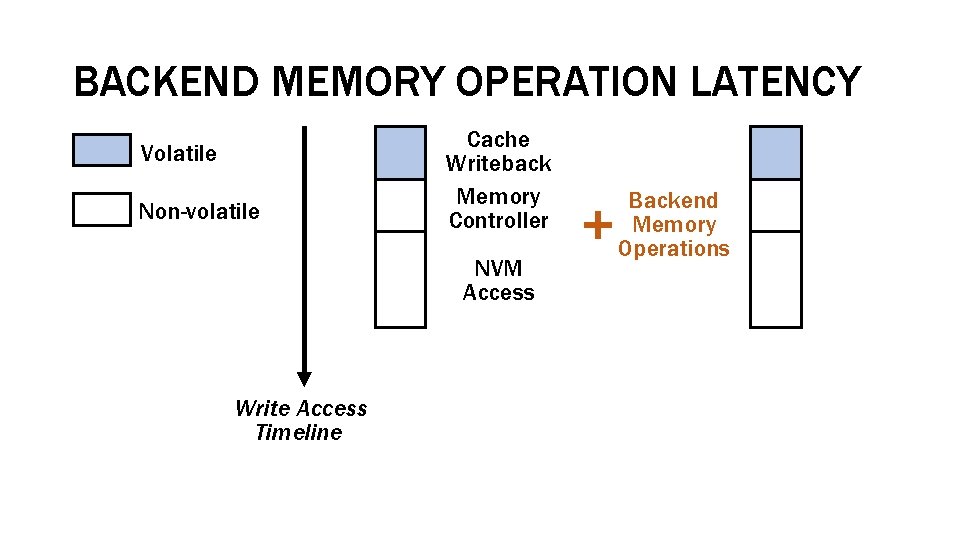
MEMORY AND STORAGE SUPPORT These supports are designed for Security Prevent attackers from stealing or tampering data Encryption, integrity verification, etc. Bandwidth Improve NVM’s limited bandwidth Deduplication, compression, etc. Endurance Extend NVM’s limited lifetime Wear-leveling, error correction, etc. We refer to these memory and storage supports as backend memory operations

BACKEND MEMORY OPERATION LATENCY Cache Writeback Memory Controller NVM Access Write Access Timeline

BACKEND MEMORY OPERATION LATENCY Volatile Non-volatile Cache Writeback Memory Controller NVM Access Write Access Timeline Backend Memory Operations

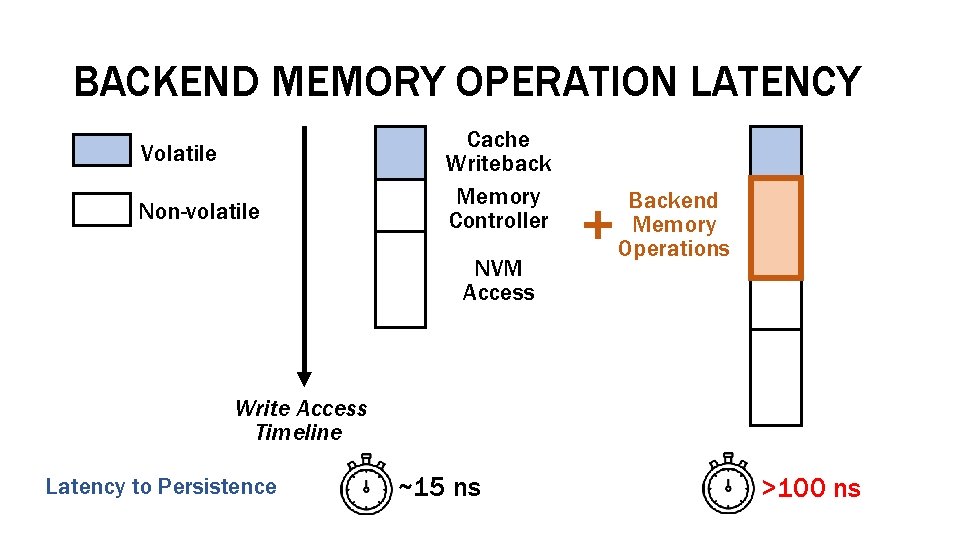
BACKEND MEMORY OPERATION LATENCY Volatile Non-volatile Cache Writeback Memory Controller NVM Access Backend Memory Operations Write Access Timeline Latency to Persistence ~15 ns >100 ns

Why is write latency important?

