CS 5323 Discretionary Access Control DAC Prof Ravi







- Slides: 35

CS 5323 Discretionary Access Control (DAC) Prof. Ravi Sandhu Executive Director and Endowed Chair Lecture 2 ravi. utsa@gmail. com www. profsandhu. com © Ravi Sandhu World-Leading Research with Real-World Impact! 1

Authentication © Ravi Sandhu World-Leading Research with Real-World Impact! 2

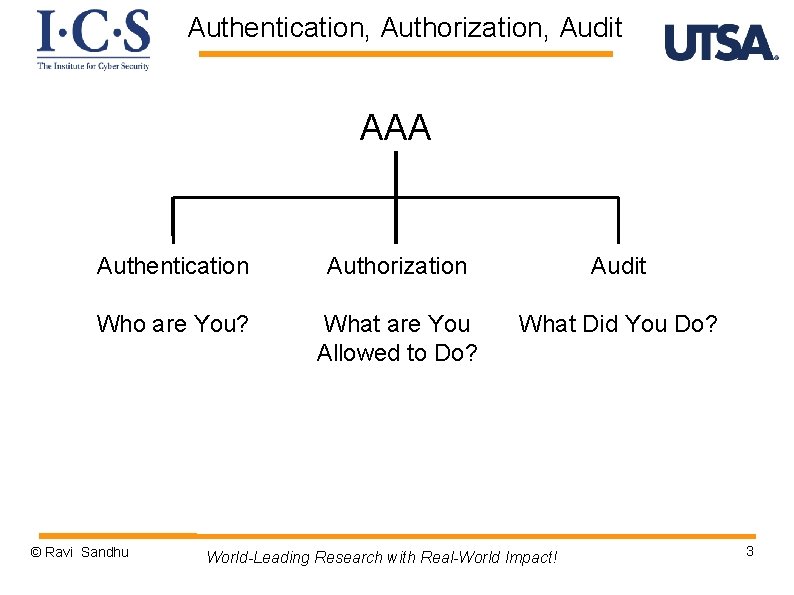
Authentication, Authorization, Audit AAA Authentication Authorization Audit Who are You? What are You Allowed to Do? What Did You Do? © Ravi Sandhu World-Leading Research with Real-World Impact! 3

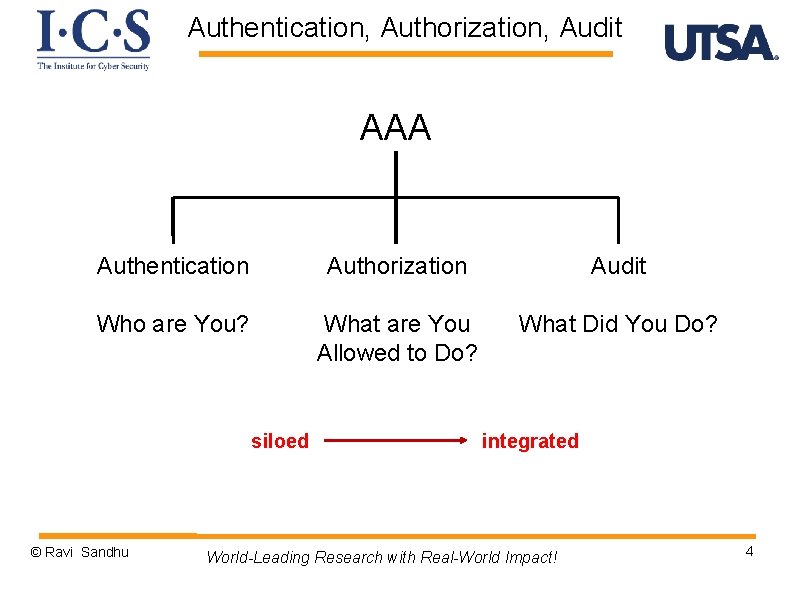
Authentication, Authorization, Audit AAA Authentication Authorization Audit Who are You? What are You Allowed to Do? What Did You Do? siloed © Ravi Sandhu integrated World-Leading Research with Real-World Impact! 4

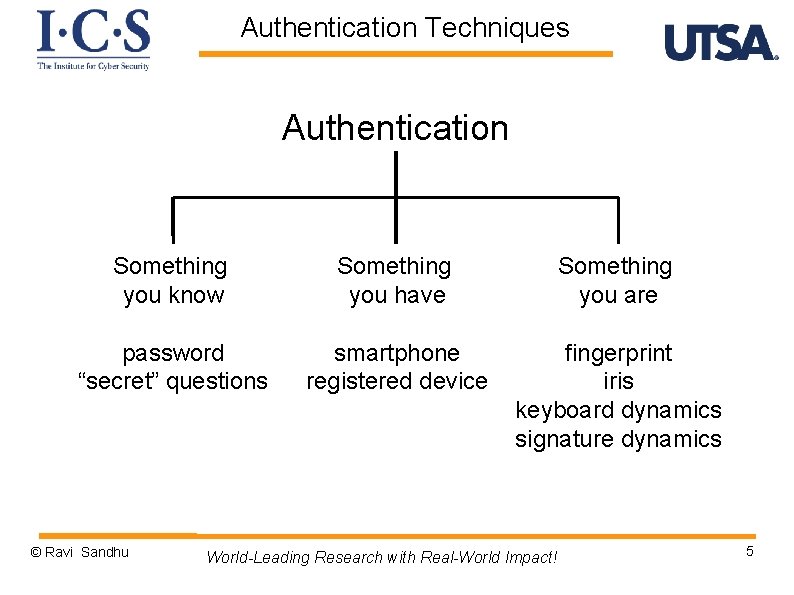
Authentication Techniques Authentication Something you know Something you have Something you are password “secret” questions smartphone registered device fingerprint iris keyboard dynamics signature dynamics © Ravi Sandhu World-Leading Research with Real-World Impact! 5

