Data Protection and Privacy SHELON PADMORE FOUNDER CEO

















- Slides: 40

Data Protection and Privacy SHELON PADMORE FOUNDER / CEO Distributed Systems Ltd. Dummy Text

TRUST IS THE FOUNDATION The financial services sector is built on trust “Don’t do anything that you don’t want your mother to find out about on the front page of the newspaper” - Bill Steinberg Morgan Stanley Executive Director Dummy Text

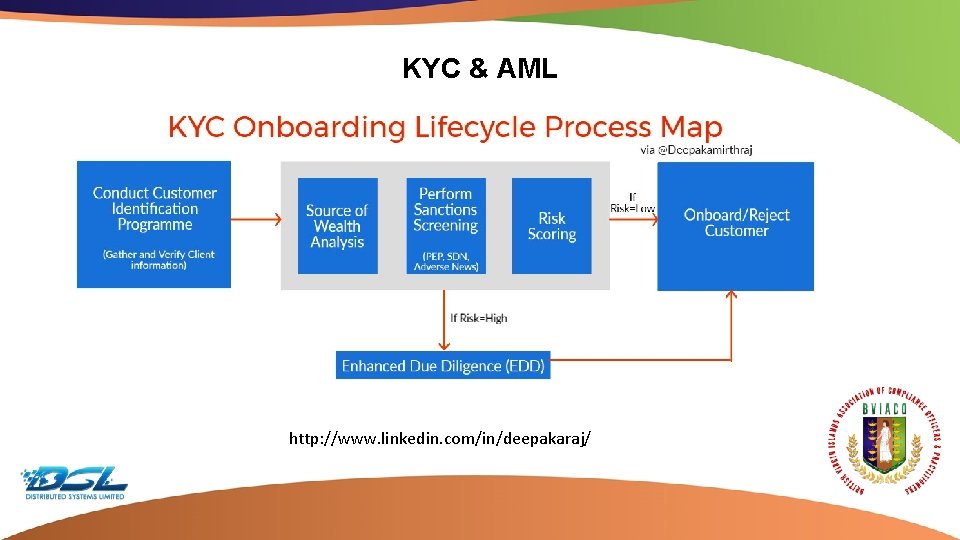
KYC & AML http: //www. linkedin. com/in/deepakaraj/ Dummy Text

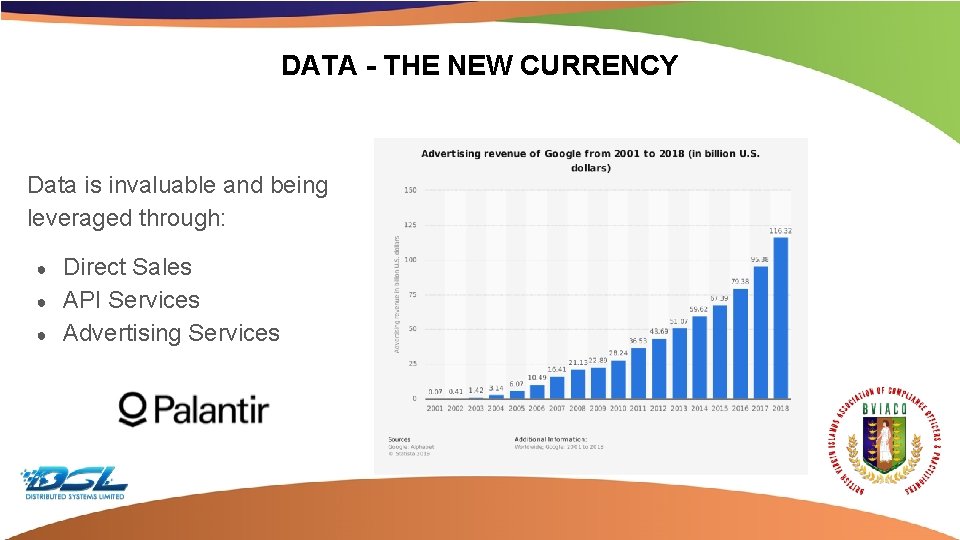
DATA - THE NEW CURRENCY Data is invaluable and being leveraged through: ● ● ● Direct Sales API Services Advertising Services Dummy Text

DATA BREACH - ASSOCIATED RISKS Financial & Regulatory Operational Reputational Dummy Text

BREACHES & EXPOSURE IN THE HEADLINES Mossack Fonseca - 11 Million Documents Facebook CA - 50 Million User accounts Equifax - 146 Million Consumers Affected and. 5 Bn in fines My. Fitness. Pal - 150 Million Records Exposed Aadhar - 1. 1 Billion Records Exposed Dummy Text

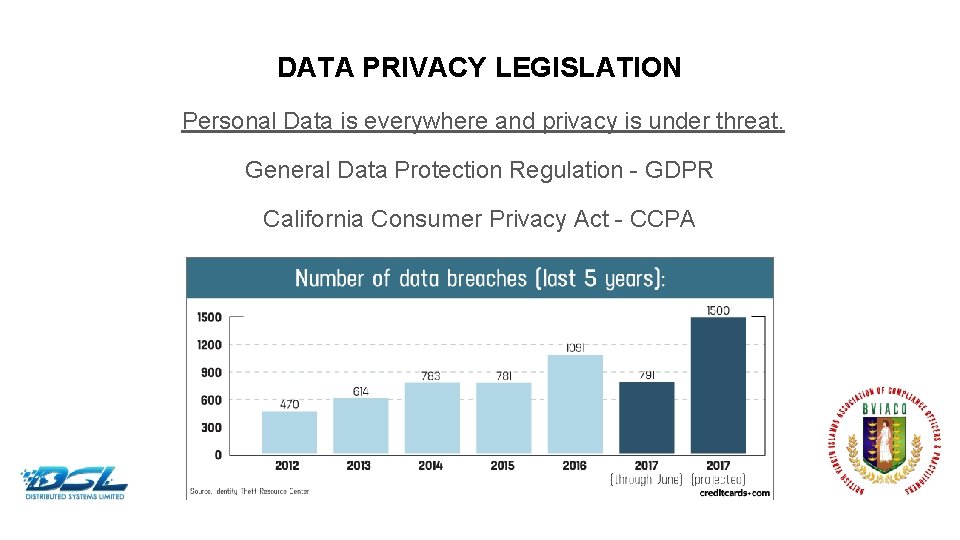
DATA PRIVACY LEGISLATION Personal Data is everywhere and privacy is under threat. General Data Protection Regulation - GDPR California Consumer Privacy Act - CCPA Dummy Text

