Exceeding Your Expectations While Enhancing Your Security Posture






- Slides: 24

Exceeding Your Expectations, While Enhancing Your Security Posture Io. T Brief Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Internet of Things (Io. T): Issues and Challenges Pete Alatzas Slate Enclave, LLC Mike Bowen Praxis Engineering Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Table of Contents Who We Are Issues and Challenges Results of Weak Security What Can You Do? ? Contact Information Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Who We Are Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Pete Alatzas • Partner – Slate Enclave, LLC • Maryland Certified Cyber Company • Experience with Commercial, Private, Do. D and Intel communities • 25 years of experience within the Engineering/Security market • Certifications • C|CISO – Certified Chief Information Officer • CISSP- ISSEP – Certified Information Systems Security Professional w/ concentration on Engineering • GPEN – GIAC Penetration Tester • CEHv 7 – Certified Ethical Hacker Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Mike Bowen • Army Intel Programs Lead – Praxis Engineering, a GDIT Company • Software & Systems Engineering services focused on intelligence enterprise • Develop and integrate sensors, frameworks, toolsets, and analytics into mission environments • 20 years of experience across Telecom Industry and Intel/Do. D Programs • Network protocols, forward and reverse engineering, complex system integration • Degrees & Associations • MS, Electrical and Computer Engineering (Johns Hopkins), 2008 • BS, Computer Engineering (Clemson University), 2003 • Vice President of AOC Susquehanna Chapter (focused on Electronic Warfare & Cyber) • Past President of AFCEA Aberdeen Chapter (focused on Communications & Electronics) • Co-executes annual steganography contest at Shmoocon Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Issues and Challenges Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Internet of Things: • Io. T describes the network of devices that are connected via the Internet • EX: smart home devices such as smart meters and smart locks, and municipal/commercial devices like water station valves • These connected smart devices share data among each other, providing benefits such as better quality of life and greater insight into business. • Variety of vendors are focused on maximizing profit margins and minimizing time-to-market – security is not always a top priority • Diversity of vendors also presents a varied security posture when multiple brands are integrated together Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Issues… • Lack of Encryption • Most Io. T devices lack the processing and framework to implement proper security • The cost to produce Io. T devices and bring them to market is cheaper • Outdated/Legacy Security • The push to market results with weak security features • A breach in an Io. T device to relay into a breach into other devices within environment • Weak Passwords • Most default passwords are set to a weak default • Leaves devices vulnerable to brute force attacks • Demand for Consumer Products • The home users are the largest consumers • Average user is unaware of the risk or necessity of security Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

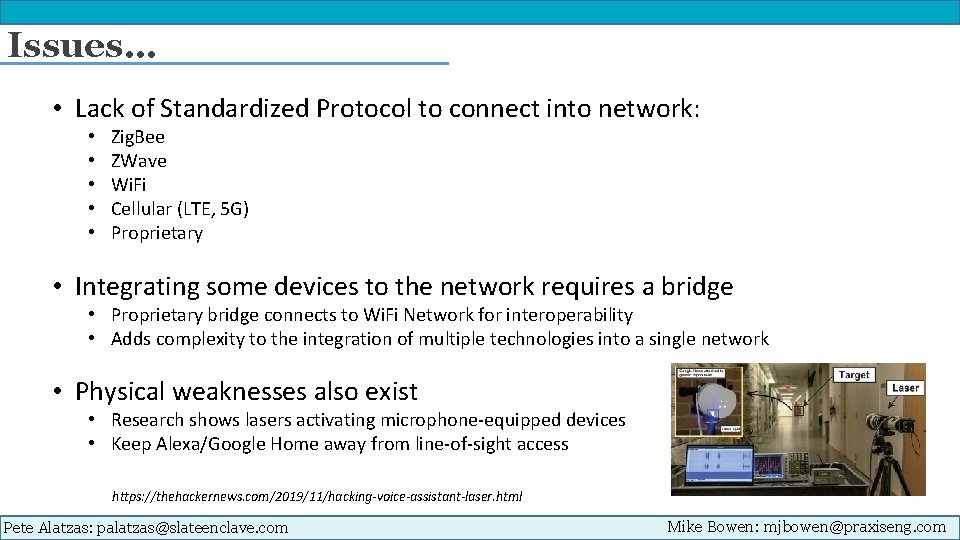
Issues… • Lack of Standardized Protocol to connect into network: • • • Zig. Bee ZWave Wi. Fi Cellular (LTE, 5 G) Proprietary • Integrating some devices to the network requires a bridge • Proprietary bridge connects to Wi. Fi Network for interoperability • Adds complexity to the integration of multiple technologies into a single network • Physical weaknesses also exist • Research shows lasers activating microphone-equipped devices • Keep Alexa/Google Home away from line-of-sight access https: //thehackernews. com/2019/11/hacking-voice-assistant-laser. html Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