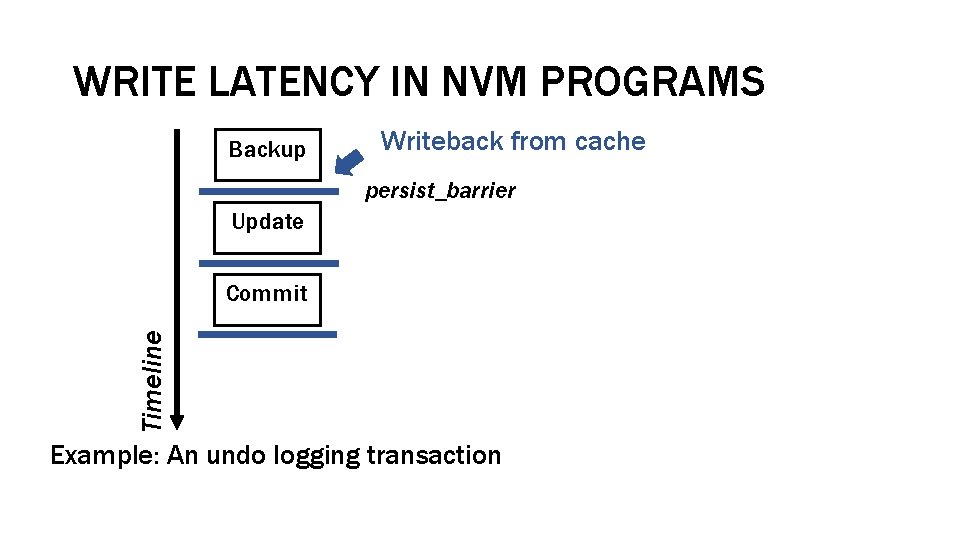
WRITE LATENCY IN NVM PROGRAMS Backup Writeback from cache persist_barrier Update Timeline Commit Example: An undo logging transaction

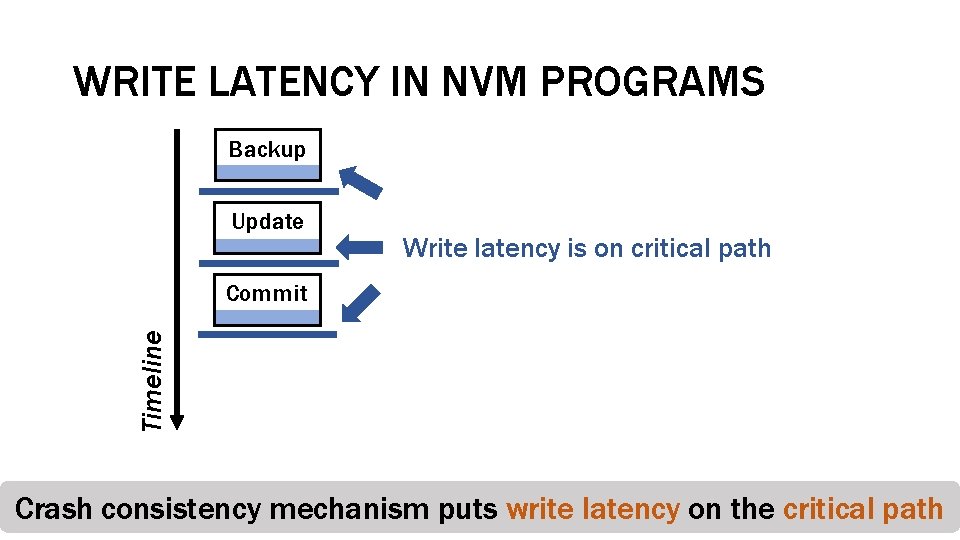
WRITE LATENCY IN NVM PROGRAMS Backup Update Write latency is on critical path Timeline Commit Crash consistency mechanism puts write latency on the critical path

