Fortinet Real Time Network Protection Computer Links University














- Slides: 33

Fortinet Real Time Network Protection Computer. Links University Joe Sarno Channel Sales Manager – South EMEA jsarno@fortinet. com

The Company

Fortinet Company Overview • Founded October, 2000 by Ken Xie – Founder, former Pres. & CEO of Net. Screen (Now JNPR) • Global Sales & Service Presence – HQ Sunnyvale, CA – – – Over 600 employees 30 Offices throughout Americas, Asia, EMEA More than 100, 000 Forti. Gate units shipped to 2, 000 customers Creators of world’s only ASIC-powered antivirus systems Addressing the need for real-time network protection • Ranked #1 by IDC in Unified Threat Management Security Appliance category • Continued strong financial performance – Among the fastest growing network security companies in history – Total equity raised $93 million CONFIDENTIAL

IDC Vision

IDC Reports Fortinet’s Market Leadership! New! Unified Threat Management (UTM) Security Appliance Market = unification of firewall, gateway anti-virus & IDP into a single platform c Fortinet ranked #1 • UTM market revenue in 2005 estimated at $515 million • Over the next 4 years, UTM appliance sales will exceed that of standard firewall/VPNs • Firewall/VPN segment – 2005 revenue of nearly $1. 8 billion • UTM market – estimated at nearly $2 billion by 2008

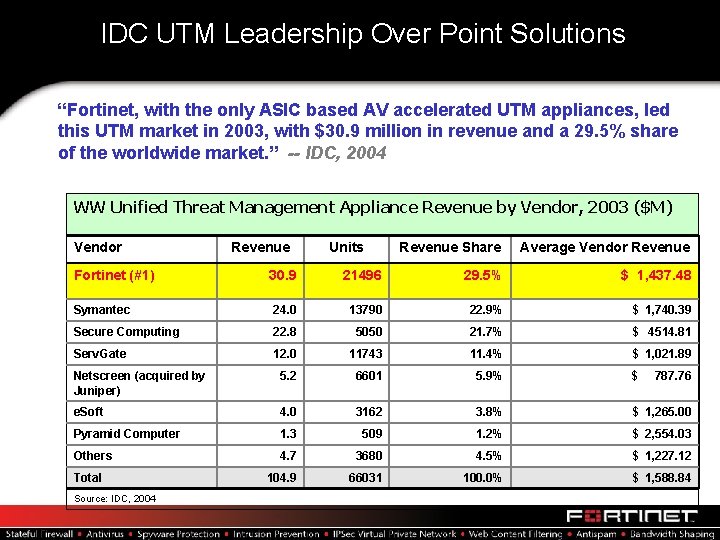
IDC UTM Leadership Over Point Solutions “Fortinet, with the only ASIC based AV accelerated UTM appliances, led this UTM market in 2003, with $30. 9 million in revenue and a 29. 5% share of the worldwide market. ” -- IDC, 2004 WW Unified Threat Management Appliance Revenue by Vendor, 2003 ($M) Vendor Fortinet (#1) Revenue Units Revenue Share Average Vendor Revenue 30. 9 21496 29. 5% $ 1, 437. 48 Symantec 24. 0 13790 22. 9% $ 1, 740. 39 Secure Computing 22. 8 5050 21. 7% $ 4514. 81 Serv. Gate 12. 0 11743 11. 4% $ 1, 021. 89 Netscreen (acquired by Juniper) 5. 2 6601 5. 9% $ e. Soft 4. 0 3162 3. 8% $ 1, 265. 00 Pyramid Computer 1. 3 509 1. 2% $ 2, 554. 03 Others 4. 7 3680 4. 5% $ 1, 227. 12 104. 9 66031 100. 0% $ 1, 588. 84 Total Source: IDC, 2004 787. 76