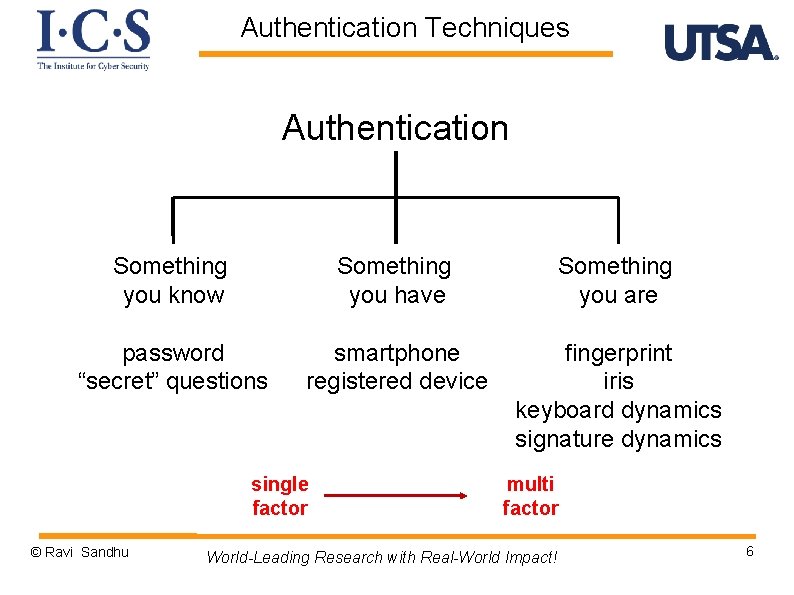
Authentication Techniques Authentication Something you know Something you have Something you are password “secret” questions smartphone registered device fingerprint iris keyboard dynamics signature dynamics single factor © Ravi Sandhu multi factor World-Leading Research with Real-World Impact! 6

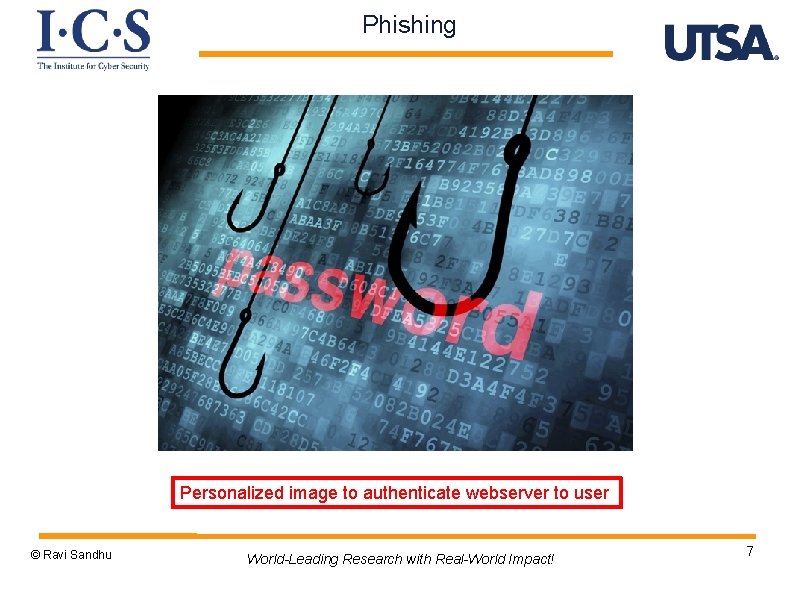
Phishing Personalized image to authenticate webserver to user © Ravi Sandhu World-Leading Research with Real-World Impact! 7

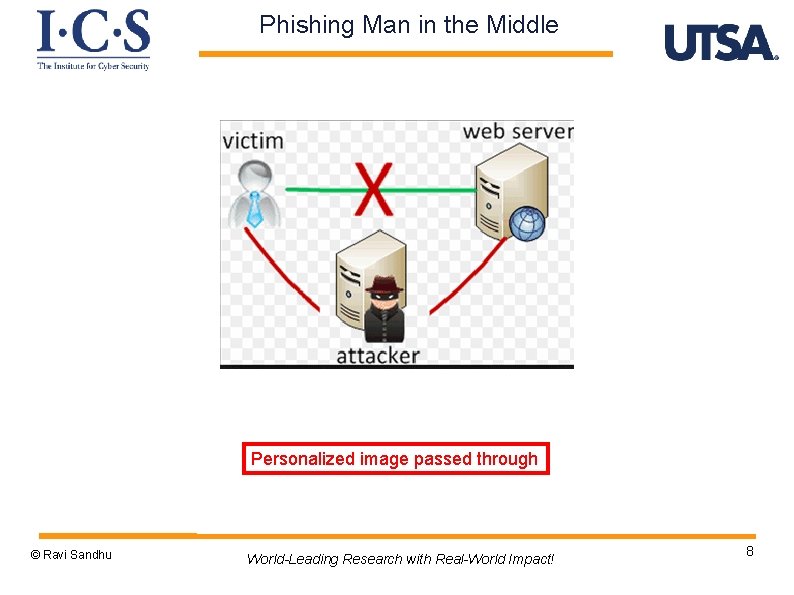
Phishing Man in the Middle Personalized image passed through © Ravi Sandhu World-Leading Research with Real-World Impact! 8