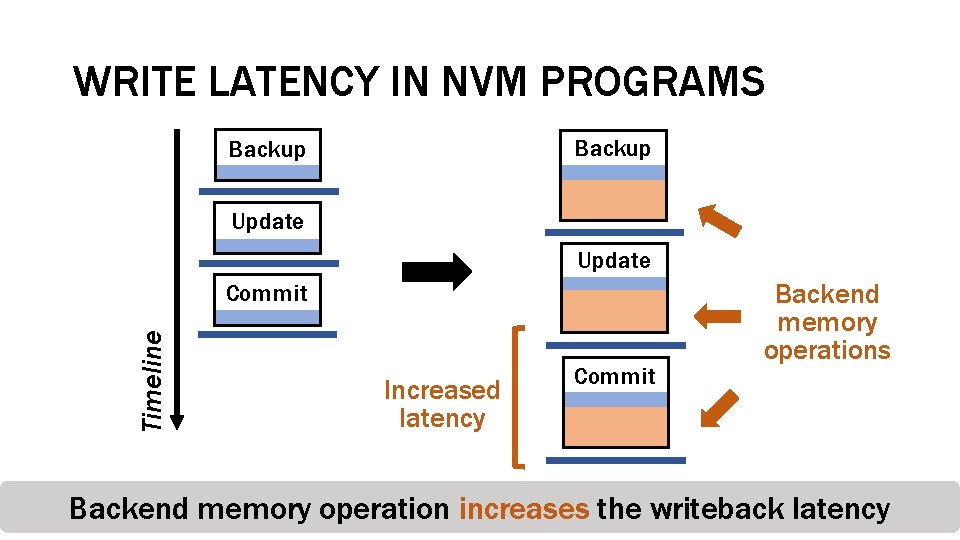
WRITE LATENCY IN NVM PROGRAMS Backup Update Timeline Commit Increased latency Commit Backend memory operations Backend memory operation increases the writeback latency

Backend memory operations are on the critical path, How to reduce the latency?

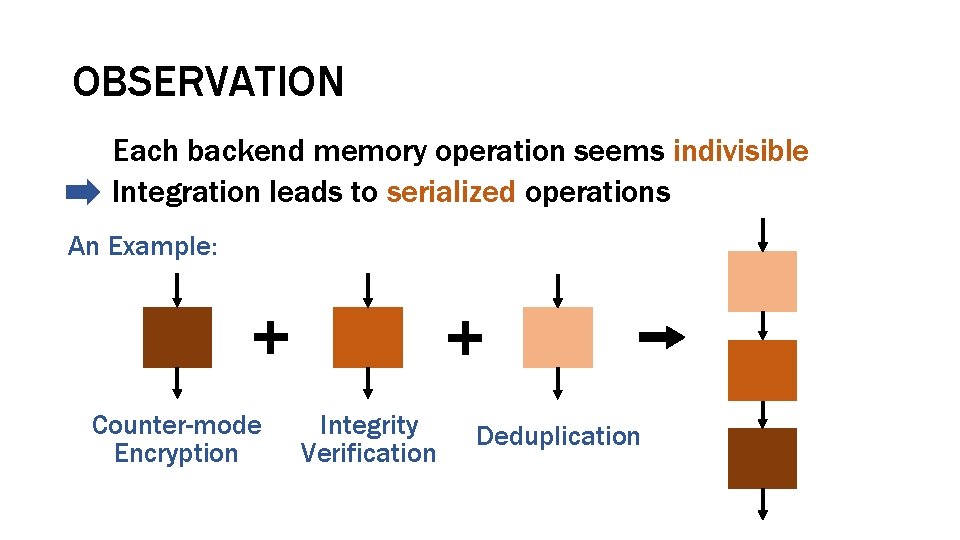
OBSERVATION Each backend memory operation seems indivisible Integration leads to serialized operations An Example: Counter-mode Encryption Integrity Verification Deduplication

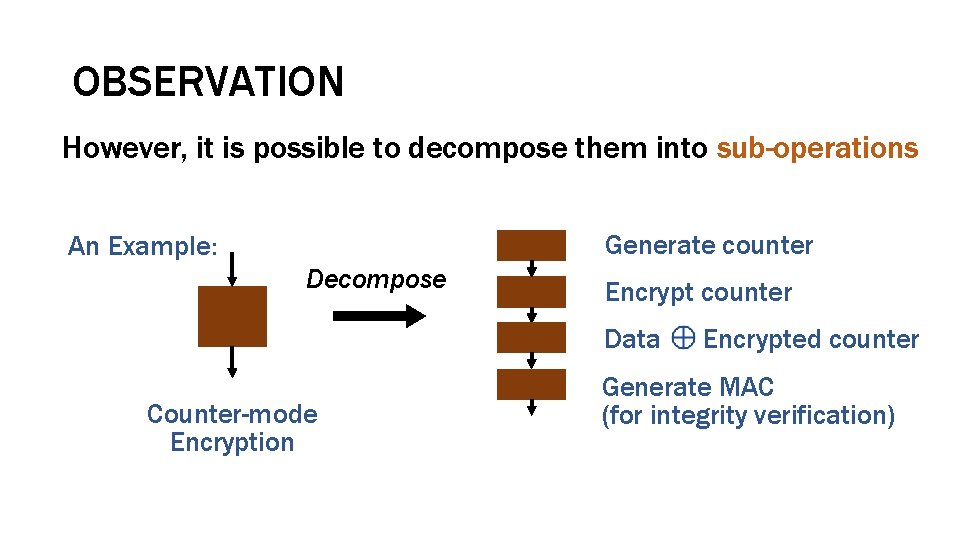
OBSERVATION However, it is possible to decompose them into sub-operations Generate counter An Example: Decompose Encrypt counter Data Counter-mode Encryption Encrypted counter Generate MAC (for integrity verification)