UTM Products Will Overtake Standalone VPN/Firewalls by 2008 “The UTM market is being created because it is quickly catching on with customers and vendors. UTM incorporates firewall, intrusion detection and prevention, and AV in one high-performance appliance. ” -- IDC, 2004 Worldwide Threat Management Security Appliances Forecast, 2004 -2008 ($M) Firewall/VPN UTM Security Appliance Total TM Security Appliance 2003 2004 $1, 479. 1 $1, 667. 7 $104. 9 $1, 584. 0 2005 2006 2007 2008 2003 Share (%) CAGR (%) $1, 791. 6 $1, 804. 4 $1, 623. 5 $1, 462. 3 93. 4% -0. 2% 42. 4% $225. 0 $517. 5 $828. 0 $1, 324. 8 $1, 987. 2 6. 6% 80. 1% 57. 6% $1, 892. 7 $ 2, 309. 1 $2, 632. 4 $2, 948. 3 $3, 449. 5 16. 8% 2008 Share (%)

Fortinet Story Unfolding

First Generation: Stateful Inspection Firewall In point solution configurations, Stateful Inspection firewall delivers network level security services Firewall / VPN IDS/IDP Antivirus Content Filter

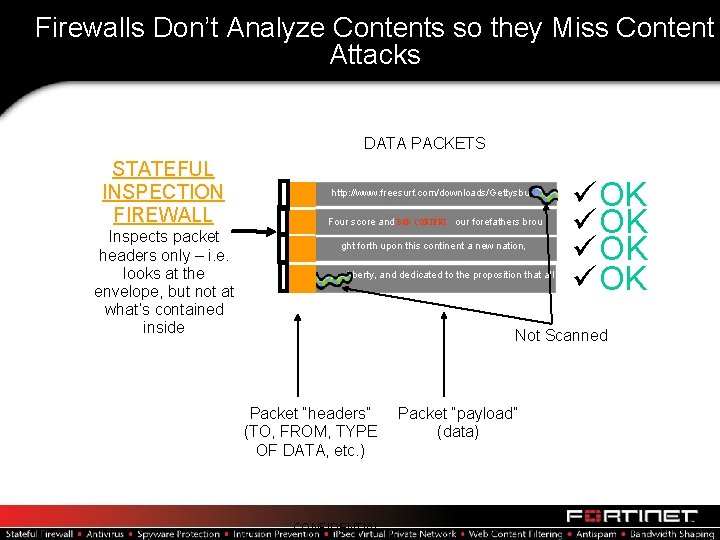
Firewalls Don’t Analyze Contents so they Miss Content Attacks DATA PACKETS STATEFUL INSPECTION FIREWALL Inspects packet headers only – i. e. looks at the envelope, but not at what’s contained inside http: //www. freesurf. com/downloads/Gettysburg Four score and BAD CONTENT our forefathers brou ght forth upon this continent a new nation, n liberty, and dedicated to the proposition that all üOK üOK Not Scanned Packet “headers” (TO, FROM, TYPE OF DATA, etc. ) CONFIDENTIAL Packet “payload” (data)

Second Generation: Deep Packet Inspection typically combines functionality of IDS/IDP system with Stateful Inspection firewall Firewall / VPN IDS/IDP Antivirus Content Filter

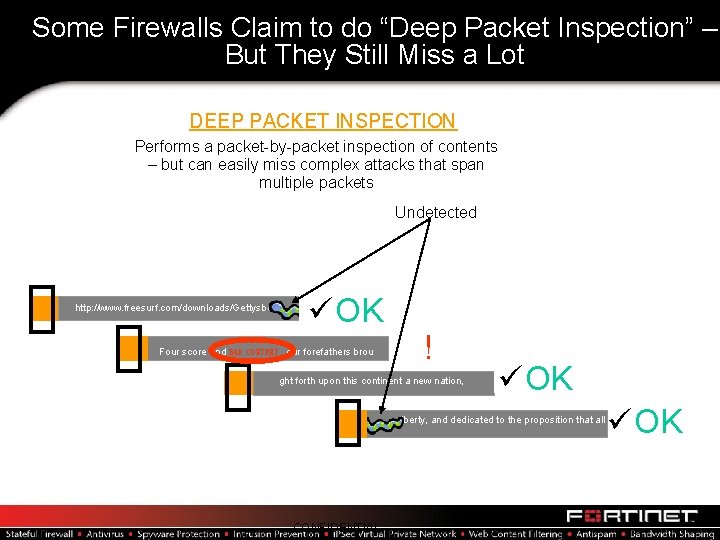
Some Firewalls Claim to do “Deep Packet Inspection” – But They Still Miss a Lot DEEP PACKET INSPECTION Performs a packet-by-packet inspection of contents – but can easily miss complex attacks that span multiple packets Undetected http: //www. freesurf. com/downloads/Gettysburg üOK Four score and BAD CONTENT our forefathers brou ! ght forth upon this continent a new nation, üOK n liberty, and dedicated to the proposition that all CONFIDENTIAL üOK

