CS 5323 SSL Secure Sockets Layer Prof Ravi


















- Slides: 56

CS 5323 SSL Secure Sockets Layer Prof. Ravi Sandhu Executive Director and Endowed Chair Lecture 6 ravi. utsa@gmail. com www. profsandhu. com © Ravi Sandhu World-Leading Research with Real-World Impact! 1

Internet Security Protocols © Ravi Sandhu World-Leading Research with Real-World Impact! 2

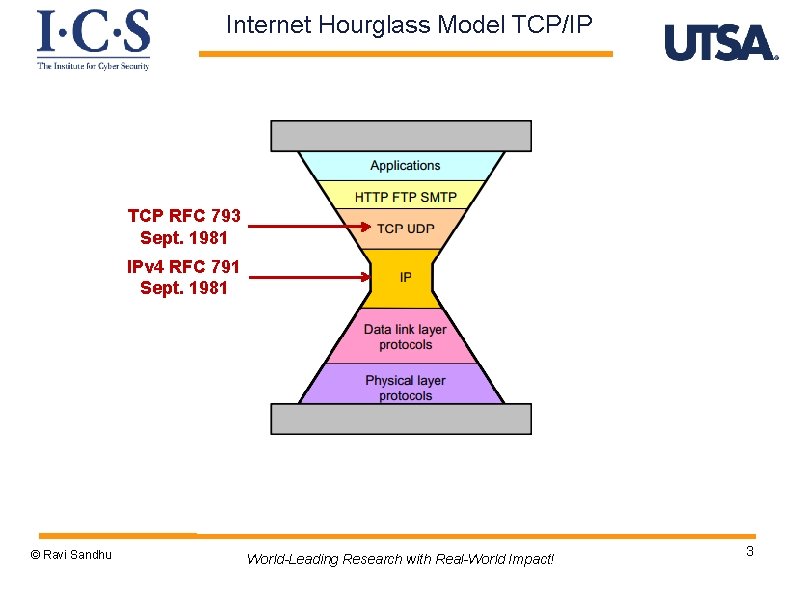
Internet Hourglass Model TCP/IP TCP RFC 793 Sept. 1981 IPv 4 RFC 791 Sept. 1981 © Ravi Sandhu World-Leading Research with Real-World Impact! 3

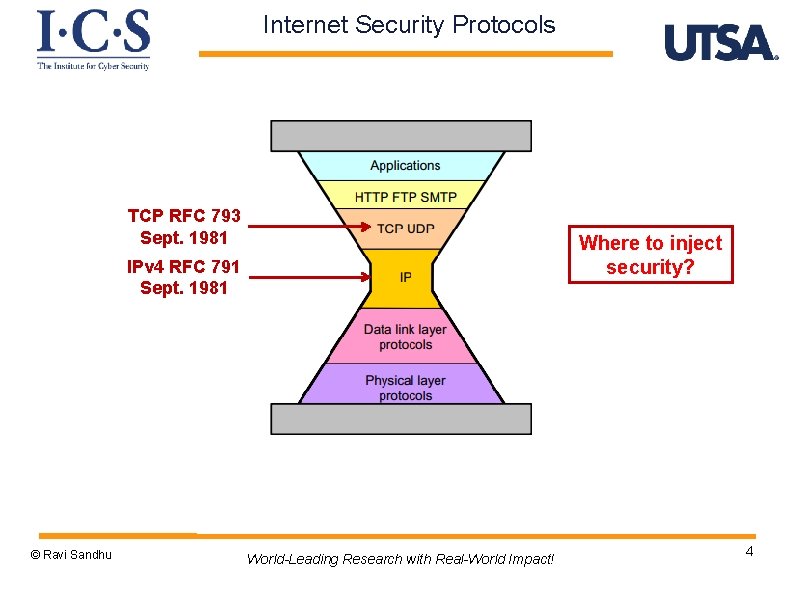
Internet Security Protocols TCP RFC 793 Sept. 1981 Where to inject security? IPv 4 RFC 791 Sept. 1981 © Ravi Sandhu World-Leading Research with Real-World Impact! 4

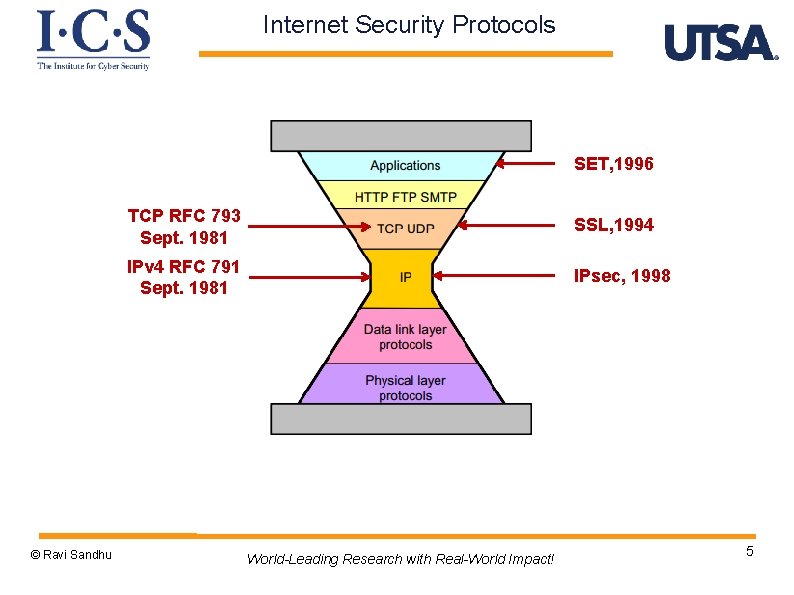
Internet Security Protocols SET, 1996 © Ravi Sandhu TCP RFC 793 Sept. 1981 SSL, 1994 IPv 4 RFC 791 Sept. 1981 IPsec, 1998 World-Leading Research with Real-World Impact! 5

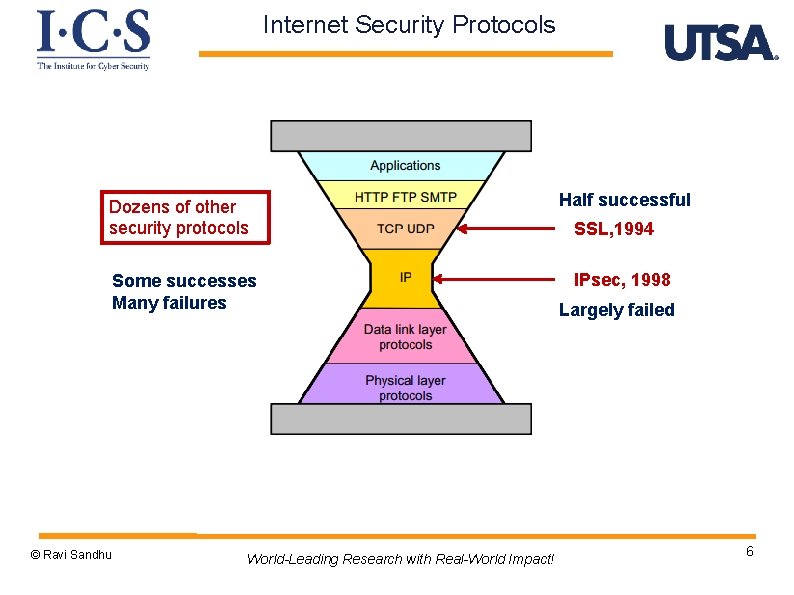
Internet Security Protocols Dozens of other security protocols Some successes Many failures © Ravi Sandhu World-Leading Research with Real-World Impact! Half successful SSL, 1994 IPsec, 1998 Largely failed 6

