e Trust Pest Patrol AntiSpyware Comprehensive AntiSpyware Solution












- Slides: 21

e. Trust™ Pest. Patrol® Anti-Spyware Comprehensive Anti-Spyware Solution Brian Grayek CISSP, ITIL, CHS-III Principal Consultant January 20, 2005 1 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Agenda § Threat Management – e. Trust Pest. Patrol solution fit – Anti-Spyware market perspective § What is spyware? § How does it spread? § e. Trust Pest. Patrol Anti-Spyware – Key features § Q&A – Open Forum 2 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

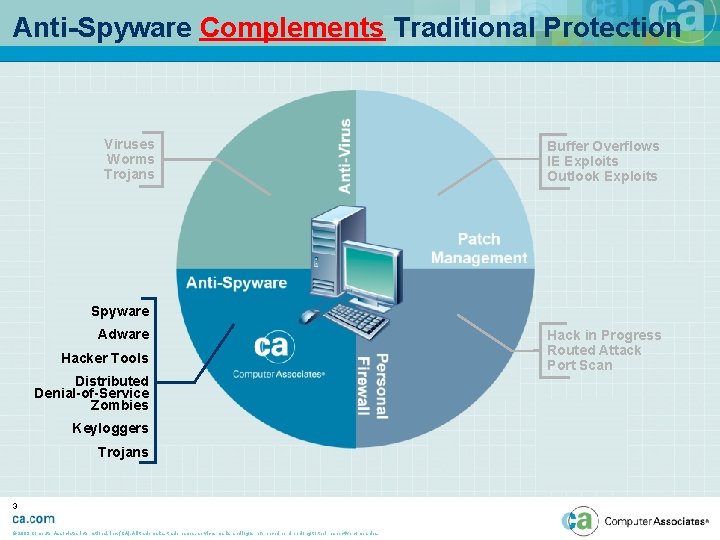
Anti-Spyware Complements Traditional Protection Viruses Worms Trojans Buffer Overflows IE Exploits Outlook Exploits Spyware Adware Hacker Tools Distributed Denial-of-Service Zombies Keyloggers Trojans 3 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. Hack in Progress Routed Attack Port Scan

Gartner Confirms the Spyware Threat § “At mid-2004, Gartner customers are seeing a surge in manifestations of ‘spyware, ’ invasive methods to steal user privacy that disrupt users and their workstations at home and at work. Customers report that the cleanup effort may take a few hours, but that in no time at all, the same systems are infected again. ” Source: Gartner, “A Field Guide to Spyware Variations, ” John Girard, July 2004 4 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

e. Trust Integrated Threat Management § Multi-layered approach to threat management – Anti-spyware management – Antivirus management – Secure content management – Intrusion detection – Vulnerability management 5 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

What is Spyware? § Spyware is a non-viral application (surveillance tool) that is loaded without the user’s knowledge and can monitor computer activity (Trojans), such as: – – Keystroke tracking and capture Email logging Instant messaging usage and snapshots Modifying application/OS behavior (e. g. Cool. Web. Search) § Spyware and adware can increase business risks: – – Theft of confidential data Unauthorized enterprise access Reduced PC performance Increased bandwidth waste 6 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

How do Computers Get Infested? § § § § Web browsing Unauthorized downloads File swapping Email attachments Instant messaging Installing “legitimate software” Intentional installation by employee 7 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

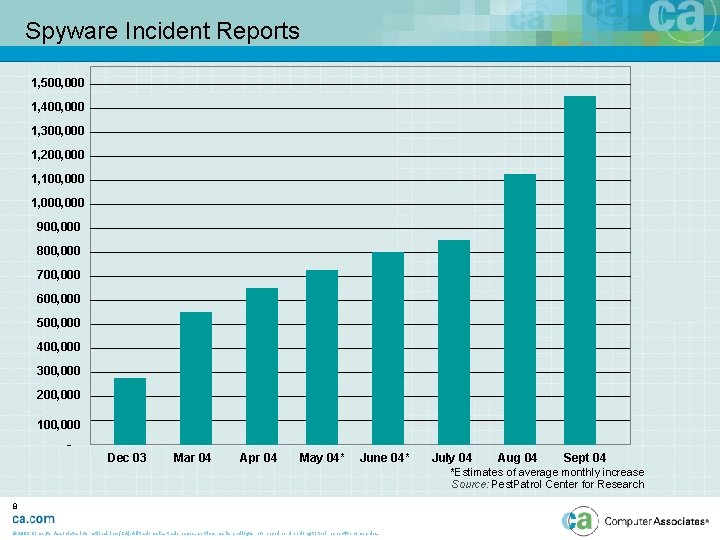
Spyware Incident Reports 1, 500, 000 1, 400, 000 1, 300, 000 1, 200, 000 1, 100, 000 1, 000 900, 000 800, 000 700, 000 600, 000 500, 000 400, 000 300, 000 200, 000 100, 000 - Dec 03 Mar 04 Apr 04 May 04* June 04* July 04 Aug 04 Sept 04 *Estimates of average monthly increase Source: Pest. Patrol Center for Research 8 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Spyware Costs Your Customers Time & Money § Microsoft estimates that spyware is responsible for 50% of all PC crashes § Dell reports 20% of its technical support calls involve spyware Source: Information. Week, “Tiny, Evil Things, ” George Hulme and Thomas Claburn, April 26, 2004 9 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