Next Generation: Complete Content Protection Combines the capabilities of Firewall, IDS/IDP, AV, CF Firewall / VPN IDS/IDP Antivirus Content Filter

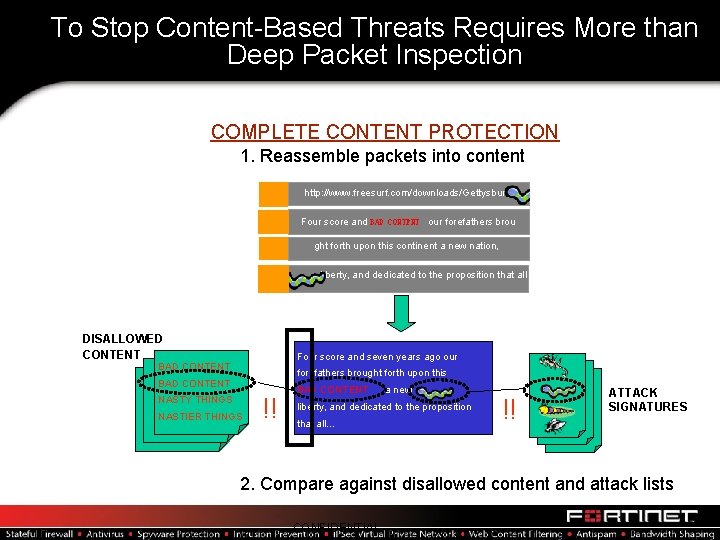
To Stop Content-Based Threats Requires More than Deep Packet Inspection COMPLETE CONTENT PROTECTION 1. Reassemble packets into content http: //www. freesurf. com/downloads/Gettysburg Four score and BAD CONTENT our forefathers brou ght forth upon this continent a new nation, n liberty, and dedicated to the proposition that all DISALLOWED CONTENT Four score and seven years ago our BAD CONTENT forefathers brought forth upon this BAD CONTENT NASTY THINGS NASTIER THINGS !! BAD CONTENT a new liberty, and dedicated to the proposition that all… !! ATTACK SIGNATURES 2. Compare against disallowed content and attack lists CONFIDENTIAL

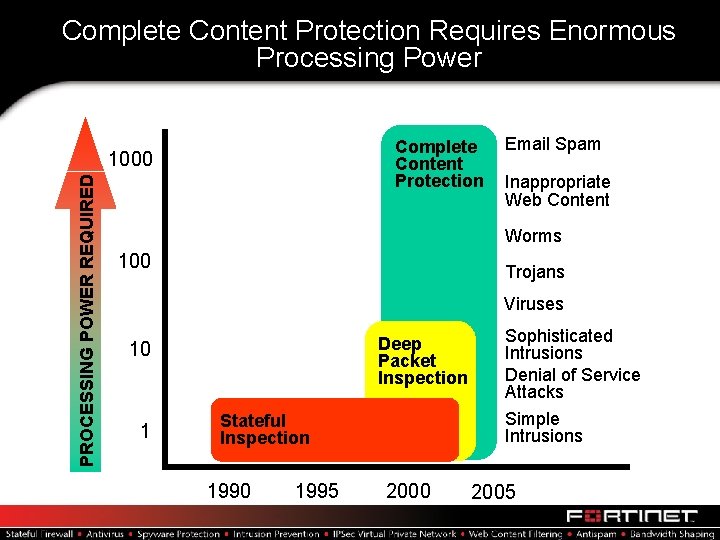
Complete Content Protection Requires Enormous Processing Power Complete Content Protection PROCESSING POWER REQUIRED 1000 Email Spam Inappropriate Web Content Worms 100 Trojans Viruses Deep Packet Inspection 10 1 Stateful Inspection 1990 1995 2000 Sophisticated Intrusions Denial of Service Attacks Simple Intrusions 2005

