Flow Twist Efficient ContextSensitive Inside Out Taint Analysis


![Results – only Class. for. Name 40 35 Runtime [min] 30 25 20 15 Results – only Class. for. Name 40 35 Runtime [min] 30 25 20 15](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-11.jpg)
![Results – all Caller Sensitive Methods 40 35 Runtime [min] 30 25 Did not Results – all Caller Sensitive Methods 40 35 Runtime [min] 30 25 Did not](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-12.jpg)
![IFDS Algorithm [17, 19] Reports Leaks Caller Sensitive ? Public Method 16 IFDS Algorithm [17, 19] Reports Leaks Caller Sensitive ? Public Method 16](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-16.jpg)
- Slides: 28

Flow. Twist: Efficient Context-Sensitive Inside. Out Taint Analysis for Large Codebases Johannes Lerch, Ben Hermann, Eric Bodden, and Mira Mezini {lastname}@cs. tu-darmstadt. de https: //github. com/johanneslerch/Flow. Twist @stg_darmstadt 07. 10. 2020 | Technische Universität Darmstadt | Software Technology Group | 1

curity holes e s h tc a p to te a d p u ew Java curity Oracle pushed out ncritical patch update contains fixes for 50 different se the latest Jasevda. Frflidaay Relea w, d raws Web attack s, reports say s. vulnerability in the flaw. A Ja va software 13 has the potential 20, and se, rs Febu 04 researchers warn to affect a wide sw that it‘s already b ath of computer Jan 10, 2013 eing explo New vulne r ited “in the wild”. abilities fo Following und in late is t latest u. Java Oracle patches 7 vulnerability st Java up h vulnerabilities p d a runtime. tes, more v cate Java runtime uln. Oracle paadtnew erabilithas o t e Breaking quarterly update schedule, released ie Aug 31, 2 its t s a h fix for this that d a a v p e e u 012 b s e a a e n le v ncy Ja Oracle decided to ruencleo”v. ered in Oracle‘s addresses recent security flaws. e g r e m e “ Java 7 Aug 30, le issuesck a new flaw in Java, bug as soon as possib Orac 2012 ly related kers atta e c s a erability h lo ln u c r v r e a e ft v a A th J o x fi n a to ility and ases software update mote attackers re w lneracble llo a ld vu. O u le co t re a ra 013 vulnerability th s Mar 04, 2 cy software update repairs untime r a s v n r e H a rg e e J o Em l us n de. melbain o ects al co f i d f ry l a itr S rb a y e l te t c cu n to exe evheitn 1 af that appaurerity still a d l u 13 te o dvises d 20 , 13 c n Ja w d a sakt. e Ds. Hs. Sursfaaces rrsuap l i f r t isabling a a v h y a Java, New J ava vulnerabilitye tuosainbgiltlhioenspuasne unpatched vuln e s J lu ra o Jan 1 gin at ris A new puts cl 4, 2013 k of rem bility may still p e r o f e r ut Web ote attac e browser and th 2012 k. s , 6 2 ep S 2

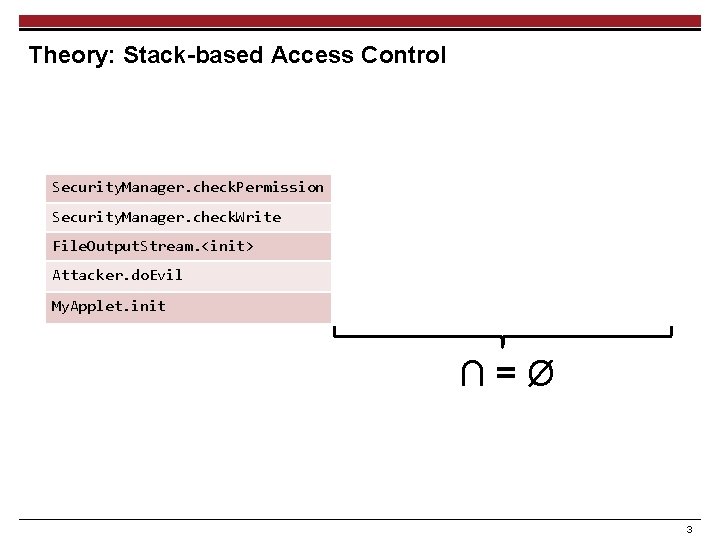
Theory: Stack-based Access Control Security. Manager. check. Permission File. Permission, Socket. Permission, . . . Security. Manager. check. Write File. Permission, Socket. Permission, . . . File. Output. Stream. <init> File. Permission, Socket. Permission, . . . Attacker. do. Evil Ø My. Applet. init Ø ∩=Ø 3

