Final Exam Review Knowledge questions True or false






- Slides: 22

Final Exam Review • Knowledge questions • True or false statement (explain why) • Protocol • Calculation • Cover the second half contents

Knowledge Question Examples • • Three classes of switch fabric Where can queue occur in router? TCP header size? IP header size? (20/20) How many bits in IP of IPv 6? Address space size? Routing: Link state vs. distance vector ? Internet two-level routing? (inter-AS, intra-AS) RIP, OSPF, BGP? Used where? – OSPF uses link state, BGP uses distance vector • Which is better? Slotted ALOHA, pure ALOHA, CSMA/CD? • CSMA/CD? CSMA/CA? Why wireless use csma/ca?

Knowledge Question Examples • MAC address bytes? Broadcast MAC addr. ? What the broadcast address for? What is ARP? • Why Ethernet is much better than aloha in efficiency? (homework 3) • Hub vs. Switch? (homework 3) • 802. 11 a, b, g: speed? Working frequency? • 802. 15? (personal area network) • Wireless no collision detection? (fading, hidden terminal) • Network security three elements: – Confidentiality, authentication, integrity • What is public key cryptography? • Why use “nonce” in security? (replay attack) • Usage of firewall? (block outside active traffic to inside) • IP spoofing? SYN flood Do. S attack?

Protocol Problem Examples • NAT address translation procedure • Digital signature procedure • HTTPS connection procedure – CA, public key • Secure email (assume known public key) – Confidentiality – Integrity

Calculation Examples • • • Homework 3 prob. 1 (subnet addressing) Homework 3, prob. 3 -4 (distance vector) Homework 3, prob. 7 (parity checking) CDMA calculation (textbook fig. 6. 5) Caesar cipher decrypt, Vigenere cipher, one-time pad decrypt (given the pad)

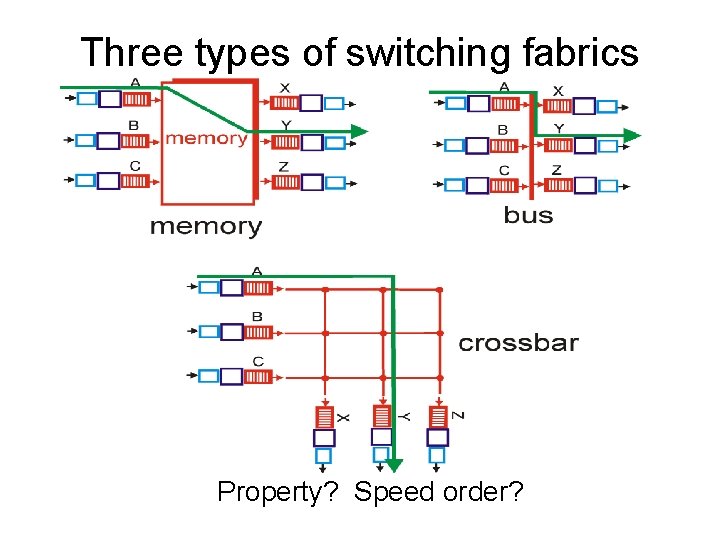
Three types of switching fabrics Property? Speed order?

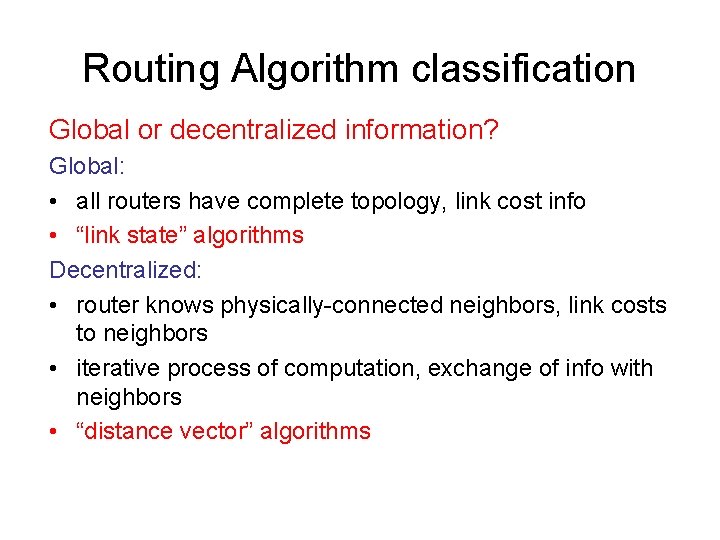
Routing Algorithm classification Global or decentralized information? Global: • all routers have complete topology, link cost info • “link state” algorithms Decentralized: • router knows physically-connected neighbors, link costs to neighbors • iterative process of computation, exchange of info with neighbors • “distance vector” algorithms

