CS 5323 Asymmetric Cryptography Prof Ravi Sandhu Executive
















- Slides: 44

CS 5323 Asymmetric Cryptography Prof. Ravi Sandhu Executive Director and Endowed Chair Lecture 8 ravi. utsa@gmail. com www. profsandhu. com © Ravi Sandhu World-Leading Research with Real-World Impact! 1

Asymmetric Encryption © Ravi Sandhu World-Leading Research with Real-World Impact! 2

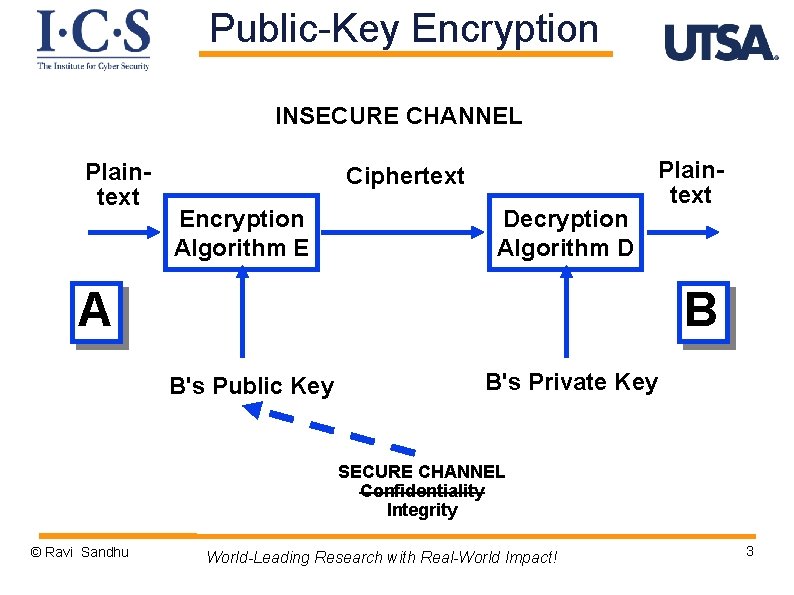
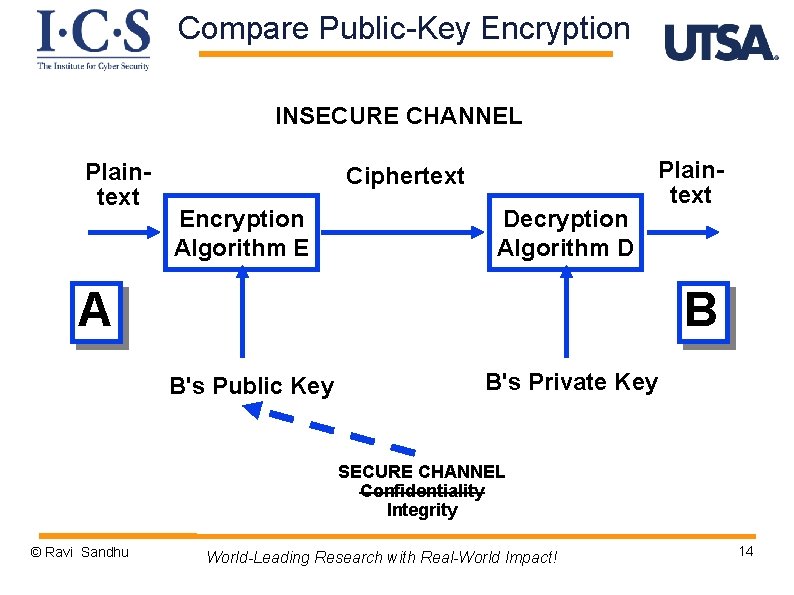
Public-Key Encryption INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Plaintext B B's Public Key B's Private Key SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 3

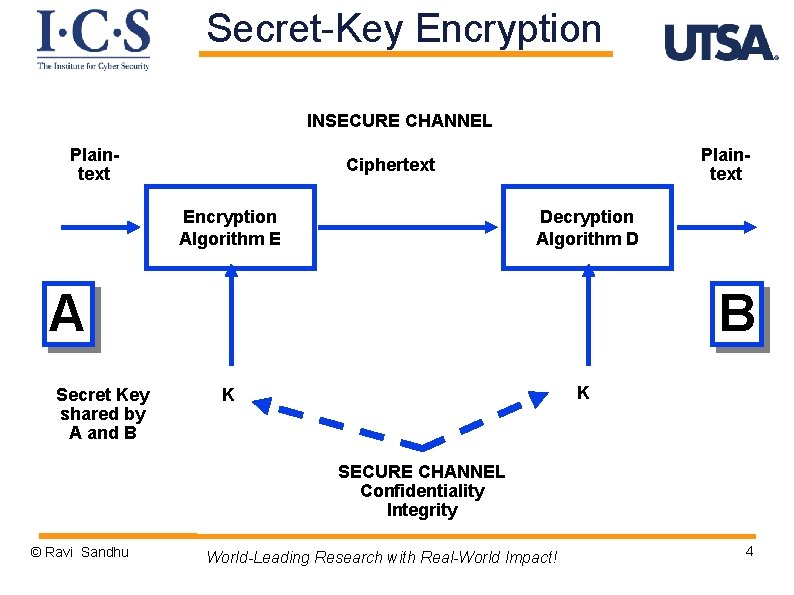
Secret-Key Encryption INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Secret Key shared by A and B B K K SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 4

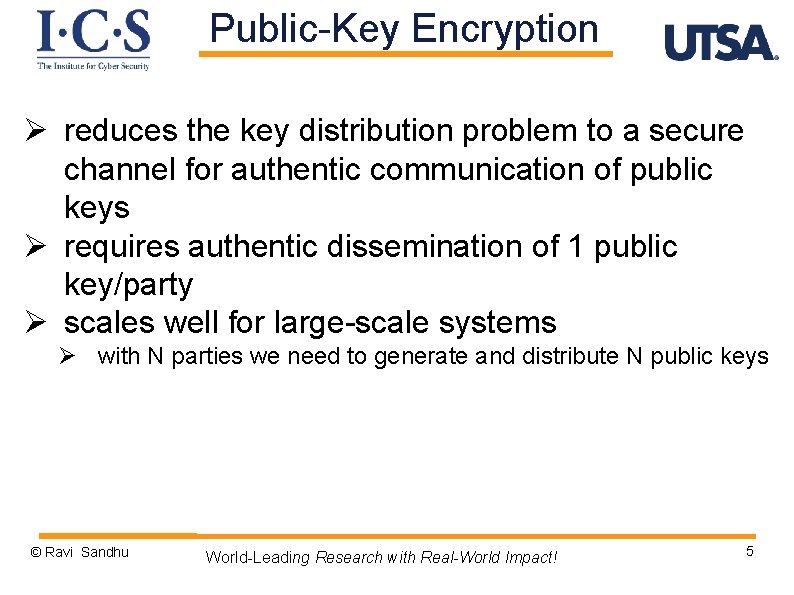
Public-Key Encryption Ø reduces the key distribution problem to a secure channel for authentic communication of public keys Ø requires authentic dissemination of 1 public key/party Ø scales well for large-scale systems Ø with N parties we need to generate and distribute N public keys © Ravi Sandhu World-Leading Research with Real-World Impact! 5