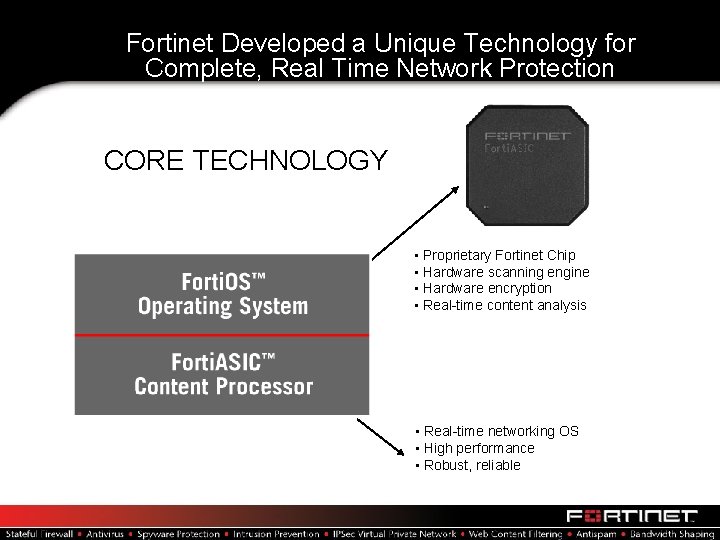
Fortinet Developed a Unique Technology for Complete, Real Time Network Protection CORE TECHNOLOGY • Proprietary Fortinet Chip • Hardware scanning engine • Hardware encryption • Real-time content analysis • Real-time networking OS • High performance • Robust, reliable

Fortinet Developed Products for Complete Real Time Network Protection Best-in-Class Applications Included in Every Forti. Gate Forti. OS Operating System

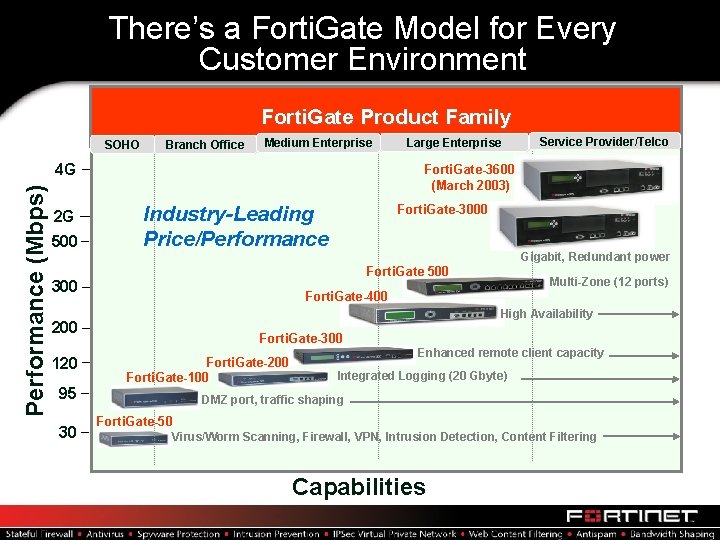
There’s a Forti. Gate Model for Every Customer Environment Forti. Gate Product Family SOHO Branch Office Medium Enterprise Performance (Mbps) 4 G 2 G 500 Large Enterprise Service Provider/Telco FGT-2000 Forti. Gate-3600 (March 2003) Industry-Leading Price/Performance Forti. Gate-3000 Gigabit, Redundant power Forti. Gate 500 300 Forti. Gate-400 High Availability 200 120 95 30 Multi-Zone (12 ports) Forti. Gate-300 Forti. Gate-200 Forti. Gate-100 Enhanced remote client capacity Integrated Logging (20 Gbyte) DMZ port, traffic shaping Forti. Gate-50 Virus/Worm Scanning, Firewall, VPN, Intrusion Detection, Content Filtering Capabilities

