Hardness Assumptions Related to AdHoc Constructions Shai Halevi



![Collision-resistance vs. the world l Not implied by PRPs via BB [S 98] l Collision-resistance vs. the world l Not implied by PRPs via BB [S 98] l](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-11.jpg)
![And beyond… l Theory of block ciphers? l Embarrassingly lacking l Luby-Rackoff [LR 88] And beyond… l Theory of block ciphers? l Embarrassingly lacking l Luby-Rackoff [LR 88]](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-13.jpg)

![Comments l X-wise independent reminiscent of “Decorrelation theory” [V] l Can’t replace 4 -wise Comments l X-wise independent reminiscent of “Decorrelation theory” [V] l Can’t replace 4 -wise](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-16.jpg)


- Slides: 19

Hardness Assumptions Related to Ad-Hoc Constructions Shai Halevi February 22, 2007

Ad-hoc constructions Hash functions: MD 5, SHA-x, RIPEMD, WHIRLPOOL, Radio. Gatún, … Block ciphers: DES, IDEA, RC 5/6, Twofish, AES, Camellia, … Stream ciphers: RC 4, A 5/x, MUGI, Py, Rabbit, SEAL, Trivium, … l Often consist of a “basic function” and a “mode of operation” around it

What conjectures to make? l We know very little about the true hardness of these “ad hoc constructions” l Use conjectures to fill some of the void l The more the merrier l Only two requirements Can be used to do something interesting* l Not known to be false l l Sometimes we even compromise on this * Let you prove interesting theorems

Standard conjectures l Block ciphers: strong PRP l Hash functions: many things Collision-resistant, 2 nd pre-image resistant, one-way, UOWHF (TCR) l PRF, MAC (when keyed) l Also others: hard to find pre-image of zero, hard to find “almost collisions”, hard to find fixed-points, “division-intractability”, … l

“Unholy conjectures” l Random oracles, Ideal ciphers l What the customer wants: this is how people who build applications think of these constructs E. g. , what’s wrong with Ek(k)? l “You proved that this is not a random oracle. That’s your problem, not ours” l Unfortunately they have a point l

Theory, anyone? l Modes of operation l Relations between notions l “Weak random oracles” l And beyond…

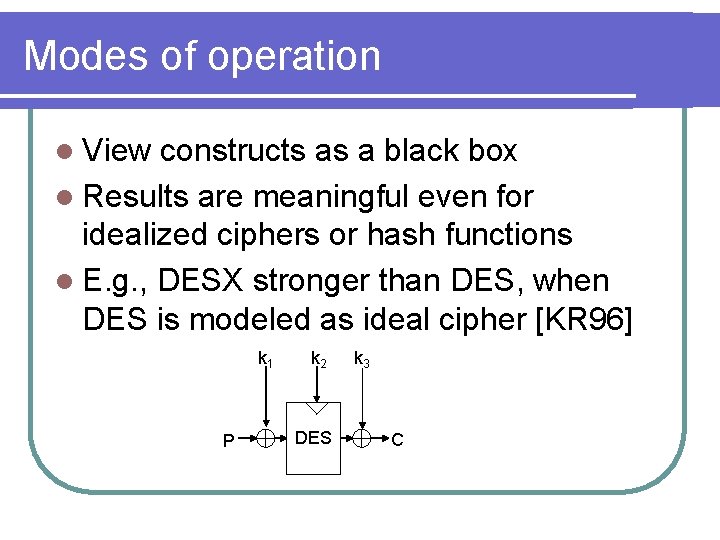
Modes of operation l View constructs as a black box l Results are meaningful even for idealized ciphers or hash functions l E. g. , DESX stronger than DES, when DES is modeled as ideal cipher [KR 96] k 1 P k 2 DES k 3 C

ROs and ideal ciphers l Using l random funcs/perms for extractors In CBC mode, HMAC mode [DGHKR 04] l Domain l Also building ROs from ideal-ciphers l Open: l extension for ROs [CDMP 05] building ideal ciphers from ROs Partial results in [DP 06] l Open: domain-extenders for ideal ciphers

Multi-property-preserving modes l Prove many claims on the same mode l E. g, for (a variant of) Merkle-Damgård If compression function is collision-resistant then so is the resulting hash function, l If compression function is PRF then so is the resulting hash function, l If compression function is a random-oracle then so is the resulting hash function, l Etc. l

Relations between notions l So many notions, we need taxonomies
![Collisionresistance vs the world l Not implied by PRPs via BB S 98 l Collision-resistance vs. the world l Not implied by PRPs via BB [S 98] l](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-11.jpg)
Collision-resistance vs. the world l Not implied by PRPs via BB [S 98] l Implied by PIR, homomorphic encryption [IKO 05] l Surprising: collision-resistance follows from secrecy guarantees l Connections to the compressibility of SAT [HN 06] l Equivalent to one-flow statistically-hiding commitment?