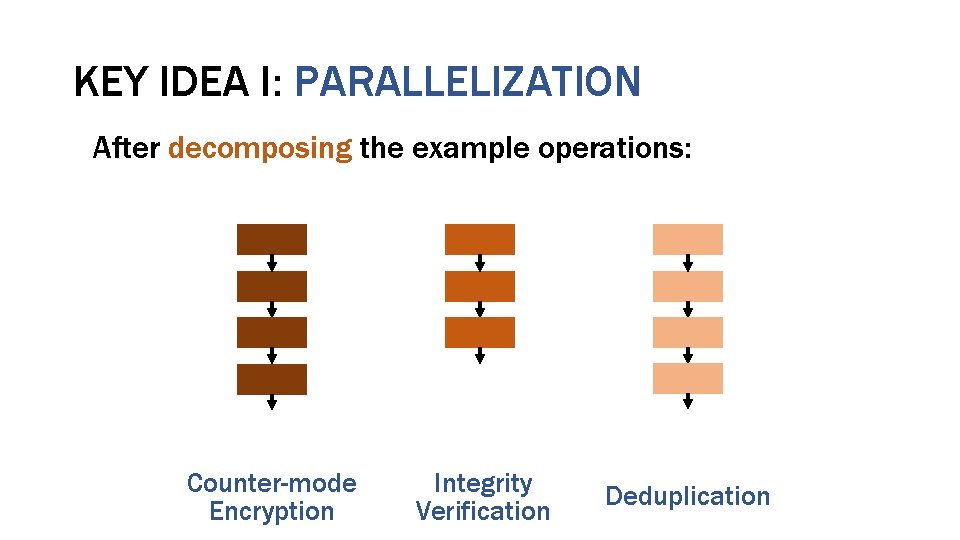
KEY IDEA I: PARALLELIZATION After decomposing the example operations: Counter-mode Encryption Integrity Verification Deduplication

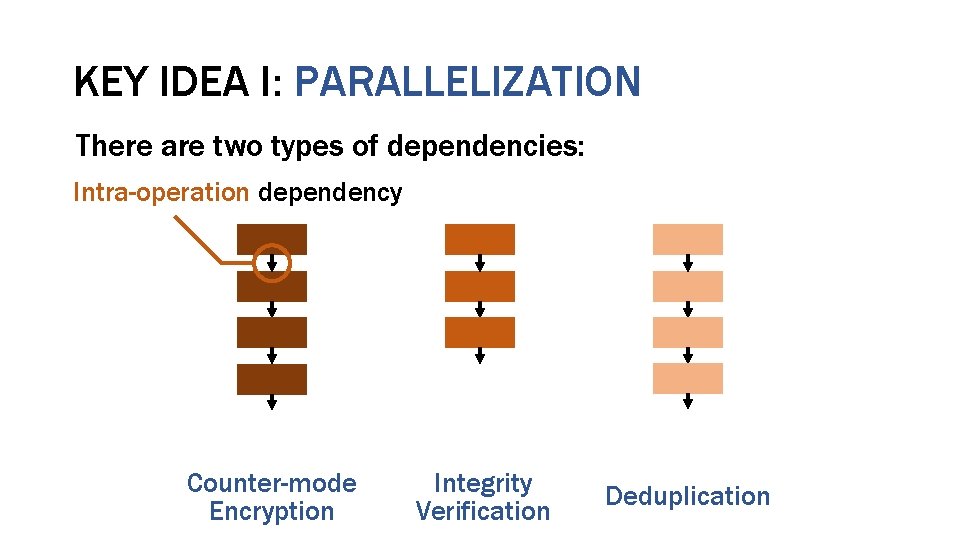
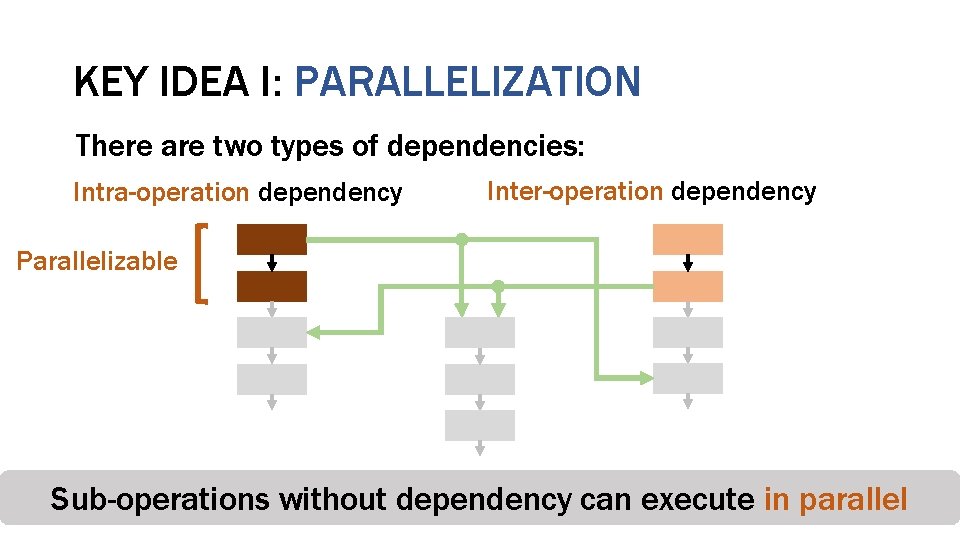
KEY IDEA I: PARALLELIZATION There are two types of dependencies: Intra-operation dependency Counter-mode Encryption Integrity Verification Deduplication

