Final Exam Review Knowledge questions True or false





- Slides: 25

Final Exam Review • Knowledge questions • True or false statement (explain why) • Protocol • Calculation • Cover the contents after midterm coverage

Knowledge Question Examples • Three classes of switch fabric, speed relationship – What is Head-of-the-line (HOL) blocking? • Where can queue occur in router? • TCP header size? IP header size? UDP header size? • How many bits in IP of IPv 6? Address space size? Why it is very slow to be deployed? (enough IP space, hard upgrading and compatible) • Routing: what are Link state, distance vector? • Internet two-level routing? (inter-AS, intra-AS) • RIP, OSPF, BGP? Used where? – OSPF uses link state, BGP/RIP uses distance vector • Which is better? pure ALOHA, slotted ALOHA, CSMA/CD? – What are their assumptions? (collision detection, time syn) • CSMA/CD? CSMA/CA? Why wireless use CSMA/CA?

Knowledge Question Examples • • • Ethernet Broadcast MAC addr. ? What the broadcast address for? What is ARP? Why Ethernet is much better than aloha in efficiency? (homework 3) Hub vs. Switch? (homework 3) 802. 11 a, b, g: speed? Working frequency? 802. 15? (personal area network, example: bluetooth) Wireless no collision detection? – listen while sending, fading, hidden terminal • • Network security three elements: – Confidentiality, authentication, integrity What is public/symmetric key cryptography? Pro vs. con? Why use “nonce” in security? (replay attack) What is man-in-the-middle attack? Usage of firewall? (block outside active traffic to inside) IP spoofing? SYN flood Do. S attack? UDP flood? What is a botnet? Different between email virus vs. worm? – Vulnerability, user interaction to propagate, speed • IPSec vs. SSL? (different layers, tcp vs. udp)

Protocol Problem Examples • NAT address translation procedure • Digital signature procedure • HTTPS connection procedure – CA, public key • Secure email (assume known public key) – Confidentiality – Integrity

Calculation Examples • • • Homework 3 prob. 7 (subnet addressing) Homework 2, prob. 9 -11 (link state, distance vector) Homework 3, prob. 4 (parity checking) Homework 3, prob. 5 (CRC calculation) Homework 3, prob. 11 (wireless MAC protocol) Caesar cipher decrypt, Vigenere cipher, one-time pad decrypt (given the pad)

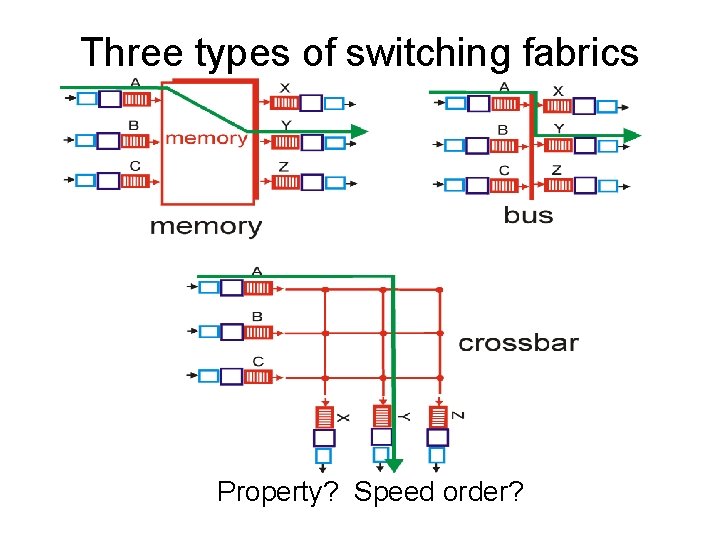
Three types of switching fabrics Property? Speed order?

