Cryptography in The Presence of Continuous SideChannel Attacks

![Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks” Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks”](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-7.jpg)
![Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks” Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks”](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-8.jpg)
![Resilience To Continuous Leakage • • • [G 87, GO 96] oblivious RAMs [ISW Resilience To Continuous Leakage • • • [G 87, GO 96] oblivious RAMs [ISW](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-9.jpg)
![Key Proxies [JRV 10]: “Key Proxy”, a new primitive to immunize a cryptographic key Key Proxies [JRV 10]: “Key Proxy”, a new primitive to immunize a cryptographic key](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-10.jpg)
- Slides: 34

Cryptography in The Presence of Continuous Side-Channel Attacks Ali Juma Yevgeniy Vahlis University of Toronto Columbia University

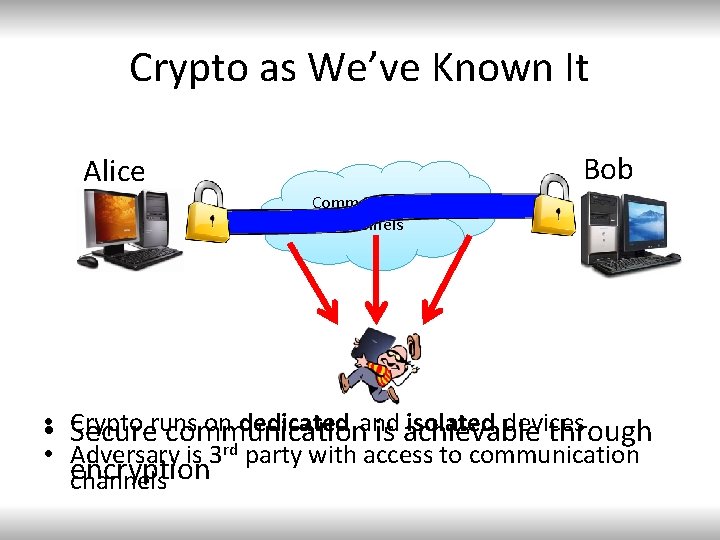
Crypto as We’ve Known It Bob Alice Communication Channels • • Crypto on dedicated and isolated devices Secureruns communication is achievable through rd • Adversary is 3 party with access to communication encryption channels

New Computing Environments Mobile Computing Cloud Computing

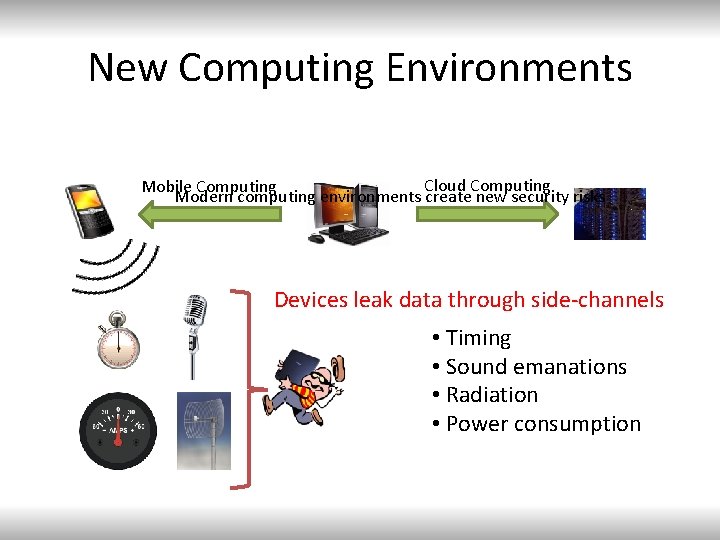
New Computing Environments Cloud Computing Mobile Computing Modern computing environments create new security risks Devices leak data through side-channels • Timing • Sound emanations • Radiation • Power consumption

