Final Exam Study Guide The Final Exam Exam



































- Slides: 37

Final Exam Study Guide � The Final Exam • Exam Questions � Review • • Lab Exercises 5/6 and 7 Technology in Focus 5 Sound-bytes 11 to 13 Chapters 11 to 13 �Please see the midterm study guides for the covered topics from chapter 1 to 10 1

The Final Exam � When • Tuesday, May 6, 2008 • 5: 45 – 8: 00 pm • MSB 115 � � 25 % of your final grade Covers • Chapters 1 to 13 • Sound-bytes 1 to 13 • Technology in Focuses 1 to 5 • Lab exercises 1 to 7 � � � This is an open-notes exam. All in-class hand-outs are allowed. Writing on your notes is ok! You may not use a textbook, a computer, or any electronic device. You may see questions from the midterm exams and quizzes again. 2

Exam Questions � 100 questions (25% of the total grade) • 30 multiple-choice questions • 30 true/false questions • 40 matching question 3

Lab Exercises Lab exercise 5/6 � • • Creating basic presentation slides using Microsoft Power. Point software Learn more about computing artifacts Lab exercise 7 � • Creating a small relational database using Microsoft Access software 4

Technology in Focus l Technology in Focus 5: The History of Computers l Data storage devices l From punch cards to DVDs l Personal computers l From Altair 8800 to modern day PC l DOS/MS-DOS Operating systems l Software applications 5

Sound-bytes l l l Collect data in Access 2007 by using email A day in the life of a network technician The history of the personal computers 6

Technology in Action Chapter 11 Behind the Scenes: Databases and Information Systems 7

Chapter Topics � Databases and their uses � Database components � Types of databases � Database management systems � Relational databases � Data warehouses and data marts � Information systems � Data mining 8

Chapter 11 Summary Questions � What is a database and why is it beneficial to use databases? • Databases are electronic collections of related data that help us organize data so that we can more easily access and use it. • By creating an organized structure for data, we hope to make data more meaningful and therefore more useful. In other words, we are attempting to turn data into information. 9

Chapter 11 Summary Questions �What components make up a database? • The three main components of a database are �Fields �Records �Tables 10

Chapter 11 Summary Questions � What types of databases are there? • Relational databases �Organize data in a (two-dimensional) table �Link tables to each other through their primary keys �Relational databases excel in the storage of structured (analytical) data. • Object-oriented databases �Stores data in objects �more adept at handling unstructured data, including audio clips, video clips, pictures, and extremely large documents • Multidimensional databases �Stores data in multiple dimensions �Can easily be customized for a variety of users �Process data much faster than pure relational database 11

Chapter 11 Summary Questions � What do database management systems do? • DBMSs are specially designed application software (such as MS Access) that interacts with the user, other applications, and database itself to capture and analyze data • Four main operations of a DBMS are: 1. Creating databases and entering data 2. Viewing and sorting data 3. Extracting data 4. Outputting data 12

Chapter 11 Summary Questions � How do relational databases organize and manipulate data? • Relational databases operate by organizing data into various tables based on logical groupings. • In relational databases, the links between tables that define how the data is related are referred to as relationships. • To establish a relationship between two tables, both tables must have a common field (or column). • In databases, the goal is to reduce data redundancy by recording data only once. This process is called normalization of the data. 13

Chapter 11 Summary Questions � What are data warehouses and data marts and how are they used? • A data warehouse is a large-scale electronic repository of data that contains and organizes in one place all the data related to an organization. Individual databases contain a wealth of information, but each database’s information usually pertains to one topic. • Data warehouses consolidate information from disparate sources to present an enterprise-wide view of business operations. • Data in the data warehouse is organized by subject. Most databases focus on one specific operational aspect of business operations. • Data marts are small slices of the data warehouse. 14

Chapter 11 Summary Questions � What is an information system and what types of information systems are used in business? • Information systems are software-based solutions used to gather and analyze information. Databases, data marts, and data warehouses are integral parts of information systems because they store the information that makes information systems functional. • All information systems perform similar functions, including �acquiring data �processing that data into information �storing the data, and �providing the user with output options with which to make the information meaningful and useful. • Most information systems fall into one of four categories: �office support systems, �transaction processing systems, �management information systems, and �decision support systems. • Each type of system almost always involves the use of one or more databases. 15

Chapter 11 Summary Questions �What is data mining and how does it work? • Data mining is the process by which great amounts of data are analyzed and investigated. The objective is to spot significant patterns or trends within the data that would otherwise not be obvious. 16

Technology in Action Chapter 12 Behind the Scenes: Networking and Security 17

Chapter Topics � � � Advantages of business networks Client/server vs. peer-to-peer networks Classifications of client/server networks Client/server network components Types of servers Network topologies Types of transmission media Network software Network adapters Moving data in a client/server network Securing networks 18