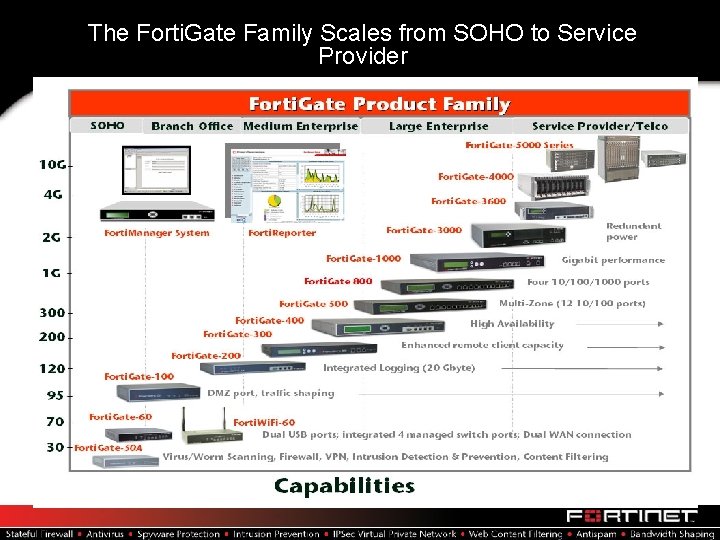
The Forti. Gate Family Scales from SOHO to Service Provider

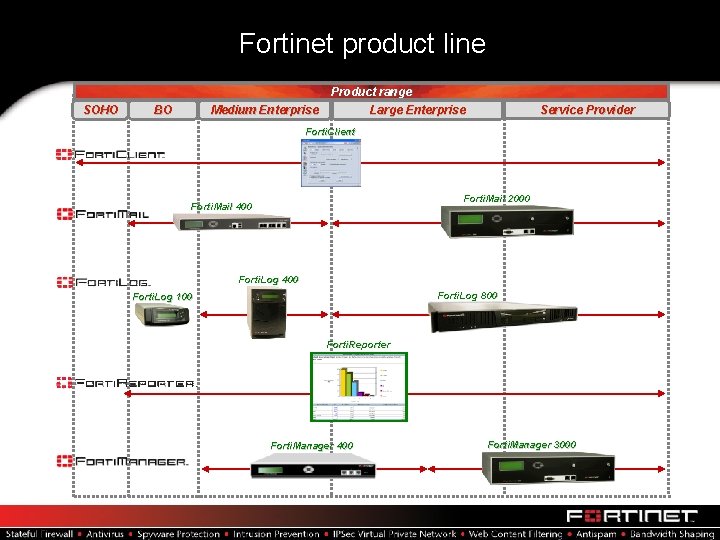
Fortinet product line Product range SOHO BO Medium Enterprise Service Provider Large Enterprise Forti. Client Forti. Mail 2000 Forti. Mail 400 Forti. Log 800 Forti. Log 100 Forti. Reporter Forti. Manager 400 Forti. Manager 3000