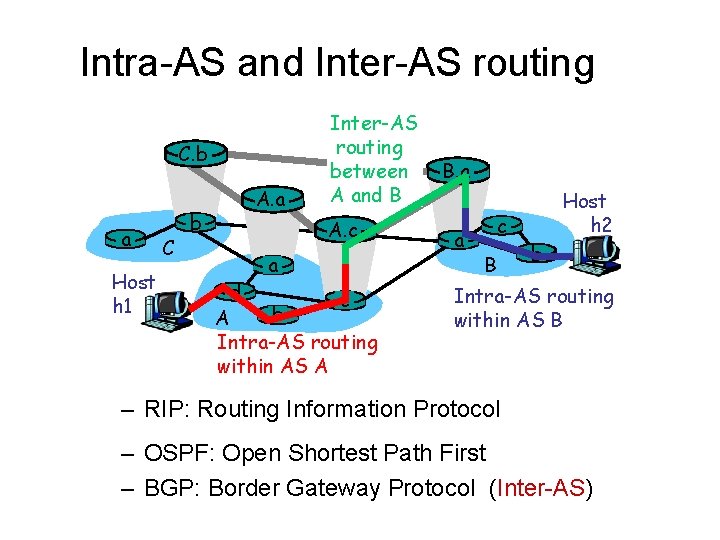
Intra-AS and Inter-AS routing C. b a Host h 1 C b A. a Inter-AS routing between A and B A. c a d c b A Intra-AS routing within AS A B. a a c B Host h 2 b Intra-AS routing within AS B – RIP: Routing Information Protocol – OSPF: Open Shortest Path First – BGP: Border Gateway Protocol (Inter-AS)

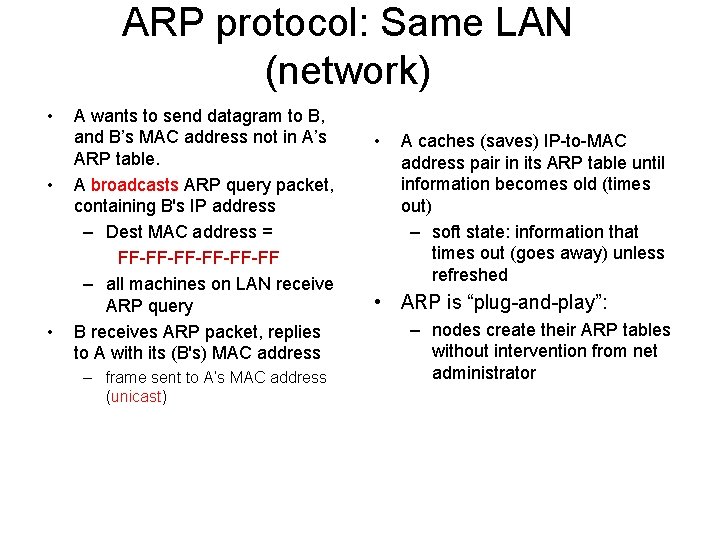
ARP protocol: Same LAN (network) • • • A wants to send datagram to B, and B’s MAC address not in A’s ARP table. A broadcasts ARP query packet, containing B's IP address – Dest MAC address = FF-FF-FF-FF – all machines on LAN receive ARP query B receives ARP packet, replies to A with its (B's) MAC address – frame sent to A’s MAC address (unicast) • A caches (saves) IP-to-MAC address pair in its ARP table until information becomes old (times out) – soft state: information that times out (goes away) unless refreshed • ARP is “plug-and-play”: – nodes create their ARP tables without intervention from net administrator

What is network security? Confidentiality: only sender, intended receiver should “understand” message contents – sender encrypts message – receiver decrypts message Authentication: sender, receiver want to confirm identity of each other – Virus email really from your friends? – The website really belongs to the bank? Message Integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection – Digital signature