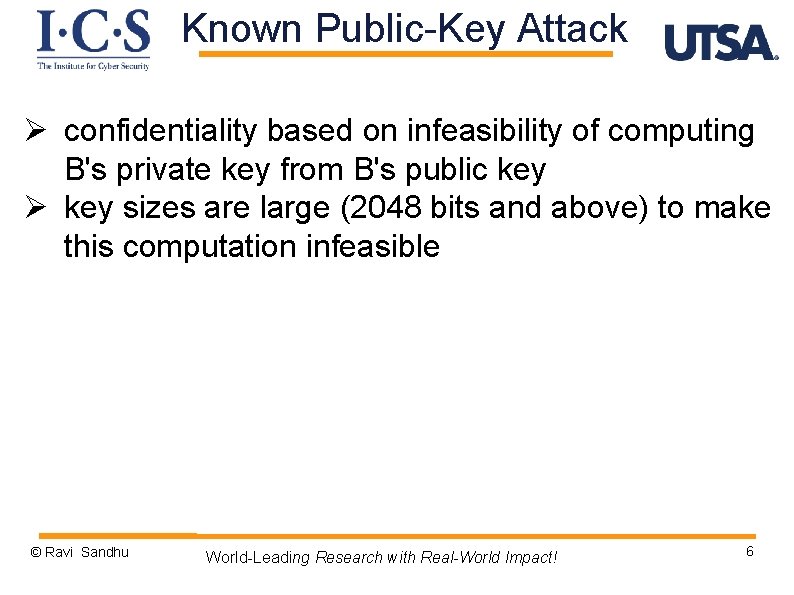
Known Public-Key Attack Ø confidentiality based on infeasibility of computing B's private key from B's public key Ø key sizes are large (2048 bits and above) to make this computation infeasible © Ravi Sandhu World-Leading Research with Real-World Impact! 6

Speed Ø public key runs 1000 times slower than secret key v think 2 g versus 4 g on smartphone Ø This large difference in speed is likely to remain v Maybe reduce to 100 times Ø Use public keys to distribute secret keys, use secret keys to protect data © Ravi Sandhu World-Leading Research with Real-World Impact! 7

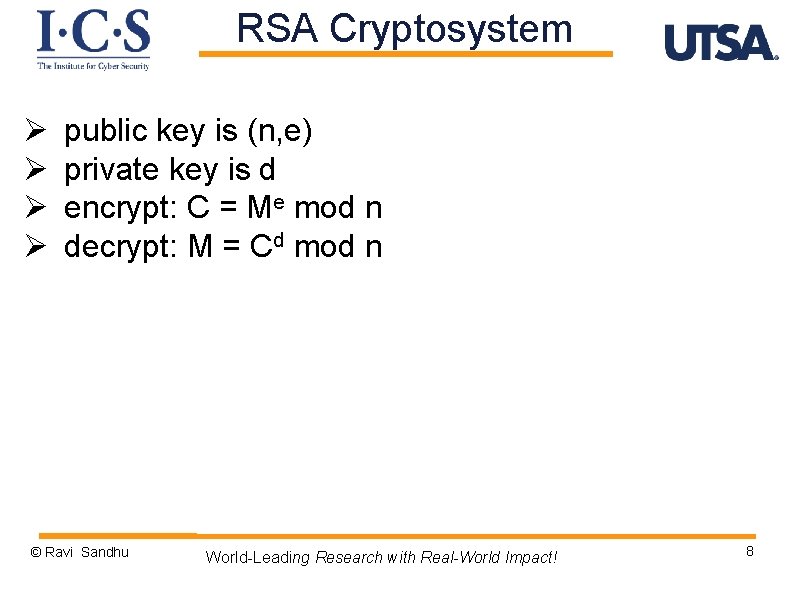
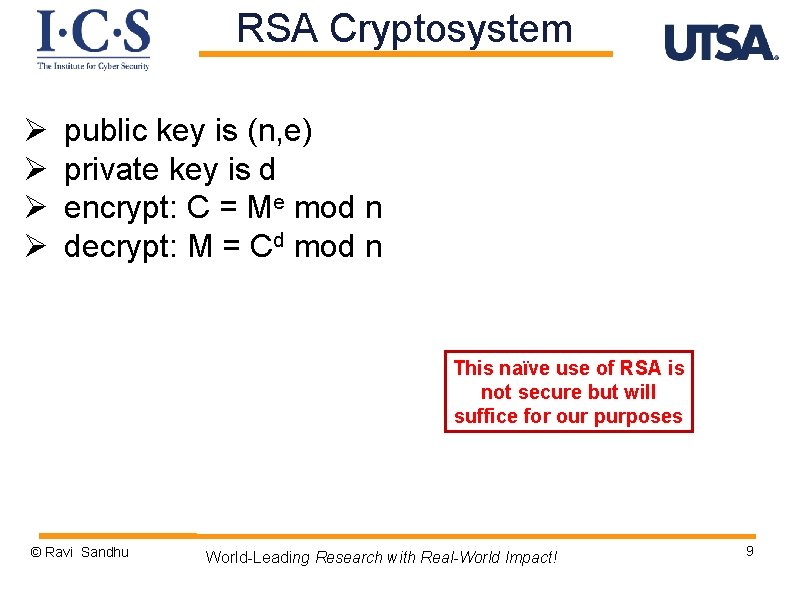
RSA Cryptosystem Ø Ø public key is (n, e) private key is d encrypt: C = Me mod n decrypt: M = Cd mod n © Ravi Sandhu World-Leading Research with Real-World Impact! 8