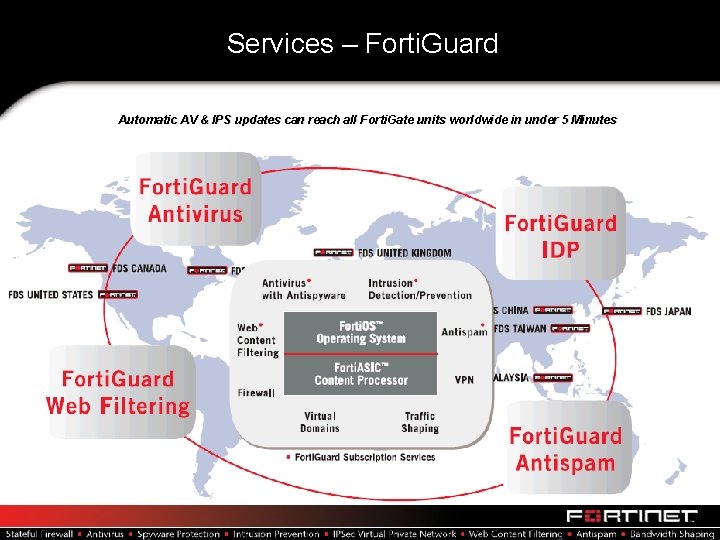
Services – Forti. Guard Automatic AV & IPS updates can reach all Forti. Gate units worldwide in under 5 Minutes

Fortinet Forti. Guard Applications Key Advantages Fortinet has developed all of its security applications from the ground up: • Antivirus – 100% coverage of the virus Wild. List (www. wildlist. org) • Intrusion Detection and Prevention – 1400+ signatures • Antispam – Bayesian and Heuristics filtering, RBL, ORDBL servers • URL Filtering – 56 Categories, 27+million rated websites, Daily updates to the URL database • Integrated application security delivers a better defense against blended threats which use multiple methods of propagation • No reliance on OEM agreements with 3 rd party vendors! • Common Criteria EAL 4+ certification just earned! Fortinet offers simplified pricing and reduces security costs by licensing security applications per device instead of per user which is practiced by many competitors reliant on 3 rd party licensing of AV, IPS, Antispam, and URL filtering. Footnote

World Class Services and Support

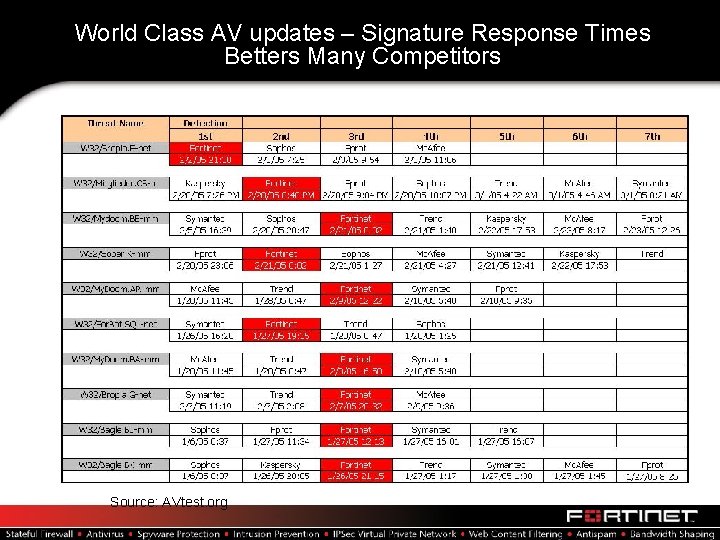
World Class AV updates – Signature Response Times Betters Many Competitors Source: AVtest. org

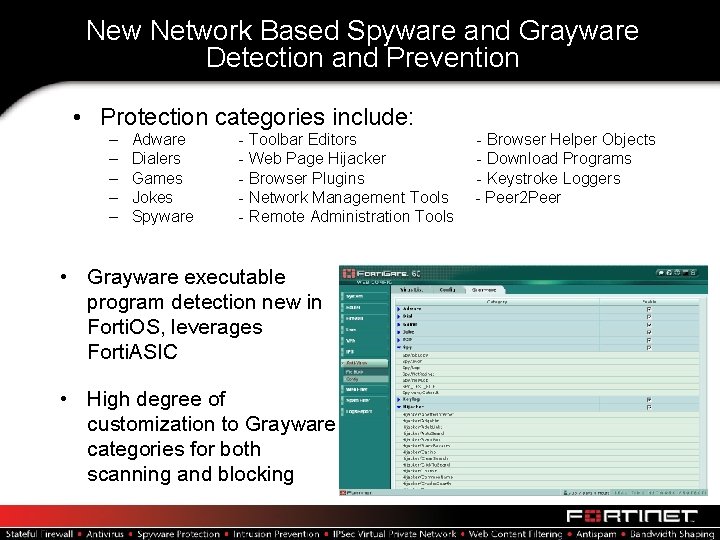
New Network Based Spyware and Grayware Detection and Prevention • Protection categories include: – – – Adware Dialers Games Jokes Spyware - Toolbar Editors - Web Page Hijacker - Browser Plugins - Network Management Tools - Remote Administration Tools • Grayware executable program detection new in Forti. OS, leverages Forti. ASIC • High degree of customization to Grayware categories for both scanning and blocking - Browser Helper Objects - Download Programs - Keystroke Loggers - Peer 2 Peer