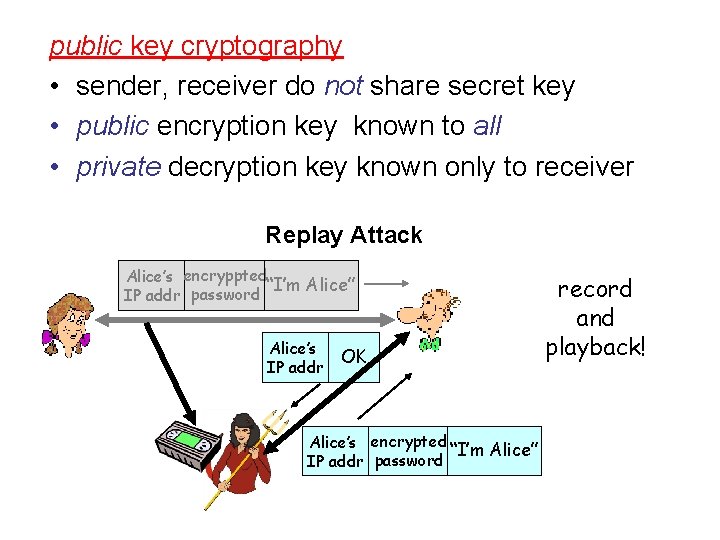
public key cryptography • sender, receiver do not share secret key • public encryption key known to all • private decryption key known only to receiver Replay Attack Alice’s encryppted “I’m Alice” IP addr password Alice’s IP addr OK Alice’s encrypted “I’m Alice” IP addr password record and playback!

Firewall • Block outside-initiated traffic to inside of a local network • Usually do not block any traffic initiated from inside to outside public Internet administered network firewall

– Denial-of-Service (Do. S) attack: • Send many fake requests to congest link or consume server resource (CPU, memory) – SYN flooding: • attacker sends many SYNs to victim; victim has to allocate connection resource; victim has no resource left for real connection requests any more. • Usually with spoofed source IP address • IP spoofing: – Attacker can generate “raw” IP packets directly from application, putting any value into IP source address field – Hide the identity of the traffic initiator

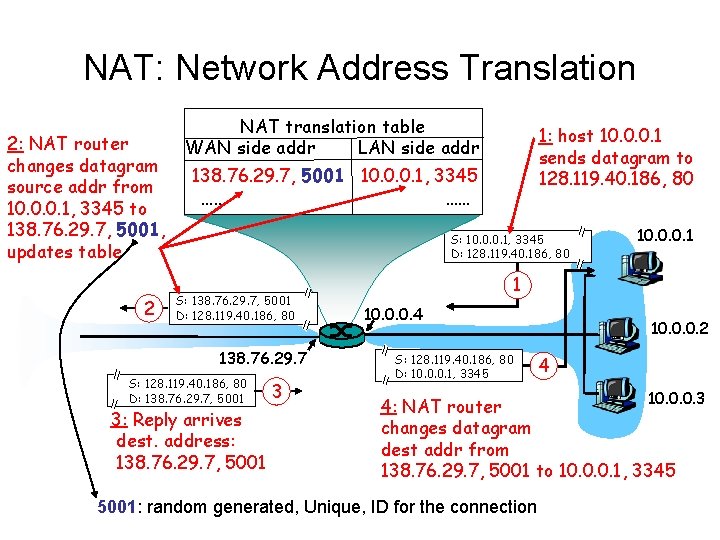
NAT: Network Address Translation 2: NAT router changes datagram source addr from 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, updates table 2 NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 sends datagram to 128. 119. 40. 186, 80 138. 76. 29. 7, 5001 10. 0. 0. 1, 3345 …… …… S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 10. 0. 0. 1 1 10. 0. 0. 4 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 10. 0. 0. 2 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345 5001: random generated, Unique, ID for the connection