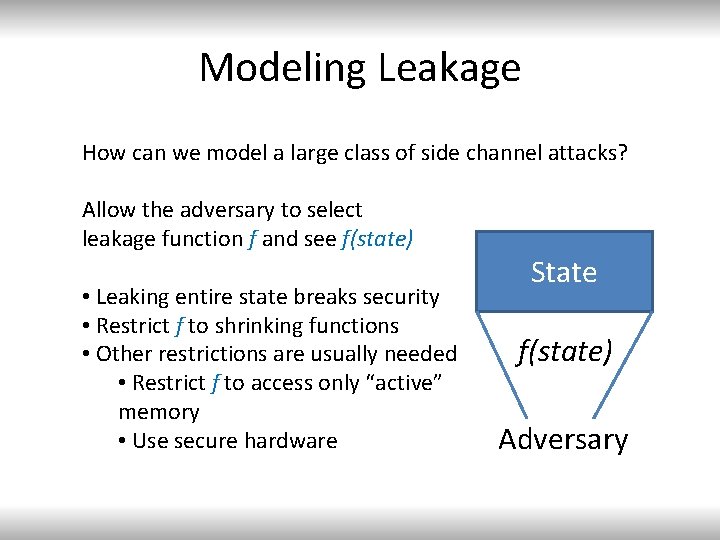
Modeling Leakage How can we model a large class of side channel attacks? Allow the adversary to select leakage function f and see f(state) • Leaking entire state breaks security • Restrict f to shrinking functions • Other restrictions are usually needed • Restrict f to access only “active” memory • Use secure hardware State f(state) Adversary

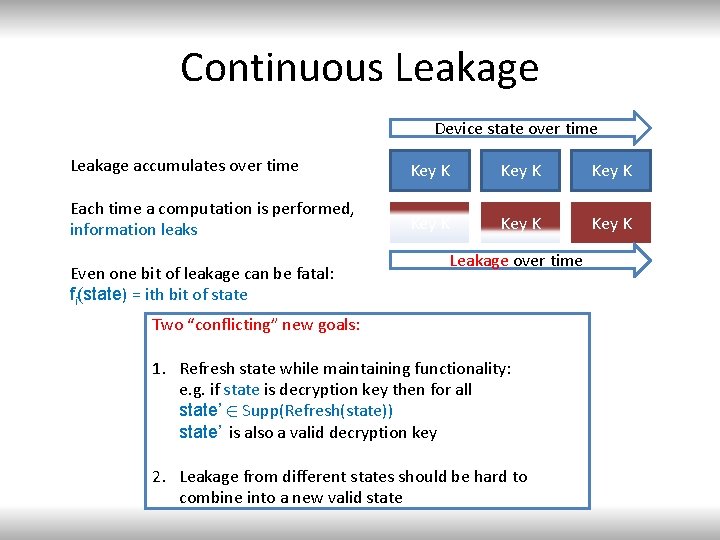
Continuous Leakage Device state over time Leakage accumulates over time Key K Each time a computation is performed, information leaks Key K Even one bit of leakage can be fatal: fi(state) = ith bit of state Leakage over time Two “conflicting” new goals: 1. Refresh state while maintaining functionality: e. g. if state is decryption key then for all state’ 2 Supp(Refresh(state)) state’ is also a valid decryption key 2. Leakage from different states should be hard to combine into a new valid state
![Only Computation Leaks We already know that computation leaks MR 04 only computation leaks Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks”](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-7.jpg)
Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks” State: Leakage Active CPU Inactive
![Only Computation Leaks We already know that computation leaks MR 04 only computation leaks Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks”](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-8.jpg)
Only Computation Leaks We already know that computation leaks [MR 04]: “only computation leaks” More formally: state=(s 1, …, sn) An algorithm consists of m parts: P 1, …, Pm and sets W 1, …, Wmµ [n] Part Pi computes and leaks on {sj | j 2 Wi} and randomness ri We model secure hardware as Pi that does not leak on ri
![Resilience To Continuous Leakage G 87 GO 96 oblivious RAMs ISW Resilience To Continuous Leakage • • • [G 87, GO 96] oblivious RAMs [ISW](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-9.jpg)
Resilience To Continuous Leakage • • • [G 87, GO 96] oblivious RAMs [ISW 03] Private circuits: securing hardware against probing attacks [MR 04] Physically observable cryptography [GKR 08] One-time programs [DP 08] Leakage-resilient cryptography [FKPR 10] Leakage-resilient signatures [FRRTV 10] Protecting against computationally bounded and noisy leakage [JV 10] On protecting cryptographic keys against continual leakage [GR 10] How to play mental solitaire under continuous side-channels [BKKV 10] Cryptography resilient to continual memory leakage [DHLW 10] Cryptography against continuous memory attacks
![Key Proxies JRV 10 Key Proxy a new primitive to immunize a cryptographic key Key Proxies [JRV 10]: “Key Proxy”, a new primitive to immunize a cryptographic key](https://slidetodoc.com/presentation_image_h/a3651120b113f3736465c8709d426ff4/image-10.jpg)
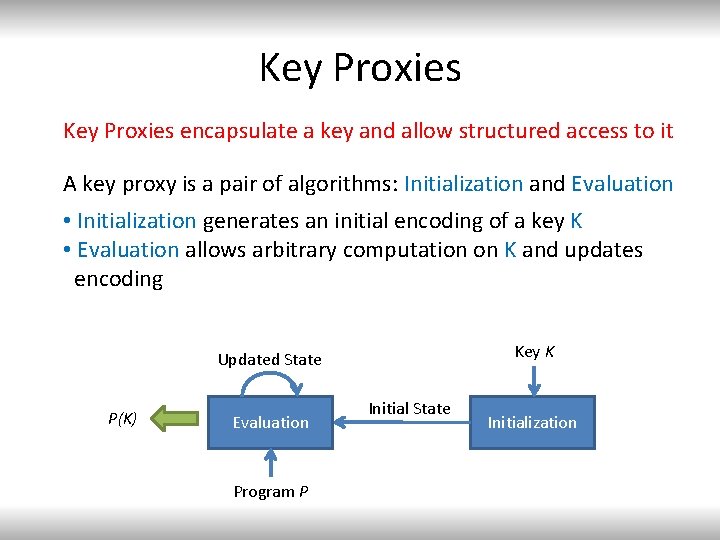
Key Proxies [JRV 10]: “Key Proxy”, a new primitive to immunize a cryptographic key against leakage, but allow arbitrary computation Building blocks: Resilience to polytime leakage without any leak • Fully homomorphic encryption free computation on the state • Secure hardware component independent from K Properties: 1. Resilience to polynomial time leakage assuming that “only computation leaks” 2. 2 l(n) secure encryption allows l(n) leakage