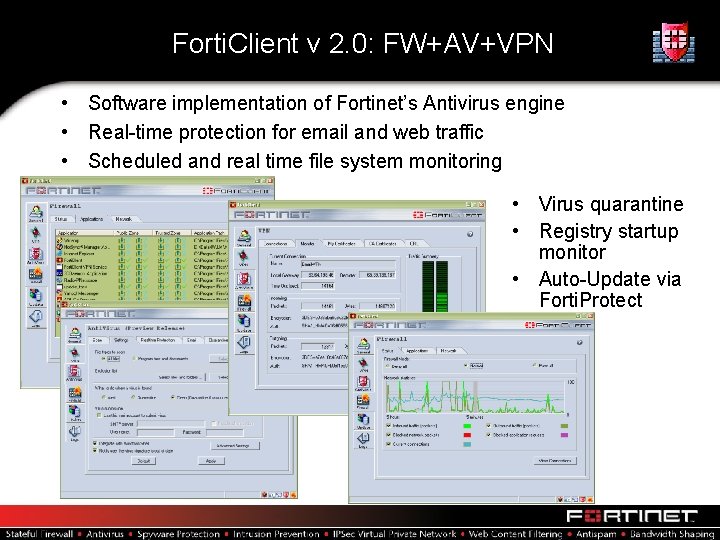
Forti. Client v 2. 0: FW+AV+VPN • Software implementation of Fortinet’s Antivirus engine • Real-time protection for email and web traffic • Scheduled and real time file system monitoring • Virus quarantine • Registry startup monitor • Auto-Update via Forti. Protect

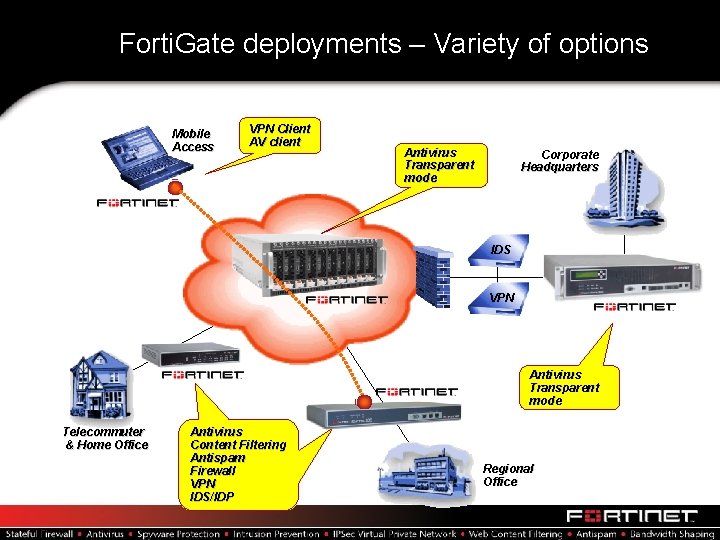
Forti. Gate deployments – Variety of options Mobile Access VPN Client AV client Antivirus Transparent mode Corporate Headquarters IDS VPN Antivirus Transparent mode Telecommuter & Home Office Antivirus Content Filtering Antispam Firewall VPN IDS/IDP Regional Office