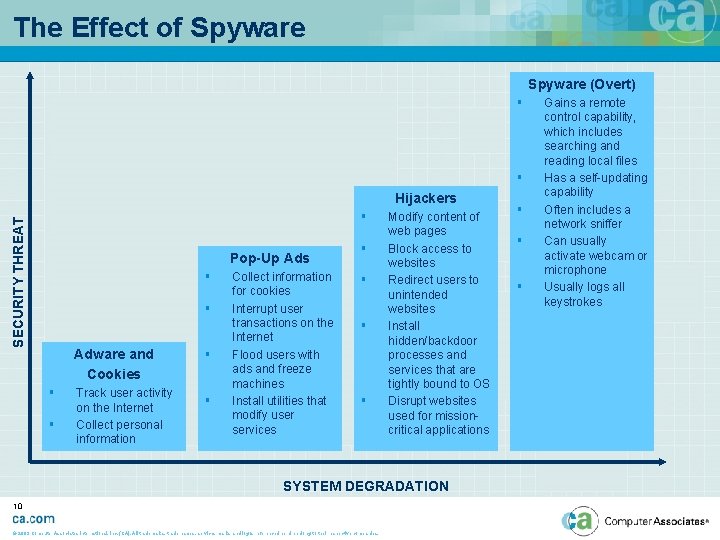
The Effect of Spyware (Overt) § § Hijackers SECURITY THREAT § Pop-Up Ads § § Adware and Cookies § § Track user activity on the Internet Collect personal information § § Collect information for cookies Interrupt user transactions on the Internet Flood users with ads and freeze machines Install utilities that modify user services § § Modify content of web pages Block access to websites Redirect users to unintended websites Install hidden/backdoor processes and services that are tightly bound to OS Disrupt websites used for missioncritical applications SYSTEM DEGRADATION 10 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies. § § § Gains a remote control capability, which includes searching and reading local files Has a self-updating capability Often includes a network sniffer Can usually activate webcam or microphone Usually logs all keystrokes

Anti-Spyware Business Drivers § Mitigate risk and limit legal liability – Protect from unauthorized access and information theft – Reduce threat to employees, partners, customers, intellectual property, regulatory compliance and brand § Help ensure business continuity – Maintain employee productivity – Avoid business disruptions and system downtime § Reduce costs – Reduce bandwidth waste – Minimize help desk calls due to spyware infestation – Productivity lost due to system down-time § Both IT staff and employee 11 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Pest. Patrol leads the Market § e. Trust Pest. Patrol in Retail § e. Trust Pest. Patrol for Corporations 12 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Agenda § Threat Management – e. Trust Pest. Patrol product fit – Anti-Spyware market perspective § What is spyware? § How does it spread? § e. Trust Pest. Patrol Anti-Spyware – Key features § Q&A – Open Forum 13 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

e. Trust Pest. Patrol — Features § § Detects a comprehensive range of spyware Protects you from spyware in real-time Updates pest definitions automatically Leverages one of the industry’s largest pest information databases § Provides an easy-to-use interface § Protects your personal and professional data § Improves PC performance 14 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

e. Trust Pest. Patrol Corporate Edition — Features Includes e. Trust Pest. Patrol features, plus: § Central management and control § § Enforces scanning and update policies Launches scans on-demand, at scheduled times or at login Reviews logs Deploys new users § Customized alerts and logs § Creates “safe lists” or exclusion files § Consolidates reports § Customizes reports based on workstation, date/time, security risk priority or pest category § Powerful Microsoft. NET infrastructure § Flexible deployment 15 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Centralized Anti-Spyware Management 16 § § Manage anti-spyware from one administrative console Launch manual or scheduled scans Automatically update pest definitions Define exclude parameters (safe lists) to reduce false alarms © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Server Setup Activities § § § Choose update preferences Set up and deploy command line configuration Set up email notification Customize the file extensions scanned for Establish exclusion files 17 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Customized Logs and Reports § Central Log of All Pest Activity on the Network § Generate Customized reports by: – Workstation, Date/time, Security risk priority, Pest category, Specific pests § Command line capabilities make it easy to create reports for remote users 18 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

e. Trust Pest. Patrol Value Proposition § Detects and removes non-viral malicious code to reduce risks and prevent unauthorized access and information theft § Helps ensure business continuity through realtime management of spyware § Reduces bandwidth waste and improves PC performance through proactive detection and removal of spyware § Streamlines security management through a centralized management console and automated pest updates 19 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Market Leadership § e. Trust Pest. Patrol was the first commercial antispyware product on the market § e. Trust Pest. Patrol was the first to offer a fully networked product § e. Trust Pest. Patrol is backed by one of the industry’s largest pest research teams § e. Trust Pest. Patrol provides one of the industry’s most comprehensive pest databases § 95% of the Fortune 500® use CA software 20 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.

Agenda § Threat Management – e. Trust Pest. Patrol product fit – Anti-Spyware market perspective § What is spyware? § How does it spread? § e. Trust Pest. Patrol Anti-Spyware – Key features § Q&A – Open Forum 21 © 2003 Computer Associates International, Inc. (CA). All trademarks, trade names, services marks and logos referenced herein belong to their respective companies.