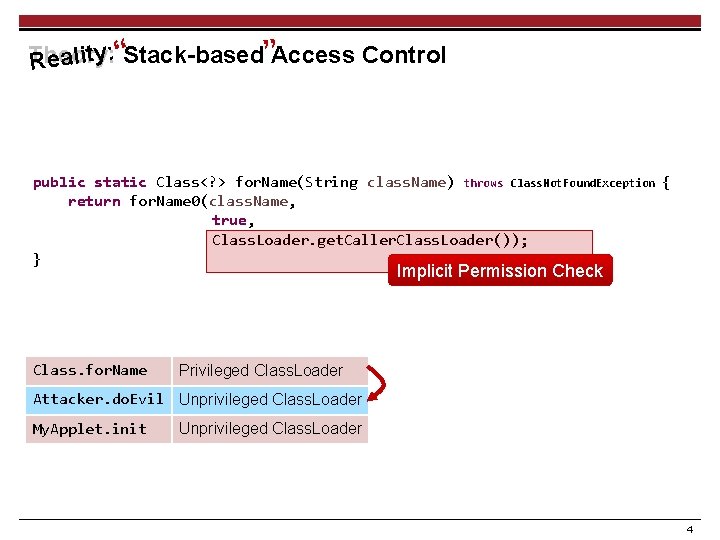
Theory: Reality: “Stack-based”Access Control public static Class<? > for. Name(String class. Name) throws Class. Not. Found. Exception { return for. Name 0(class. Name, true, Class. Loader. get. Caller. Class. Loader()); } Implicit Permission Check Class. for. Name Privileged Class. Loader Attacker. do. Evil Unprivileged Class. Loader My. Applet. init Unprivileged Class. Loader 4

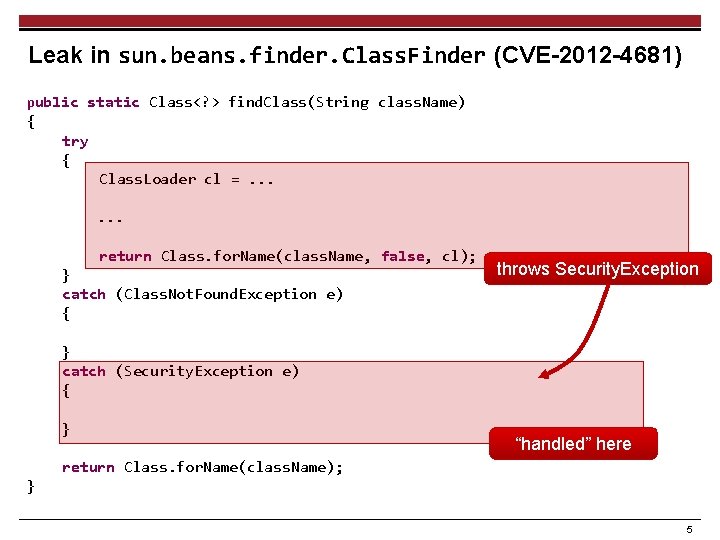
Leak in sun. beans. finder. Class. Finder (CVE-2012 -4681) public static Class<? > find. Class(String class. Name) { try { Class. Loader cl =. . . return Class. for. Name(class. Name, false, cl); } catch (Class. Not. Found. Exception e) { throws Security. Exception } catch (Security. Exception e) { } “handled” here return Class. for. Name(class. Name); } 5

Leak in sun. beans. finder. Class. Finder (CVE-2012 -4681) public static Class<? > find. Class(String class. Name) { try { Class. Loader cl =. . . Class. for. Name Privileged return Class. for. Name(class. Name, false, Class. Loader cl); throws Security. Exception } Class. Finder. find. Class Privileged Class. Loader catch (Class. Not. Found. Exception e) { Attacker. do. Evil Unprivileged Class. Loader My. Applet. init } catch (Security. Exception e) { } Unprivileged Class. Loader “handled” here return Class. for. Name(class. Name); } 6

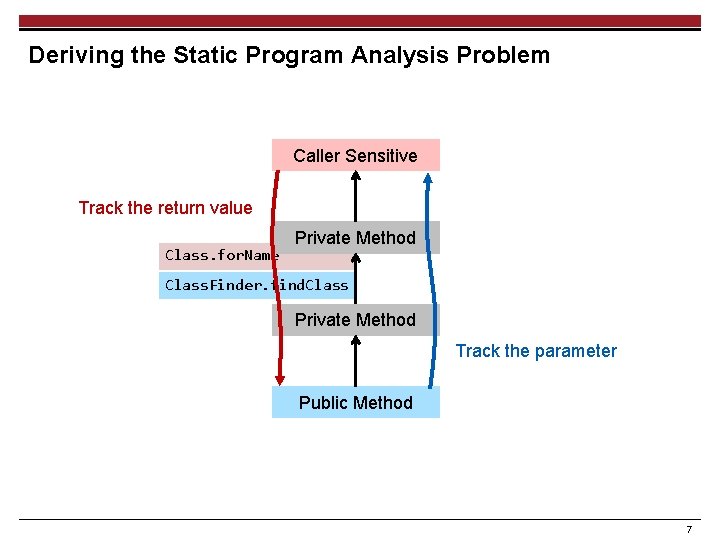
Deriving the Static Program Analysis Problem Caller Sensitive Track the return value Class. for. Name Private Method Privileged Class. Loader Class. Finder. find. Class Privileged Class. Loader Attacker. do. Evil. Private Method Unprivileged Class. Loader My. Applet. init Unprivileged Class. Loader Track the parameter Public Method 7