WHAT IS GDPR AND WHO DOES IT AFFECT? EU Data Protection Legislation EU Resident Customers globally Dummy Text

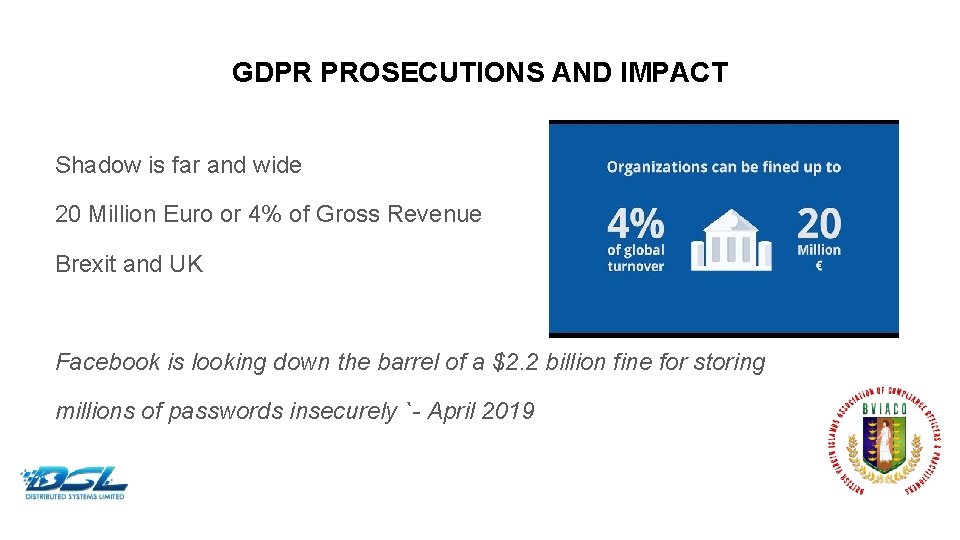
GDPR PROSECUTIONS AND IMPACT Shadow is far and wide 20 Million Euro or 4% of Gross Revenue Brexit and UK Facebook is looking down the barrel of a $2. 2 billion fine for storing millions of passwords insecurely `- April 2019 Dummy Text

GDPR COMPLIANCE REQUIREMENTS 1. Obtain Consent 2. Timely Breach Notification 3. Right to Access Data 4. Right to be Forgotten 5. Data Portability 6. Privacy by Design 7. Appointment of Data Protection Officer Dummy Text

KEY VULNERABILITIES ● ● ● Malware Unpatched Vulnerabilities Phishing (Social Engineering) Io. T Devices & Pivoting DDo. S Non-Secure Third party services ● ● ● ● Ransomware Identity Theft SQL Injection Iframe Injection BYOD Exposure Man in the Middle Shadow IT Dummy Text

MALWARE What is Malware? Software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system. Types of Malware ● ● ● Ransomware Trojans Worms Dummy Text

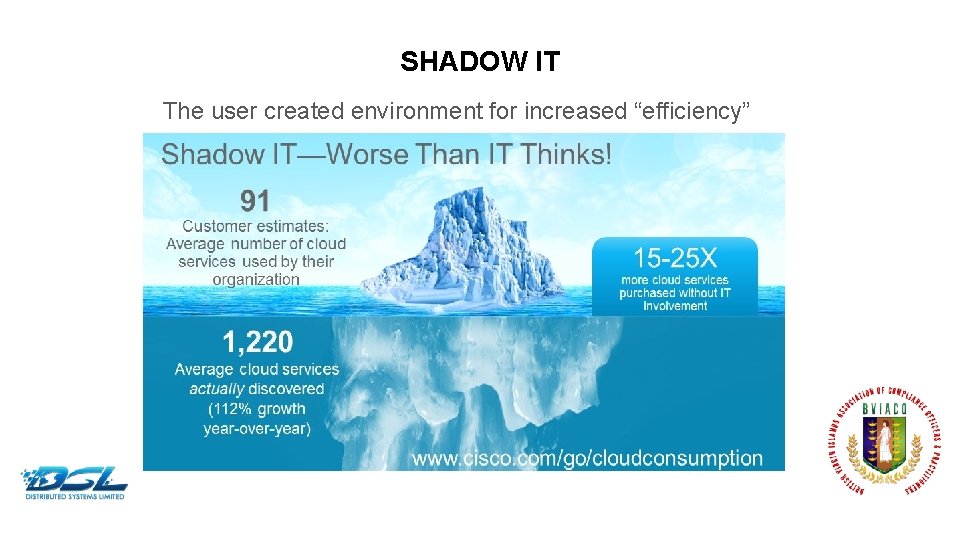
SHADOW IT The user created environment for increased “efficiency” Dummy Text