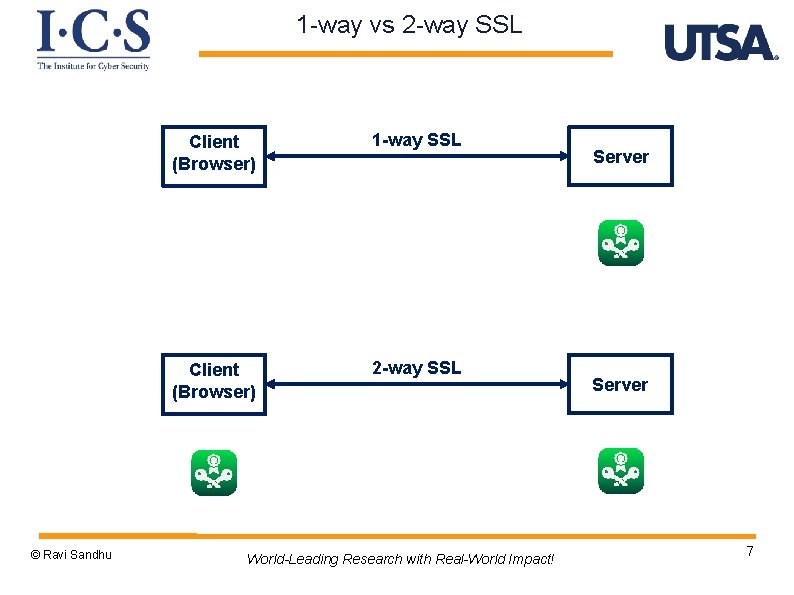
1 -way vs 2 -way SSL © Ravi Sandhu Client (Browser) 1 -way SSL Client (Browser) 2 -way SSL World-Leading Research with Real-World Impact! Server 7

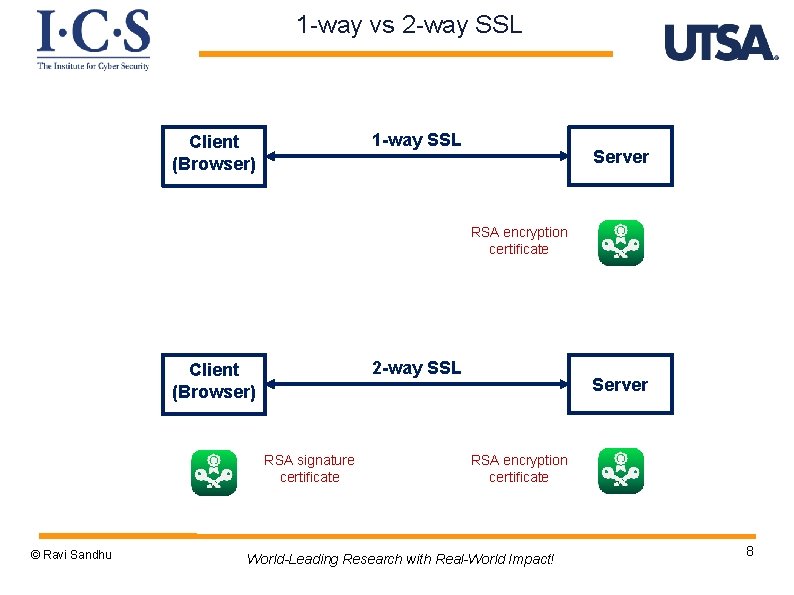
1 -way vs 2 -way SSL 1 -way SSL Client (Browser) Server RSA encryption certificate 2 -way SSL Client (Browser) RSA signature certificate © Ravi Sandhu Server RSA encryption certificate World-Leading Research with Real-World Impact! 8

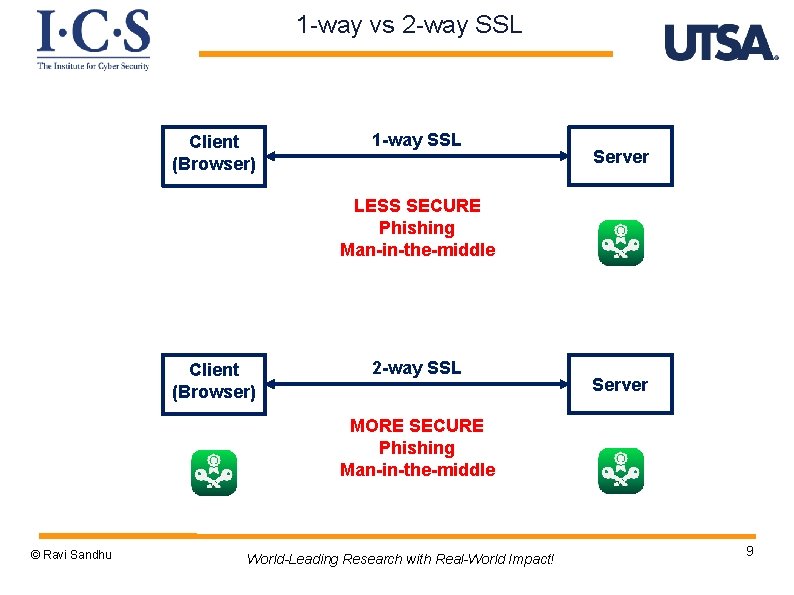
1 -way vs 2 -way SSL Client (Browser) 1 -way SSL Server LESS SECURE Phishing Man-in-the-middle Client (Browser) 2 -way SSL Server MORE SECURE Phishing Man-in-the-middle © Ravi Sandhu World-Leading Research with Real-World Impact! 9

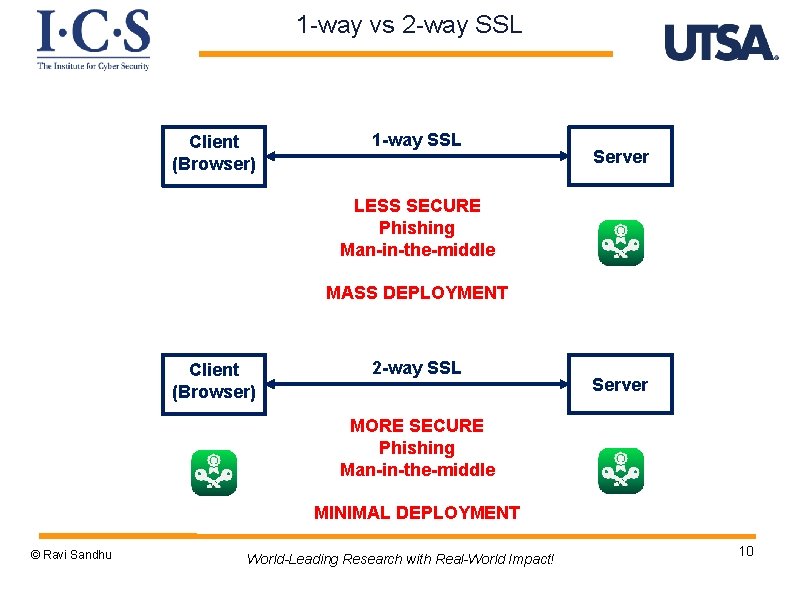
1 -way vs 2 -way SSL Client (Browser) 1 -way SSL Server LESS SECURE Phishing Man-in-the-middle MASS DEPLOYMENT Client (Browser) 2 -way SSL Server MORE SECURE Phishing Man-in-the-middle MINIMAL DEPLOYMENT © Ravi Sandhu World-Leading Research with Real-World Impact! 10

The SSL Lesson Ø Client-less trumps client-full Ø Start-ups (SSL) trump committees (IPSEC) © Ravi Sandhu World-Leading Research with Real-World Impact! 11

SSL Details © Ravi Sandhu World-Leading Research with Real-World Impact! 12

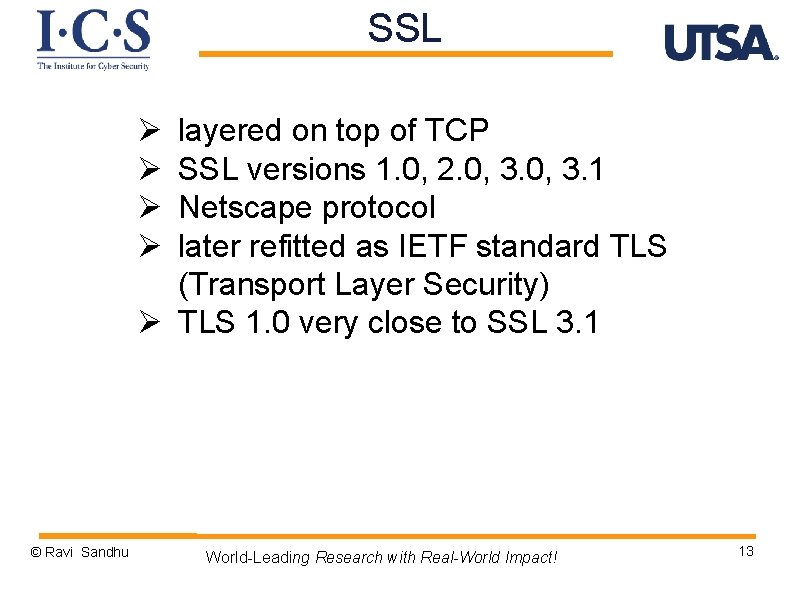
SSL Ø Ø layered on top of TCP SSL versions 1. 0, 2. 0, 3. 1 Netscape protocol later refitted as IETF standard TLS (Transport Layer Security) Ø TLS 1. 0 very close to SSL 3. 1 © Ravi Sandhu World-Leading Research with Real-World Impact! 13