RSA Cryptosystem Ø Ø public key is (n, e) private key is d encrypt: C = Me mod n decrypt: M = Cd mod n This naïve use of RSA is not secure but will suffice for our purposes © Ravi Sandhu World-Leading Research with Real-World Impact! 9

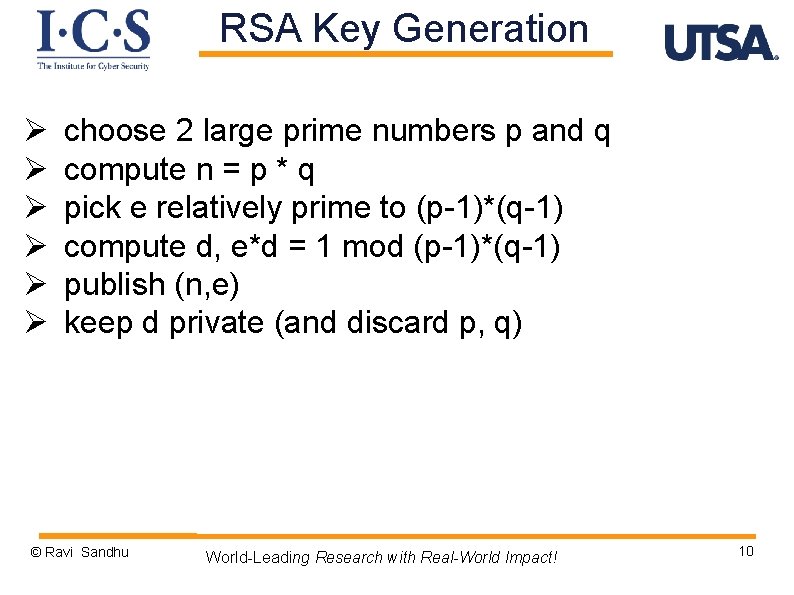
RSA Key Generation Ø Ø Ø choose 2 large prime numbers p and q compute n = p * q pick e relatively prime to (p-1)*(q-1) compute d, e*d = 1 mod (p-1)*(q-1) publish (n, e) keep d private (and discard p, q) © Ravi Sandhu World-Leading Research with Real-World Impact! 10

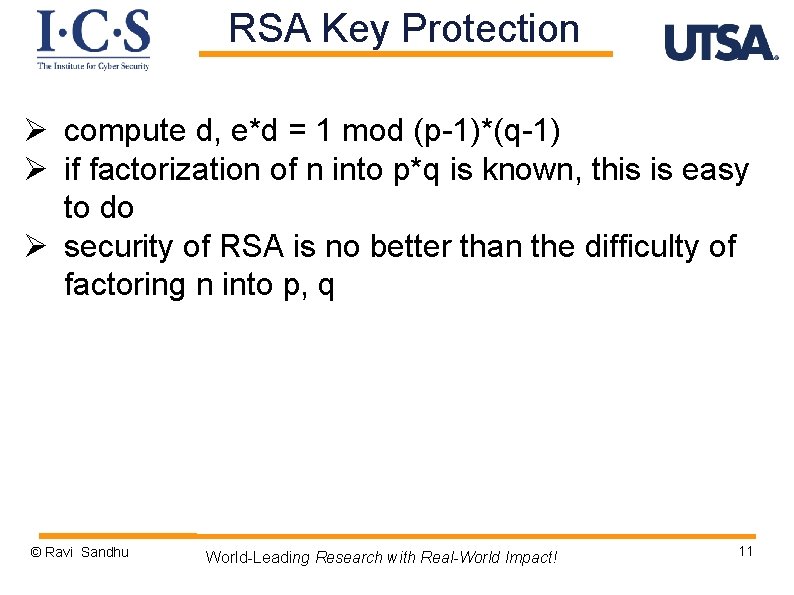
RSA Key Protection Ø compute d, e*d = 1 mod (p-1)*(q-1) Ø if factorization of n into p*q is known, this is easy to do Ø security of RSA is no better than the difficulty of factoring n into p, q © Ravi Sandhu World-Leading Research with Real-World Impact! 11

Asymmetric Digital Signatures © Ravi Sandhu World-Leading Research with Real-World Impact! 12

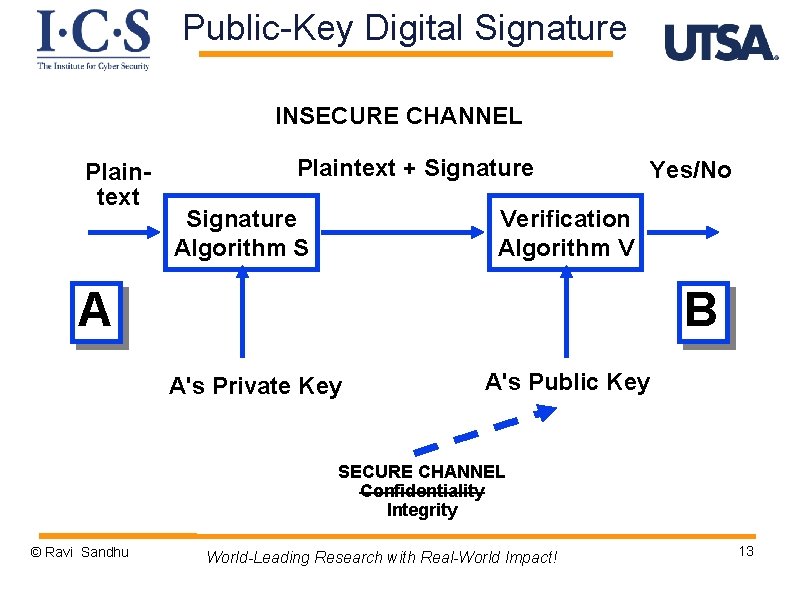
Public-Key Digital Signature INSECURE CHANNEL Plaintext + Signature Algorithm S Yes/No Verification Algorithm V A B A's Private Key A's Public Key SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 13

Compare Public-Key Encryption INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Plaintext B B's Public Key B's Private Key SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 14