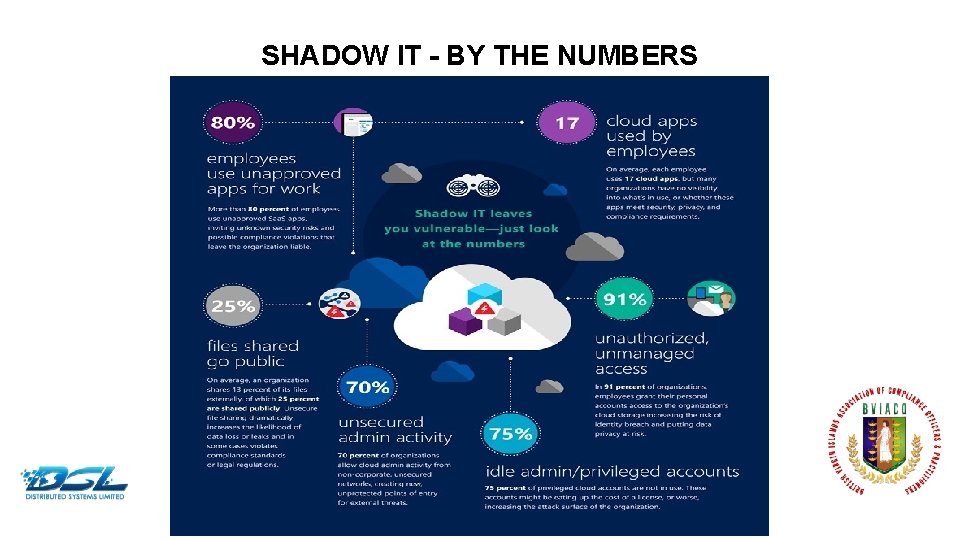
SHADOW IT - BY THE NUMBERS Dummy Text

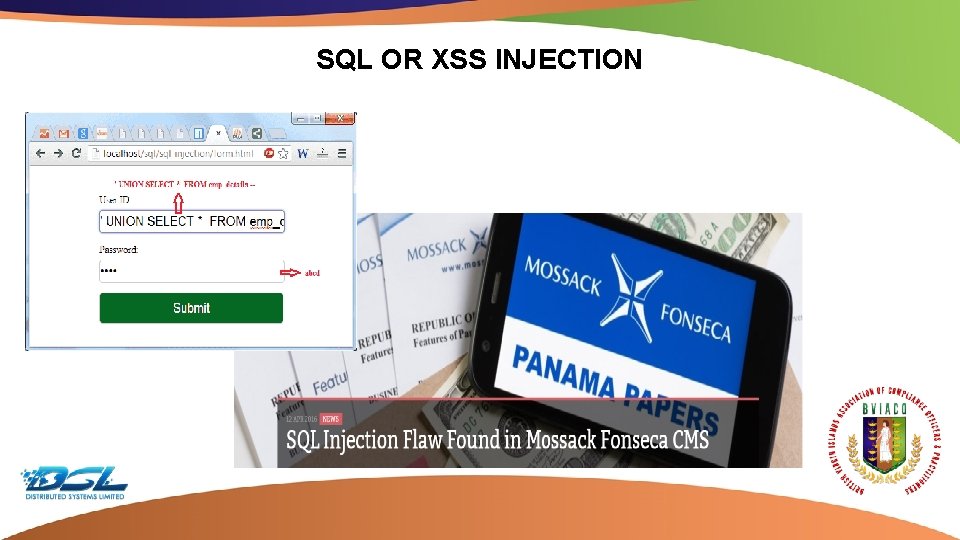
SQL OR XSS INJECTION Dummy Text

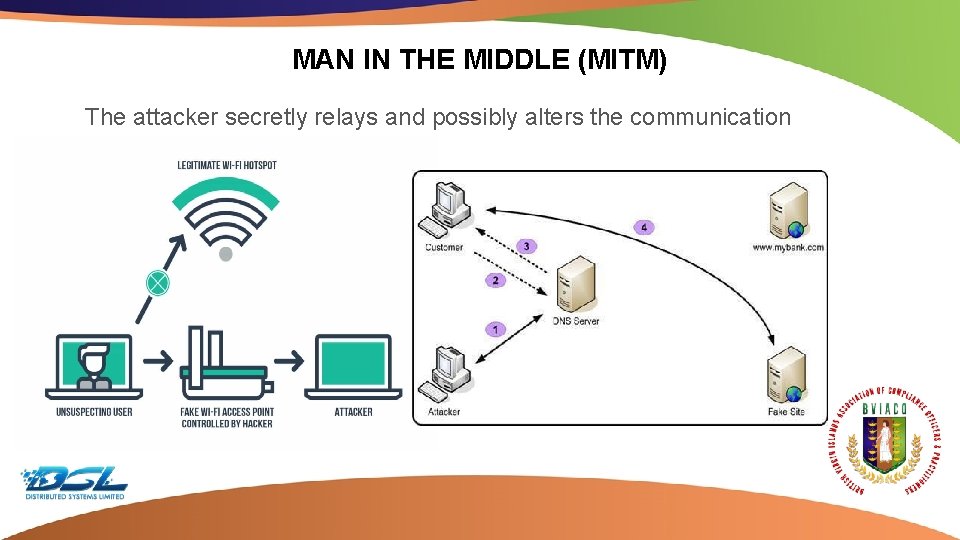
MAN IN THE MIDDLE (MITM) The attacker secretly relays and possibly alters the communication Dummy Text

PHISHING AND SOCIAL ENGINEERING A fraudulent attempt to gain sensitive information Still on the increase Often a precursor to Identity Theft, Account Takeover & Fraud This methodology is often based in the following sequence Establish Trust / Credibility Evoke Fear Call to Action Collect Sensitive Information Dummy Text

PHISHING AND OFF THE SHELF EXPLOITS ● Exploits ● Zero-Day Exploits ● Dark Web The. Real. Deal Market ● Hacking Services Dummy Text