Key Proxies encapsulate a key and allow structured access to it A key proxy is a pair of algorithms: Initialization and Evaluation • Initialization generates an initial encoding of a key K • Evaluation allows arbitrary computation on K and updates encoding Key K Updated State P(K) Evaluation Program P Initial State Initialization

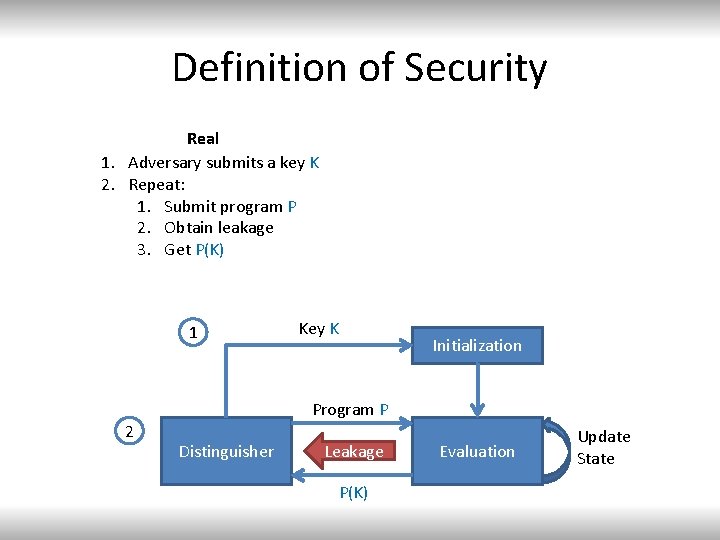
Definition of Security Real 1. Adversary submits a key K 2. Repeat: 1. Submit program P 2. Obtain leakage 3. Get P(K) 1 2 Key K Initialization Program P Distinguisher Leakage P(K) Evaluation Update State