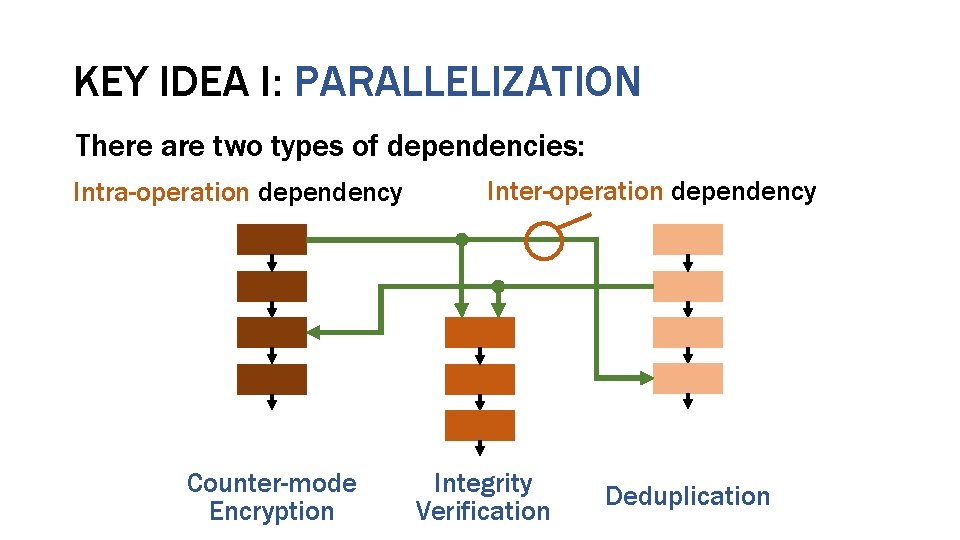
KEY IDEA I: PARALLELIZATION There are two types of dependencies: Intra-operation dependency Counter-mode Encryption Inter-operation dependency Integrity Verification Deduplication