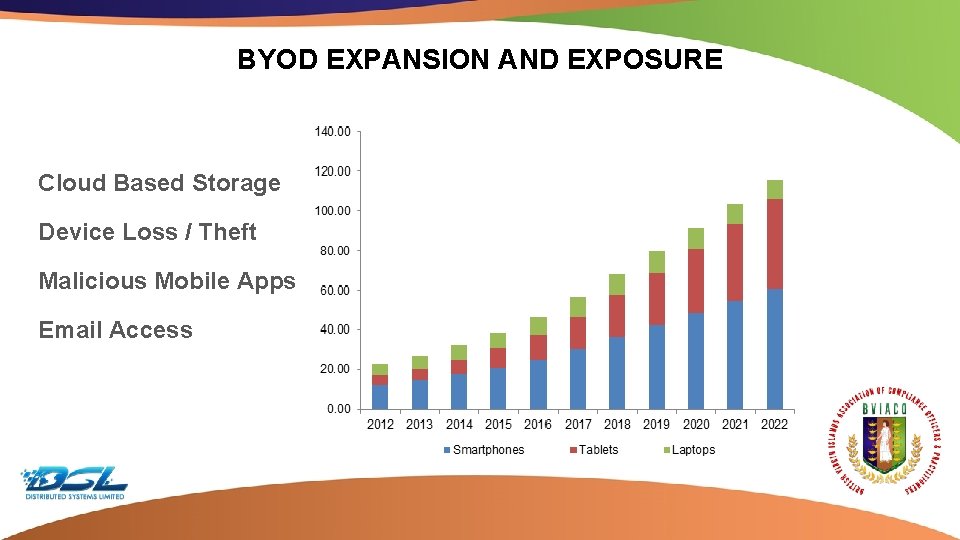
BYOD EXPANSION AND EXPOSURE Cloud Based Storage Device Loss / Theft Malicious Mobile Apps Email Access Dummy Text

UNPATCHED VULNERABILITIES • Security Updates or Patches should be obtained and applied in a timely manner; • A major undiscovered zero day is often worth tens of thousands of dollars -- sometimes more than $100, 000; • Over 70% of businesses will leave holes in their defenses for over a month; • Less than 1% of breaches are due to zero day exploits. Dummy Text

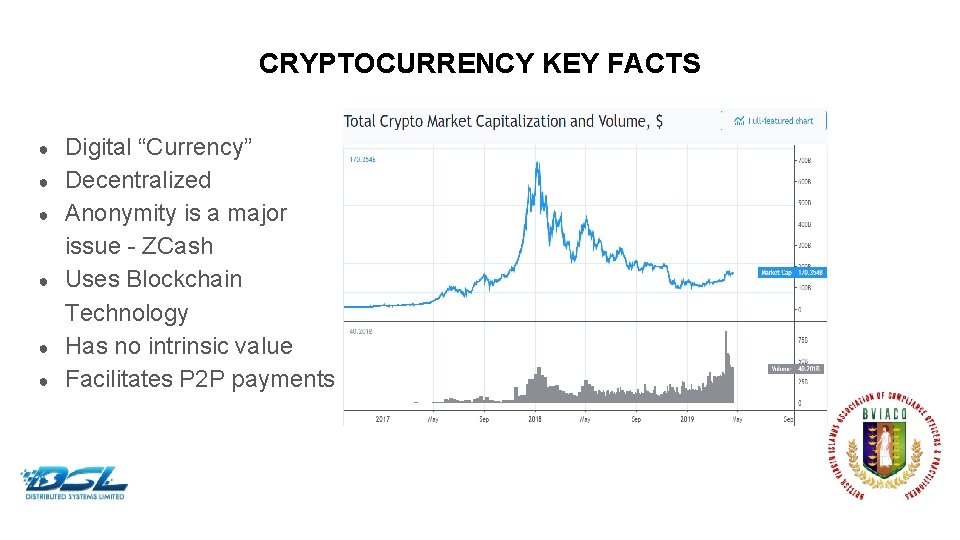
CRYPTOCURRENCY KEY FACTS ● ● ● Digital “Currency” Decentralized Anonymity is a major issue - ZCash Uses Blockchain Technology Has no intrinsic value Facilitates P 2 P payments Dummy Text