SSL Ø application protocol independent Ø does not specify how application protocols add security with SSL v how to initiate SSL handshaking v how to interpret certificates Ø left to designers of upper layer protocols to figure out © Ravi Sandhu World-Leading Research with Real-World Impact! 14

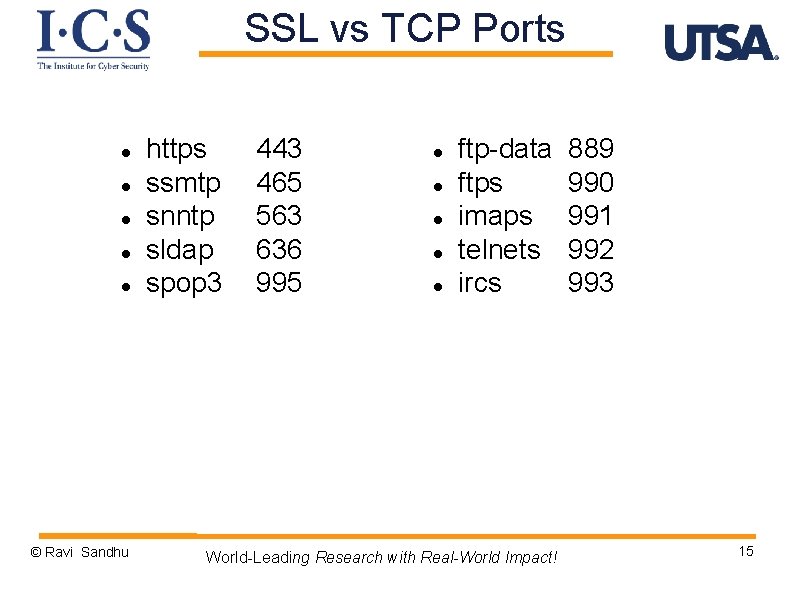
SSL vs TCP Ports © Ravi Sandhu https ssmtp snntp sldap spop 3 443 465 563 636 995 ftp-data ftps imaps telnets ircs World-Leading Research with Real-World Impact! 889 990 991 992 993 15

SSL Services Ø Ø Ø peer entity authentication data confidentiality data authentication and integrity compression/decompression generation/distribution of session keys v integrated into protocol Ø security parameter negotiation © Ravi Sandhu World-Leading Research with Real-World Impact! 16

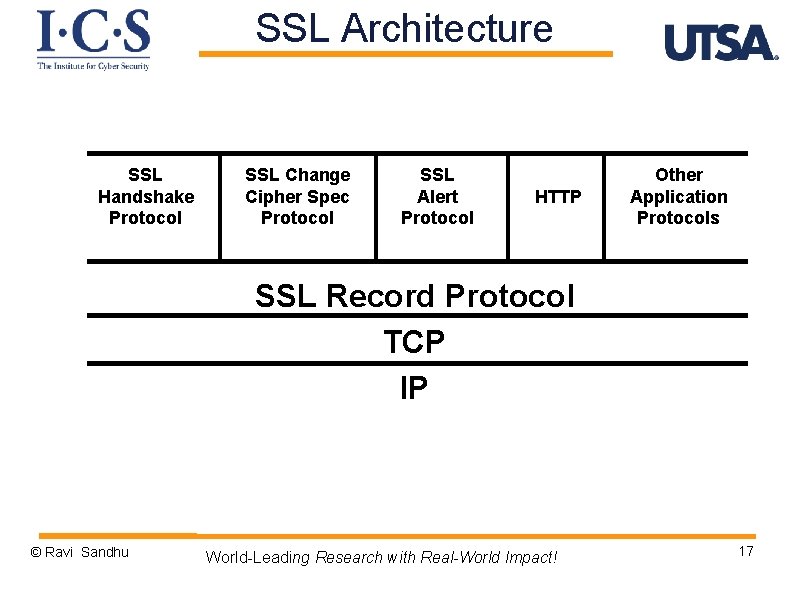
SSL Architecture SSL Handshake Protocol SSL Change Cipher Spec Protocol SSL Alert Protocol HTTP Other Application Protocols SSL Record Protocol TCP IP © Ravi Sandhu World-Leading Research with Real-World Impact! 17

SSL Architecture Ø Handshake protocol: complicated v embodies key exchange & authentication v runs in plaintext v 10 message types Ø Change Cipher Spec protocol: straightforward v single 1 byte message with value 1 v could be considered part of handshake protocol v transitions from plaintext to encrypted and mac’ed Ø Record protocol: straightforward v fragment, compress, MAC, encrypt v uses 4 symmetric keys Ø Alert protocol: straightforward v 2 byte messages v 1 byte alert level- fatal or warning; 1 byte alert code © Ravi Sandhu World-Leading Research with Real-World Impact! 18

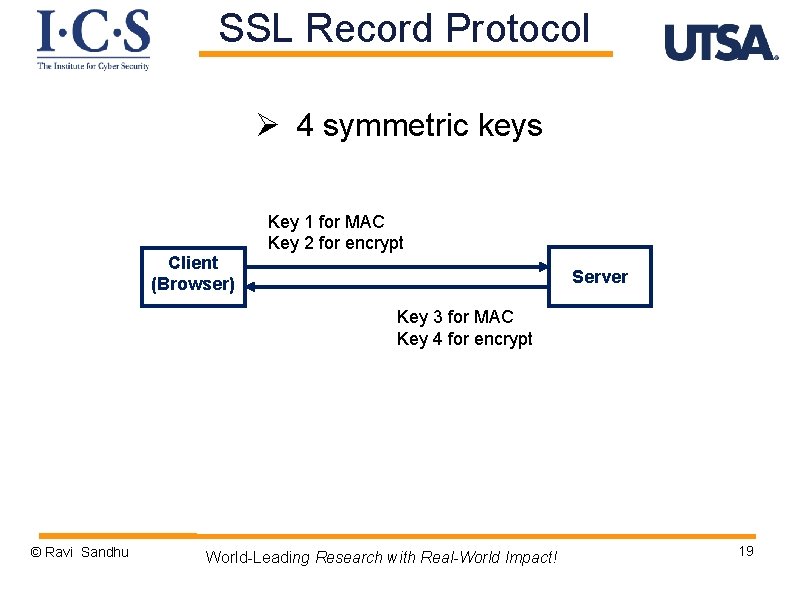
SSL Record Protocol Ø 4 symmetric keys Client (Browser) Key 1 for MAC Key 2 for encrypt Server Key 3 for MAC Key 4 for encrypt © Ravi Sandhu World-Leading Research with Real-World Impact! 19