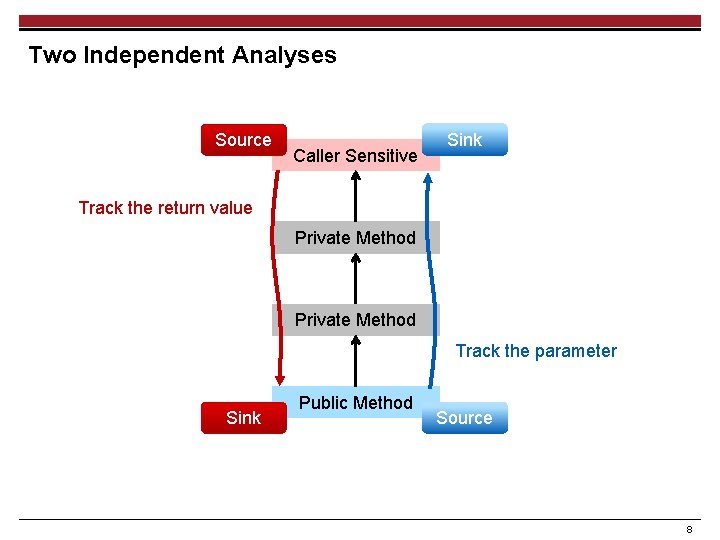
Two Independent Analyses Source Caller Sensitive Sink Track the return value Private Method Track the parameter Sink Public Method Source 8

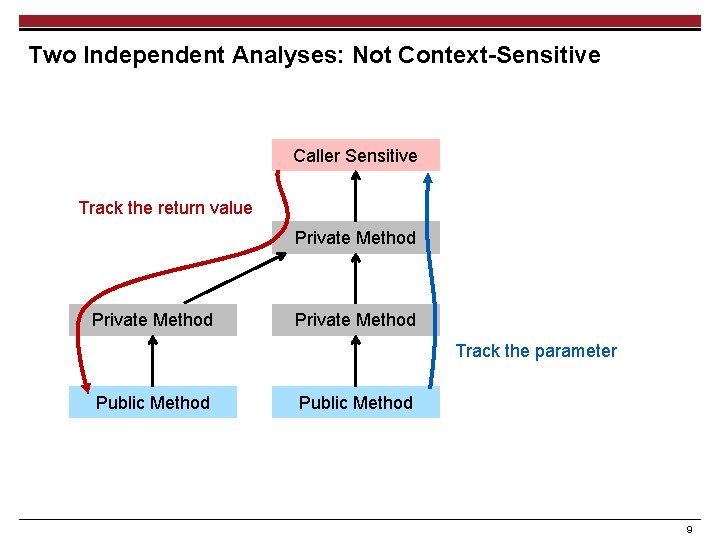
Two Independent Analyses: Not Context-Sensitive Caller Sensitive Track the return value Private Method Track the parameter Public Method 9