Passwords © Ravi Sandhu World-Leading Research with Real-World Impact! 9

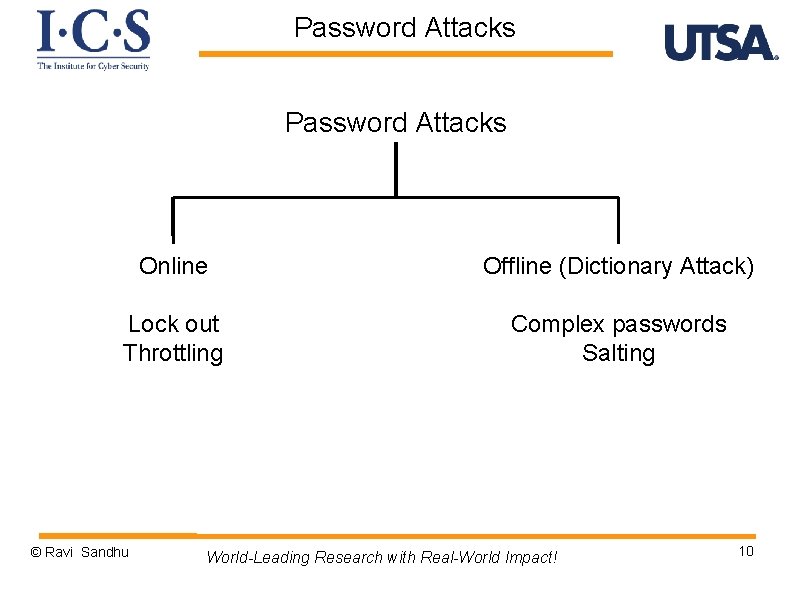
Password Attacks Online Offline (Dictionary Attack) Lock out Throttling Complex passwords Salting © Ravi Sandhu World-Leading Research with Real-World Impact! 10

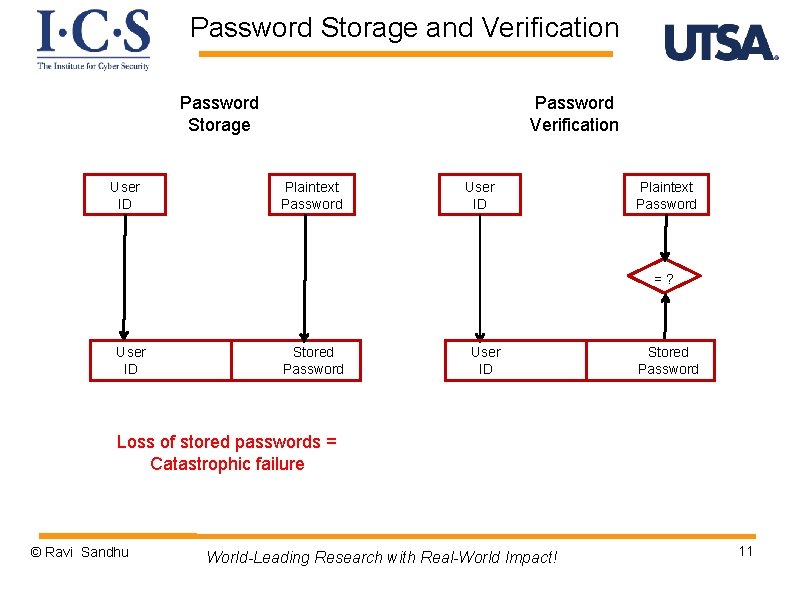
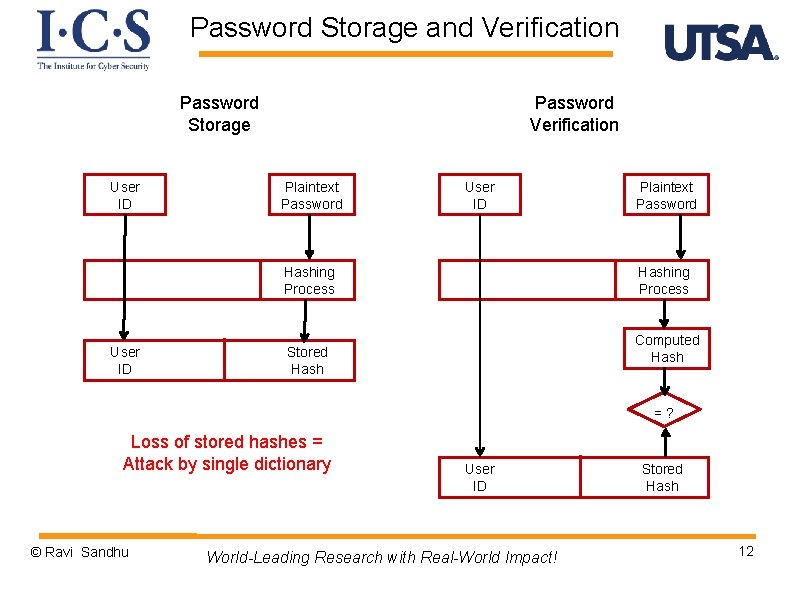
Password Storage and Verification Password Storage User ID Password Verification Plaintext Password User ID Plaintext Password =? User ID Stored Password Loss of stored passwords = Catastrophic failure © Ravi Sandhu World-Leading Research with Real-World Impact! 11

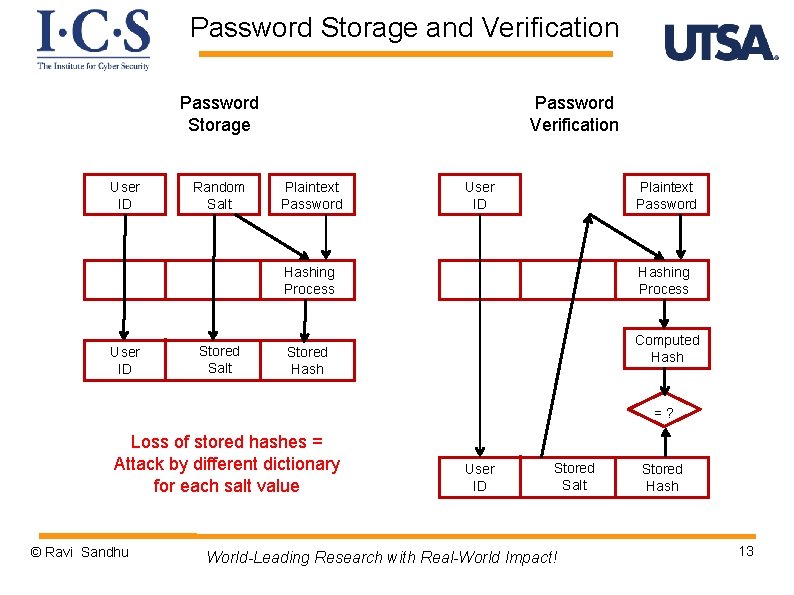
Password Storage and Verification Password Storage User ID Password Verification Plaintext Password User ID Hashing Process User ID Plaintext Password Hashing Process Computed Hash Stored Hash =? Loss of stored hashes = Attack by single dictionary © Ravi Sandhu User ID World-Leading Research with Real-World Impact! Stored Hash 12