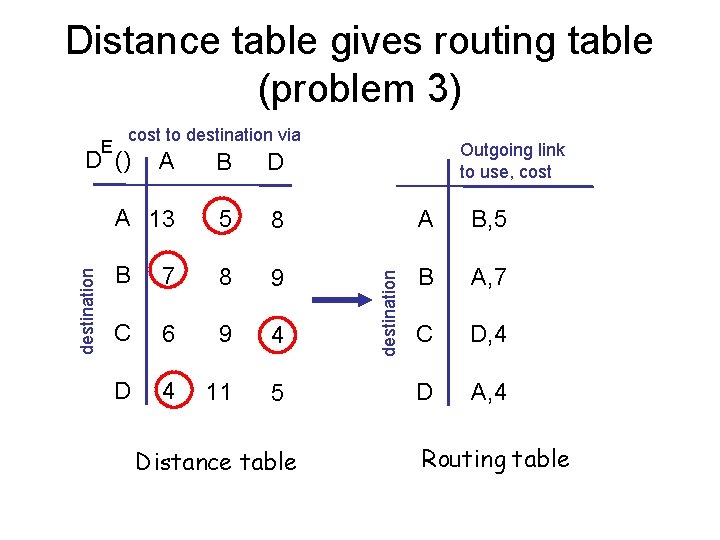
Distance table gives routing table (problem 3) cost to destination via destination D () Outgoing link to use, cost A B D A 13 5 8 A B, 5 B 7 8 9 B A, 7 C 6 9 4 C D, 4 D 4 11 5 D A, 4 Distance table destination E Routing table

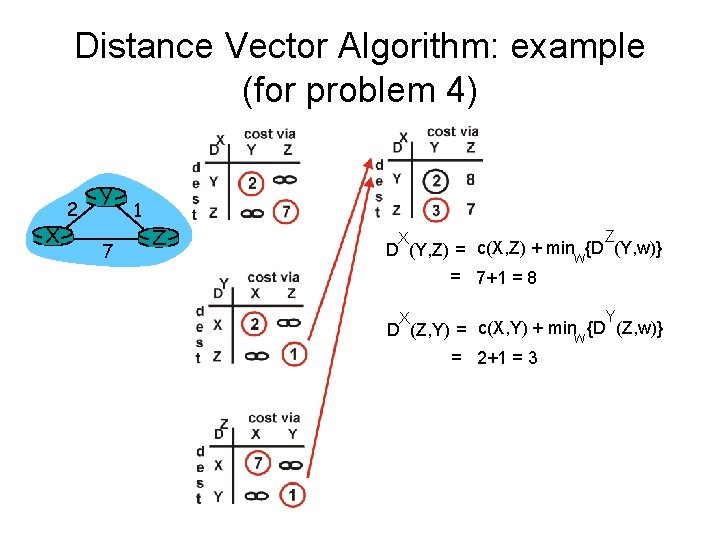
Distance Vector Algorithm: example (for problem 4) X 2 Y 7 1 Z Z X D (Y, Z) = c(X, Z) + minw{D (Y, w)} = 7+1 = 8 Y X D (Z, Y) = c(X, Y) + minw {D (Z, w)} = 2+1 = 3

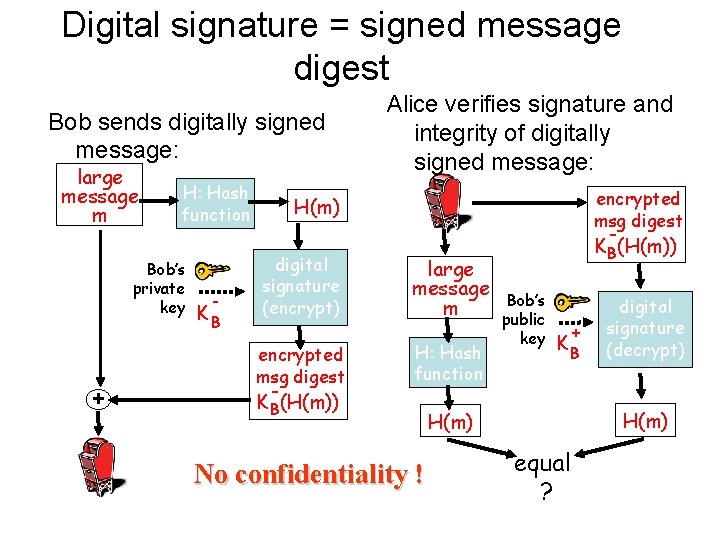
Digital signature = signed message digest Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB Alice verifies signature and integrity of digitally signed message: encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function No confidentiality ! KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ?