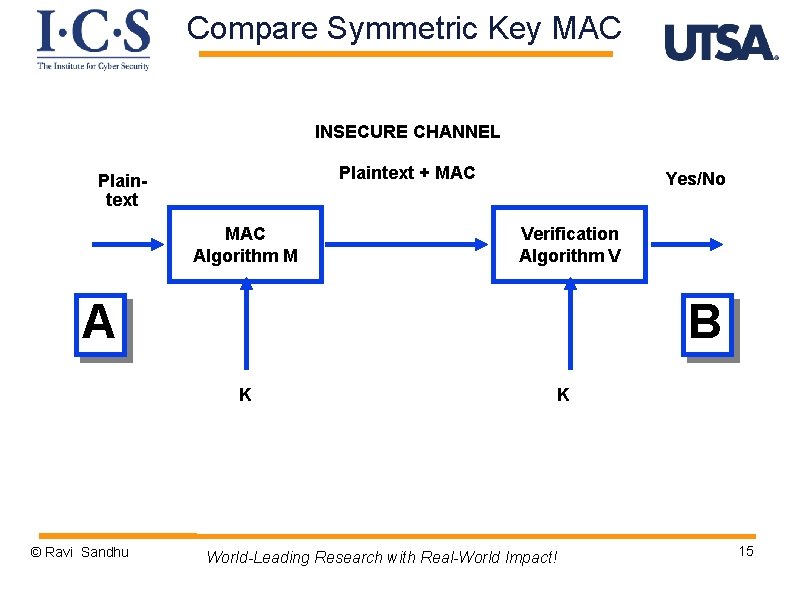
Compare Symmetric Key MAC INSECURE CHANNEL Plaintext + MAC Plaintext MAC Algorithm M Yes/No Verification Algorithm V A B K © Ravi Sandhu K World-Leading Research with Real-World Impact! 15

Digital Signatures in RSA Ø RSA has a unique property, not shared by other public key systems Ø Encryption and decryption commute Ø (Me mod n)d mod n = M encryption Ø (Md mod n)e mod n = M signature Ø Same public key can be use for encryption and signature v But not recommended © Ravi Sandhu World-Leading Research with Real-World Impact! 16

Message Digest © Ravi Sandhu World-Leading Research with Real-World Impact! 17

Encryption Speed Revisited Ø public key runs 1000 times slower than secret key v think 2 g versus 4 g on smartphone Ø This large difference in speed is likely to remain v Maybe reduce to 100 times Ø Use public keys to distribute secret keys, use secret keys to protect data © Ravi Sandhu World-Leading Research with Real-World Impact! 18

Digital Signature Speed Ø public key runs 1000 times slower than secret key v think 2 g versus 4 g on smartphone Ø This large difference in speed is likely to remain v Maybe reduce to 100 times Ø Sign the message digest (or hash) not the message © Ravi Sandhu World-Leading Research with Real-World Impact! 19

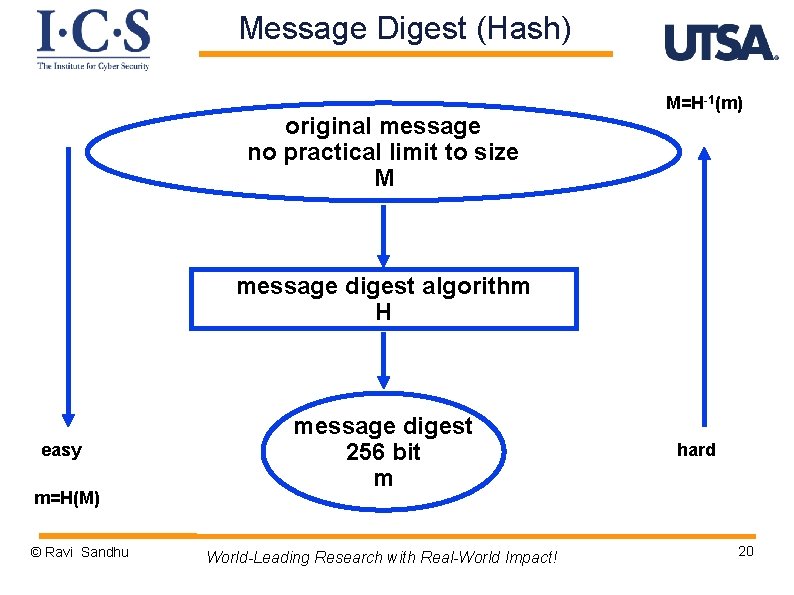
Message Digest (Hash) original message no practical limit to size M M=H-1(m) message digest algorithm H easy m=H(M) © Ravi Sandhu message digest 256 bit m World-Leading Research with Real-World Impact! hard 20

Desired Characteristics Ø weak hash function v difficult to find M' such that H(M')=H(M) Ø given M, m=H(M) try messages at random to find M’ with H(M’)=m v 2 k trials on average, k=128 to be safe © Ravi Sandhu World-Leading Research with Real-World Impact! 21

Desired Characteristics Ø strong hash function v difficult to find any two M and M' such that H(M')=H(M) Ø try pairs of messages at random to find M and M’ such that H(M’)=H(M) v 2 k/2 trials on average, k=256 to be safe Birthday paradox © Ravi Sandhu World-Leading Research with Real-World Impact! 22

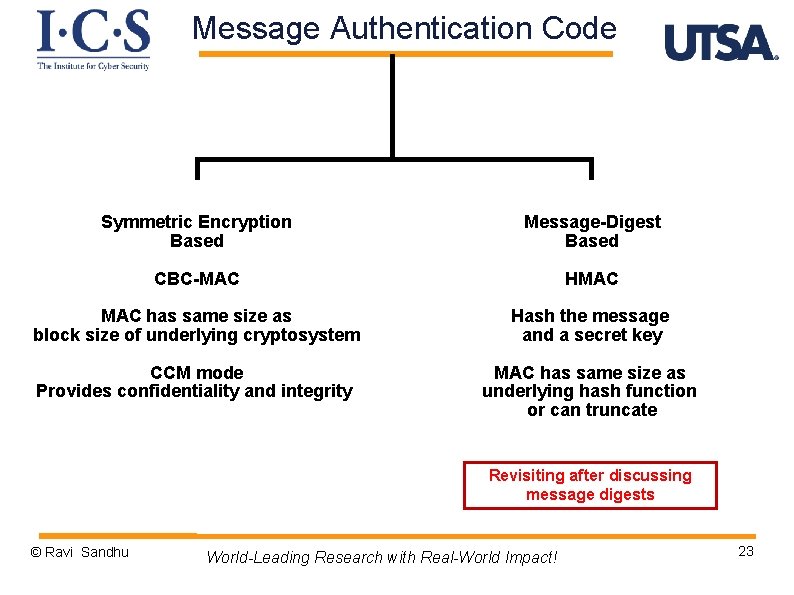
Message Authentication Code Symmetric Encryption Based Message-Digest Based CBC-MAC HMAC has same size as block size of underlying cryptosystem Hash the message and a secret key CCM mode Provides confidentiality and integrity MAC has same size as underlying hash function or can truncate Revisiting after discussing message digests © Ravi Sandhu World-Leading Research with Real-World Impact! 23