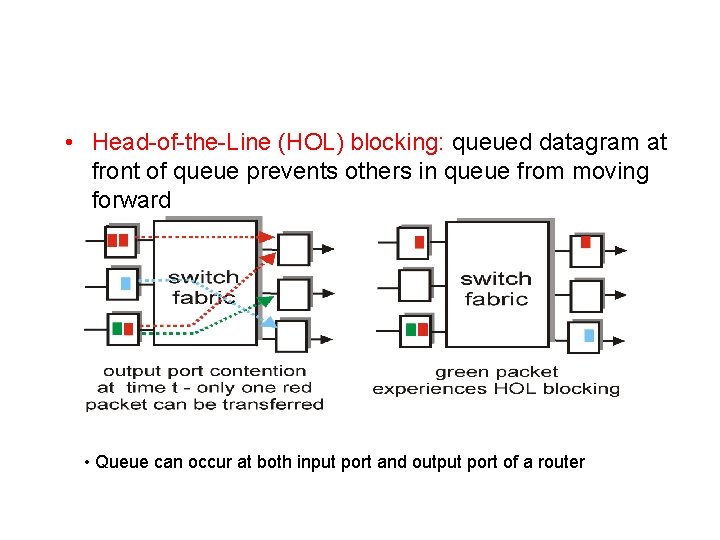
• Head-of-the-Line (HOL) blocking: queued datagram at front of queue prevents others in queue from moving forward • Queue can occur at both input port and output port of a router

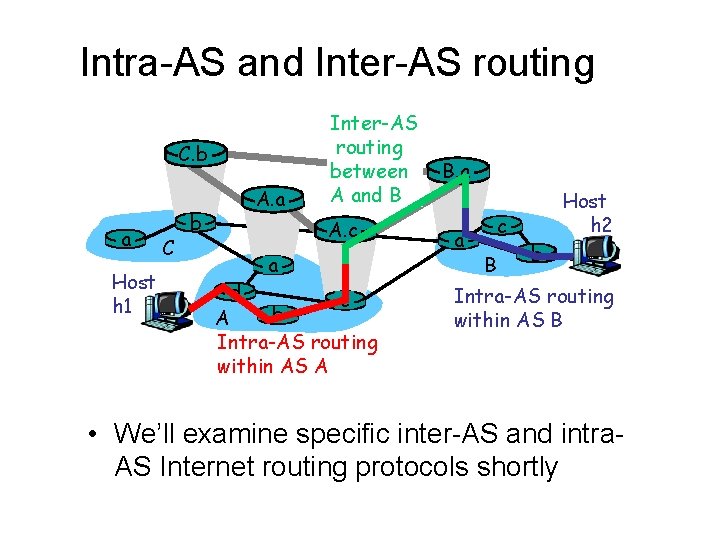
Intra-AS and Inter-AS routing C. b a Host h 1 C b A. a Inter-AS routing between A and B A. c a d c b A Intra-AS routing within AS A B. a a c B Host h 2 b Intra-AS routing within AS B • We’ll examine specific inter-AS and intra. AS Internet routing protocols shortly

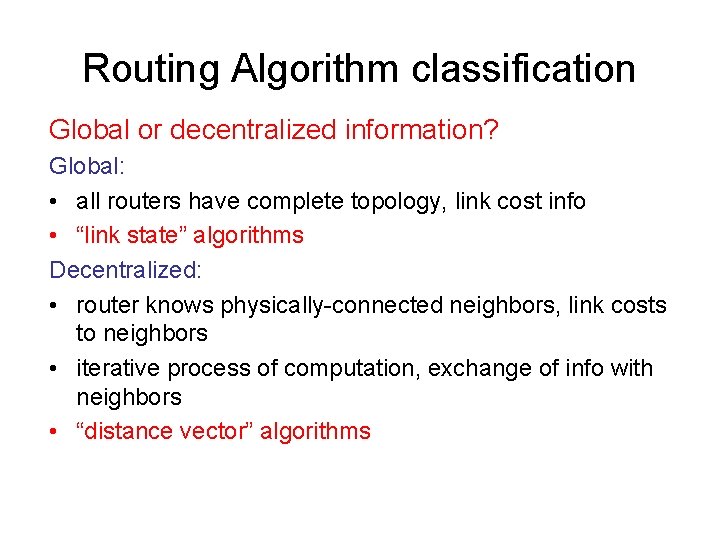
Routing Algorithm classification Global or decentralized information? Global: • all routers have complete topology, link cost info • “link state” algorithms Decentralized: • router knows physically-connected neighbors, link costs to neighbors • iterative process of computation, exchange of info with neighbors • “distance vector” algorithms