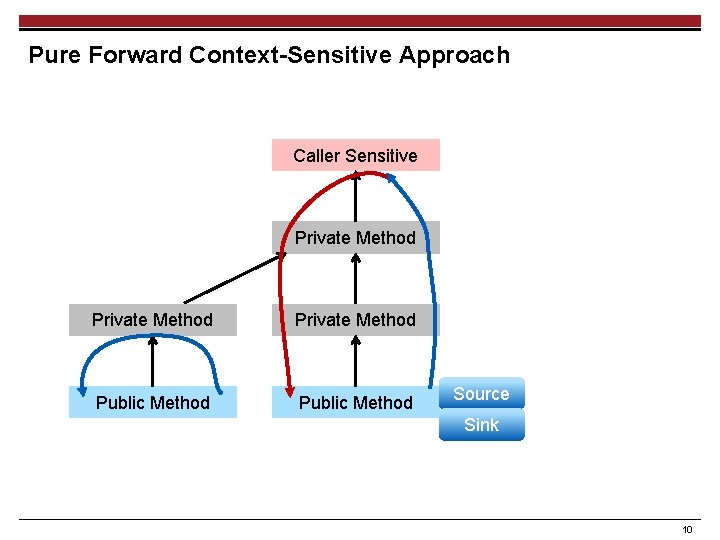
Pure Forward Context-Sensitive Approach Caller Sensitive Private Method Public Method Source Sink 10
![Results only Class for Name 40 35 Runtime min 30 25 20 15 Results – only Class. for. Name 40 35 Runtime [min] 30 25 20 15](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-11.jpg)
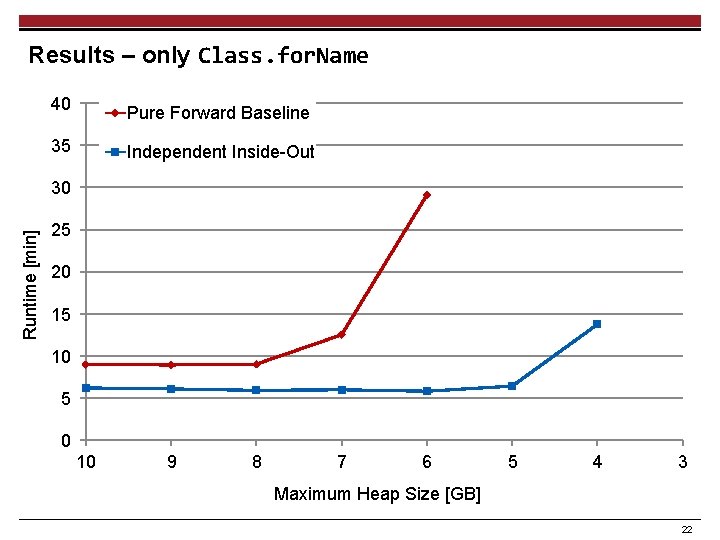
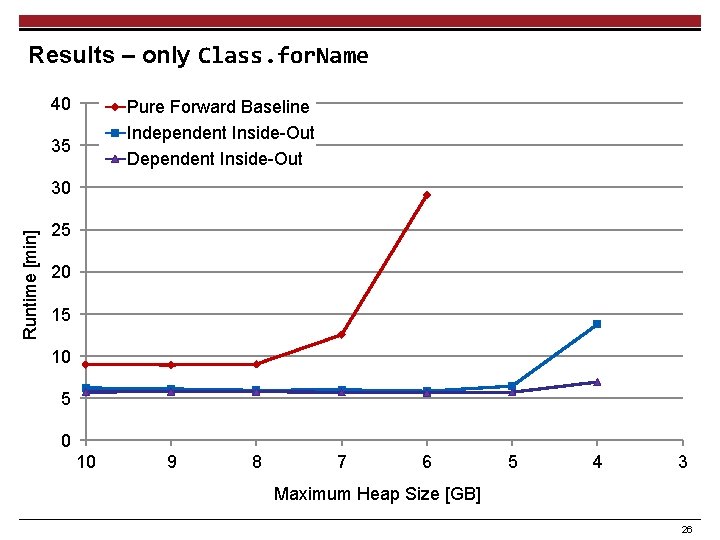
Results – only Class. for. Name 40 35 Runtime [min] 30 25 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 11
![Results all Caller Sensitive Methods 40 35 Runtime min 30 25 Did not Results – all Caller Sensitive Methods 40 35 Runtime [min] 30 25 Did not](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-12.jpg)
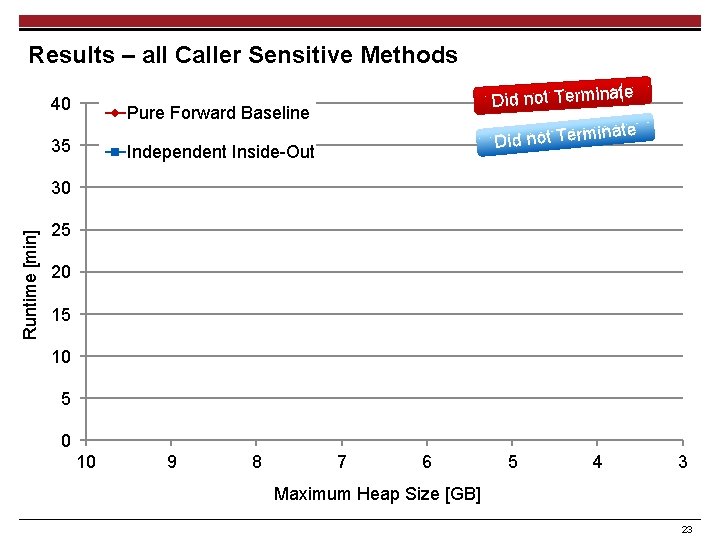
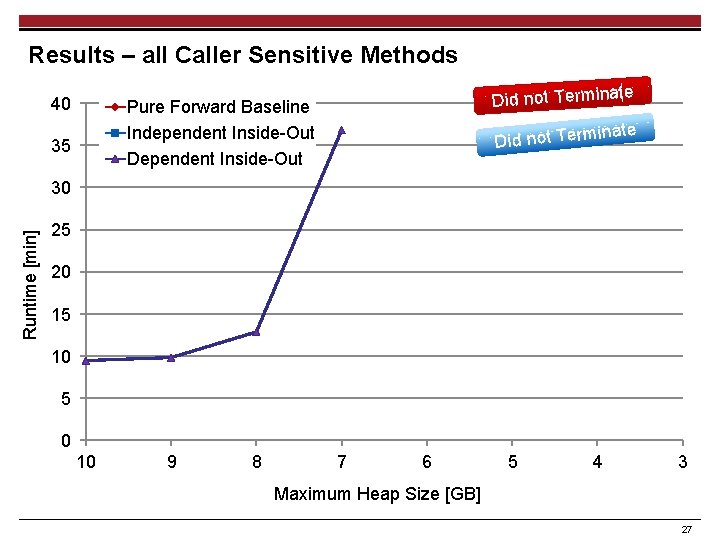
Results – all Caller Sensitive Methods 40 35 Runtime [min] 30 25 Did not Terminate 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 12