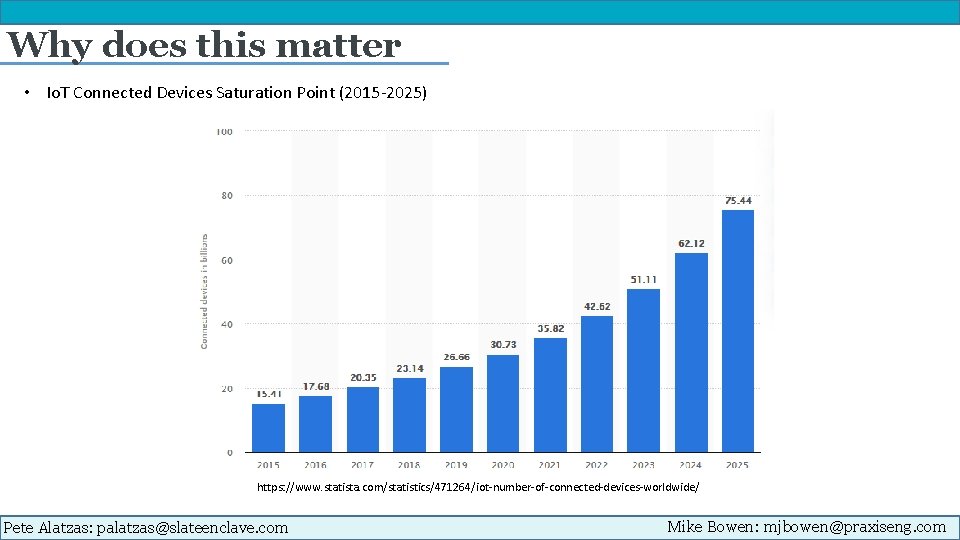
Why does this matter • Io. T Connected Devices Saturation Point (2015 -2025) https: //www. statista. com/statistics/471264/iot-number-of-connected-devices-worldwide/ Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Results of Weak Security Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Results… • Increased Network Traffic • Io. T devices tend to be noisy • They like to phone home • Increase of Bot. Nets… • Weak security has turned into increased botnets • Ex. Three college students created “Mirai” in 2016, targeted Io. T default passwords and took down major platforms like Netflix, Amazon and Twitter. • You Are the Product • • • You ever wonder why those devices are cheap? While most homes/small businesses lack internal network security they are sweeping the infrastructure They gather usage statistics and send them to manufacturer They sell collected data Who OWNS the data they collect from your devices • This is always overlooked in the name of convenience Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Results… • Use Man-In-The-Middle proxies to collect data • Sent without any real user notification • Ring disclosed they were sharing their data with: • Facebook (even if you don’t have an acct) • Apps. Flyer – mobile marketing company • Mix. Panel – user behavioral analytics • Local law enforcement – claims this is to thwart crime • Ring states that: • “…these third-party service providers evaluate the use of the apps to help improve the features and optimize the customer experience…” SOURCE: https: //threatpost. com/ring-sharing-user-data-facebook-data-miners/152300/ Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