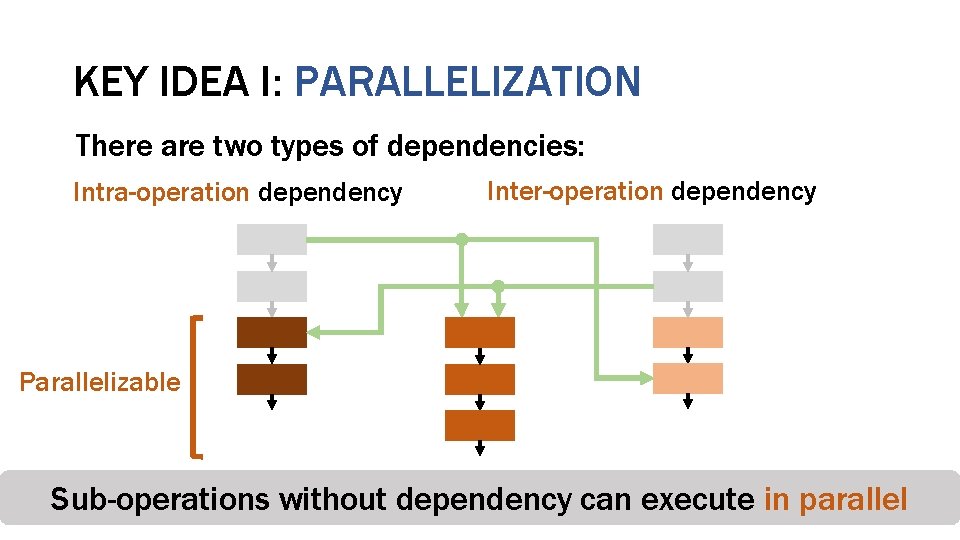
KEY IDEA I: PARALLELIZATION There are two types of dependencies: Intra-operation dependency Inter-operation dependency Parallelizable Counter-mode Sub-operations without Encryption Integrity dependency Verification Deduplication can execute in parallel

KEY IDEA I: PARALLELIZATION There are two types of dependencies: Intra-operation dependency Inter-operation dependency Parallelizable Counter-mode Sub-operations without Encryption Integrity dependency Verification Deduplication can execute in parallel

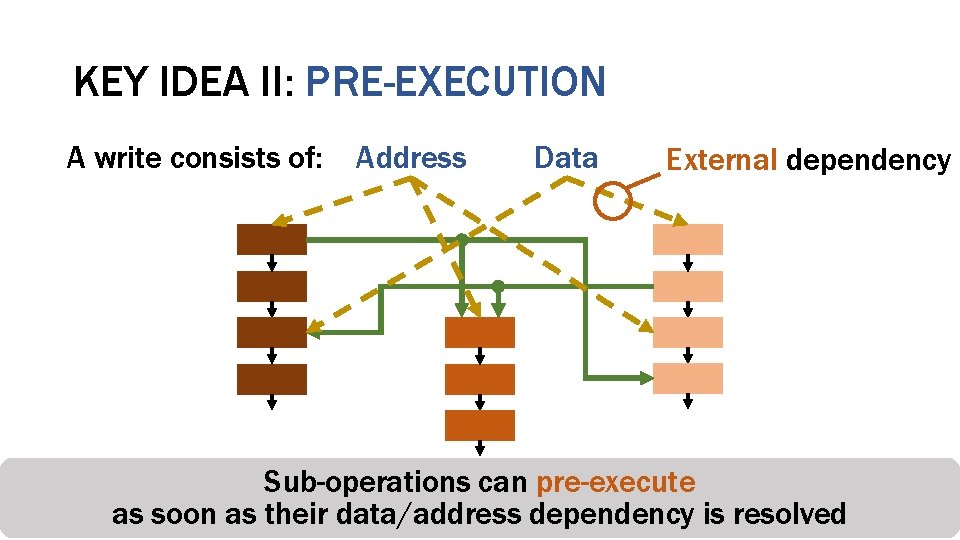
KEY IDEA II: PRE-EXECUTION A write consists of: Address Data External dependency Sub-operations can pre-execute Counter-mode Integrity Deduplication Encryption Verification as soon as their data/address dependency is resolved

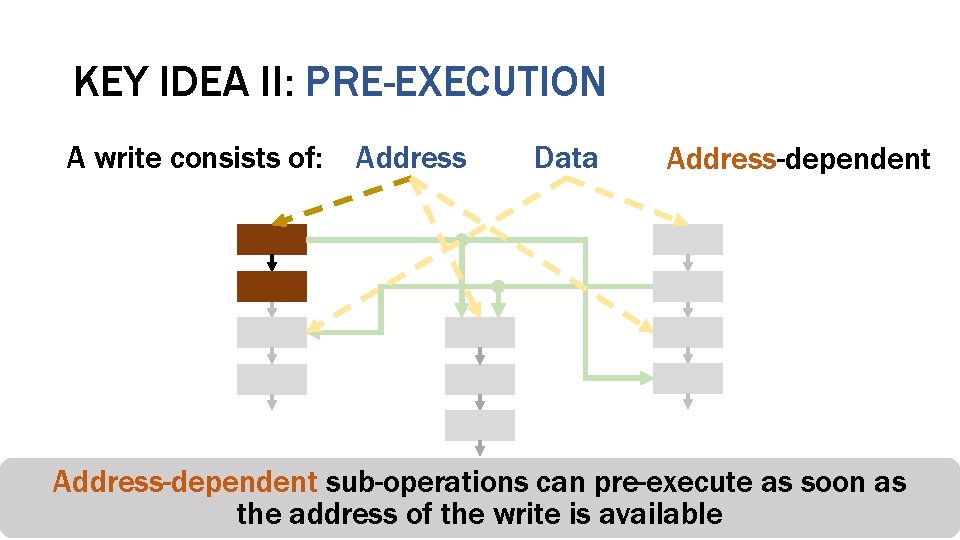
KEY IDEA II: PRE-EXECUTION A write consists of: Address Data Address-dependent sub-operations as soon as Counter-mode Integrity can pre-execute Deduplication Encryption Verification the address of the write is available