Chapter 12 Summary Questions � What are the advantages of a business network? • Large business networks provide the following advantages: �They increase productivity. Networks allow workers to share data and peripherals with coworkers and communicate with them efficiently. �They enable people to share peripherals such as printers. �They enable software sharing. Installing a new version of software on everyone’s desktop in a company with 1, 000 employees can be timeconsuming. However, if the computers are networked, all employees can access the same copy of a program from the server. Although companies must still purchase a software license for each employee, with a network they avoid having to install the program on every desktop. �Through a network, large groups of employees can share one Internet connection, reducing Internet connectivity expenses. 19

Chapter 12 Summary Questions � How does a client/server network differ from a peer-to-peer network? • The main advantage of a client/server relationship is that it makes data flow more efficiently than in peer-to-peer networks. Servers can respond to requests from a large number of clients at the same time. • Also, servers are configured to perform specific tasks (such as handling e-mail or database requests) efficiently. • Client/server networks are also scalable networks, meaning additional users can be added easily without affecting the performance of the other network nodes. • In addition, whereas P 2 P networks are decentralized (users are responsible for creating their own data backups and for providing security for their computer), client/server networks are centralized, meaning all clients connect to a server that performs tasks for them. 20

Chapter 12 Summary Questions � What are the different classifications of client/server networks? • Local area networks (LANs) are generally smaller groups of • • computers and peripherals linked together over a relatively small geographic area. Wide area networks (WANs) comprise large numbers of users or separate LANs that are miles apart and linked together. Metropolitan area networks (MANs) are established WANs to link users in a specific geographic area (such as within a city or county). Personal area networks (PANs) are used to connect wireless devices (such as Bluetooth-enabled devices) in close proximity to each other. An intranet is a private corporate network that is used exclusively by company employees to facilitate information sharing, database access, group scheduling, videoconferencing, or other employee collaboration. 21

Chapter 12 Summary Questions � What components are needed to construct a client/server network? • Server. Unlike P 2 P networks, client/server networks contain at least one • • • computer that functions solely as a server. Network topology. Because client/server networks are more complex than P 2 P networks, the layout and structure of the network must be carefully planned. Transmission media (cable or wireless communications technology) is needed based on the network topology. Client/server networks use a wider variety of cable types than do simpler P 2 P networks. Network operating system (NOS) software. All client/server networks require network operating system (NOS) software, which is specialized software that is installed on servers and client computers that enables the network to function. Network adapters (or network interface cards) are attached or installed to each device on a client/server network. These adapters enable the computer (or peripheral) to communicate with the network using a common data communication language, or protocol. Network navigation devices. Because of the complexity of a client/server network, specialized network navigation devices (such as routers, hubs, and switches) are needed to move data signals around the network. 22

Chapter 12 Summary Questions � What do the various types of servers do? • The number and types of servers on a client/server network depend on the network’s size and workload. • As more users are added to a network, dedicated servers are used to fulfill one specific function (such as handling e-mail). When dedicated servers are deployed, the main server then becomes merely an authentication server and/or a file server. • Authentication servers keep track of who is logging on to the network and which services on the network are available to each user. Authentication servers also act as overseers for the network. They manage and coordinate the services provided by any other dedicated servers located on the network. • File servers store and manage files for network users. On corporate networks, employees are provided with space on a file server to store files they create. 23

Chapter 12 Summary Questions �What are the various network topologies? • Network topology refers to the physical or logical arrangement of computers, transmission media (cable), and other network components. • The most common client/server network topologies are bus, ring, and star. • Combining multiple topologies into one network is known as constructing a hybrid topology. 24

Chapter 12 Summary Questions � What types of transmission media are used in client/server networks? • Transmission media comprises the routes data takes to flow between devices on the network. • For business networks, the three main cable types that are used today are twisted pair, coaxial, and fiber-optic. Wireless networks are another popular option. 25

Chapter 12 Summary Questions � What software needs to be running on computers attached to a client/server network? • Network operating system (NOS) needs to be installed on each client computer and server connected to the network to provide the services necessary for them to communicate. • Many modern operating systems (such as Windows XP and Mac OS X) include NOS client software as part of the basic installation. • However, if your OS does not include NOS client software, it must be installed on each client. 26

Chapter 12 Summary Questions � How do network adapters enable computers to participate in a client/server network? • Network adapters perform three critical functions: �They generate high-powered signals to enable network transmissions. �They are responsible for breaking the data down into packets and preparing them for transmission across the network. �They act as gatekeepers for information flowing to and from the client computer. 27

Chapter 12 Summary Questions � What devices assist in moving data around a client/server network? • Repeaters are devices whose sole function is to amplify a signal and • • retransmit it. Repeaters are used to extend cable runs beyond the maximum run length (over which a signal would degrade and be unreadable). Hubs are devices that also transmit signals. In addition, they have multiple ports to which devices are connected. A switch can be viewed as a “smart” hub. It makes decisions, based on the MAC address of the data, as to where the data is to be sent. Therefore, only the intended recipient of the data receives the signal as opposed to a hub, which sends out data to all devices connected to it. Bridges are devices that are used to send data between different collision domains. Routers are designed to send information between two networks. To accomplish this, routers must look at higher-level network addresses (such as IP addresses), not MAC addresses. When the router notices data with an address that does not belong to a device on the network from which it originated, it sends the data to another network to which it is attached (or out onto the Internet). 28