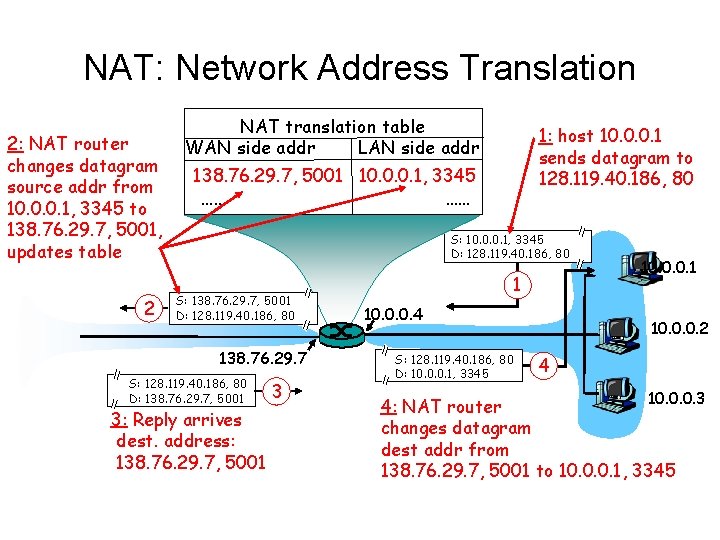
NAT: Network Address Translation 2: NAT router changes datagram source addr from 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, updates table 2 NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 sends datagram to 128. 119. 40. 186, 80 138. 76. 29. 7, 5001 10. 0. 0. 1, 3345 …… …… S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 1 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345

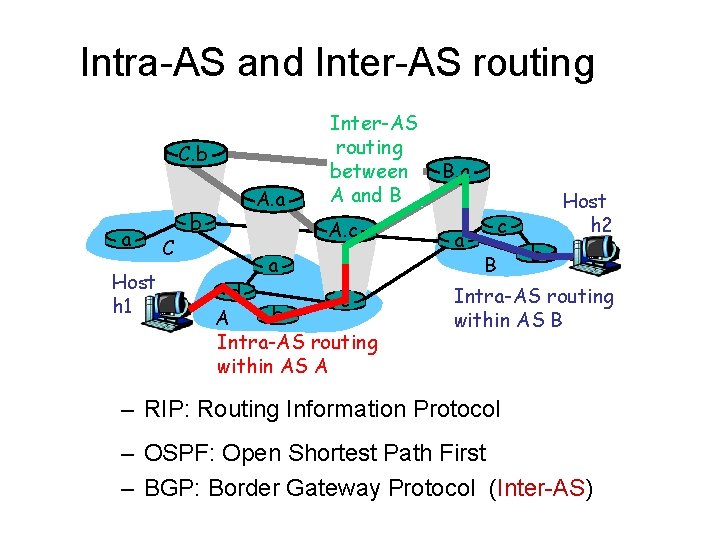
Intra-AS and Inter-AS routing C. b a Host h 1 C b A. a Inter-AS routing between A and B A. c a d c b A Intra-AS routing within AS A B. a a c B Host h 2 b Intra-AS routing within AS B – RIP: Routing Information Protocol – OSPF: Open Shortest Path First – BGP: Border Gateway Protocol (Inter-AS)

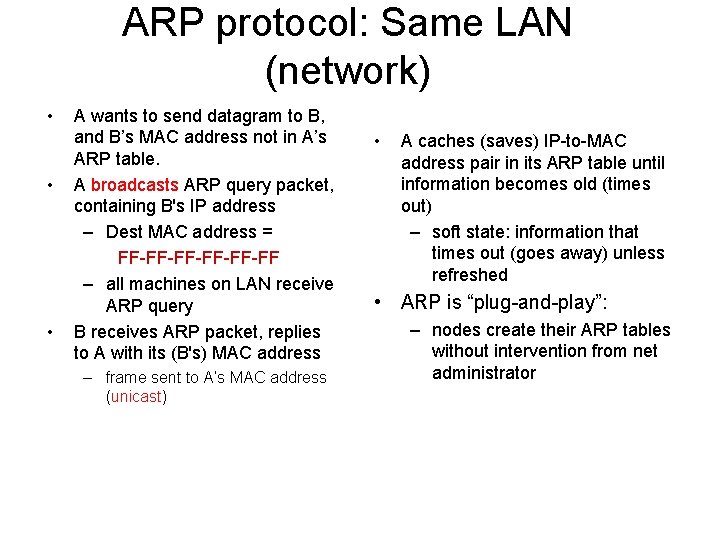
ARP protocol: Same LAN (network) • • • A wants to send datagram to B, and B’s MAC address not in A’s ARP table. A broadcasts ARP query packet, containing B's IP address – Dest MAC address = FF-FF-FF-FF – all machines on LAN receive ARP query B receives ARP packet, replies to A with its (B's) MAC address – frame sent to A’s MAC address (unicast) • A caches (saves) IP-to-MAC address pair in its ARP table until information becomes old (times out) – soft state: information that times out (goes away) unless refreshed • ARP is “plug-and-play”: – nodes create their ARP tables without intervention from net administrator