Password Storage and Verification Password Storage User ID Random Salt Password Verification Plaintext Password User ID Plaintext Password Hashing Process User ID Stored Salt Hashing Process Computed Hash Stored Hash =? Loss of stored hashes = Attack by different dictionary for each salt value © Ravi Sandhu User ID Stored Salt World-Leading Research with Real-World Impact! Stored Hash 13

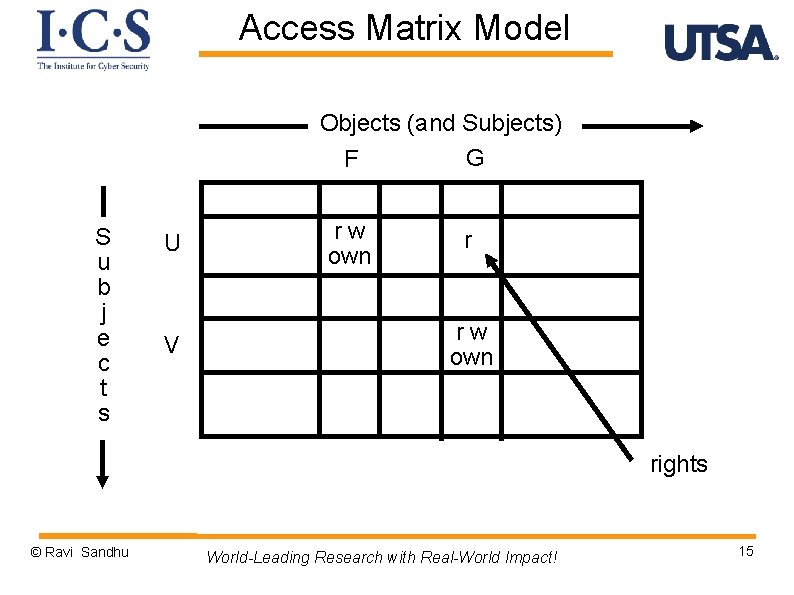
Access Matrix Model © Ravi Sandhu World-Leading Research with Real-World Impact! 14

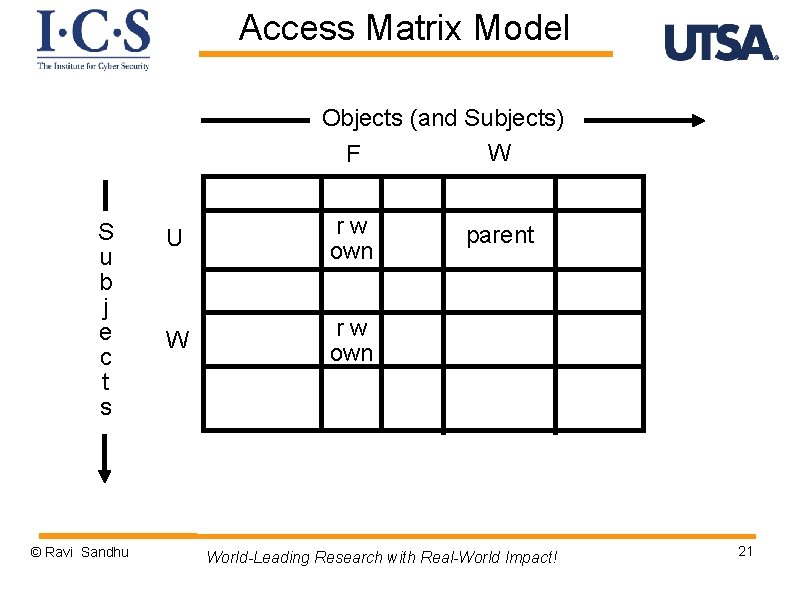
Access Matrix Model Objects (and Subjects) G F S u b j e c t s U V rw own rights © Ravi Sandhu World-Leading Research with Real-World Impact! 15

Access Matrix Model Ø Basic Abstractions v Subjects v Objects v Rights ØThe rights in a cell specify the access of the subject (row) to the object (column) © Ravi Sandhu World-Leading Research with Real-World Impact! 16