Asymmetric Key Exchange © Ravi Sandhu World-Leading Research with Real-World Impact! 24

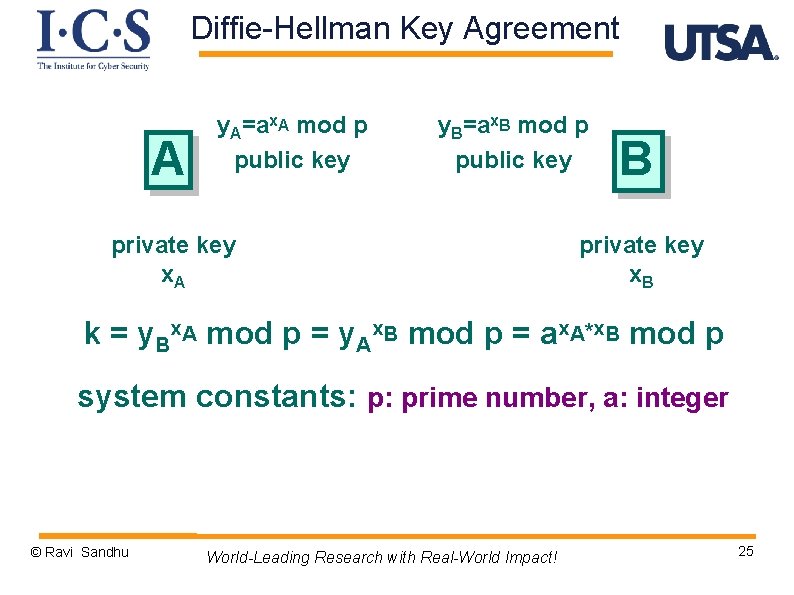
Diffie-Hellman Key Agreement A y. A=ax. A mod p public key y. B=ax. B mod p public key private key x. A B private key x. B k = y. Bx. A mod p = y. Ax. B mod p = ax. A*x. B mod p system constants: p: prime number, a: integer © Ravi Sandhu World-Leading Research with Real-World Impact! 25

Diffie-Hellman Key Agreement Ø security depends on difficulty of computing x given y=ax mod p Ø called the discrete logarithm problem © Ravi Sandhu World-Leading Research with Real-World Impact! 26

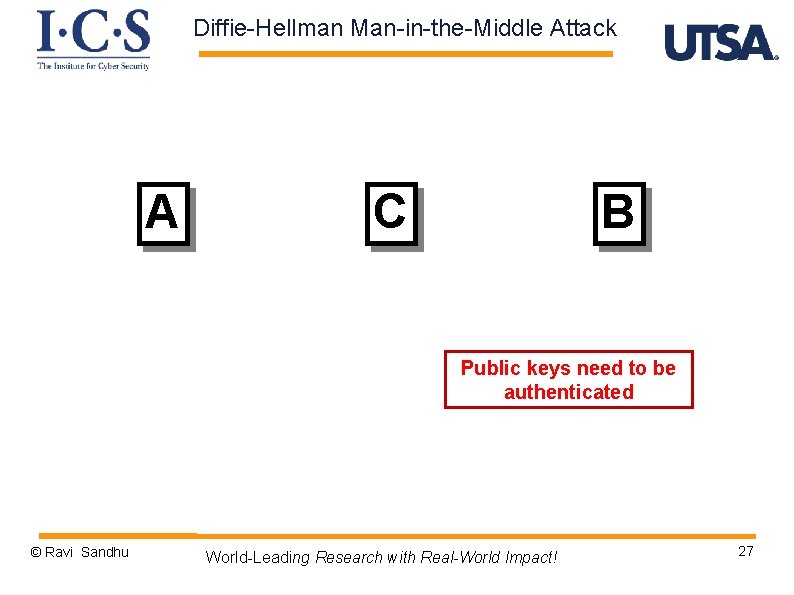
Diffie-Hellman Man-in-the-Middle Attack A C B Public keys need to be authenticated © Ravi Sandhu World-Leading Research with Real-World Impact! 27

Public-Key Certificates © Ravi Sandhu World-Leading Research with Real-World Impact! 28

Public-Key Certificates Ø authenticated distribution of public-keys Ø public-key encryption v sender needs public key of receiver Ø public-key digital signatures v receiver needs public key of sender Ø public-key agreement v both need each other’s public keys © Ravi Sandhu World-Leading Research with Real-World Impact! 29