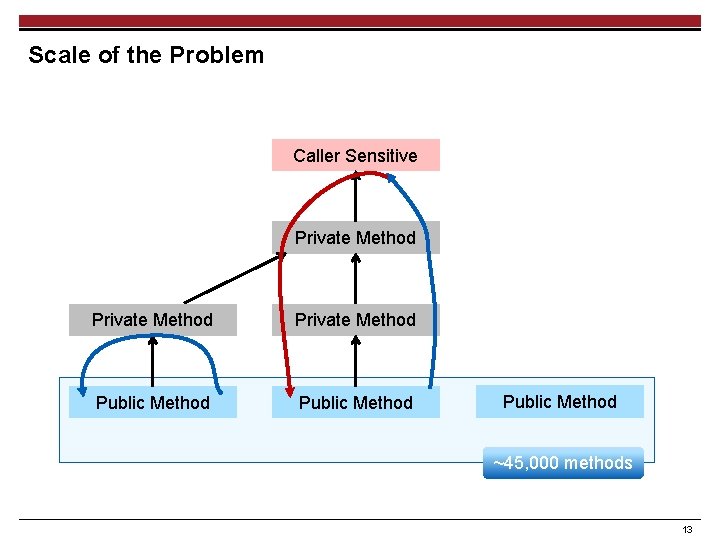
Scale of the Problem Caller Sensitive Private Method Public Method ~45, 000 methods 13

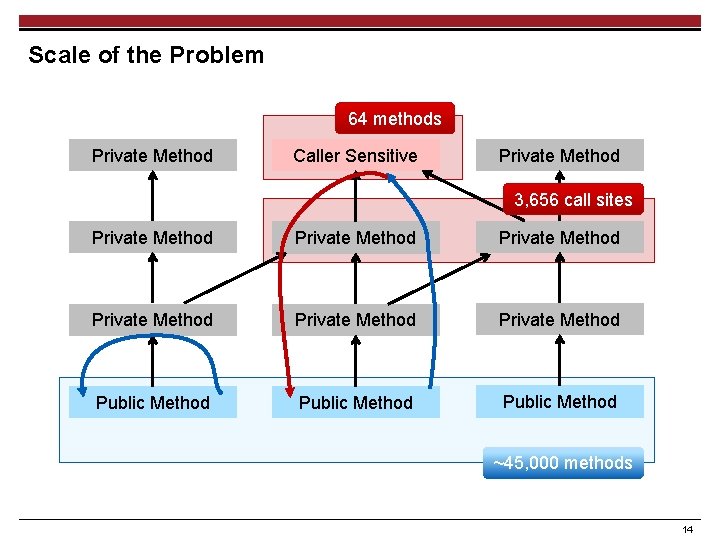
Scale of the Problem 64 methods Private Method Caller Sensitive Private Method 3, 656 call sites Private Method Private Method Public Method ~45, 000 methods 14