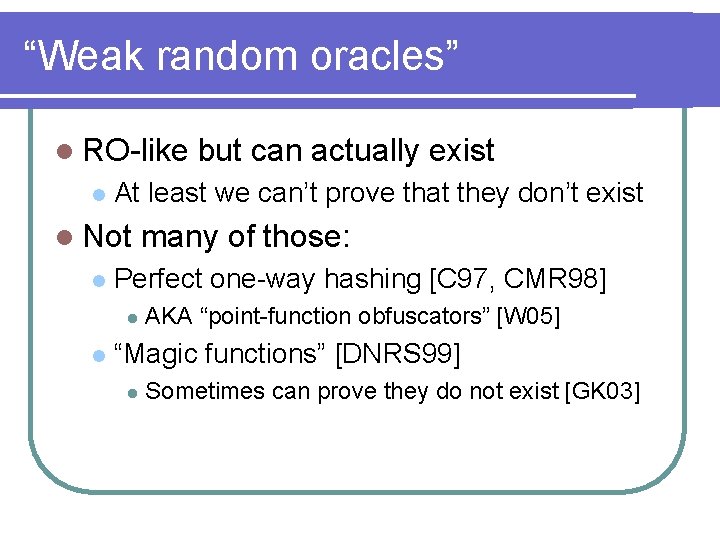
“Weak random oracles” l RO-like l At least we can’t prove that they don’t exist l Not l many of those: Perfect one-way hashing [C 97, CMR 98] l l but can actually exist AKA “point-function obfuscators” [W 05] “Magic functions” [DNRS 99] l Sometimes can prove they do not exist [GK 03]
![And beyond l Theory of block ciphers l Embarrassingly lacking l LubyRackoff LR 88 And beyond… l Theory of block ciphers? l Embarrassingly lacking l Luby-Rackoff [LR 88]](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-13.jpg)
And beyond… l Theory of block ciphers? l Embarrassingly lacking l Luby-Rackoff [LR 88] for Feistel networks? + refinement by Naor-Reingold [NR 97] l Dodis-Puniya [DP 07] analyze Feistel with round functions weaker than PRFs l Relevance to block-cipher design is a huge leap of faith l

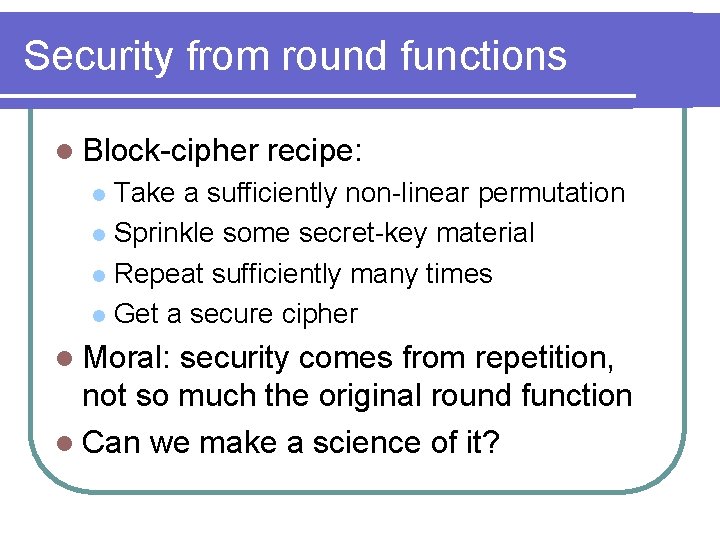
Security from round functions l Block-cipher recipe: Take a sufficiently non-linear permutation l Sprinkle some secret-key material l Repeat sufficiently many times l Get a secure cipher l l Moral: security comes from repetition, not so much the original round function l Can we make a science of it?

Charlie’s conjecture l Due l to Charlie Rackoff Take “simple enough” permutation family l E. g. , computed in NC 0 Repeat enough times to get “almost four-wise independence” l The result is a PRP l l Can anyone disprove it?
![Comments l Xwise independent reminiscent of Decorrelation theory V l Cant replace 4 wise Comments l X-wise independent reminiscent of “Decorrelation theory” [V] l Can’t replace 4 -wise](https://slidetodoc.com/presentation_image_h2/88940168b0b7fd14af53b34071960ce1/image-16.jpg)
Comments l X-wise independent reminiscent of “Decorrelation theory” [V] l Can’t replace 4 -wise with 3 -wise l Otherwise it’s false l Simplicity of round function is important Otherwise it’s false (e. g. , if you start from a 4 -wise independent permutation) l The point is to have many repetitions l

What can we do with Charlie? l The l conjecture implies that PRPs exist But PRPs with a very specific structure l Do they imply CR hashing? l If not: come up with a similar conjecture that implies collision-resistant hashing l Or implies both PRPs and CR hashing

Summary l We know very little about the true hardness of these “ad hoc constructions” l Conjectures can fill some of the void l The more the merrier l Only two requirements Not known to be false (? ) l Can be used to do something interesting* l * Let you prove interesting theorems

dank u
 Shai halevi
Shai halevi Adhoc.com
Adhoc.com Ad hoc polymorphism
Ad hoc polymorphism Plumb bob distortion model
Plumb bob distortion model Shai vardi
Shai vardi Coptic letters pronunciation
Coptic letters pronunciation Robert ho shai lai
Robert ho shai lai The integration of eye, hand, and foot movements
The integration of eye, hand, and foot movements Health-related skills
Health-related skills Impersonal passive constructions
Impersonal passive constructions Hypothetical constructions
Hypothetical constructions Constructions with se
Constructions with se Argument structure constructions
Argument structure constructions 1-6 basic constructions answers
1-6 basic constructions answers Impersonal passive voice examples
Impersonal passive voice examples Les information suivantes
Les information suivantes Lesson 10 unknown angle proofs
Lesson 10 unknown angle proofs Nino constructions
Nino constructions Square edge constructions
Square edge constructions Passive constructions
Passive constructions