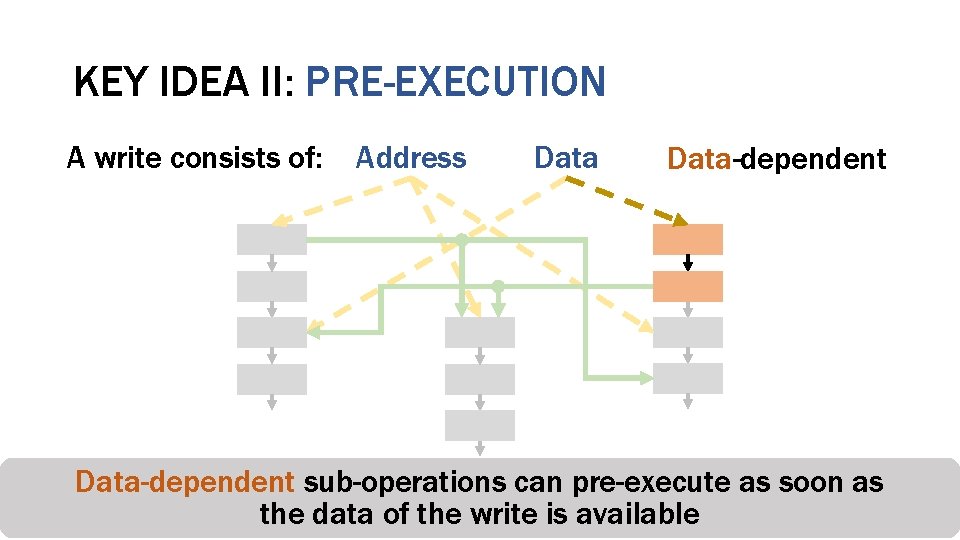
KEY IDEA II: PRE-EXECUTION A write consists of: Address Data-dependent sub-operations can pre-execute as soon as Counter-mode Integrity Deduplication Encryption Verification the data of the write is available

KEY IDEA II: PRE-EXECUTION A write consists of: Address Data Both-dependent sub-operations can pre-execute as soon as Counter-mode Integrity Deduplication Encryption Verification both the data and address of the write are available

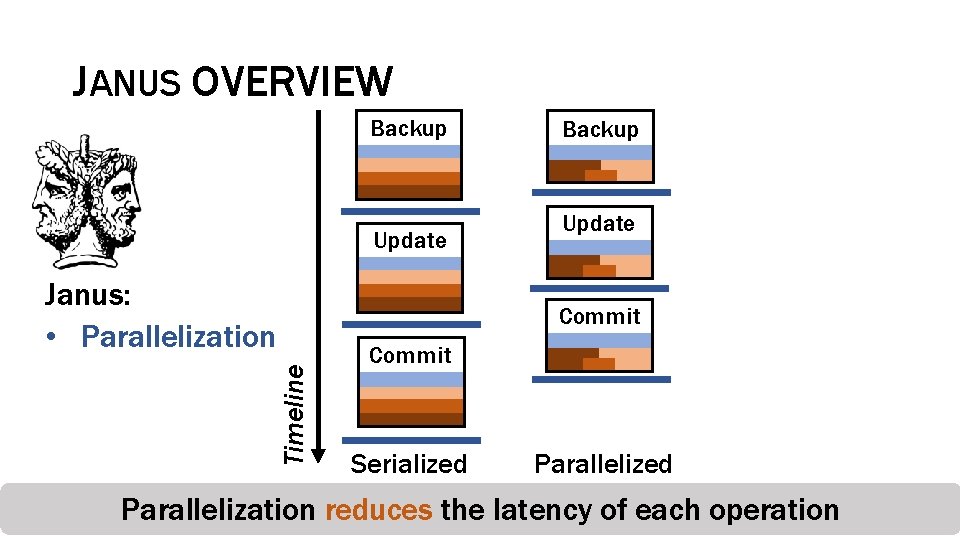
JANUS OVERVIEW Backup Update Janus: • Parallelization Backup Update Timeline Commit Serialized Parallelization reduces the latency of each operation