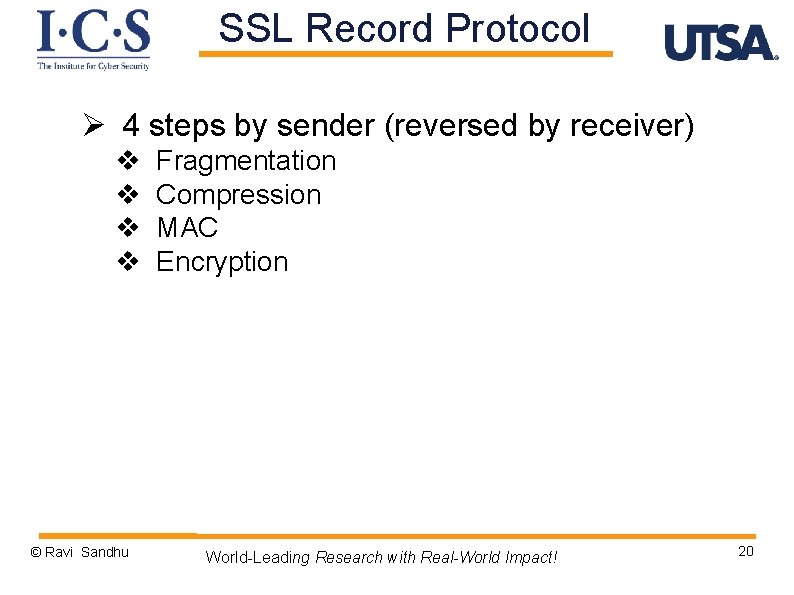
SSL Record Protocol Ø 4 steps by sender (reversed by receiver) v v © Ravi Sandhu Fragmentation Compression MAC Encryption World-Leading Research with Real-World Impact! 20

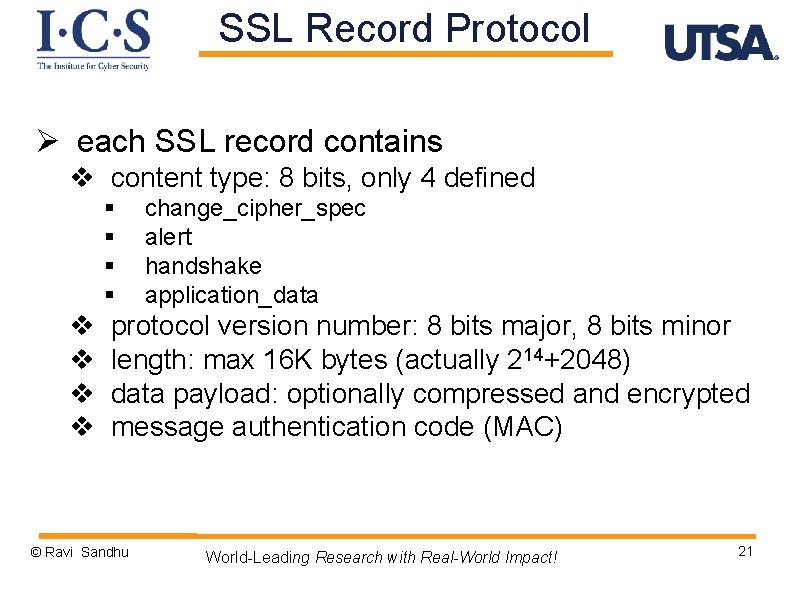
SSL Record Protocol Ø each SSL record contains v content type: 8 bits, only 4 defined § § v v change_cipher_spec alert handshake application_data protocol version number: 8 bits major, 8 bits minor length: max 16 K bytes (actually 214+2048) data payload: optionally compressed and encrypted message authentication code (MAC) © Ravi Sandhu World-Leading Research with Real-World Impact! 21

SSL Handshake Protocol Ø initially SSL session has null compression and cipher algorithms Ø both are set by the handshake protocol at beginning of session Ø handshake protocol may be repeated during the session © Ravi Sandhu World-Leading Research with Real-World Impact! 22

SSL Session Ø SSL session negotiated by handshake protocol v session ID § chosen by server v X. 509 public-key certificate of peer § possibly null v compression algorithm v cipher spec § § encryption algorithm message digest algorithm v master secret § 48 byte shared secret v is resumable flag § § © Ravi Sandhu can be used to initiate new connections each session is created with one connection, but additional connections within the session can be further created World-Leading Research with Real-World Impact! 23

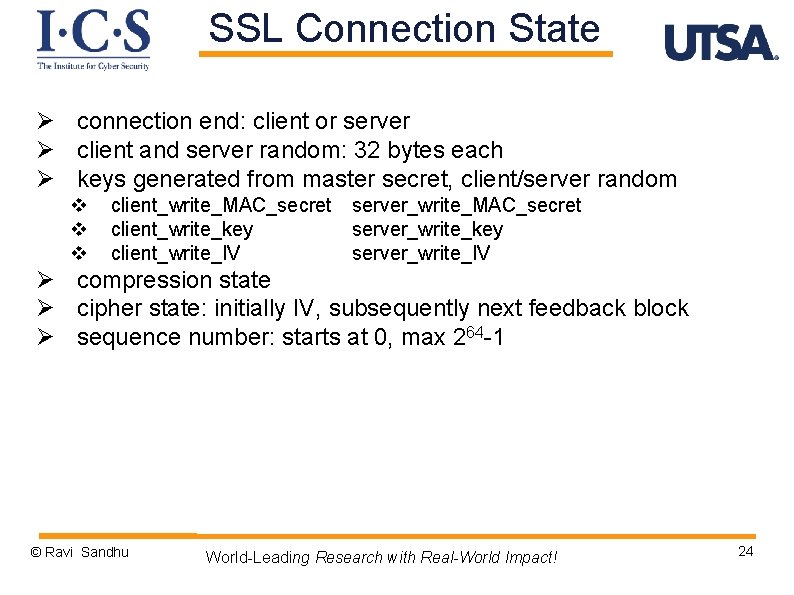
SSL Connection State Ø connection end: client or server Ø client and server random: 32 bytes each Ø keys generated from master secret, client/server random v v v client_write_MAC_secret server_write_MAC_secret client_write_key server_write_key client_write_IV server_write_IV Ø compression state Ø cipher state: initially IV, subsequently next feedback block Ø sequence number: starts at 0, max 264 -1 © Ravi Sandhu World-Leading Research with Real-World Impact! 24

SSL Connection State Ø 4 parts to state v v current read state current write state pending read state pending write state Ø handshake protocol v v initially current state is empty either pending state can be made current and reinitialized to empty © Ravi Sandhu World-Leading Research with Real-World Impact! 25

SSL Handshake Protocol Ø Type: 1 byte v 10 message types defined Ø length: 3 bytes Ø content © Ravi Sandhu World-Leading Research with Real-World Impact! 26

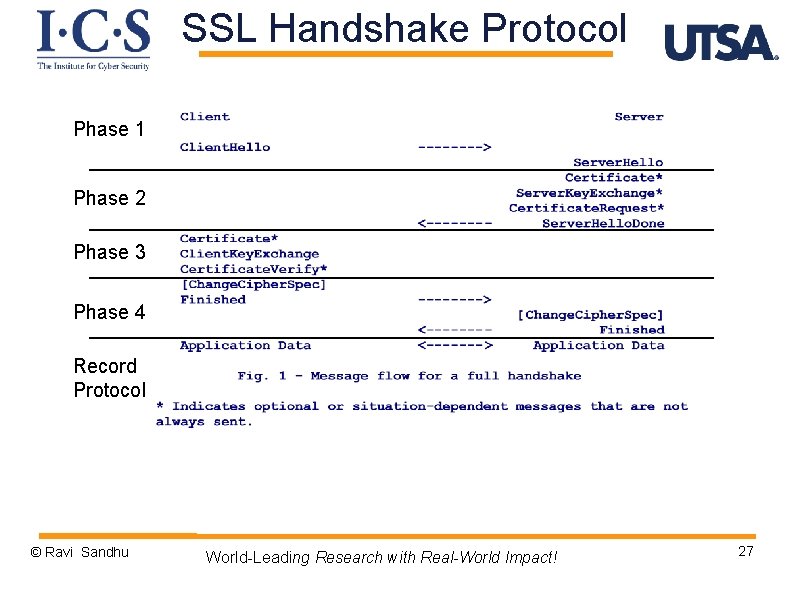
SSL Handshake Protocol Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 27