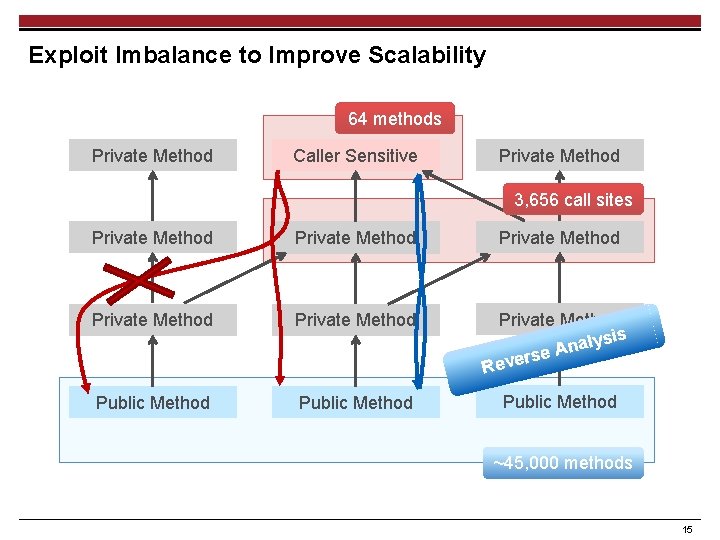
Exploit Imbalance to Improve Scalability 64 methods Private Method Caller Sensitive Private Method 3, 656 call sites Private Method Private Method ysis l a n rse A e v e R Public Method ~45, 000 methods 15
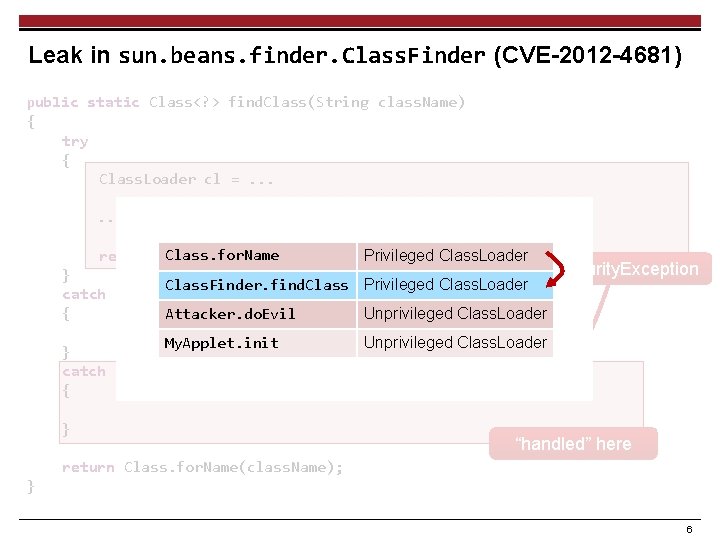
![IFDS Algorithm 17 19 Reports Leaks Caller Sensitive Public Method 16 IFDS Algorithm [17, 19] Reports Leaks Caller Sensitive ? Public Method 16](https://slidetodoc.com/presentation_image/eecb186c2a54686c311801da17e97768/image-16.jpg)
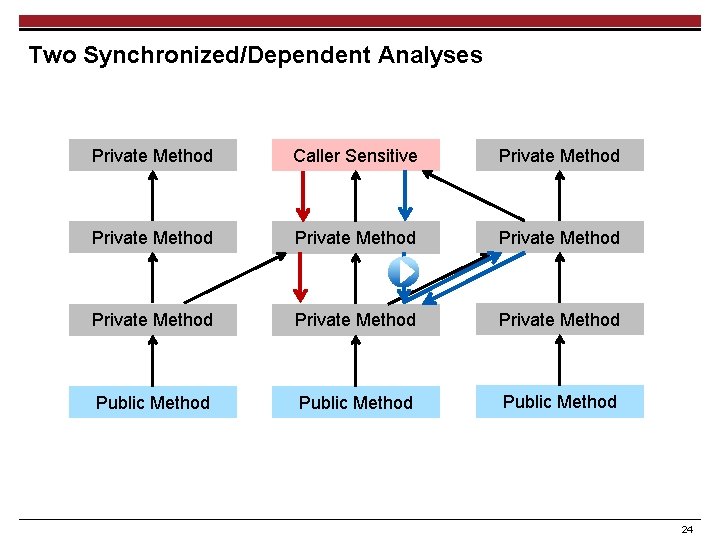
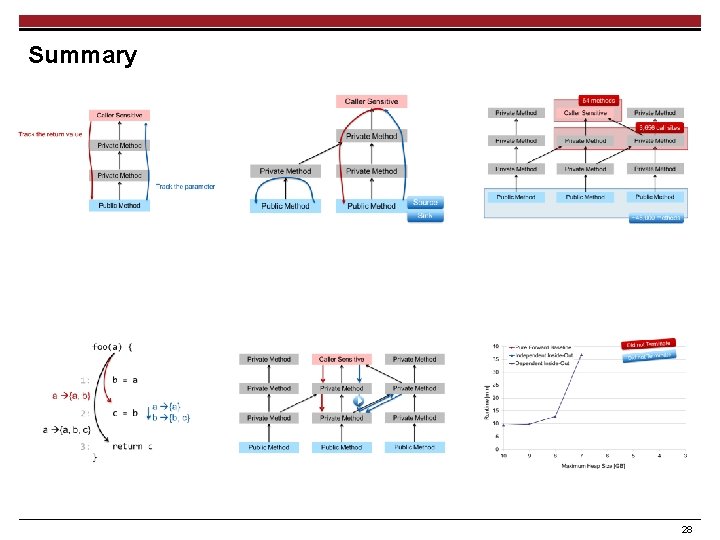
IFDS Algorithm [17, 19] Reports Leaks Caller Sensitive ? Public Method 16