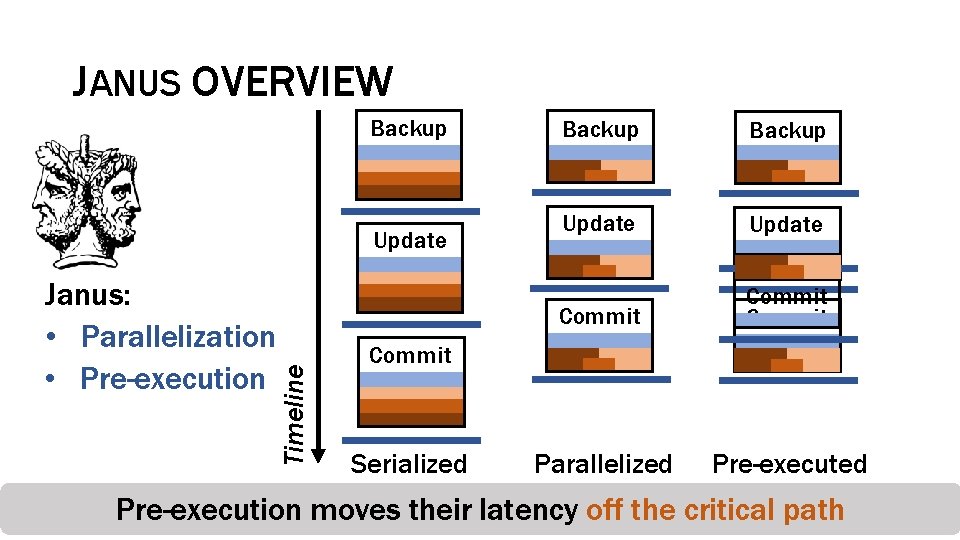
JANUS OVERVIEW Backup Janus: • Parallelization • Pre-execution Timeline Update Backup Update Commit Parallelized Pre-executed Commit Serialized Pre-execution moves their latency off the critical path

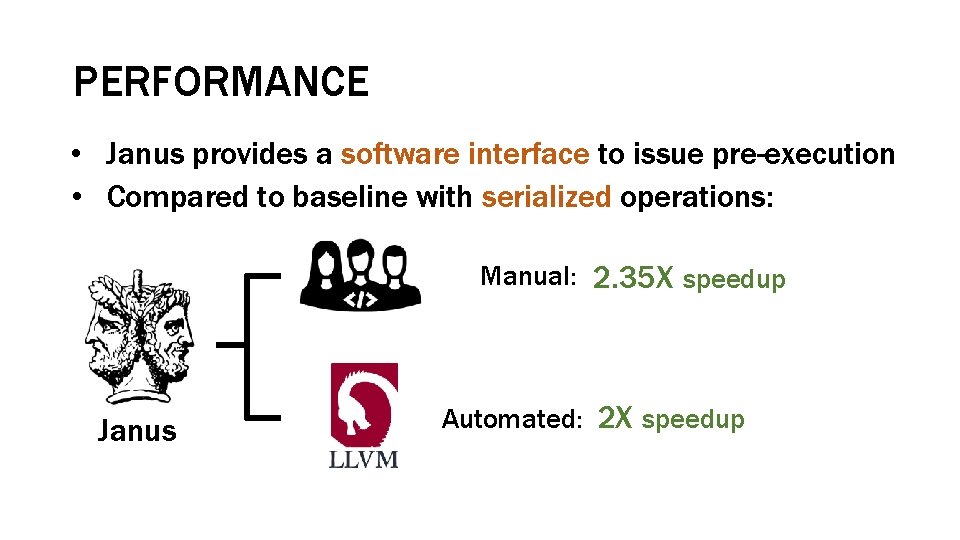
PERFORMANCE • Janus provides a software interface to issue pre-execution • Compared to baseline with serialized operations: Manual: 2. 35 X speedup Janus Automated: 2 X speedup

Janus Optimizing Memory and Storage Support for Non -Volatile Memory Systems Sihang Liu Korakit Seemakhupt, Gennady Pekhimenko, Aasheesh Kolli, and Samira Khan