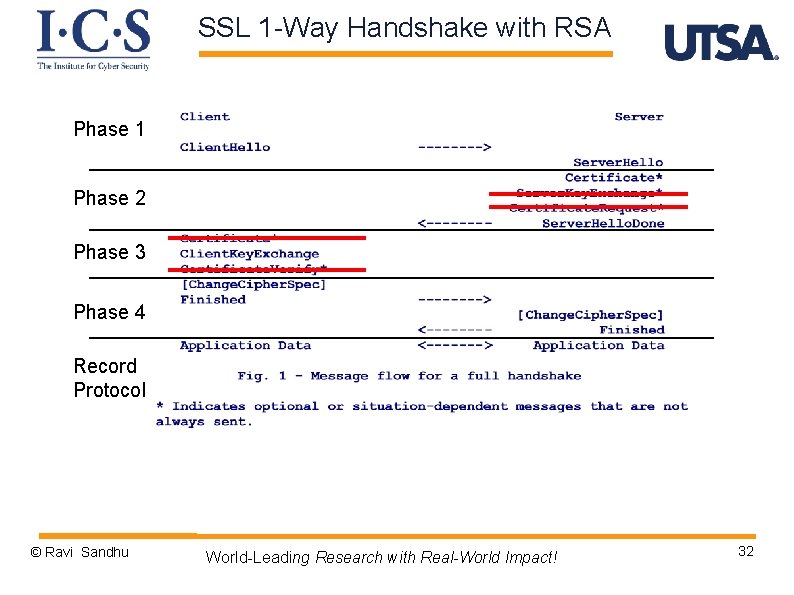
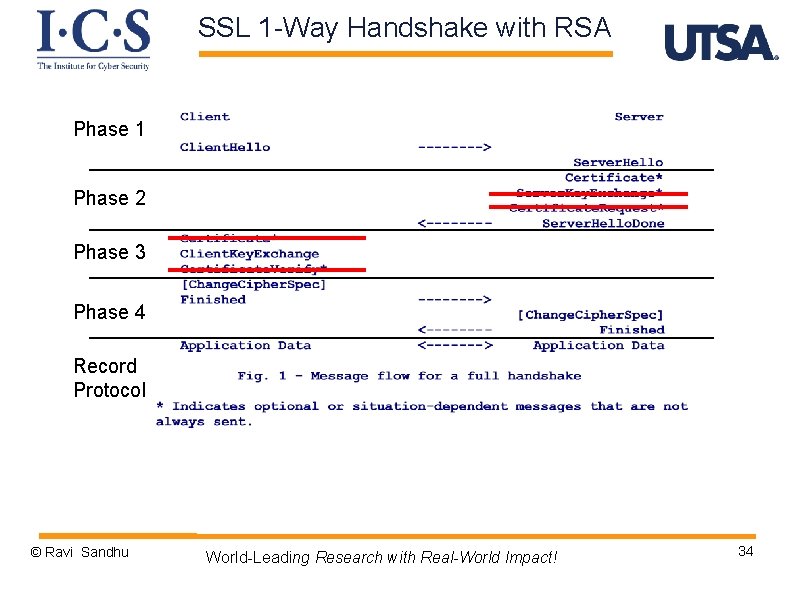
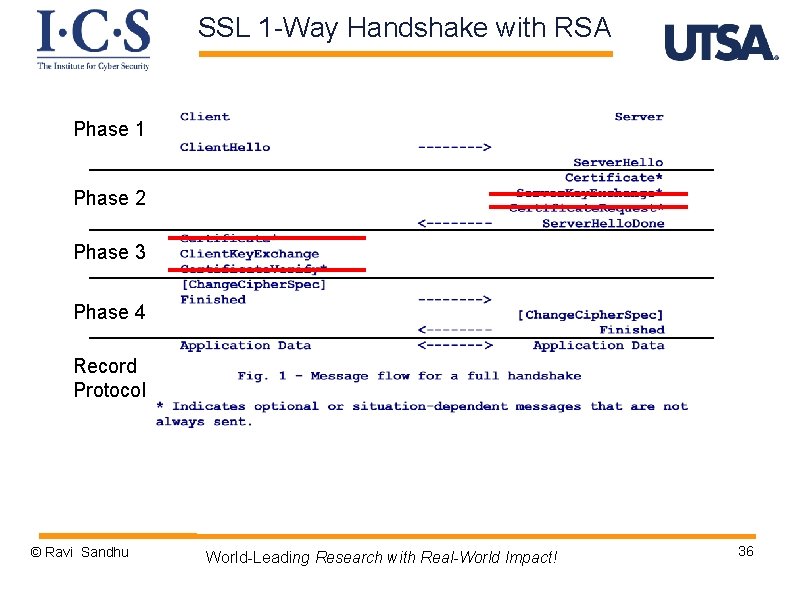
SSL Handshake Protocol Ø Phase 1: v Establish security capabilities Ø Phase 2: v Server authentication and key exchange Ø Phase 3: v Client authentication and key exchange Ø Phase 4: v Finish © Ravi Sandhu World-Leading Research with Real-World Impact! 28

SSL Handshake Protocol Ø these handshake messages must occur in order Ø optional messages can be eliminated Ø 10 th message v hello_request v can be sent anytime from server to client to request client to start handshake protocol to renegotiate session Ø change_cipher_spec is a separate 1 message protocol v functionally just like a message in the handshake protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 29

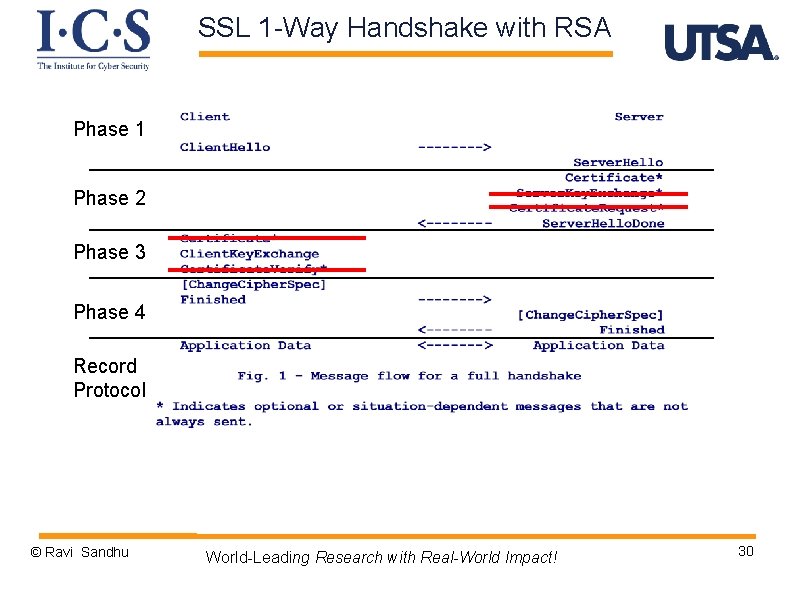
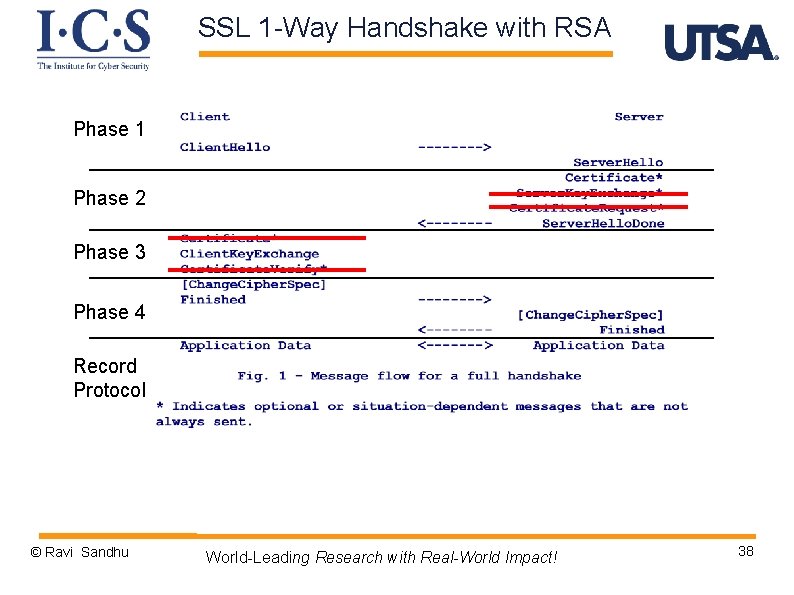
SSL 1 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 30