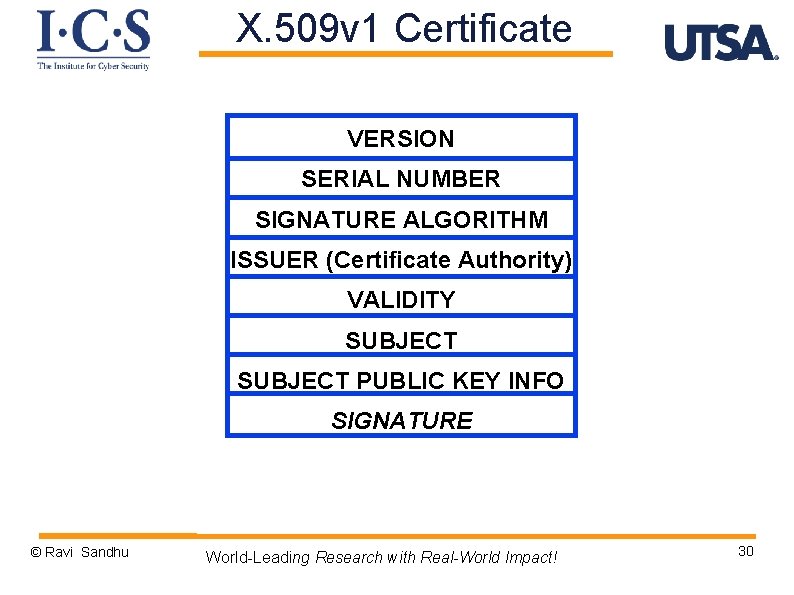
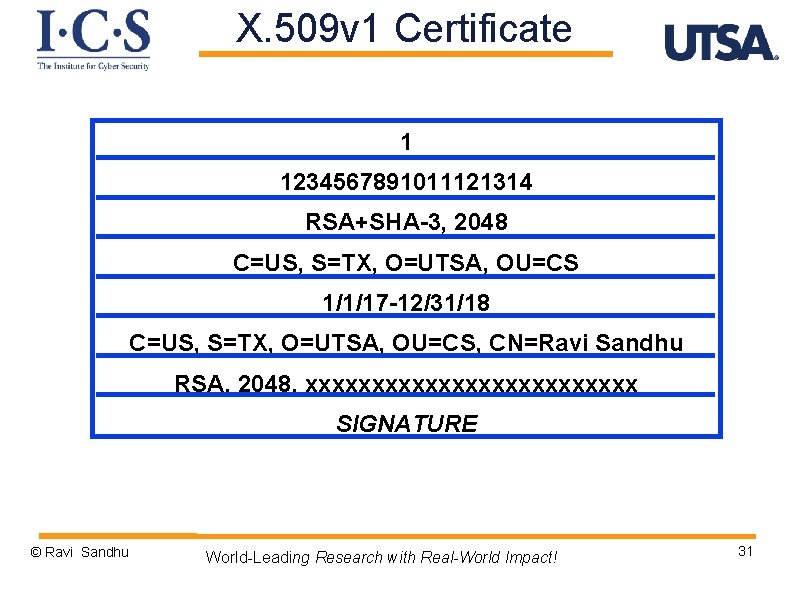
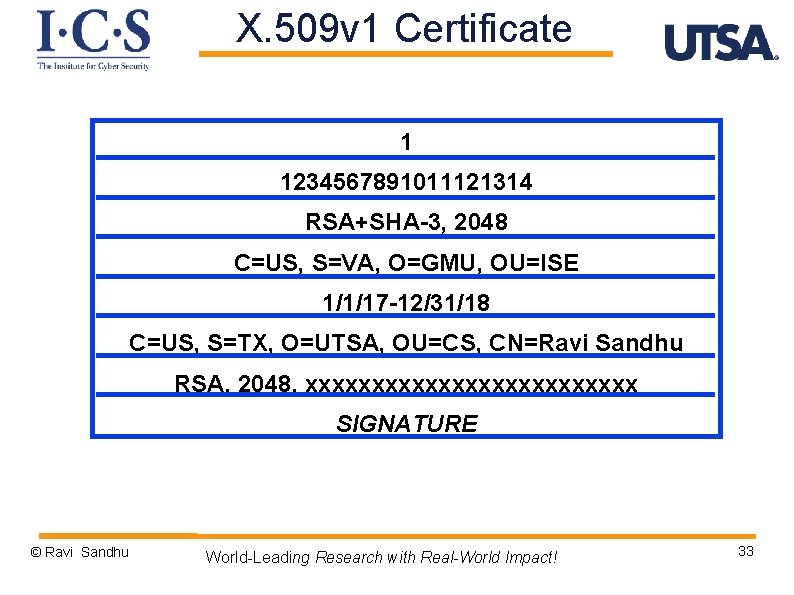
X. 509 v 1 Certificate VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER (Certificate Authority) VALIDITY SUBJECT PUBLIC KEY INFO SIGNATURE © Ravi Sandhu World-Leading Research with Real-World Impact! 30

X. 509 v 1 Certificate 1 1234567891011121314 RSA+SHA-3, 2048 C=US, S=TX, O=UTSA, OU=CS 1/1/17 -12/31/18 C=US, S=TX, O=UTSA, OU=CS, CN=Ravi Sandhu RSA, 2048, xxxxxxxxxxxxx SIGNATURE © Ravi Sandhu World-Leading Research with Real-World Impact! 31

Certificate Trust Ø how to acquire public key of the issuer to verify signature Ø whether or not to trust certificates signed by the issuer for this subject v prefix rule is not universally applicable © Ravi Sandhu World-Leading Research with Real-World Impact! 32

X. 509 v 1 Certificate 1 1234567891011121314 RSA+SHA-3, 2048 C=US, S=VA, O=GMU, OU=ISE 1/1/17 -12/31/18 C=US, S=TX, O=UTSA, OU=CS, CN=Ravi Sandhu RSA, 2048, xxxxxxxxxxxxx SIGNATURE © Ravi Sandhu World-Leading Research with Real-World Impact! 33

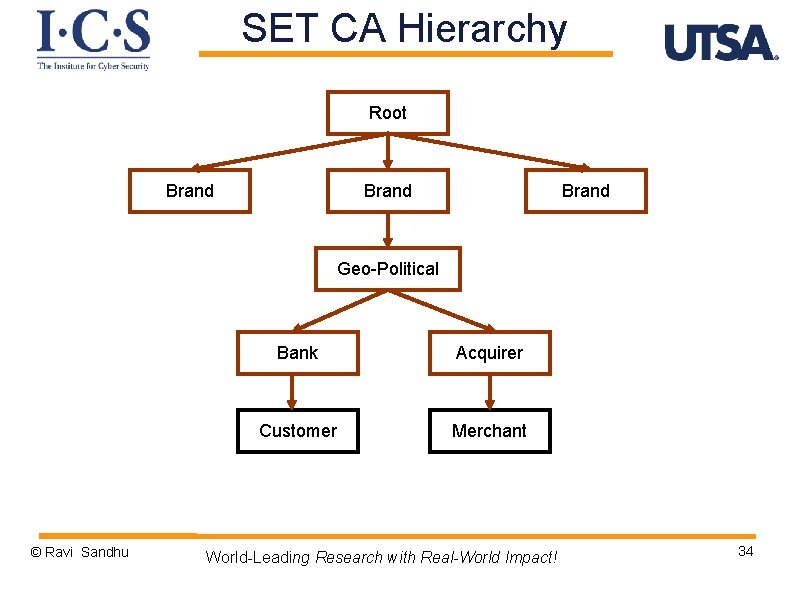
SET CA Hierarchy Root Brand Geo-Political © Ravi Sandhu Bank Acquirer Customer Merchant World-Leading Research with Real-World Impact! 34