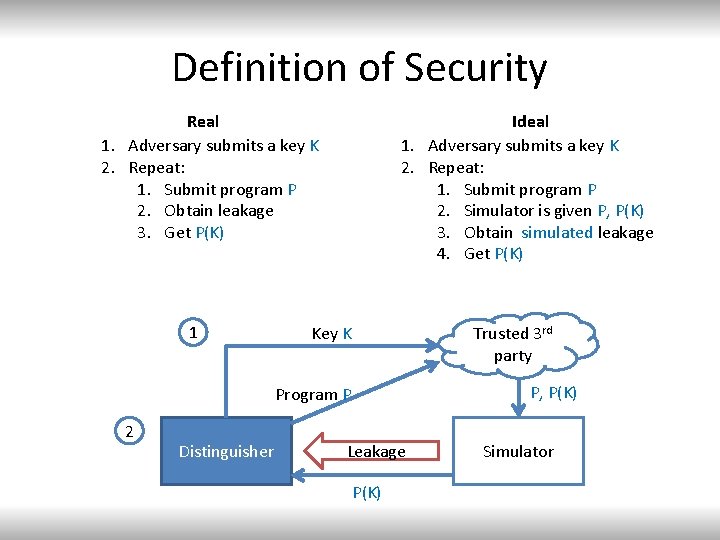
Definition of Security Real 1. Adversary submits a key K 2. Repeat: 1. Submit program P 2. Obtain leakage 3. Get P(K) 1 Ideal 1. Adversary submits a key K 2. Repeat: 1. Submit program P 2. Simulator is given P, P(K) 3. Obtain simulated leakage 4. Get P(K) Key K Trusted 3 rd party P, P(K) Program P 2 Distinguisher Leakage P(K) Simulator

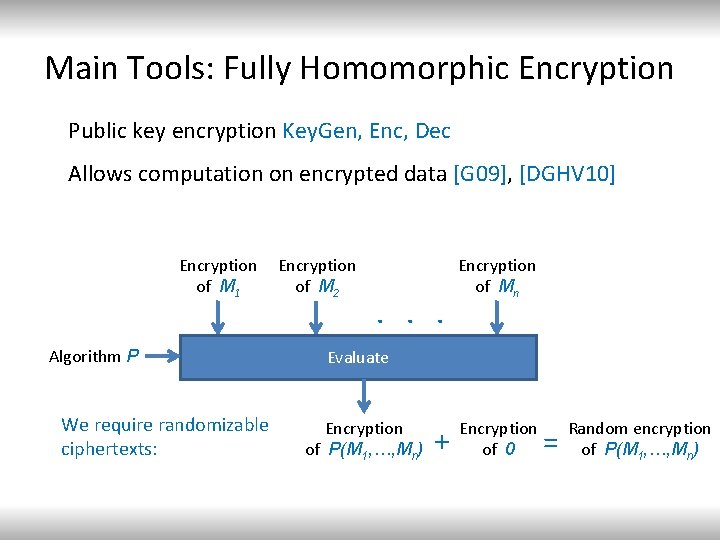
Main Tools: Fully Homomorphic Encryption Public key encryption Key. Gen, Enc, Dec Allows computation on encrypted data [G 09], [DGHV 10] Encryption of M 1 Algorithm P We require randomizable ciphertexts: Encryption of M 2 . . . Encryption of Mn Evaluate Encryption of P(M 1, …, Mn) + Encryption of 0 = Random encryption of P(M 1, …, Mn)

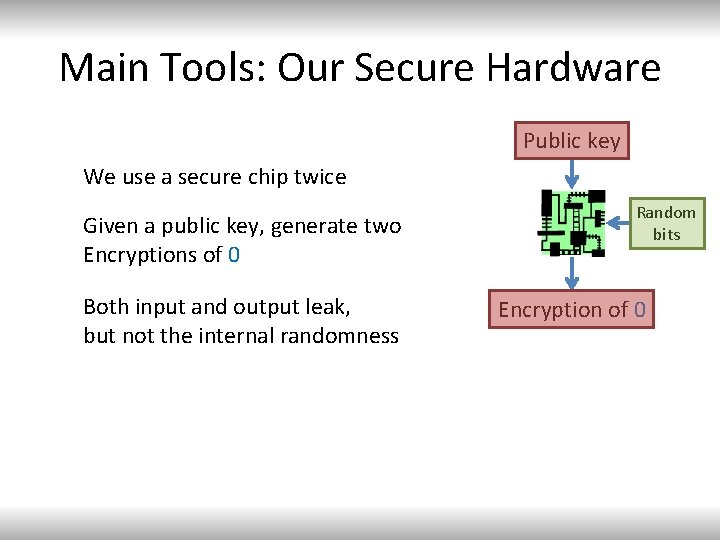
Main Tools: Our Secure Hardware Public key We use a secure chip twice Given a public key, generate two Encryptions of 0 Both input and output leak, but not the internal randomness Random bits Encryption of 0