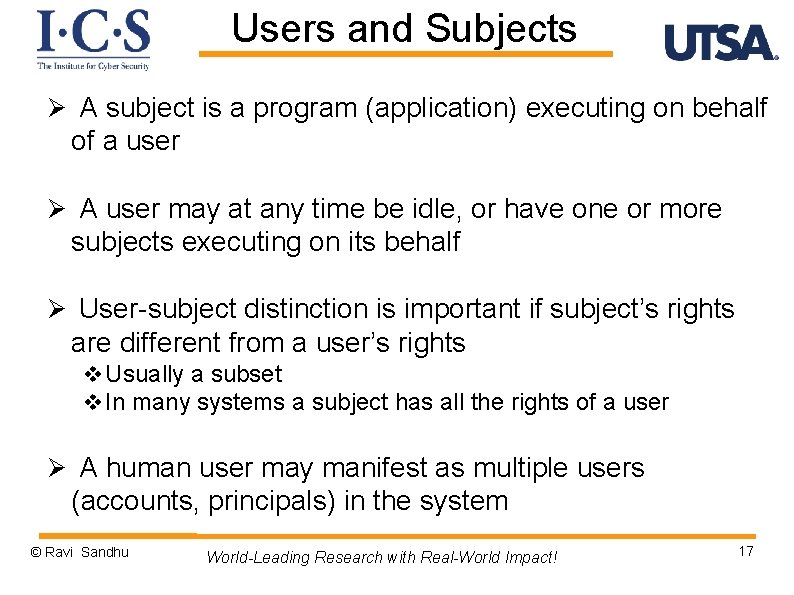
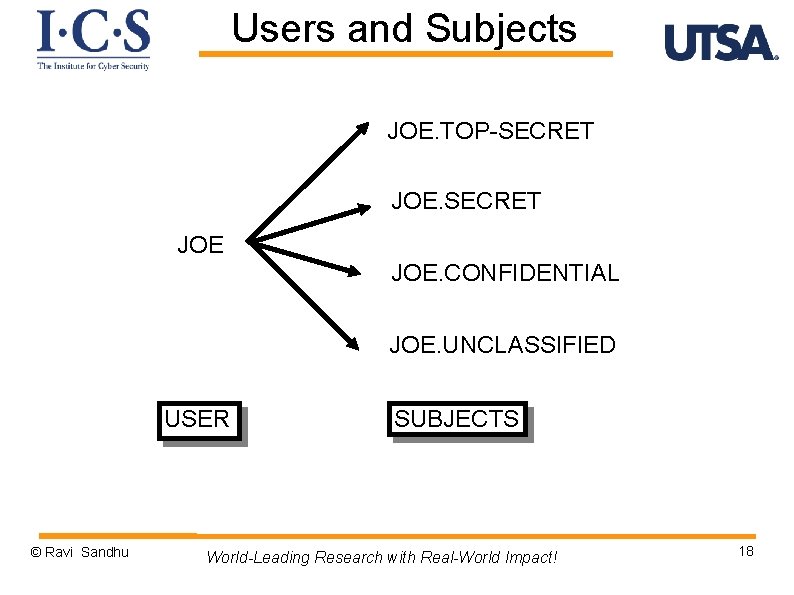
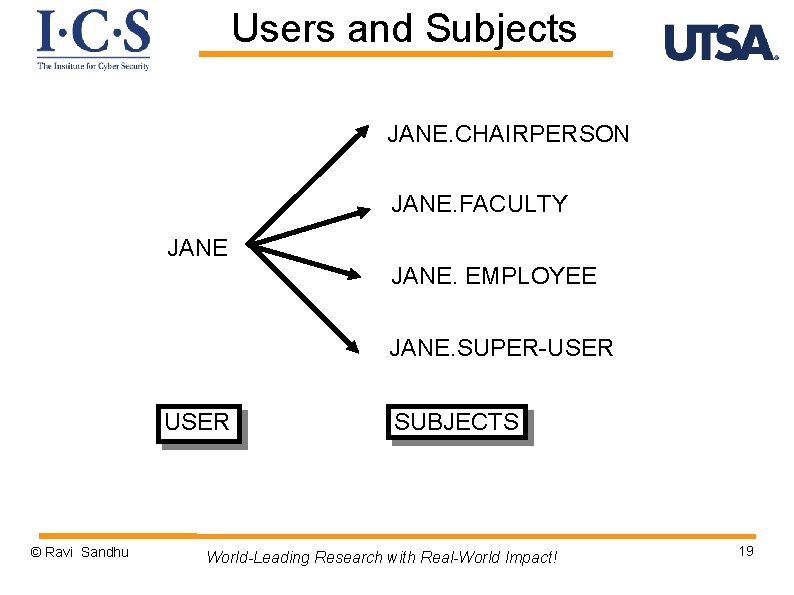
Users and Subjects Ø A subject is a program (application) executing on behalf of a user Ø A user may at any time be idle, or have one or more subjects executing on its behalf Ø User-subject distinction is important if subject’s rights are different from a user’s rights v Usually a subset v In many systems a subject has all the rights of a user Ø A human user may manifest as multiple users (accounts, principals) in the system © Ravi Sandhu World-Leading Research with Real-World Impact! 17

Users and Subjects JOE. TOP-SECRET JOE. CONFIDENTIAL JOE. UNCLASSIFIED USER © Ravi Sandhu SUBJECTS World-Leading Research with Real-World Impact! 18

Users and Subjects JANE. CHAIRPERSON JANE. FACULTY JANE. EMPLOYEE JANE. SUPER-USER © Ravi Sandhu SUBJECTS World-Leading Research with Real-World Impact! 19

Objects Ø An object is anything on which a subject can perform operations (mediated by rights) Ø Usually objects are passive, for example: v File v Directory (or Folder) v Memory segment with CRUD operations (create, read, update, delete) Ø But, subjects can also be objects, with operations v kill v suspend v resume © Ravi Sandhu World-Leading Research with Real-World Impact! 20

Access Matrix Model Objects (and Subjects) W F S u b j e c t s © Ravi Sandhu U rw own W rw own parent World-Leading Research with Real-World Impact! 21

Implementation Ø Access Control Lists Ø Capabilities Ø Relations © Ravi Sandhu World-Leading Research with Real-World Impact! 22

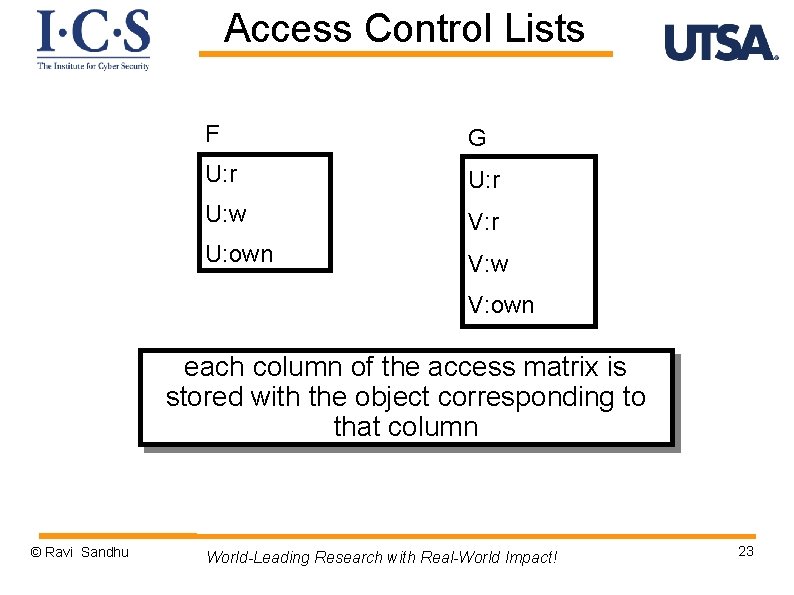
Access Control Lists F G U: r U: w V: r U: own V: w V: own each column of the access matrix is stored with the object corresponding to that column © Ravi Sandhu World-Leading Research with Real-World Impact! 23