Many Awards and Industry Certifications

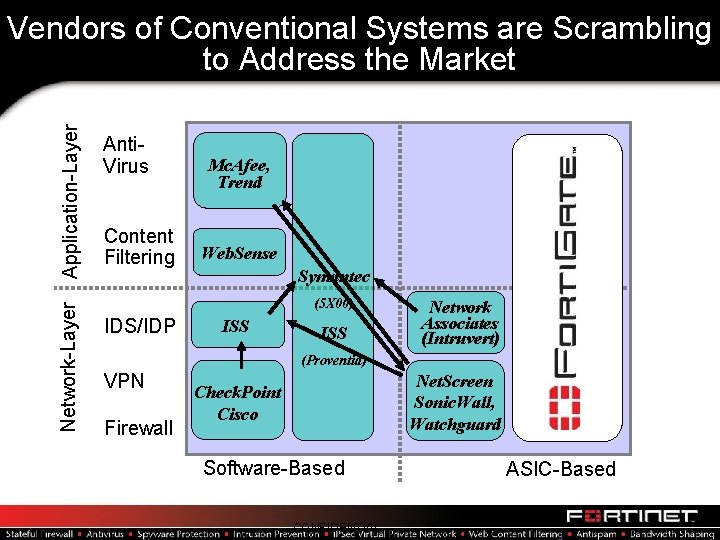
Network-Layer Application-Layer Vendors of Conventional Systems are Scrambling to Address the Market Anti. Virus Content Filtering Mc. Afee, Trend Web. Sense Symantec (5 X 00) IDS/IDP ISS Network Associates (Intruvert) (Proventia) VPN Firewall Net. Screen Sonic. Wall, Watchguard Check. Point Cisco Software-Based CONFIDENTIAL ASIC-Based

Network-Layer Application-Layer Vendors of Conventional Systems are Scrambling to Address the Market Anti. Virus Content Filtering Mc. Afee, Trend Web. Sense Symantec (5 X 00) IDS/IDP ISS Network Associates (Intruvert) (Proventia) VPN Firewall Net. Screen Sonic. Wall, Watchguard Check. Point Cisco Software-Based CONFIDENTIAL ASIC-Based

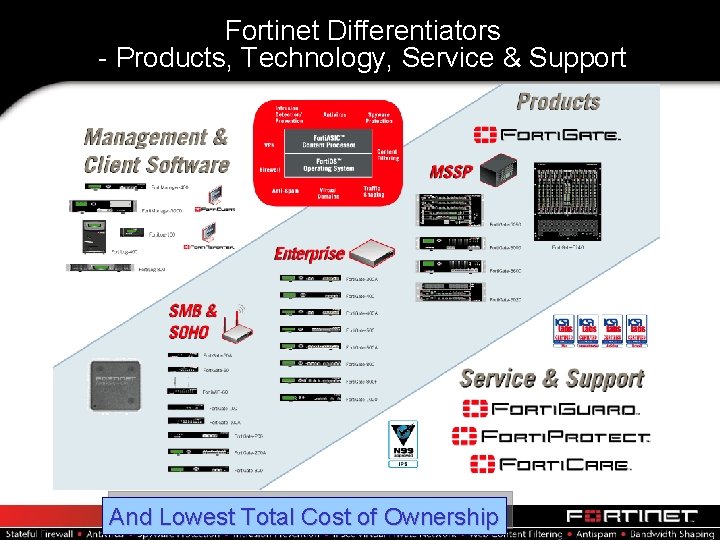
Fortinet Differentiators - Products, Technology, Service & Support And Lowest Total Cost of Ownership

The First and Only Company to Address All the Security Market Needs – and at Lowest Total Cost

Thank You! For more information: www. fortinet. com jsarno@fortinet. com Fortinet Online Knowledge Base: http: //kc. forticare. com Forti. Guard Center: http: //www. fortinet. com/Forti. Guard. Center Forti. Partner Extranet: http: //partner. fortinet. com