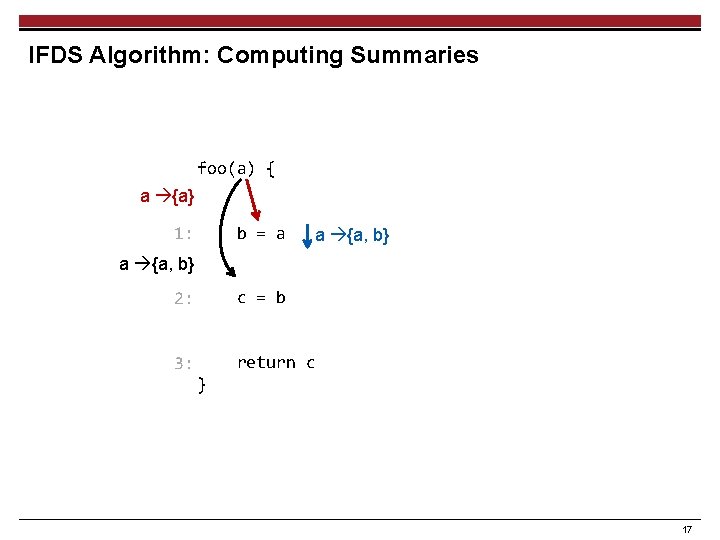
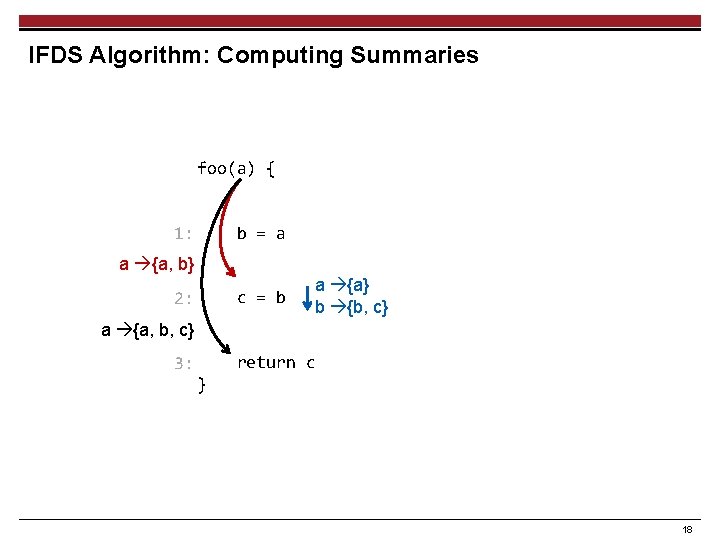
IFDS Algorithm: Computing Summaries foo(a) { a {a} b = a 1: a {a, b} 2: c = b 3: return c } 17

IFDS Algorithm: Computing Summaries foo(a) { b = a 1: a {a, b} c = b 2: a {a} b {b, c} a {a, b, c} 3: return c } 18

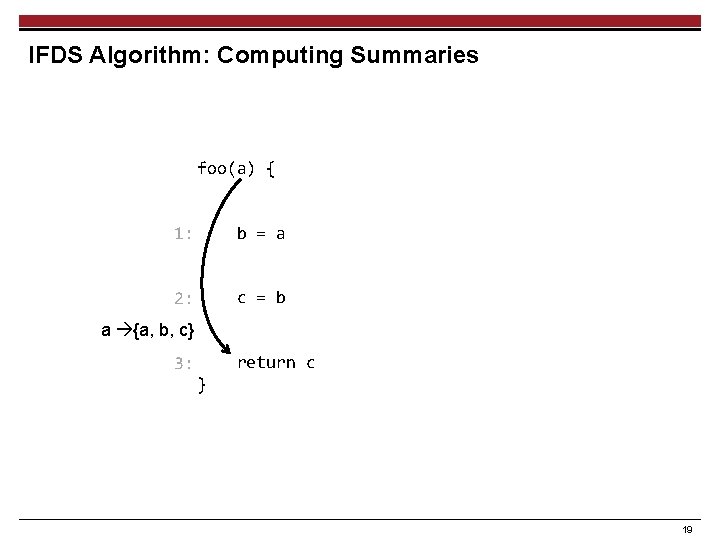
IFDS Algorithm: Computing Summaries foo(a) { 1: b = a 2: c = b a {a, b, c} 3: return c } 19