What is network security? Confidentiality: only sender, intended receiver should “understand” message contents – sender encrypts message – receiver decrypts message Authentication: sender, receiver want to confirm identity of each other – Virus email really from your friends? – The website really belongs to the bank? Message Integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection – Digital signature

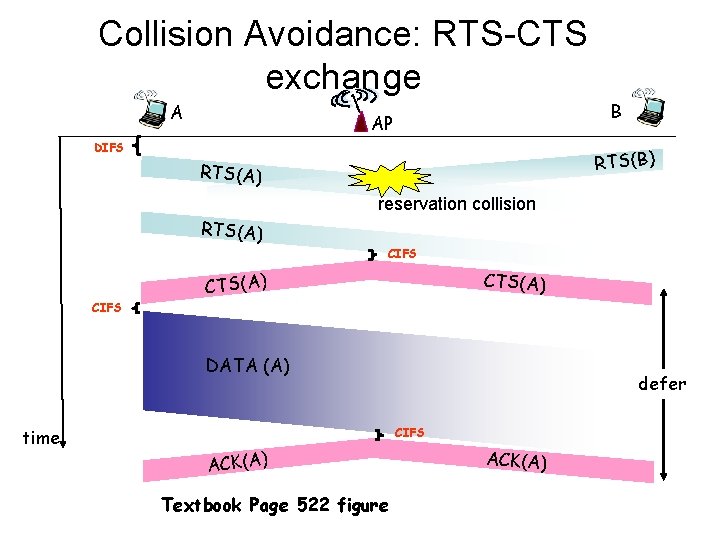
Collision Avoidance: RTS-CTS exchange A B AP DIFS RTS(B) RTS(A) reservation collision RTS(A) CIFS CTS(A) DATA (A) time defer CIFS ACK(A) Textbook Page 522 figure ACK(A)

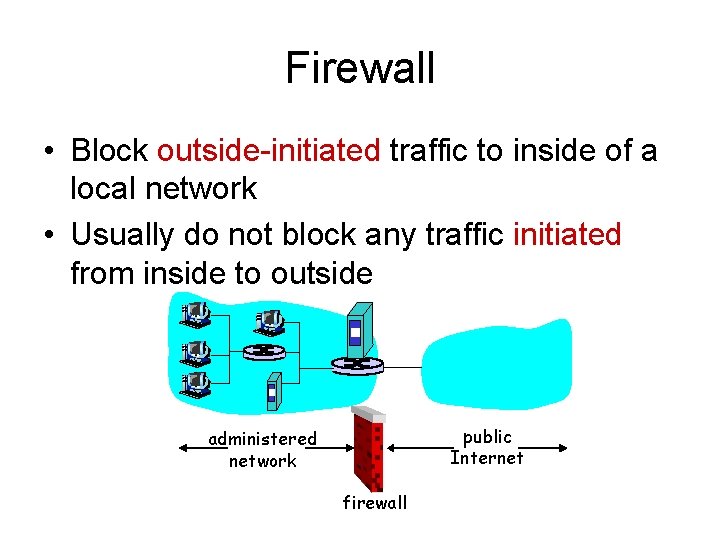
Firewall • Block outside-initiated traffic to inside of a local network • Usually do not block any traffic initiated from inside to outside public Internet administered network firewall