SSL Handshake Phase 1 Ø Ø Establish security capabilities client hello message v v 4 byte timestamp, 28 byte random value session ID: § § v v client version: highest version cipher_suite list: ordered list § v Ø non-zero for new connection on existing session zero for new connection on new session key exchange method, encryption method, MAC method compression list: ordered list server hello message v v 32 byte random value session ID: § v version § v v new or reuse lower of client suggested and highest supported cipher_suite list: single choice compression list: single choice © Ravi Sandhu World-Leading Research with Real-World Impact! 31

SSL 1 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 32

SSL RSA 1 -way Handshake Phase 2 Ø Server authentication and key exchange Ø certificate message v server’s X. 509 v 3 certificate followed by optional chain of certificates v required for RSA Ø server done message v ends phase 2, always required © Ravi Sandhu World-Leading Research with Real-World Impact! 33

SSL 1 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 34

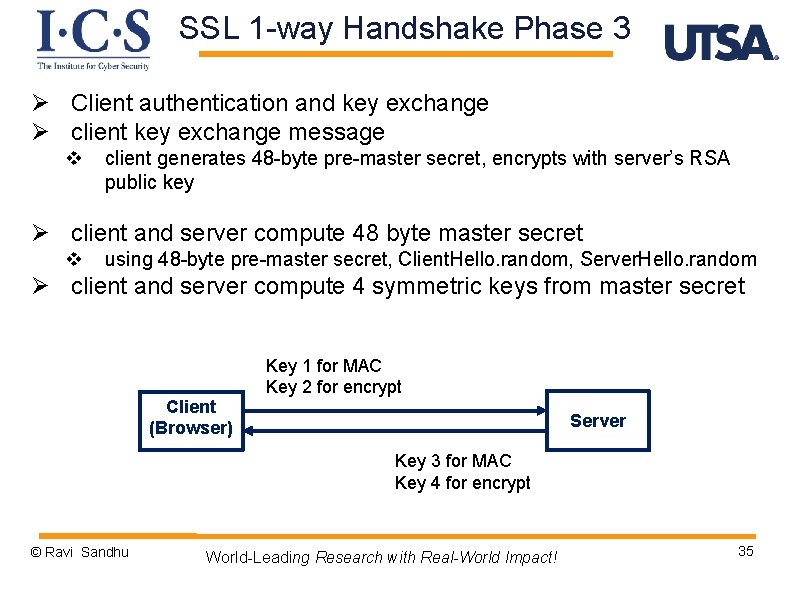
SSL 1 -way Handshake Phase 3 Ø Client authentication and key exchange Ø client key exchange message v client generates 48 -byte pre-master secret, encrypts with server’s RSA public key Ø client and server compute 48 byte master secret v using 48 -byte pre-master secret, Client. Hello. random, Server. Hello. random Ø client and server compute 4 symmetric keys from master secret Client (Browser) Key 1 for MAC Key 2 for encrypt Server Key 3 for MAC Key 4 for encrypt © Ravi Sandhu World-Leading Research with Real-World Impact! 35

SSL 1 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 36

SSL 1 -way RSA Handshake Phase 4 Ø Finish and move to record protocol Ø change cipher spec message v not considered part of handshake protocol but in some sense is part of it v 1 byte message protected by current state v copies pending state to current state Ø Finished message v sent under new algorithms and keys v content is MAC of all previous messages with master secret and constant “client finished” or “server finished” © Ravi Sandhu World-Leading Research with Real-World Impact! 37

SSL 1 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 38

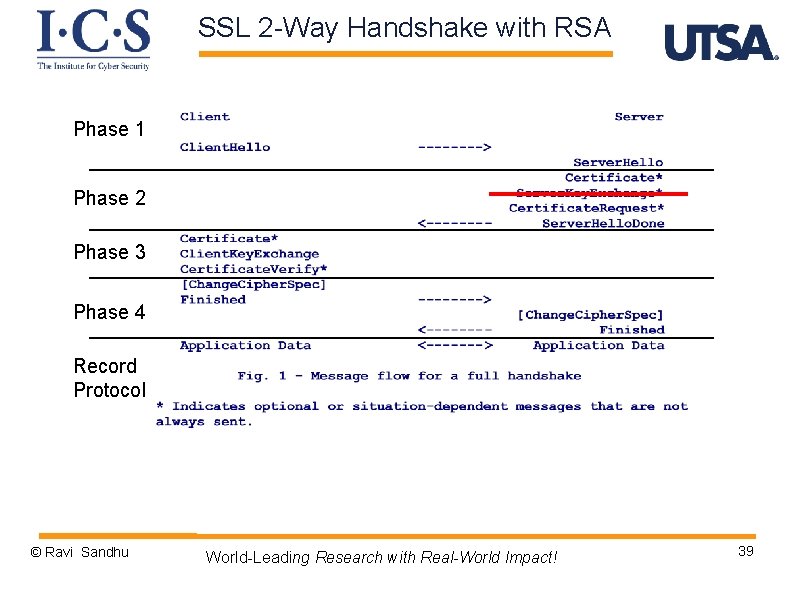
SSL 2 -Way Handshake with RSA Phase 1 Phase 2 Phase 3 Phase 4 Record Protocol © Ravi Sandhu World-Leading Research with Real-World Impact! 39

SSL RSA 2 -way Handshake Phase 2 Ø Server authentication and key exchange Ø certificate message v server’s X. 509 v 3 certificate followed by optional chain of certificates v required for RSA Ø certificate request message v request a certificate from client v specifies Certificate Type and Certificate Authorities Ø server done message v ends phase 2, always required © Ravi Sandhu World-Leading Research with Real-World Impact! 40

SSL 2 -way Handshake Phase 3 Ø Client authentication and key exchange Ø certificate message v client’s X. 509 v 3 certificate followed by optional chain of certificates Ø client key exchange message v client generates 48 -byte pre-master secret, encrypts with server’s RSA public key Ø certificate verify message v signs hash of master secret (established by key exchange) and all handshake messages so far Ø client and server compute 48 byte master secret v using 48 -byte pre-master secret, Client. Hello. random, Server. Hello. random Ø client and server compute 4 symmetric keys from master secret © Ravi Sandhu World-Leading Research with Real-World Impact! 41

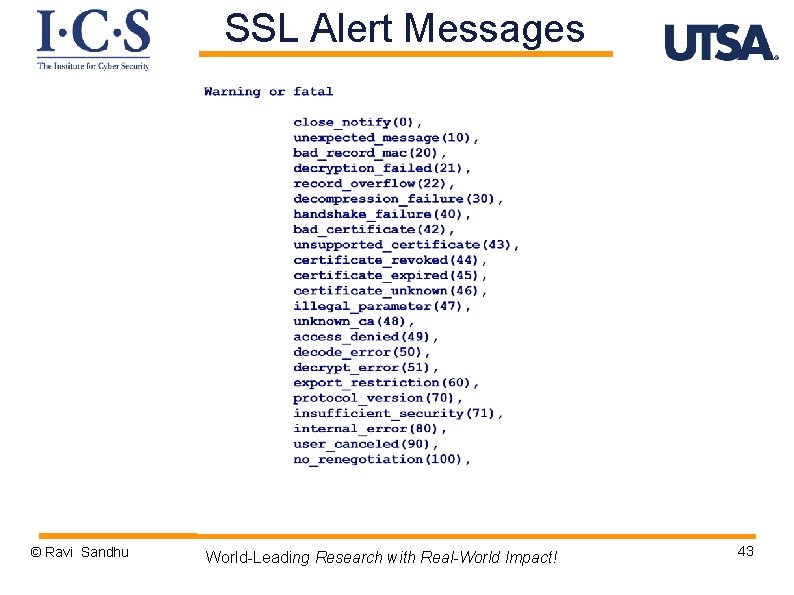
SSL Alert Protocol Ø 2 byte alert messages v 1 byte level § fatal or warning v 1 byte § alert code © Ravi Sandhu World-Leading Research with Real-World Impact! 42

SSL Alert Messages © Ravi Sandhu World-Leading Research with Real-World Impact! 43

SSL Alert Messages Ø always fatal v v v © Ravi Sandhu unexpected_message bad_record_mac decompression_failure handshake_failure illegal_parameter World-Leading Research with Real-World Impact! 44