Chapter 12 Summary Questions � What measures are employed to keep large networks secure? • To gain access to a typical client/server network, you have to enter a user ID • • and a password. This is a process known as authentication. However, authentication can also be achieved through the use of biometric devices and through possessed objects. Examples include identification badges, magnetic key cards, and smart keys. Each user has access privileges granted in accordance with his or her requirements. In this way, all activity on the network can be tracked to a particular user. Beyond this, physical protection of key equipment is accomplished by keeping servers in areas with highly limited access. These areas often have biometric access protection or special access cards. Biometrics identify users by a physical trait like fingerprints, retina scans, or facial recognition. These devices can be fooled and research is leading to newer biometric methods, but none are yet perfected. To protect a network from outside connection vulnerability, firewalls are installed that prevent unauthorized access into the network from ports into the Internet. 29

Technology in Action Chapter 13 Behind the Scenes: The Internet: How It Works 30

Chapter Topics � Managing the Internet � Interaction between Internet components � Internet data transmission and protocols � IP addresses and domain names � FTP and Telnet � HTML and XLM � How e-mail and instant messaging work and how to keep them secure 31

Chapter 13 Summary Questions � What data transmissions and protocols does the Internet use? • Although many protocols are available on the Internet, the main suite of protocols used is TCP/IP. • The suite is named after the original two protocols that were developed for the Internet: the Transmission Control Protocol (TCP) and the Internet Protocol (IP). • TCP prepares data for transmission and provides for errorchecking and resending lost data. • IP is responsible for sending the information from one computer to another. 32

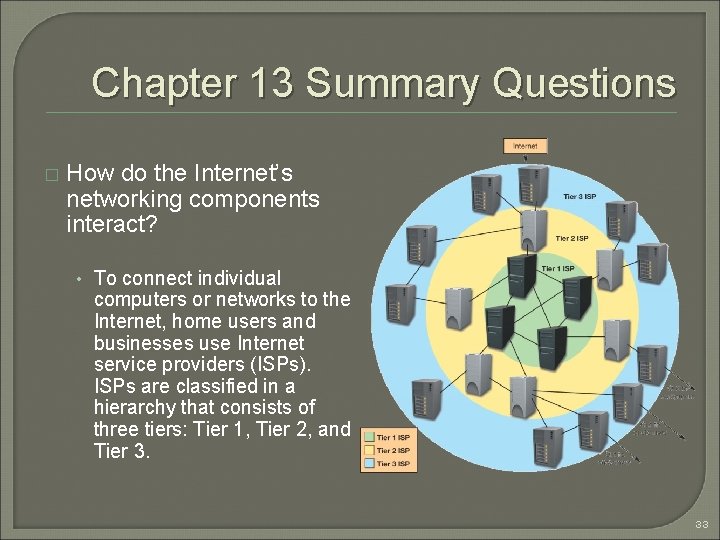
Chapter 13 Summary Questions � How do the Internet’s networking components interact? • To connect individual computers or networks to the Internet, home users and businesses use Internet service providers (ISPs). ISPs are classified in a hierarchy that consists of three tiers: Tier 1, Tier 2, and Tier 3. 33

Chapter 13 Summary Questions � Why are IP addresses and domain names important for Internet communications? • Each computer, server, or device connected to the Internet is required to have a unique number identifying it, called an IP address. • A domain name is simply a name that takes the place of an IP address, making it easier for people to remember. For example, google. com is a domain name. 34

Chapter 13 Summary Questions � What are FTP and Telnet and how do I use them? • The File Transfer Protocol (FTP) enables users to share files that reside on local computers with remote computers. If you’re attempting to download files using FTP to your local computer, the FTP client program first establishes a TCP session with the remote computer. • Telnet is both a protocol for connecting to a remote computer and a TCP/IP service that runs on a remote computer to make it accessible to other computers. Telnet enables you to take control of a remote computer (the server) with your computer (the client) and manipulate files and data on the server as if you were sitting in front of that server. 35

Chapter 13 Summary Questions � What are HTML and XML used for? • A Web page is merely a text document that is formatted using the Hypertext Markup Language (HTML). • The current version of HTML is called the Extensible Hypertext Markup Language (XHTML). XHTML has much more stringent rules than HTML regarding tagging (for instance, all elements require an end tag). • Extensible Markup Language (XML) is a set of tools you can use to create your own markup language. In a sense, it is a more flexible version of HTML/XHTML. 36

Chapter 13 Summary Questions � How does e-mail work? • E-mail uses a protocol first developed by Ray Tomlinson in 1971. Using the @ symbol, e-mail addresses place a user at a Web location. The protocol works in a client/server format where e-mail is sent to a server and is forwarded to another server where it is retrieved by the addressee. • Just like other kinds of data that flow along the Internet, e-mail has its own protocol. The Simple Mail Transfer Protocol (SMTP) is responsible for sending e-mail along the Internet to its destination. • The Multipurpose Internet Mail Extensions (MIME) specification was introduced in 1991 to simplify adding attachments to e-mail messages. All e-mail client software now uses this protocol for attaching files. 37