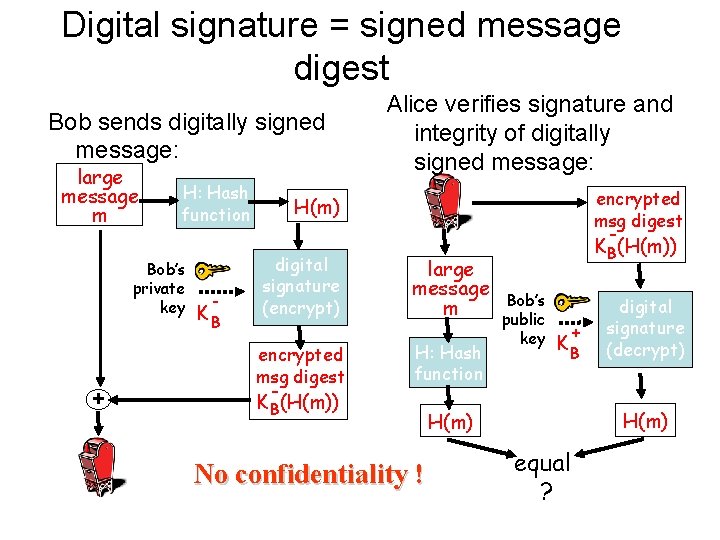
Digital signature = signed message digest Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB Alice verifies signature and integrity of digitally signed message: encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function No confidentiality ! KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ?

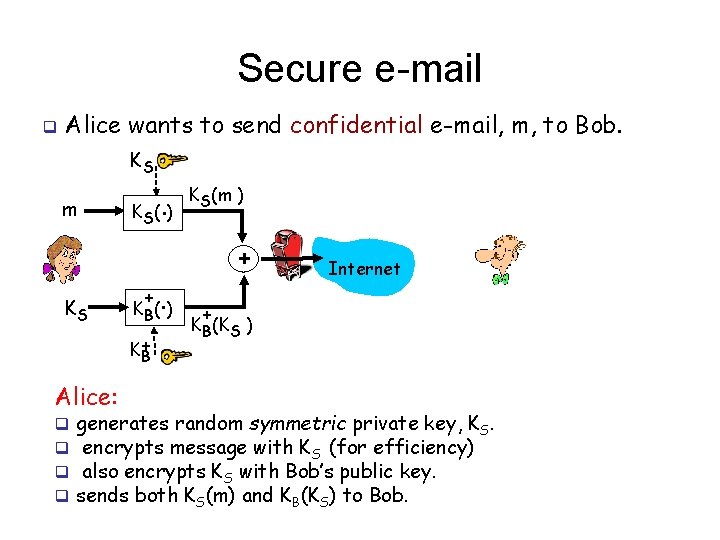
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Alice: q q . K B( ) KS(m ) + Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob.

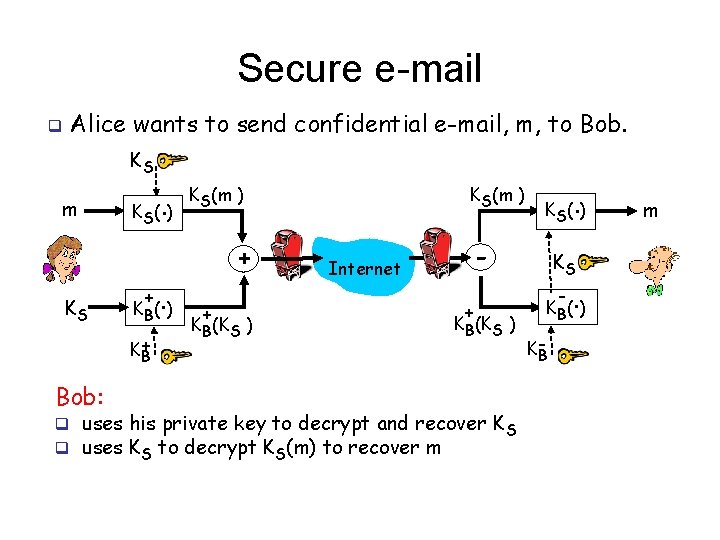
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Bob: . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m KS - . K B( ) KB m

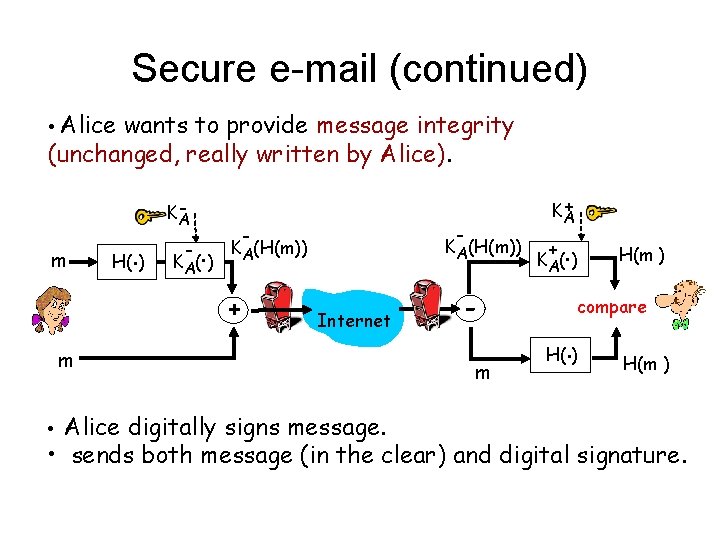
Secure e-mail (continued) • Alice wants to provide message integrity (unchanged, really written by Alice). m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m • Alice digitally signs message. m + . K A( ) H(m ) compare . H( ) H(m ) • sends both message (in the clear) and digital signature.