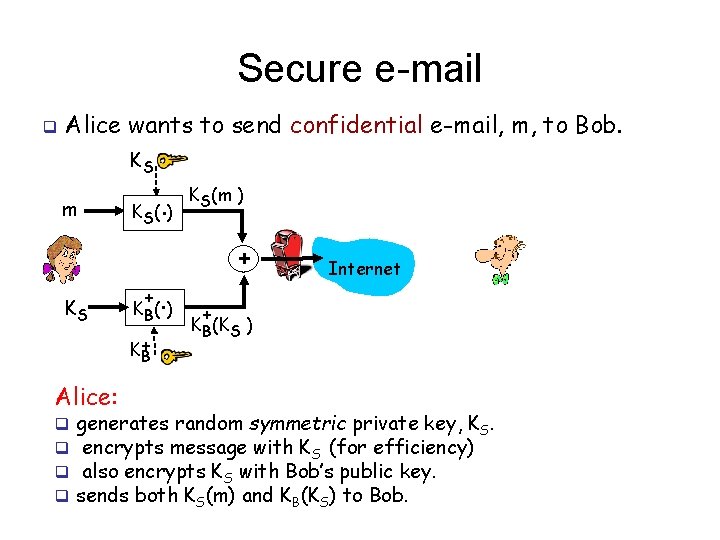
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Alice: q q . K B( ) KS(m ) + Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob.

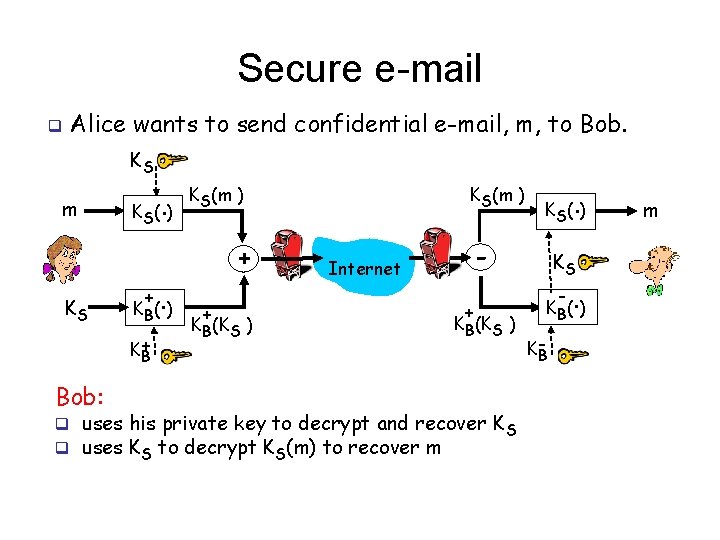
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Bob: . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m KS - . K B( ) KB m

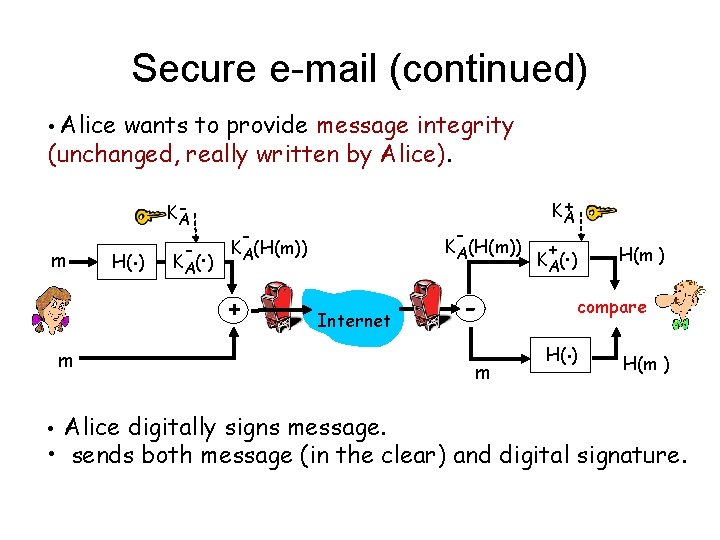
Secure e-mail (continued) • Alice wants to provide message integrity (unchanged, really written by Alice). m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m • Alice digitally signs message. m + . K A( ) H(m ) compare . H( ) H(m ) • sends both message (in the clear) and digital signature.


• Caesar cipher decrypt: – “welcome”, key= +2 • Vigenere cipher – “final exam” key=3, 4, -1 (blank space does not change)