SSL Man-in-the-Middle (MITM) Attack © Ravi Sandhu World-Leading Research with Real-World Impact! 45

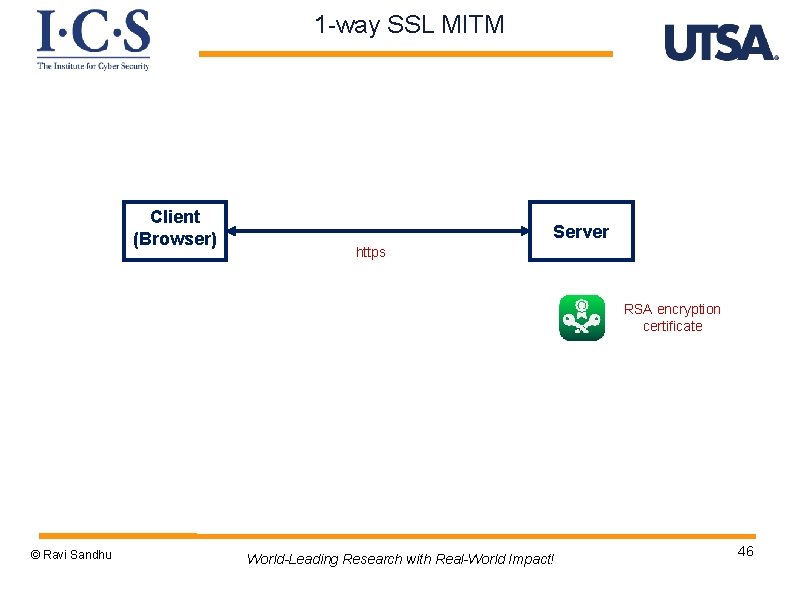
1 -way SSL MITM Client (Browser) Server https RSA encryption certificate © Ravi Sandhu World-Leading Research with Real-World Impact! 46

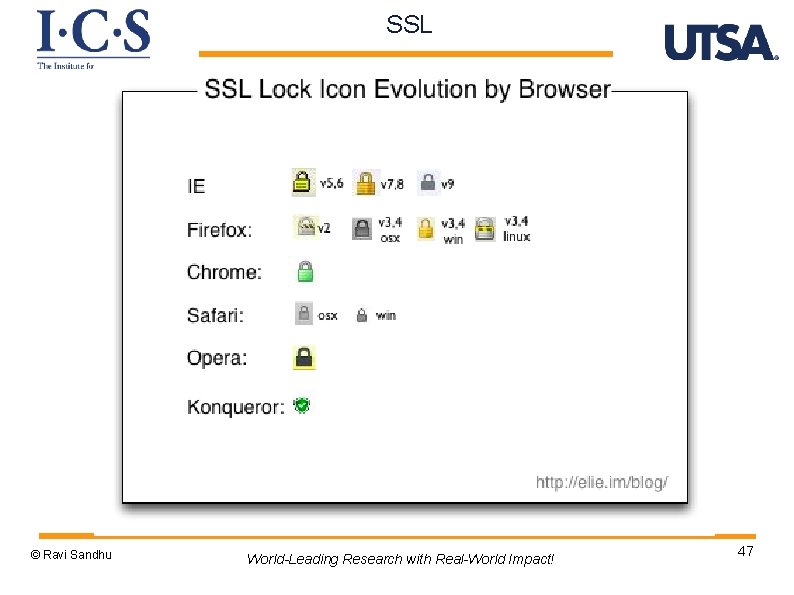
SSL © Ravi Sandhu World-Leading Research with Real-World Impact! 47

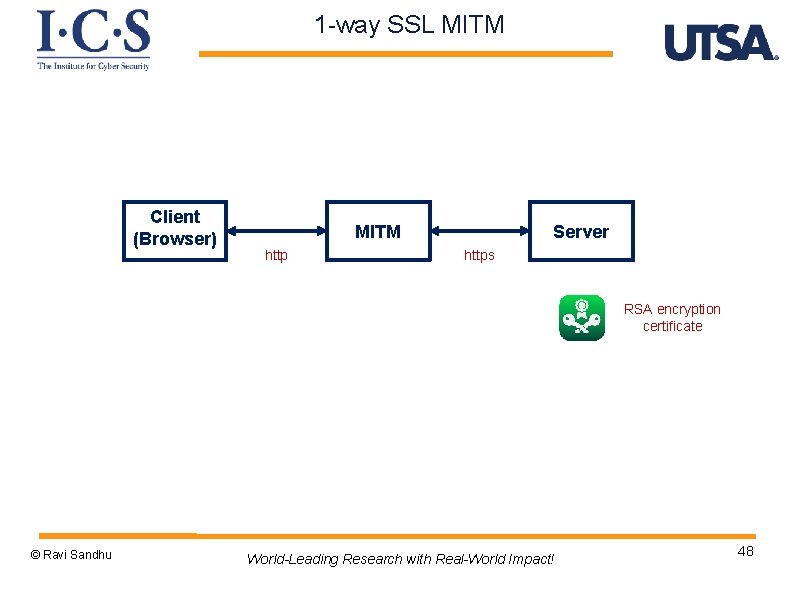
1 -way SSL MITM Client (Browser) MITM http Server https RSA encryption certificate © Ravi Sandhu World-Leading Research with Real-World Impact! 48

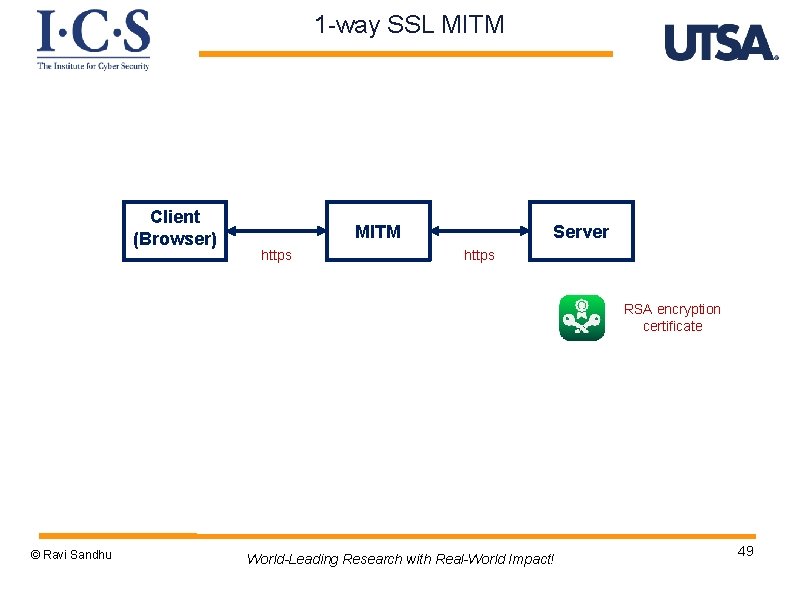
1 -way SSL MITM Client (Browser) MITM https Server https RSA encryption certificate © Ravi Sandhu World-Leading Research with Real-World Impact! 49

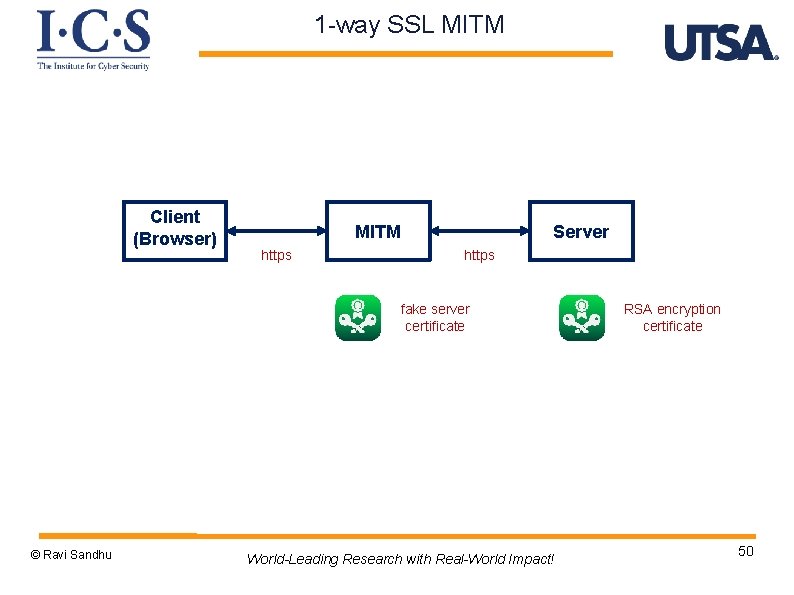
1 -way SSL MITM Client (Browser) MITM https Server https fake server certificate © Ravi Sandhu World-Leading Research with Real-World Impact! RSA encryption certificate 50