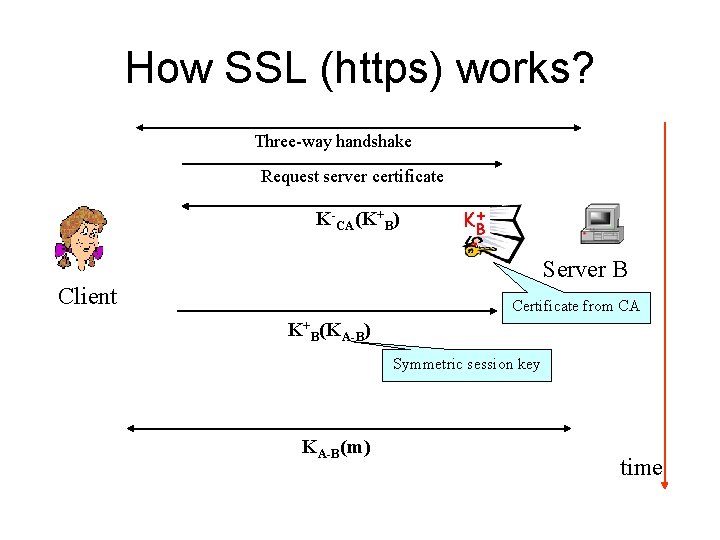
How SSL (https) works? Three-way handshake Request server certificate K-CA(K+B) KB+ Server B Client Certificate from CA K+B(KA-B) Symmetric session key KA-B(m) time

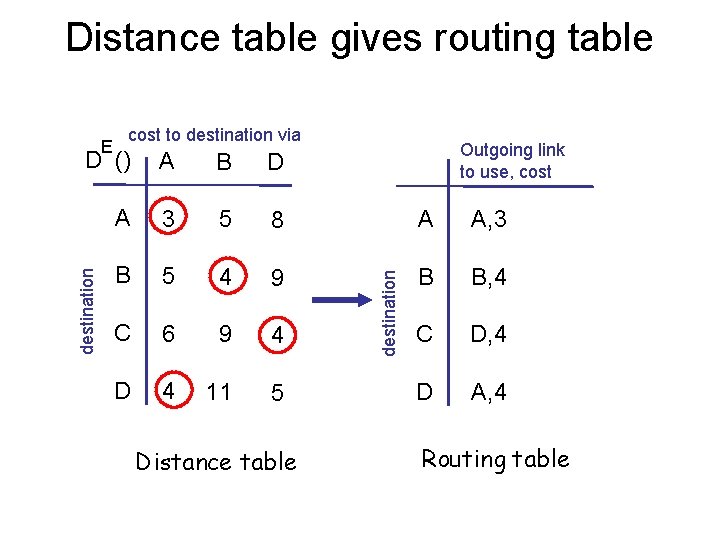
Distance table gives routing table E cost to destination via Outgoing link to use, cost B D A 3 5 8 A A, 3 B 5 4 9 B B, 4 C 6 9 4 C D, 4 D 4 11 5 D A, 4 Distance table destination A destination D () Routing table