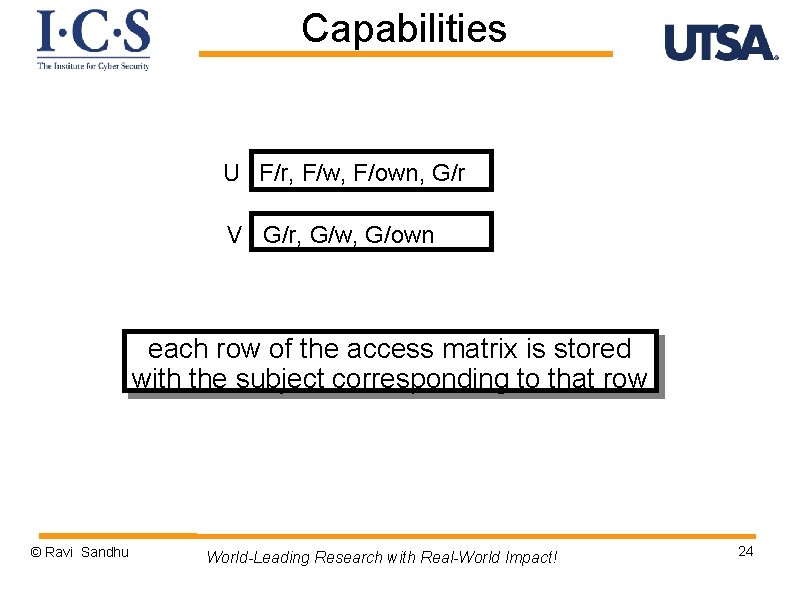
Capabilities U F/r, F/w, F/own, G/r V G/r, G/w, G/own each row of the access matrix is stored with the subject corresponding to that row © Ravi Sandhu World-Leading Research with Real-World Impact! 24

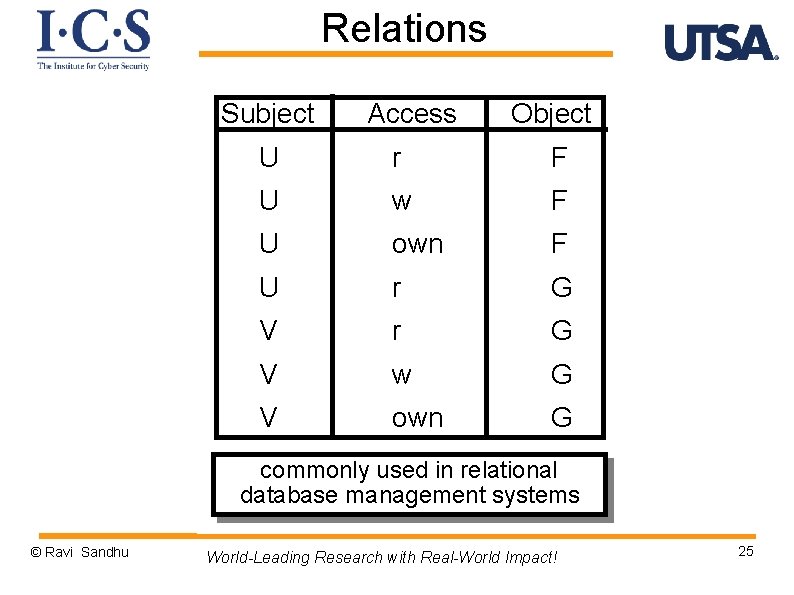
Relations Subject Access Object U r F U w F U own F U r G V w G V own G commonly used in relational database management systems © Ravi Sandhu World-Leading Research with Real-World Impact! 25

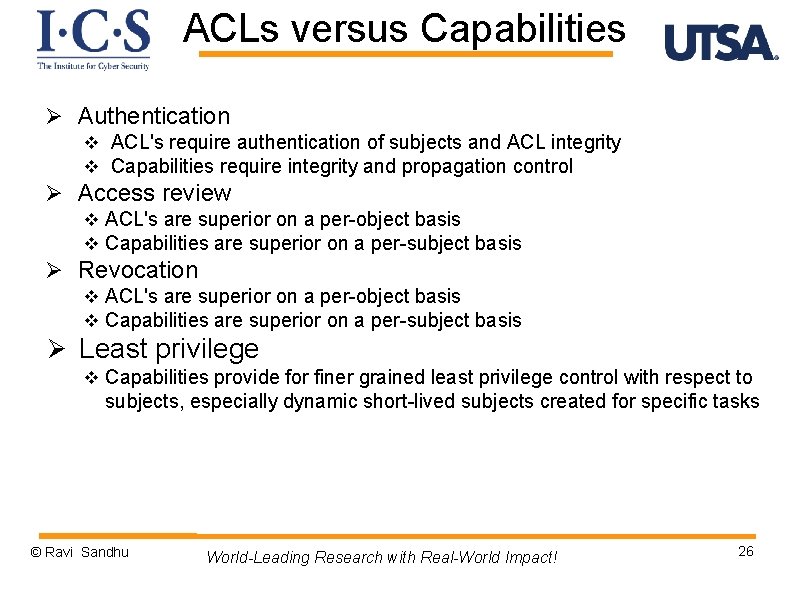
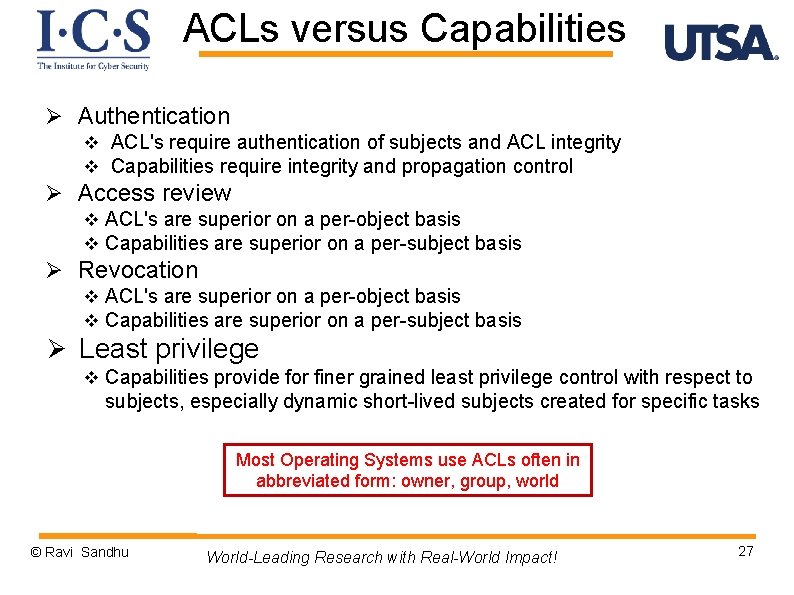
ACLs versus Capabilities Ø Authentication v ACL's require authentication of subjects and ACL integrity v Capabilities require integrity and propagation control Ø Access review v ACL's are superior on a per-object basis v Capabilities are superior on a per-subject basis Ø Revocation v ACL's are superior on a per-object basis v Capabilities are superior on a per-subject basis Ø Least privilege v Capabilities provide for finer grained least privilege control with respect to subjects, especially dynamic short-lived subjects created for specific tasks © Ravi Sandhu World-Leading Research with Real-World Impact! 26