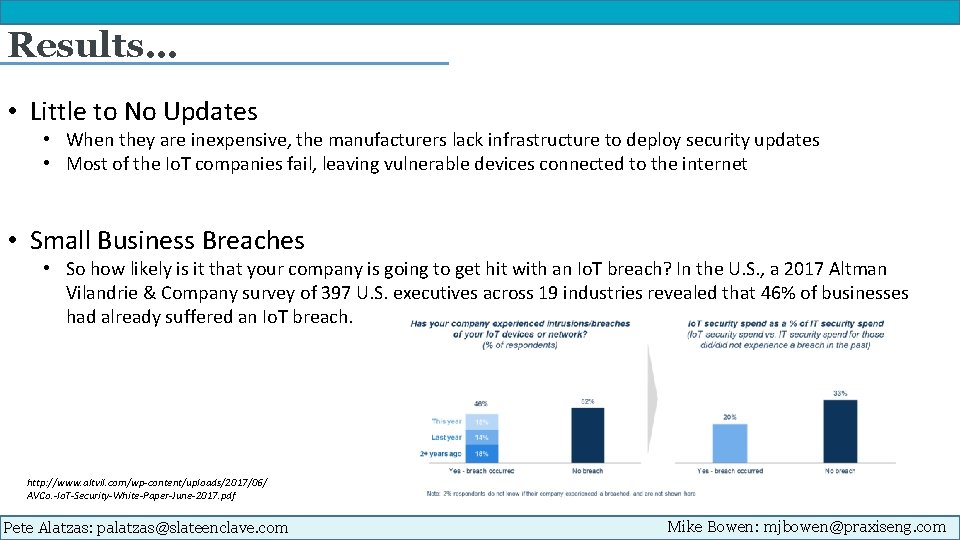
Results… • Little to No Updates • When they are inexpensive, the manufacturers lack infrastructure to deploy security updates • Most of the Io. T companies fail, leaving vulnerable devices connected to the internet • Small Business Breaches • So how likely is it that your company is going to get hit with an Io. T breach? In the U. S. , a 2017 Altman Vilandrie & Company survey of 397 U. S. executives across 19 industries revealed that 46% of businesses had already suffered an Io. T breach. http: //www. altvil. com/wp-content/uploads/2017/06/ AVCo. -Io. T-Security-White-Paper-June-2017. pdf Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

What Can You Do? ? Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

What Can You Do… • Slow down – do some research • • • Does the manufacturer have a track record of performing updates Have they been in business for an extended period of time Do they allow for password changes and encrypted management ports Do they require the ability to phone home – why? Ensure you are buying from a reputable seller (avoid “aftermarket” firmware) • Segment your network • Put your Io. T devices in their own network segment • If segmented and blocked, this stops the ability to talk to other sensitive devices in your network • Home networks – create a guest network • Patches/Updates • Make sure you are paying attention to the other devices in your network • Update/patch – the easiest thing and most affective Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

What Can You Do… • Monitor the environment • Have conditional alerts sent to you • Use Anti-Malware software to block scripts and alert • Advanced: add a malware/adware filter for your whole network (e. g. Pi. Hole) • Carefully configure your devices • Plug ‘n’ Play = Plug ‘n’ Pray (even for security) • Default settings are meant to make setup easy, not secure • Turn off services you do not need • Block external connections • Some Io. T Devices use cloud services (Advantages and Disadvantages) • Allows for no open ports for home/business environment. (plus) • Disable UPn. P on your home router • Where is the cloud presence? How is the data protected? Who owns it? (minus) • Advanced: create a VPN to your web management interfaces for the Io. T devices Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

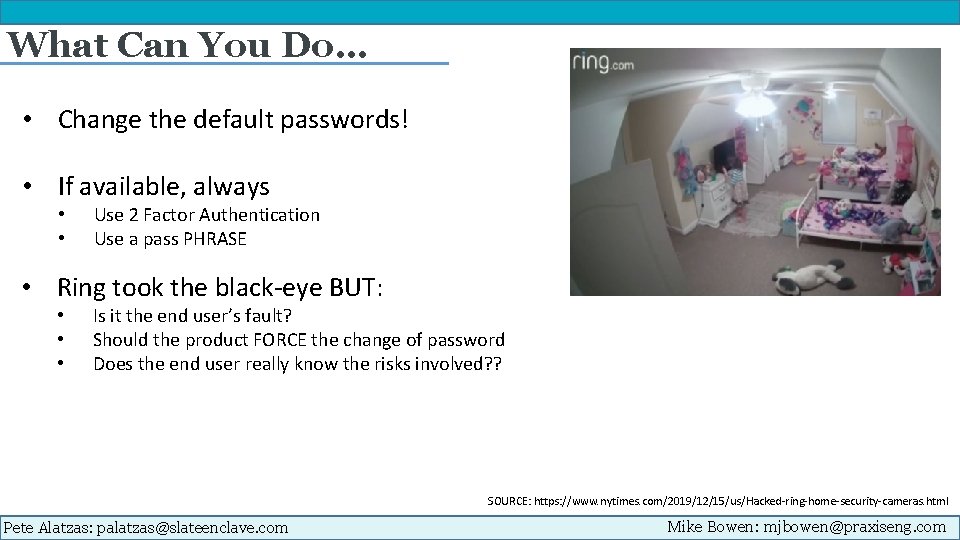
What Can You Do… • Change the default passwords! • If available, always • • Use 2 Factor Authentication Use a pass PHRASE • Ring took the black-eye BUT: • • • Is it the end user’s fault? Should the product FORCE the change of password Does the end user really know the risks involved? ? SOURCE: https: //www. nytimes. com/2019/12/15/us/Hacked-ring-home-security-cameras. html Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