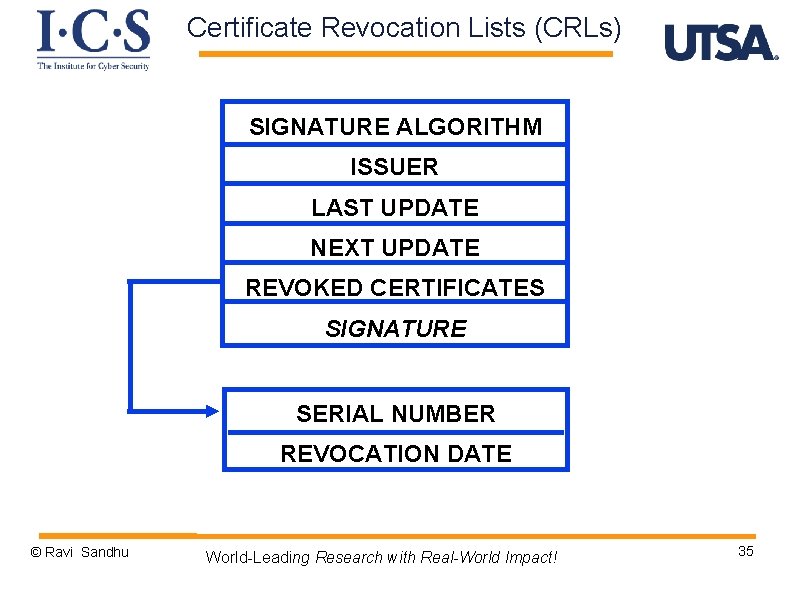
Certificate Revocation Lists (CRLs) SIGNATURE ALGORITHM ISSUER LAST UPDATE NEXT UPDATE REVOKED CERTIFICATES SIGNATURE SERIAL NUMBER REVOCATION DATE © Ravi Sandhu World-Leading Research with Real-World Impact! 35

X. 509 Certificates Ø X. 509 v 1 v very basic Ø X. 509 v 2 v adds unique identifiers to prevent against reuse of X. 500 names Ø X. 509 v 3 v adds many extensions v can be further extended © Ravi Sandhu World-Leading Research with Real-World Impact! 36

X. 509 v 3 Innovations Ø distinguish various certificates v signature, encryption, key-agreement Ø identification info in addition to X. 500 name v internet names: email addresses, host names, URLs Ø issuer can state policy and usage v ok for casual email but not for signing checks Ø extensible v proprietary extensions can be defined and registered Ø attribute certificates v to enable attribute-based authorization © Ravi Sandhu World-Leading Research with Real-World Impact! 37

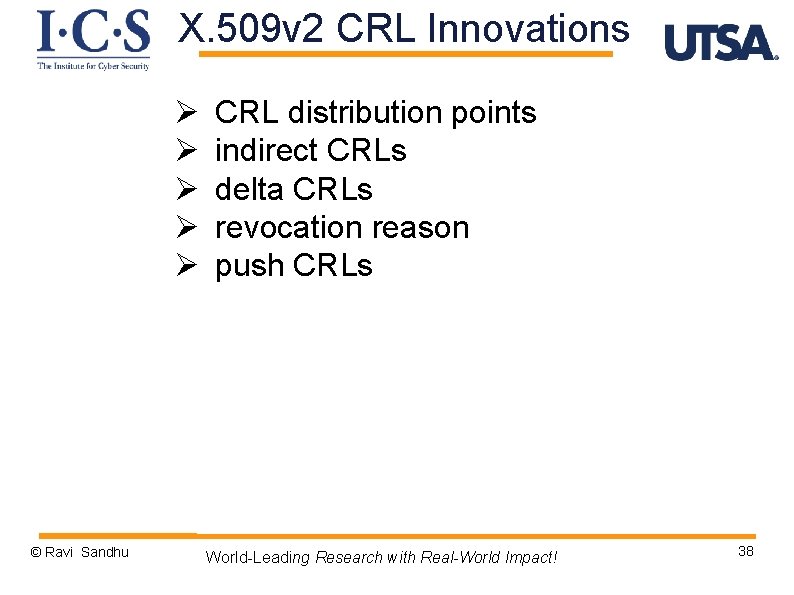
X. 509 v 2 CRL Innovations Ø Ø Ø © Ravi Sandhu CRL distribution points indirect CRLs delta CRLs revocation reason push CRLs World-Leading Research with Real-World Impact! 38

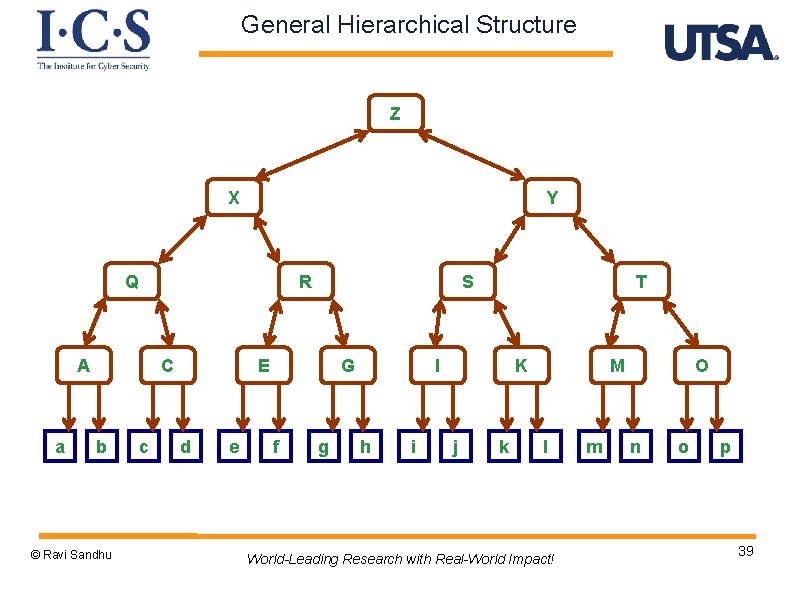
General Hierarchical Structure Z X Y Q R A a C b © Ravi Sandhu c S E d e G f g T I h i K j k M l World-Leading Research with Real-World Impact! m O n o p 39