ACLs versus Capabilities Ø Authentication v ACL's require authentication of subjects and ACL integrity v Capabilities require integrity and propagation control Ø Access review v ACL's are superior on a per-object basis v Capabilities are superior on a per-subject basis Ø Revocation v ACL's are superior on a per-object basis v Capabilities are superior on a per-subject basis Ø Least privilege v Capabilities provide for finer grained least privilege control with respect to subjects, especially dynamic short-lived subjects created for specific tasks Most Operating Systems use ACLs often in abbreviated form: owner, group, world © Ravi Sandhu World-Leading Research with Real-World Impact! 27

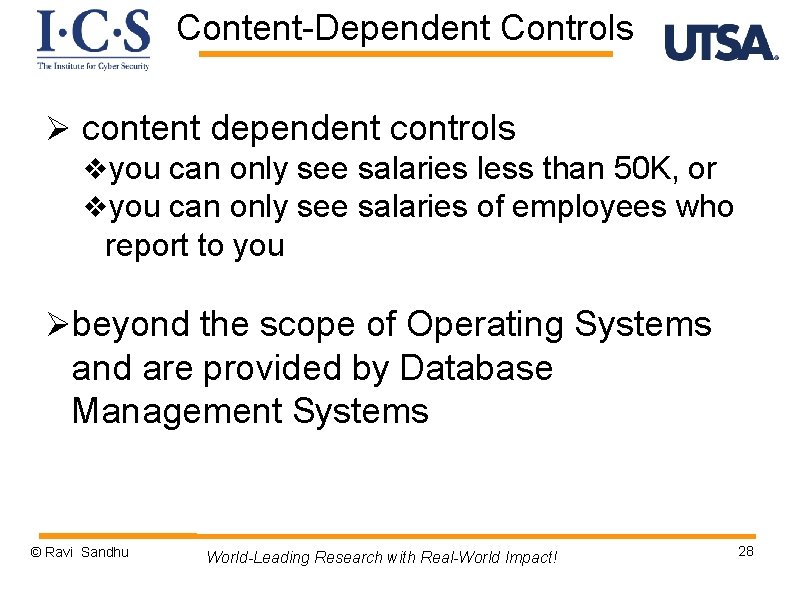
Content-Dependent Controls Ø content dependent controls vyou can only see salaries less than 50 K, or vyou can only see salaries of employees who report to you Øbeyond the scope of Operating Systems and are provided by Database Management Systems © Ravi Sandhu World-Leading Research with Real-World Impact! 28

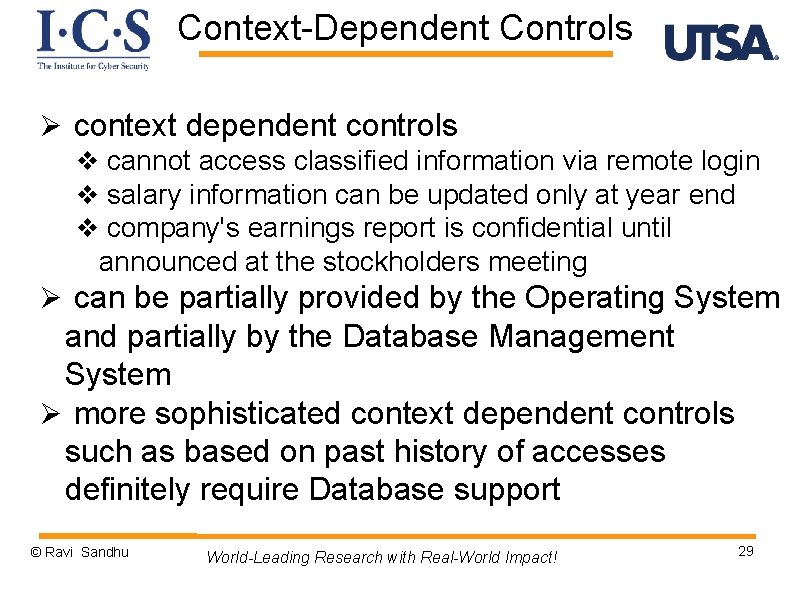
Context-Dependent Controls Ø context dependent controls v cannot access classified information via remote login v salary information can be updated only at year end v company's earnings report is confidential until announced at the stockholders meeting Ø can be partially provided by the Operating System and partially by the Database Management System Ø more sophisticated context dependent controls such as based on past history of accesses definitely require Database support © Ravi Sandhu World-Leading Research with Real-World Impact! 29