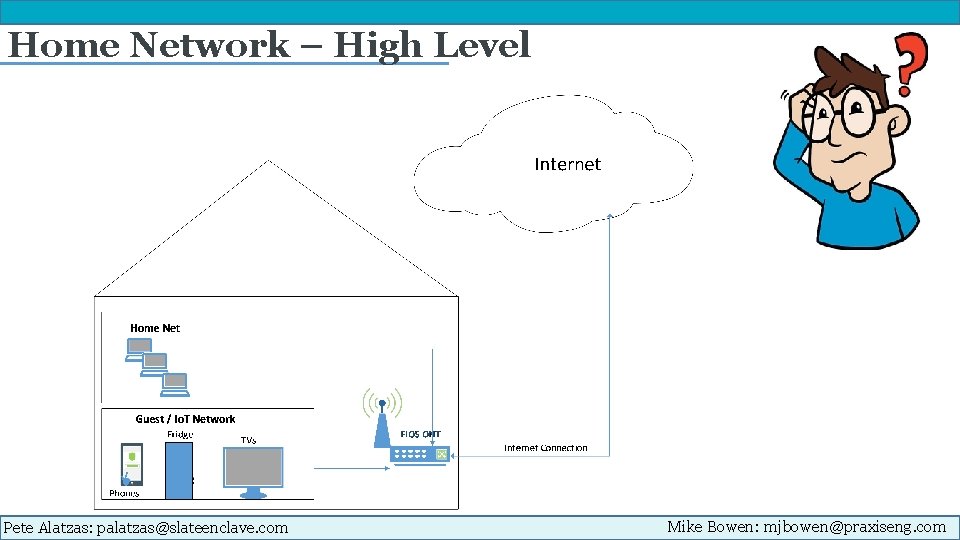
Home Network – High Level Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Business Standpoint - Wild West Network • We recommend against it as part of the Enterprise • Wild West Network Access • Guest Access to internet – still site controlled to prevent illegal activity • Personal devices, non-controlled devices • Not responsible for any adverse affects to personal devices • If it is TRULY needed • Perform a cost benefit / risk analysis to determine true need • Sandbox the network • Create access lists to prevent access to enterprise network Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

What We Use • Ubiquiti and Synology Networking Equipment • Cost effective compared to full commercial solutions • Offer variety of network segmentation, VPN, and advanced security • Home-hosted Blue. Iris camera system • Cameras are blocked from Internet access at the router • Video streams terminate into Blue. Iris computer, then available via HTTPS • Security System • Ring with two-factor activated • Doorbells face outside the house only • No “smart” control for entryways • Commercial spying devices • We do have an assortment of Alexa and Google Home devices for entertainment and limited convenience Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Questions? Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com

Contact Information Pete Alatzas Mike Bowen palatzas@slateenclave. com mjbowen@praxiseng. com 410 -989 -1102 443 -655 -1295 http: //www. slateenclave. com http: //www. praxiseng. com 201 International Circle 4695 Millennium Drive Suite 230 Belcamp, Maryland 21017 Hunt Valley, MD 21030 Pete Alatzas: palatzas@slateenclave. com Mike Bowen: mjbowen@praxiseng. com