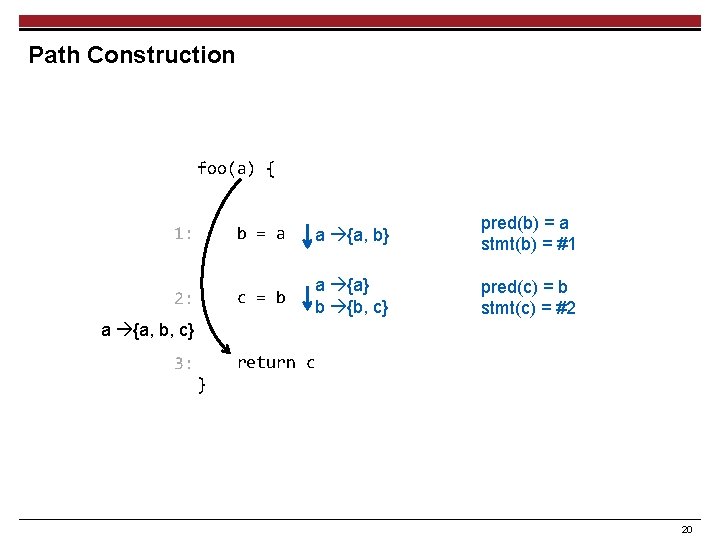
Path Construction foo(a) { 1: b = a a {a, b} pred(b) = a stmt(b) = #1 2: c = b a {a} b {b, c} pred(c) = b stmt(c) = #2 a {a, b, c} 3: return c } 20

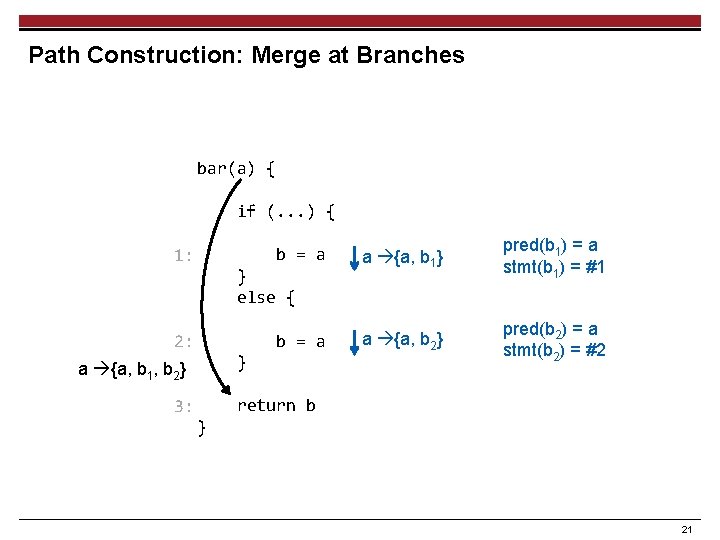
Path Construction: Merge at Branches bar(a) { if (. . . ) { b = a 1: } else { b = a 2: } a {a, b 1, b 2} 3: a {a, b 1} pred(b 1) = a stmt(b 1) = #1 a {a, b 2} pred(b 2) = a stmt(b 2) = #2 return b } 21

Results – only Class. for. Name 40 Pure Forward Baseline 35 Independent Inside-Out Runtime [min] 30 25 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 22

Results – all Caller Sensitive Methods 40 Did not Terminate Pure Forward Baseline 35 inate Did not Term Independent Inside-Out Runtime [min] 30 25 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 23

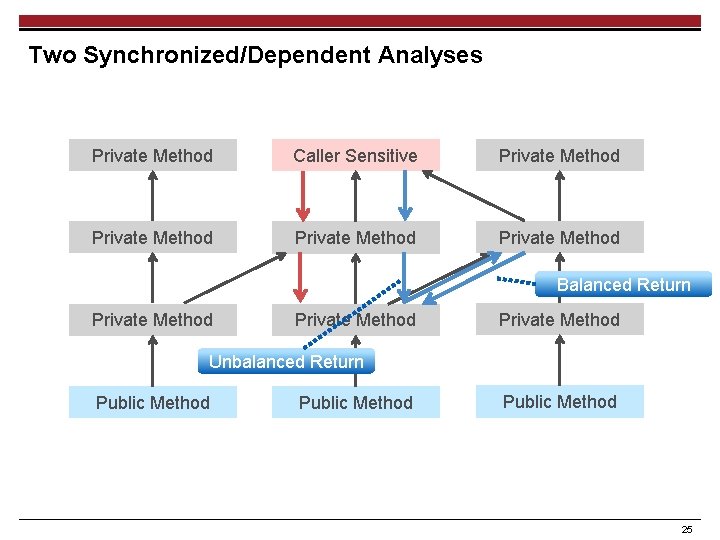
Two Synchronized/Dependent Analyses Private Method Caller Sensitive Private Method Private Method Public Method 24

Two Synchronized/Dependent Analyses Private Method Caller Sensitive Private Method Balanced Return Private Method Unbalanced Return Public Method 25

Results – only Class. for. Name 40 Pure Forward Baseline Independent Inside-Out Dependent Inside-Out 35 Runtime [min] 30 25 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 26

Results – all Caller Sensitive Methods 40 Did not Terminate Pure Forward Baseline Independent Inside-Out Dependent Inside-Out 35 inate Did not Term Runtime [min] 30 25 20 15 10 5 0 10 9 8 7 6 5 4 3 Maximum Heap Size [GB] 27

Summary 28