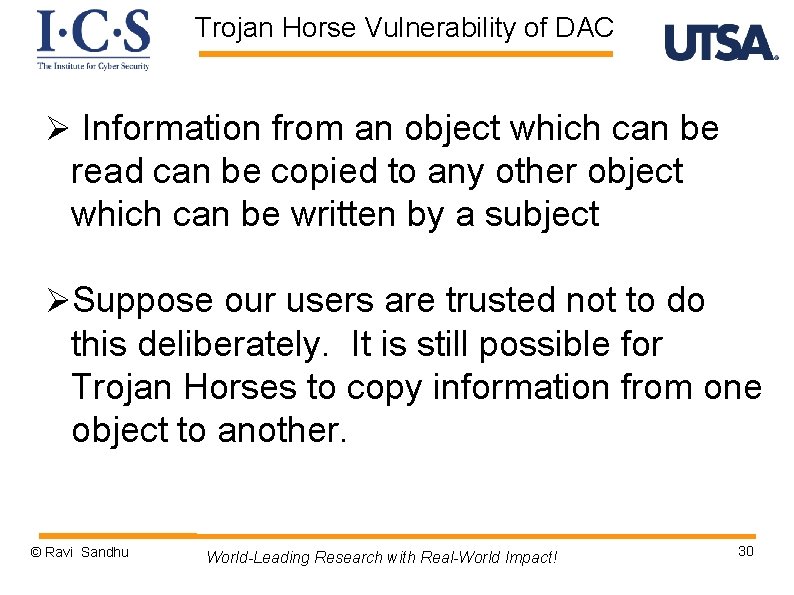
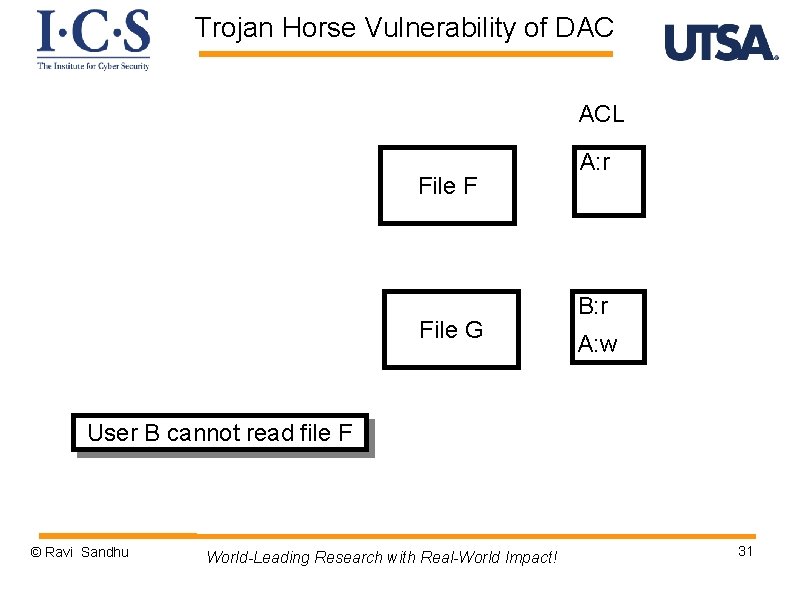
Trojan Horse Vulnerability of DAC Ø Information from an object which can be read can be copied to any other object which can be written by a subject ØSuppose our users are trusted not to do this deliberately. It is still possible for Trojan Horses to copy information from one object to another. © Ravi Sandhu World-Leading Research with Real-World Impact! 30

Trojan Horse Vulnerability of DAC ACL File F File G A: r B: r A: w User B cannot read file F © Ravi Sandhu World-Leading Research with Real-World Impact! 31

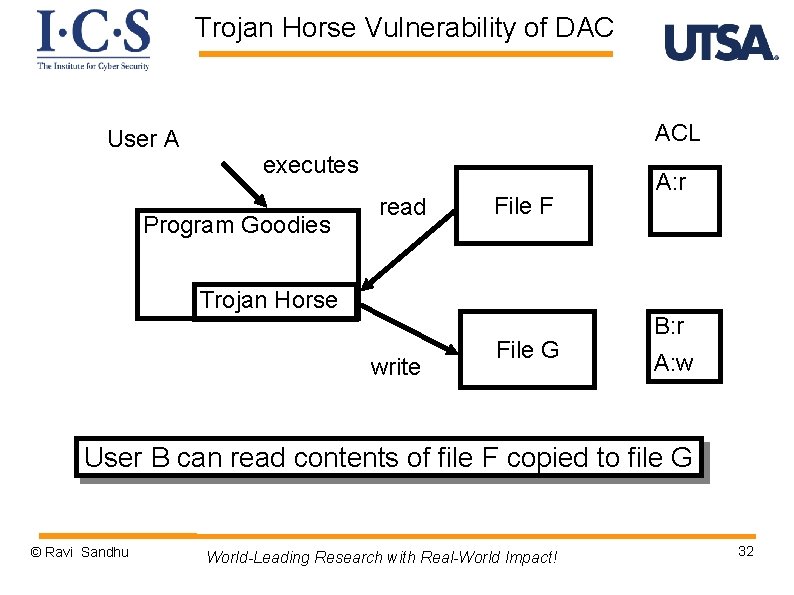
Trojan Horse Vulnerability of DAC User A ACL executes Program Goodies read File F Trojan Horse write File G A: r B: r A: w User B can read contents of file F copied to file G © Ravi Sandhu World-Leading Research with Real-World Impact! 32

Copy Difference for rw Ø Read of a digital copy is as good as read of original Ø Write to a digital copy is not so useful © Ravi Sandhu World-Leading Research with Real-World Impact! 33

DAC Subtleties Ø Chains of grants and revokes Ø Inheritance of permissions Ø Negative rights © Ravi Sandhu World-Leading Research with Real-World Impact! 34

HRU Model Harrison, M. A. , Ruzzo, W. L. , & Ullman, J. D. (1976). Protection in operating systems. Communications of the ACM, 19(8), 461 -471. © Ravi Sandhu World-Leading Research with Real-World Impact! 35