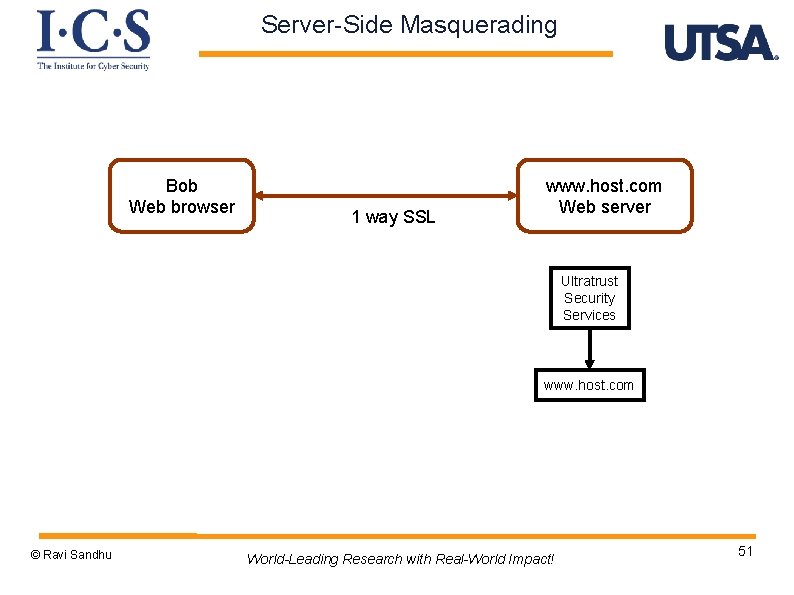
Server-Side Masquerading Bob Web browser 1 way SSL www. host. com Web server Ultratrust Security Services www. host. com © Ravi Sandhu World-Leading Research with Real-World Impact! 51

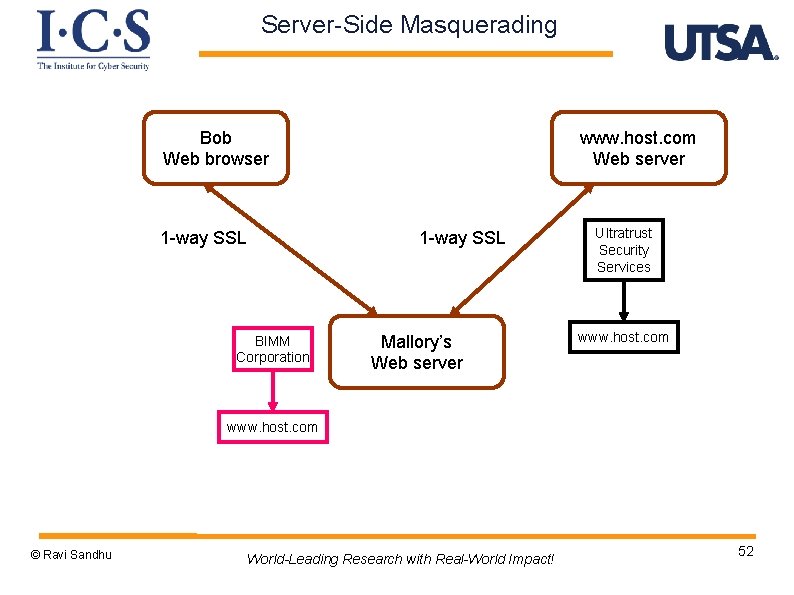
Server-Side Masquerading Bob Web browser 1 -way SSL www. host. com Web server 1 -way SSL BIMM Corporation Mallory’s Web server Ultratrust Security Services www. host. com © Ravi Sandhu World-Leading Research with Real-World Impact! 52

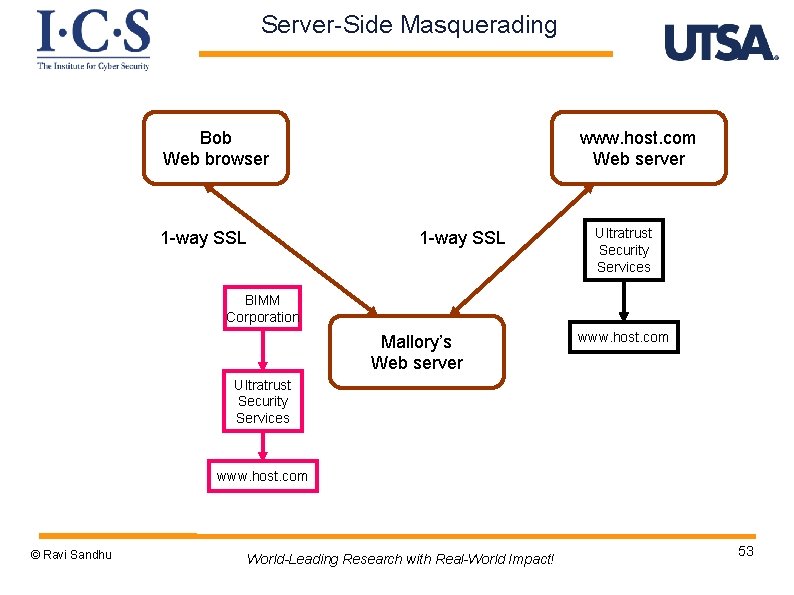
Server-Side Masquerading Bob Web browser 1 -way SSL www. host. com Web server 1 -way SSL Ultratrust Security Services BIMM Corporation Mallory’s Web server www. host. com Ultratrust Security Services www. host. com © Ravi Sandhu World-Leading Research with Real-World Impact! 53

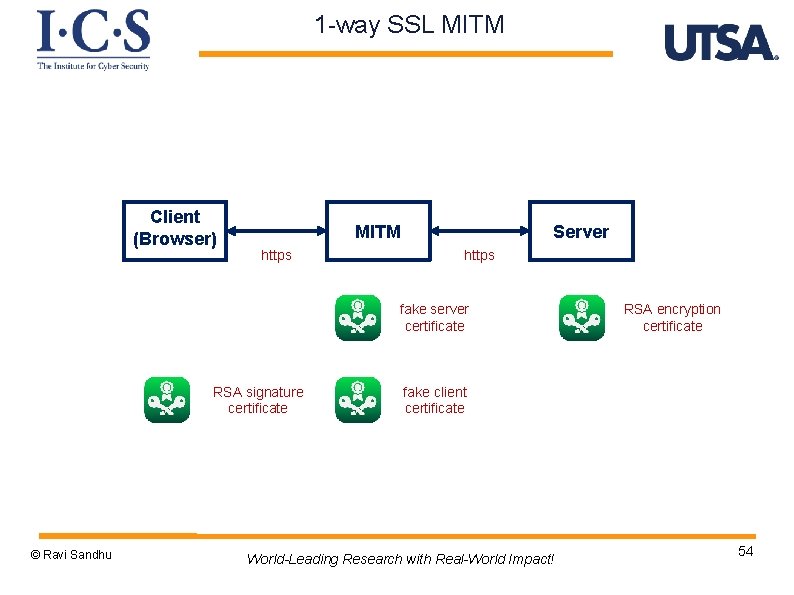
1 -way SSL MITM Client (Browser) MITM https Server https fake server certificate RSA signature certificate © Ravi Sandhu RSA encryption certificate fake client certificate World-Leading Research with Real-World Impact! 54

Open. SSL Heartbleed Attack X Not covered in lecture © Ravi Sandhu World-Leading Research with Real-World Impact! 55

Heartbeat Protocol: RFC 6520, Feb. 2012 X Not covered in lecture © Ravi Sandhu World-Leading Research with Real-World Impact! 56