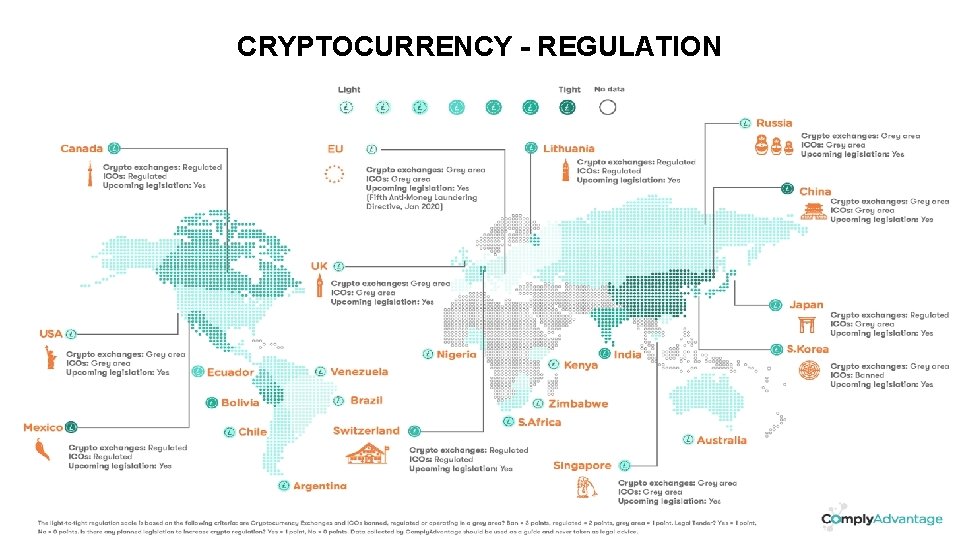
CRYPTOCURRENCY - REGULATION Dummy Text

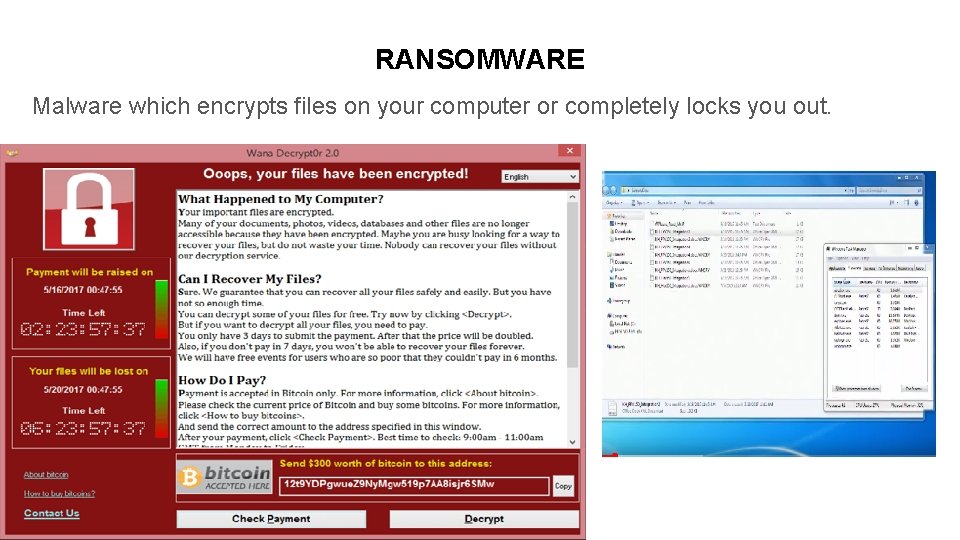
RANSOMWARE Malware which encrypts files on your computer or completely locks you out. Dummy Text


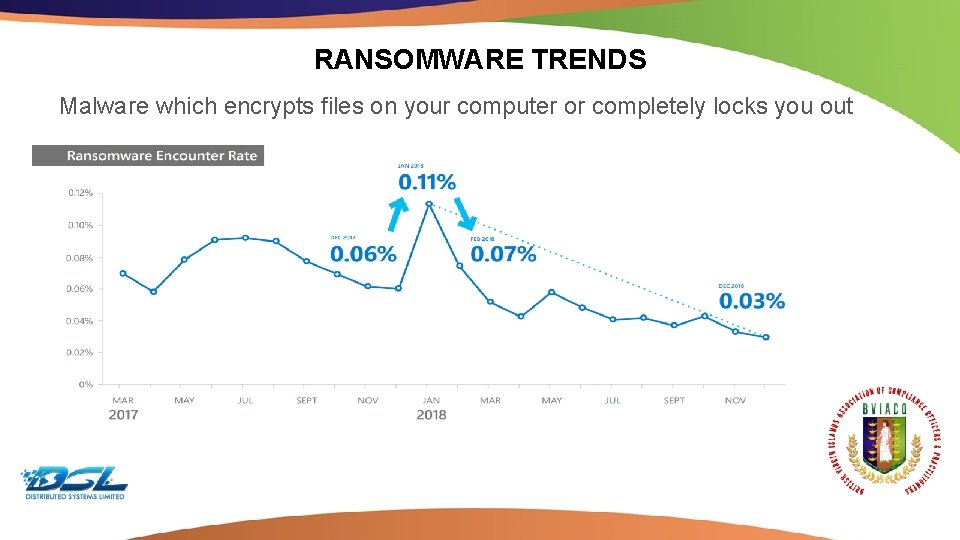
RANSOMWARE TRENDS Malware which encrypts files on your computer or completely locks you out Dummy Text

