The Data Protection Act ICT Law Did you


















- Slides: 21

The Data Protection Act & ICT Law


Did you see anything wrong with that? Most people wouldn’t want that sort of information posted in a public place. Why? Because it is private and personal – nothing to do with anyone else. In order to keep our details private, we need a Data Protection Act.

The purpose of the act The Data Protection Act 1998 sets out to protect the privacy of personal information. It only covers personal information about living individuals, not about businesses. It covers data stored on computer or in a paper-based filing system. It lets people check what data is being held about them. It is run by the Information Commissioner’s Office.

Subjects and users Data subjects are people who have data held about them – just about everybody really. Data users are the people or organizations who hold the data. There are far more data users than many people think. An organization holding data has to have a data controller – a person who makes sure the act is followed.

It’s the principle of the thing The act says that data must be: (The 8 Principles) • • • For the personal data that controllers store and process: It must be collected and used fairly and inside the law. It must only be held and used for the reasons given to the Information Commissioner. It can only be used for those registered purposes and only be disclosed to those people mentioned in the register entry. You cannot give it away or sell it unless you said you would to begin with. The information held must be adequate, relevant and not excessive when compared with the purpose stated in the register. So you must have enough detail but not too much for the job that you are doing with the data. It must be accurate and be kept up to date. There is a duty to keep it up to date, for example to change an address when people move. It must not be kept longer than is necessary for the registered purpose. It is alright to keep information for certain lengths of time but not indefinitely. This rule means that it would be wrong to keep information about past customers longer than a few years at most. The information must be kept safe and secure. This includes keeping the information backed up and away from any unauthorised access. It would be wrong to leave personal data open to be viewed by just anyone. The files may not be transferred outside of the European Economic Area (that's the EU plus some small European countries) unless the country that the data is being sent to has a suitable data protection law. This part of the DPA has led to some countries passing similar laws to allow computer data centres to be located in their area.

What rights do data subjects have? They have the right to: see what data is being held about them if they ask the data user. They may have to pay to see it change anything that is wrong refuse to have some data stored at all, if it might cause damage or distress refuse to allow processing for direct marketing – junk mail complain to the Data Protection Commission if they think the rules have been broken claim compensation if they can prove they have been caused damage by a data controller breaking the rules.

Do users always have those rights? There a few cases when the Data Protection Act does not apply. These are called exemptions to the Act. Here a few of them: national security – you cannot demand to see your data if national security is at stake police investigations – information being used to prevent crime is not covered (though police records are) examination results are exempt until they are published by the examining bodies.

Computer Misuse Act • Hacking - Unauthorised user who attempts to or gains access to an information system • Virus - A virus is a program written to cause mischief or damage to a computer system. • The Computer Misuse Act (1990) was developed to cope with the problems of computer hackers and viruses. • There are three principles to the act

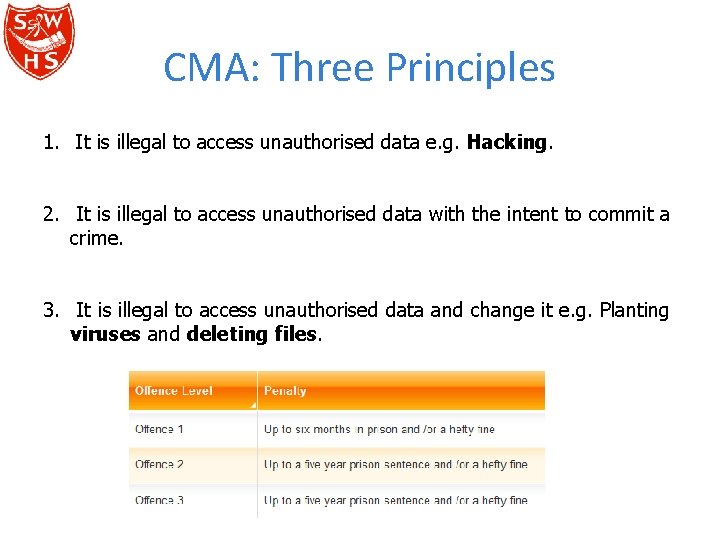
CMA: Three Principles 1. It is illegal to access unauthorised data e. g. Hacking. 2. It is illegal to access unauthorised data with the intent to commit a crime. 3. It is illegal to access unauthorised data and change it e. g. Planting viruses and deleting files.

Protecting systems from Hackers http: //www. teach-ict. com/gcse_new/protecting_systems/hackers/miniweb/index. htm

Copyright, Designs and Patents Act 1988 • People spend a lot of time creating original work so they should be able to protect it and not allow others to use it without permission. • The Act protects intellectual property being copied such as: – – – A piece of music Images on a website, pictures Text - a newspaper article, books etc. New software New Hardware

Copyright, Designs and Patents Act 1988 • These are some examples of actions that are illegal: – Copying software and music illegally – Copying images and text without permission – Copying sections of websites – Sharing digital music – Running more copies of software than is allowed by license

RIPA & The Electronic Communications Act WJEC ICT – Unit 3

What is RIPA? • It allows authorised people to carry out surveillance or data investigations upon individuals or businesses. • It makes it illegal for unauthorised people to do this. • It covers two main areas: – Detection and prevention of terrorism – Prevention and detection of crime

What does it let people do? • It’s all about protecting national security. • It gives authorised people (e. g. police) permission to: – – – Intercept and read (or listen to) electronic communications Read all mail. Demand access to your personal equipment (e. g. PC). Monitor your internet activity. Carry out surveillance upon you • IF THERE IS A POTENTIAL NATIONAL SECURITY RISK FROM TERRORISM OR A CRIME.

Issues • Many people believe this is an invasion of privacy – especially when being falsely accused. • Many businesses monitor people at work – invasion of privacy? • Many people are encrypting communications making it very difficult to monitor!

Electronic Communications Act

What is it? • The government realised that internet communications were growing (in 2000). • They wanted to ensure people trusted ecommunications and online sales. • They introduced this law to ensure that companies and people can have legal support when trading online.

What does it cover? • Encryption (cryptographic) services – ensures that encryption with credit card transactions etc. are regulated and controlled – to ensure protection. • Makes digital signatures legally binding like a normal handwritten signature.

Issues • Not many people know what a digital signature is or how to get one. • Not many people know how to actually use a digital signature. • Most people still do not 100% fully trust the internet and prefer a handwritten signature and documents in important situations (e. g. buying a house, car etc. )