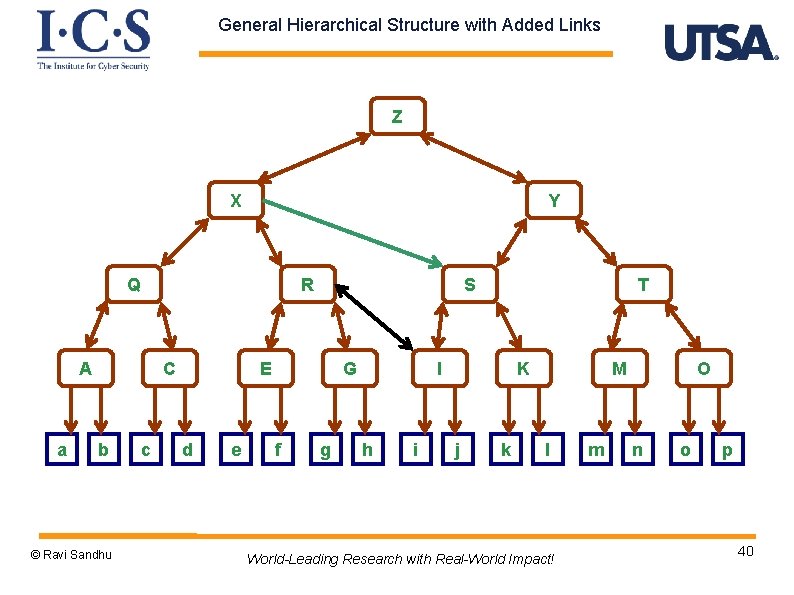
General Hierarchical Structure with Added Links Z X Y Q R A a C b © Ravi Sandhu c S E d e G f g T I h i K j k M l World-Leading Research with Real-World Impact! m O n o p 40

Top-Down Hierarchical Structure Z X Y Q R A a C b © Ravi Sandhu c S E d e G f g T I h i K j k M l World-Leading Research with Real-World Impact! m O n o p 41

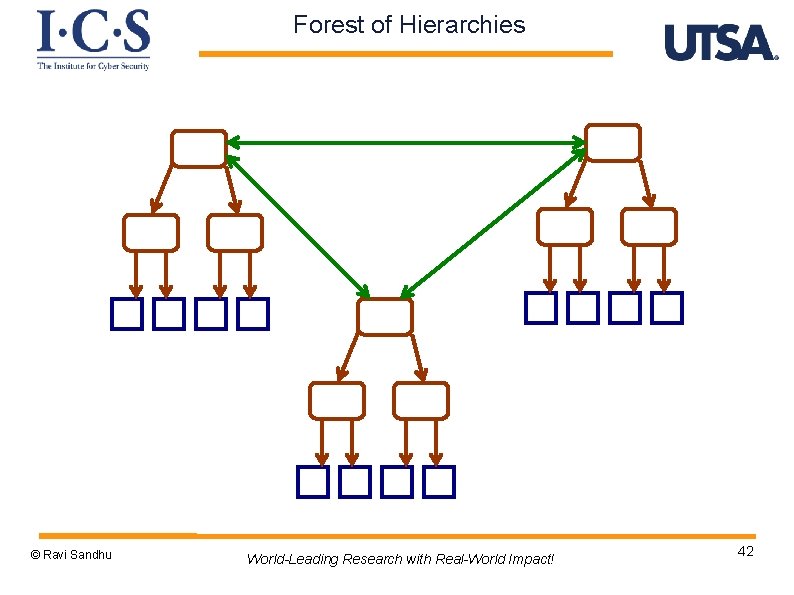
Forest of Hierarchies © Ravi Sandhu World-Leading Research with Real-World Impact! 42

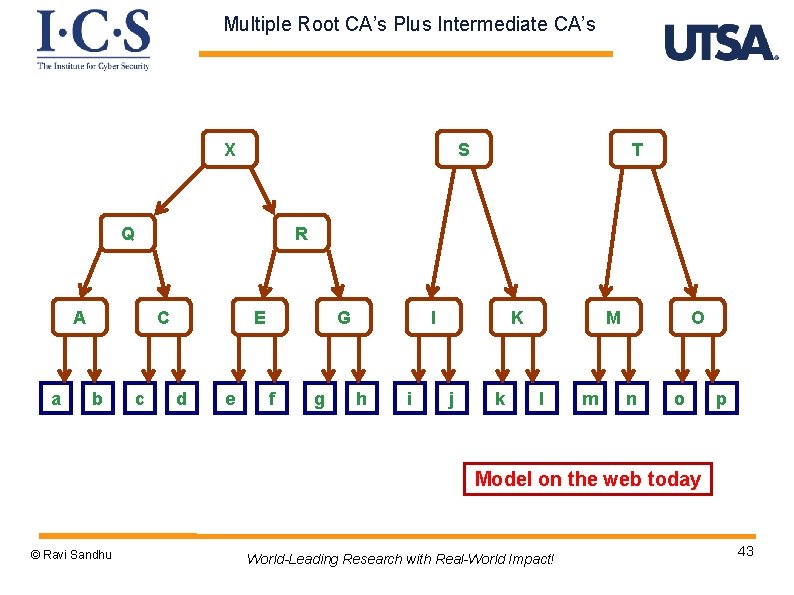
Multiple Root CA’s Plus Intermediate CA’s X S Q R A a C b T c E d e G f g I h i K j k M l m O n o p Model on the web today © Ravi Sandhu World-Leading Research with Real-World Impact! 43

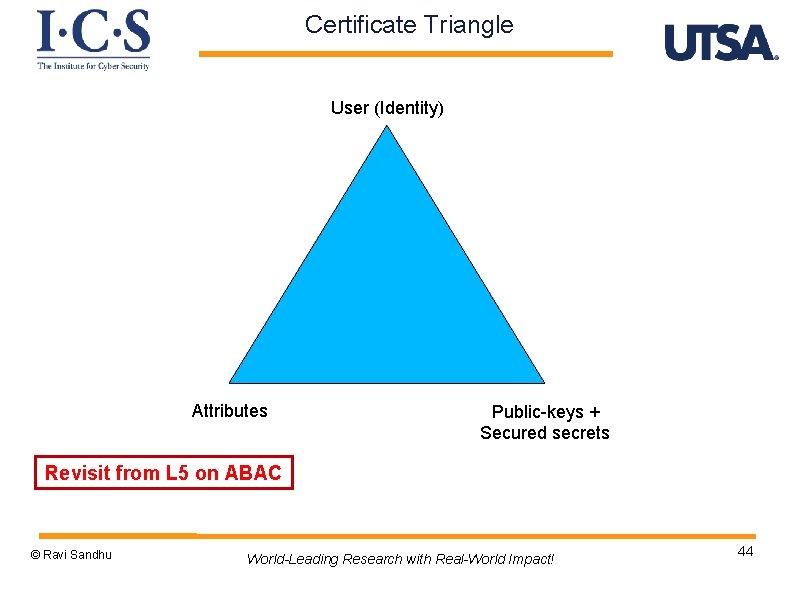
Certificate Triangle User (Identity) Attributes Public-keys + Secured secrets Revisit from L 5 on ABAC © Ravi Sandhu World-Leading Research with Real-World Impact! 44