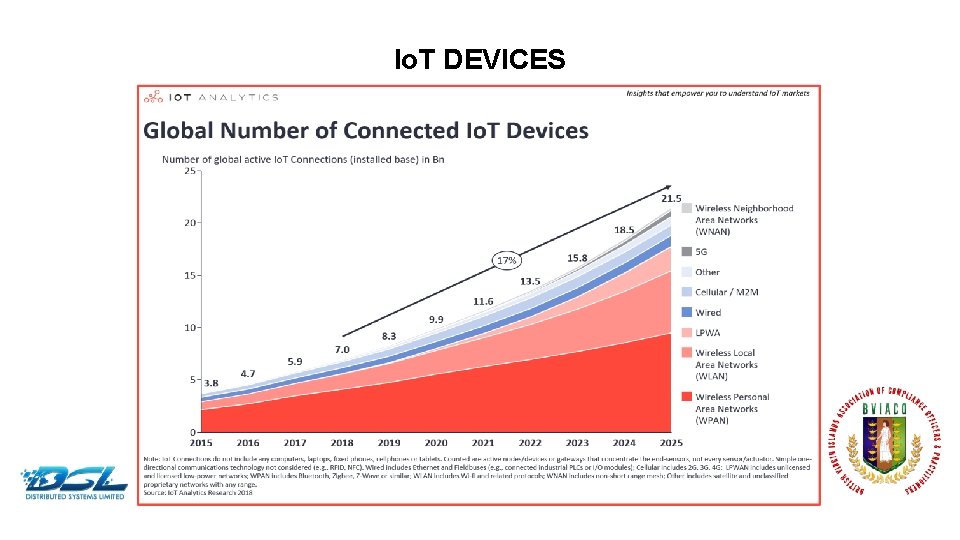
Io. T DEVICES Dummy Text

Io. T DEVICES AND PIVOTING Dummy Text

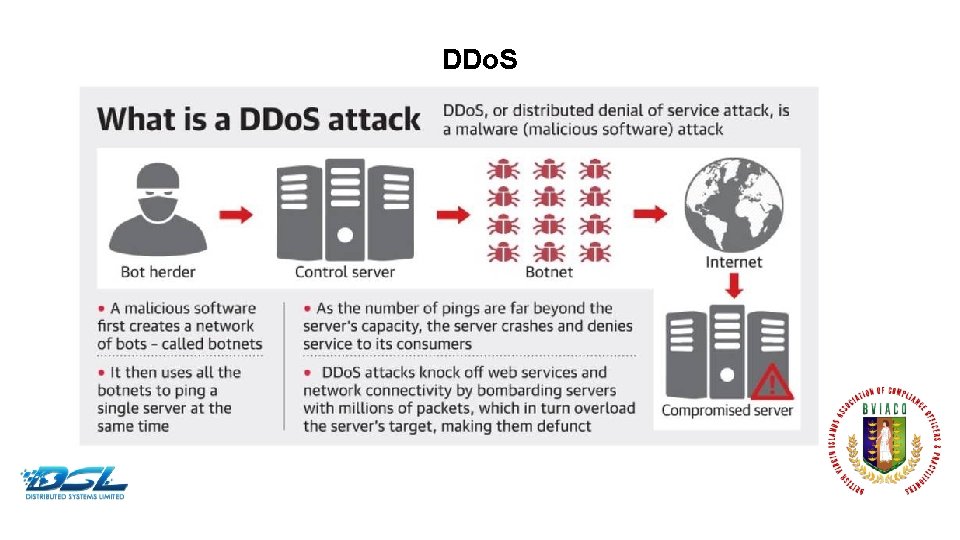
DDo. S Dummy Text

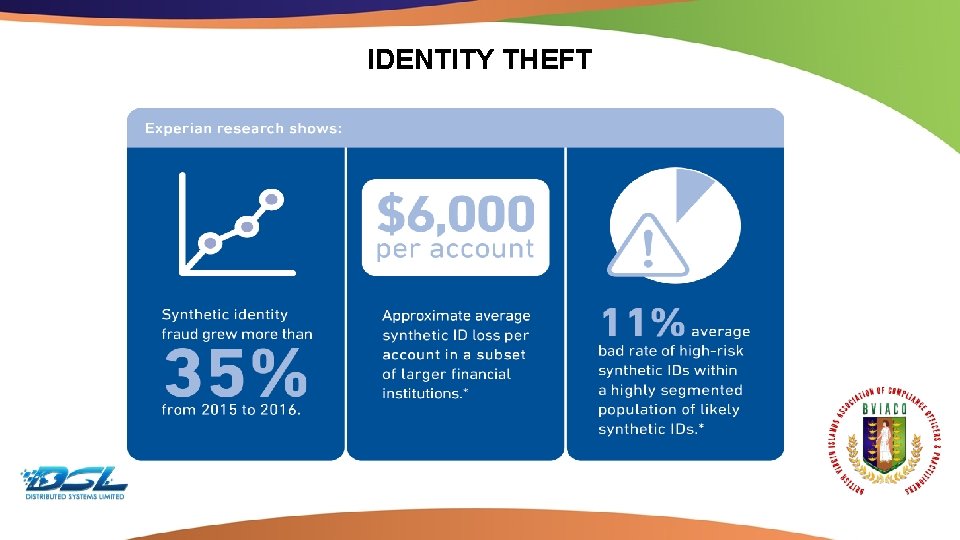
IDENTITY THEFT Dummy Text

NON-SECURE THIRD PARTY VENDORS Limit Your Exposure By Considering the following: ● Ensure your vendors conduct regular security assessments; ● Make sure vendors have written information security policies and procedures in place; ● Verify that your vendors encrypt data in transit, including data stored on laptops, external hard drives and application databases; ● Ensure vendors have a disaster recovery program in place. Dummy Text

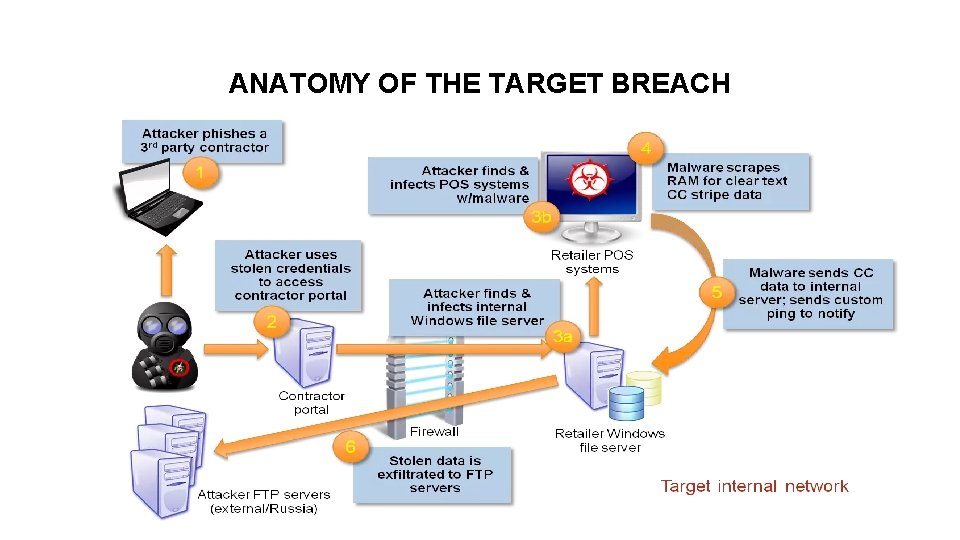
ANATOMY OF THE TARGET BREACH Dummy Text

RISK MITIGATION APPROACH 1. Conduct Cyber Risk Assessment 2. Evaluate your DRV? 3. Formulate/Strengthen data protection plan DPP 4. Formulate/Strengthen a data breach response plan Dummy Text

PROACTIVE STEPS AND BEST PRACTICES ● ● ● ● User Training Penetration Testing Legislative Guidance Stay in the know Proxy & Firewall Patches & Updates Address Shadow IT ● ● ● ● Cloud vs Local Data Encryption 2 Factor Authentication Backup Policy BYOD Policy Io. T Policy Zero Data & Obfuscation Dummy Text