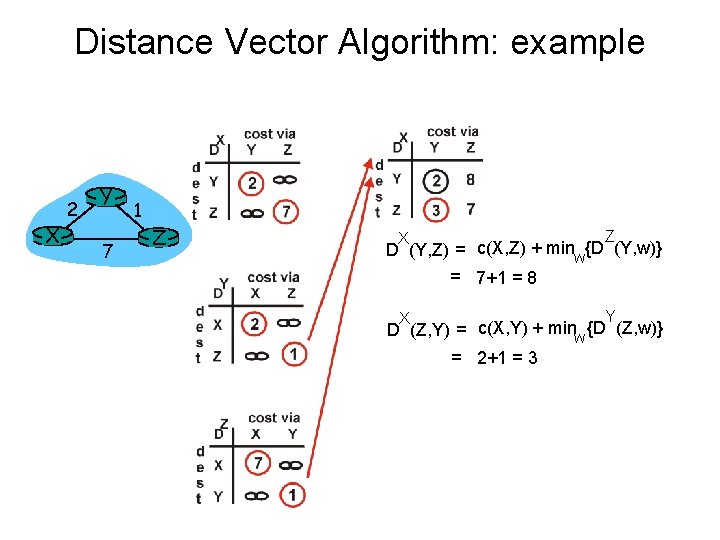
Distance Vector Algorithm: example X 2 Y 7 1 Z Z X D (Y, Z) = c(X, Z) + minw{D (Y, w)} = 7+1 = 8 Y X D (Z, Y) = c(X, Y) + minw {D (Z, w)} = 2+1 = 3

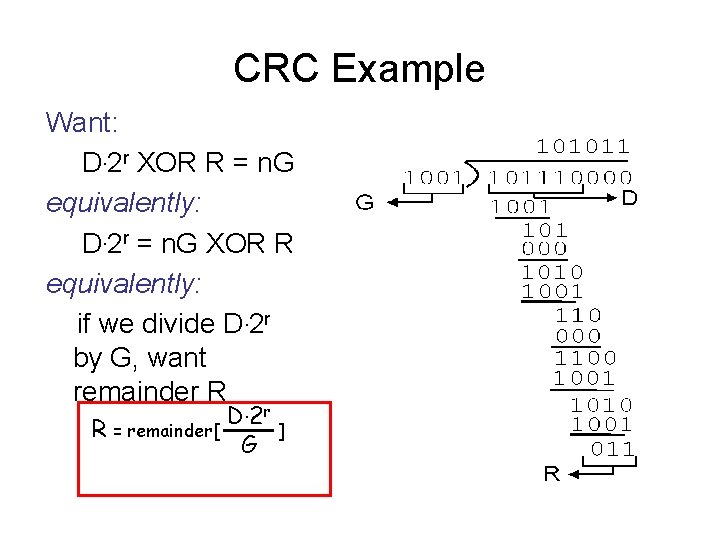
CRC Example Want: D. 2 r XOR R = n. G equivalently: D. 2 r = n. G XOR R equivalently: if we divide D. 2 r by G, want remainder R R = remainder[ D. 2 r G ]

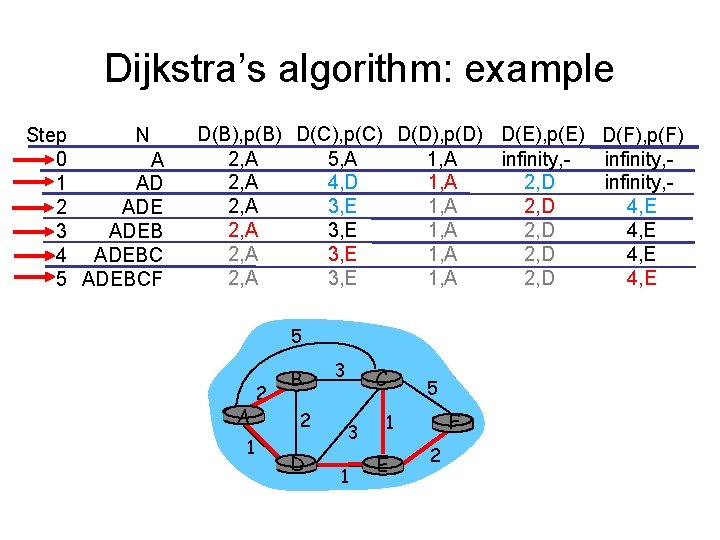
Dijkstra’s algorithm: example Step N 0 A 1 AD 2 ADE 3 ADEB 4 ADEBC 5 ADEBCF D(B), p(B) D(C), p(C) D(D), p(D) D(E), p(E) D(F), p(F) 2, A 5, A 1, A infinity, 2, A 4, D 1, A 2, D infinity, 2, A 3, E 1, A 2, D 4, E 5 A 1 2 B 2 D 3 C 3 1 5 F 1 E 2

• Caesar cipher decrypt: – “welcome”, key= +2 • Vigenere cipher – “final exam” key=3, 4, -1 (blank space does not change)