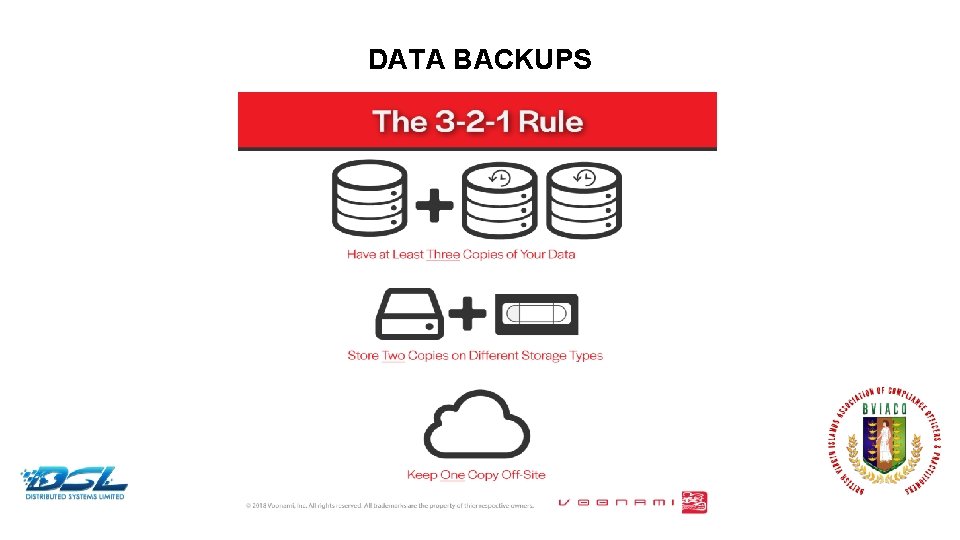
DATA BACKUPS Dummy Text

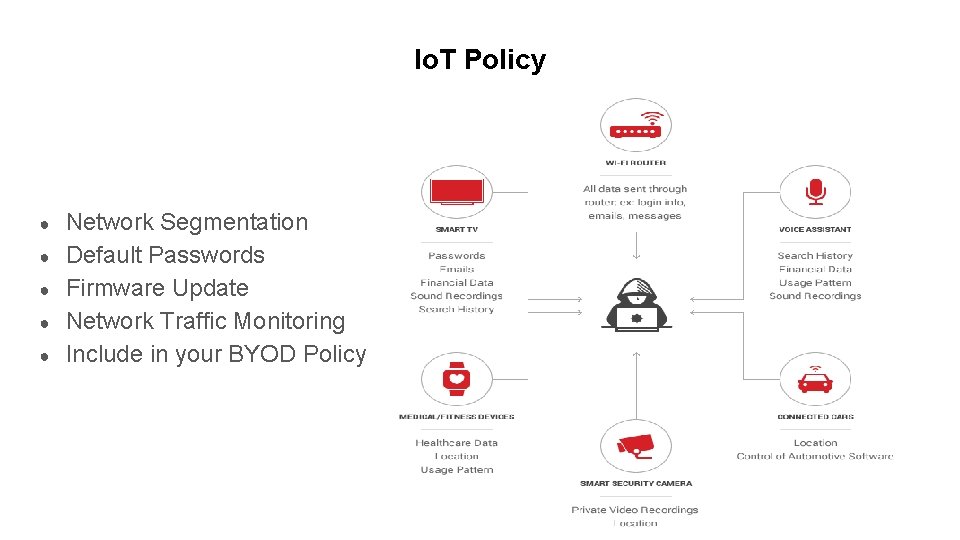
Io. T Policy ● ● ● Network Segmentation Default Passwords Firmware Update Network Traffic Monitoring Include in your BYOD Policy Dummy Text

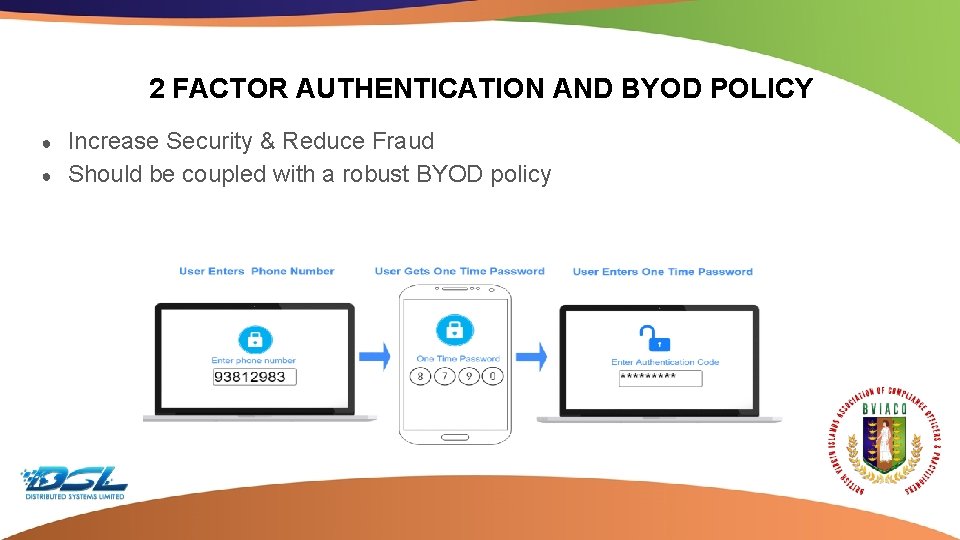
2 FACTOR AUTHENTICATION AND BYOD POLICY ● ● Increase Security & Reduce Fraud Should be coupled with a robust BYOD policy Dummy Text

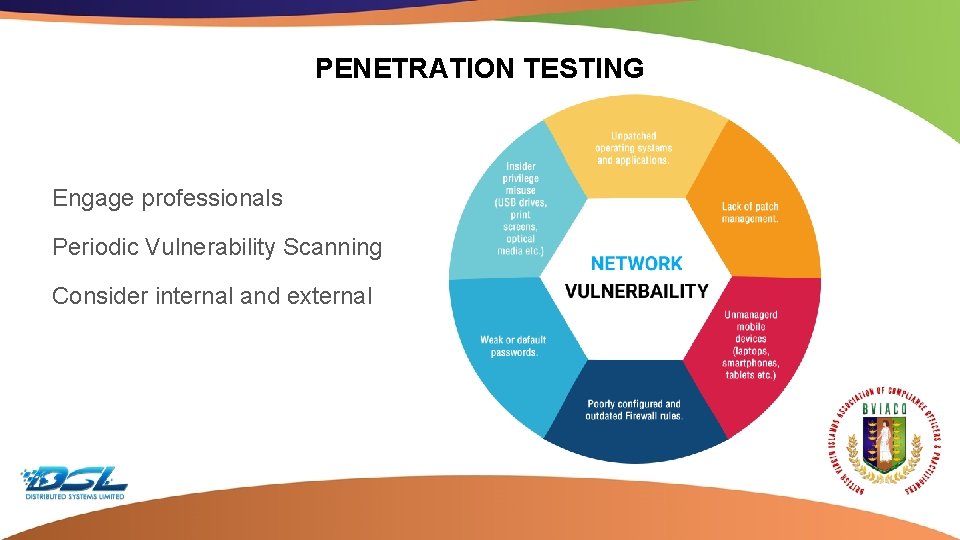
PENETRATION TESTING Engage professionals Periodic Vulnerability Scanning Consider internal and external Dummy Text

CLOUD VS LOCAL STORAGE POLICY Out of the Box Benefits ● ● ● ● Penetration Testing Logging and Monitoring Data Encryption DDo. S Mitigation Identity & Access Control Application Inspector Redundancy & Failover AI Security Mechanisms Dummy Text

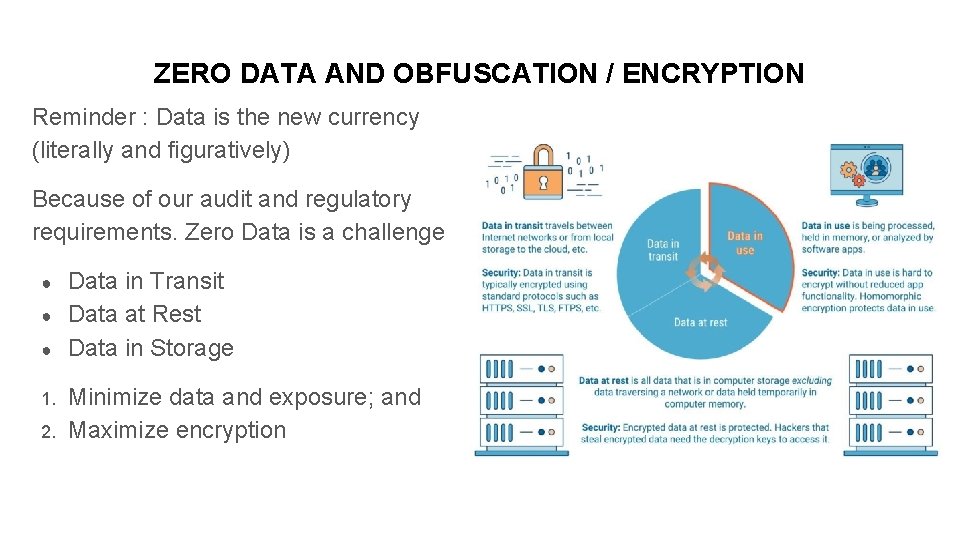
ZERO DATA AND OBFUSCATION / ENCRYPTION Reminder : Data is the new currency (literally and figuratively) Because of our audit and regulatory requirements. Zero Data is a challenge ● ● ● 1. 2. Data in Transit Data at Rest Data in Storage Minimize data and exposure; and Maximize encryption Dummy Text

THANK YOU! spadmore@finshield. net 1. 868. 346. 9090 Dummy Text
 Cvs privacy awareness and hipaa training answers
Cvs privacy awareness and hipaa training answers Malaysia data privacy law
Malaysia data privacy law Big data privacy issues in public social media
Big data privacy issues in public social media Data privacy
Data privacy Data privacy massachusetts
Data privacy massachusetts Data protection act in health and social care settings
Data protection act in health and social care settings Ceo and coo org chart
Ceo and coo org chart Owens and minor ceo fired
Owens and minor ceo fired Fairness and flawless ceo
Fairness and flawless ceo Dignity champion certificate
Dignity champion certificate Microsoft from back doors patch gov
Microsoft from back doors patch gov Ferpa
Ferpa Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Family educational rights and privacy act of 1974
Family educational rights and privacy act of 1974 Confidentiality and privacy controls
Confidentiality and privacy controls Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Three primary privacy issues are accuracy property and
Three primary privacy issues are accuracy property and Hipaa privacy and security awareness training
Hipaa privacy and security awareness training What is the destructive event or prank the virus delivers
What is the destructive event or prank the virus delivers Unhcr data protection policy
Unhcr data protection policy Data protection act 1998 bbc bitesize
Data protection act 1998 bbc bitesize Raid system of data protection
Raid system of data protection Data protection policy
Data protection policy Data protection strategy template
Data protection strategy template Teach ict data protection act
Teach ict data protection act Azure data protection
Azure data protection Data protection
Data protection State service of ukraine on personal data protection
State service of ukraine on personal data protection Data protection act 1998 ict
Data protection act 1998 ict European data protection office edpo
European data protection office edpo Convention 108 data protection
Convention 108 data protection Daoism founder
Daoism founder Who is the founder of disney world
Who is the founder of disney world The founder of utilitarianism
The founder of utilitarianism Tracy david swena
Tracy david swena Pengertian total quality management
Pengertian total quality management Praise analysis
Praise analysis Lesson 2 the new england colonies
Lesson 2 the new england colonies Founder of buddhism
Founder of buddhism Sikishm founder
Sikishm founder