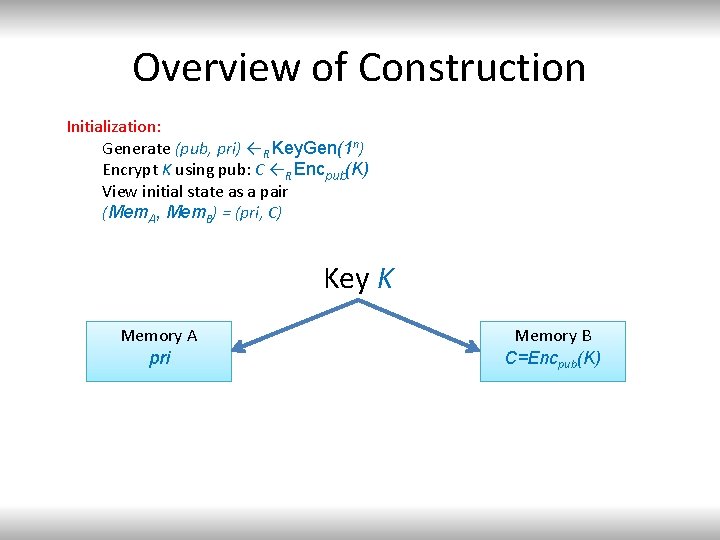
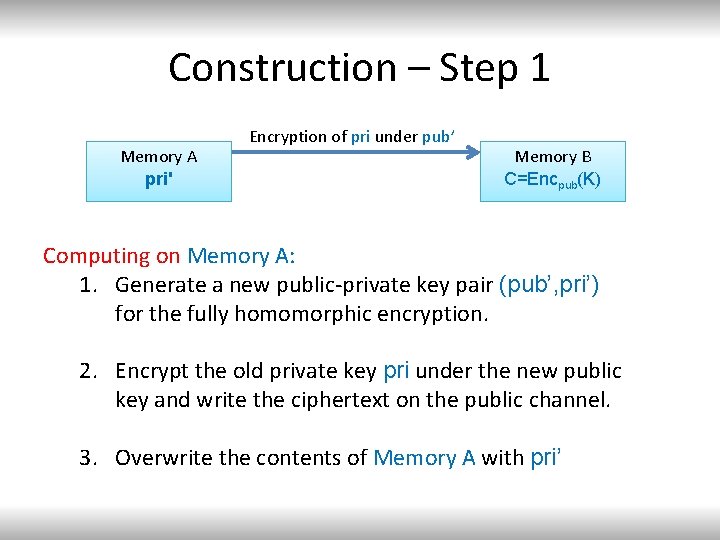
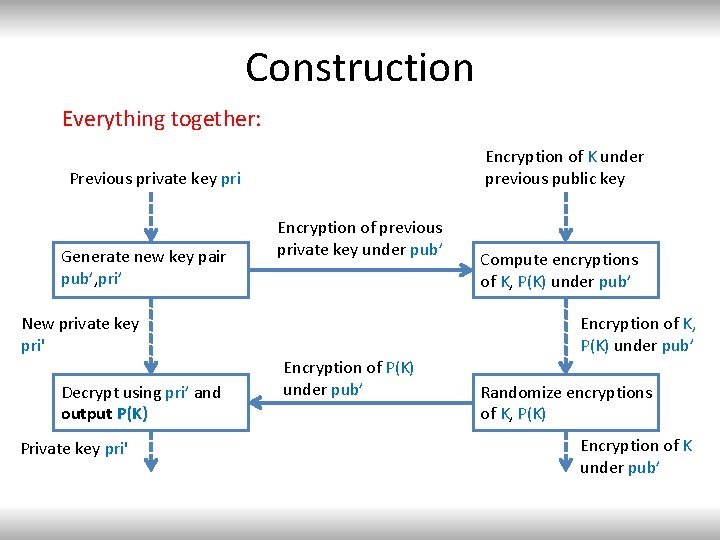
Overview of Construction Initialization: Generate (pub, pri) ← R Key. Gen(1 n) Encrypt K using pub: C ←R Encpub(K) View initial state as a pair (Mem. A, Mem. B) = (pri, C) Key K Memory A pri Memory B C=Encpub(K)

Overview of Construction Memory A pri Memory B C=Encpub(K)

Construction – Step 1 Memory A pri' pri Encryption of pri under pub’ Memory B C=Encpub(K) Computing on Memory A: 1. Generate a new public-private key pair (pub’, pri’) for the fully homomorphic encryption. 2. Encrypt the old private key pri under the new public key and write the ciphertext on the public channel. 3. Overwrite the contents of Memory A with pri’

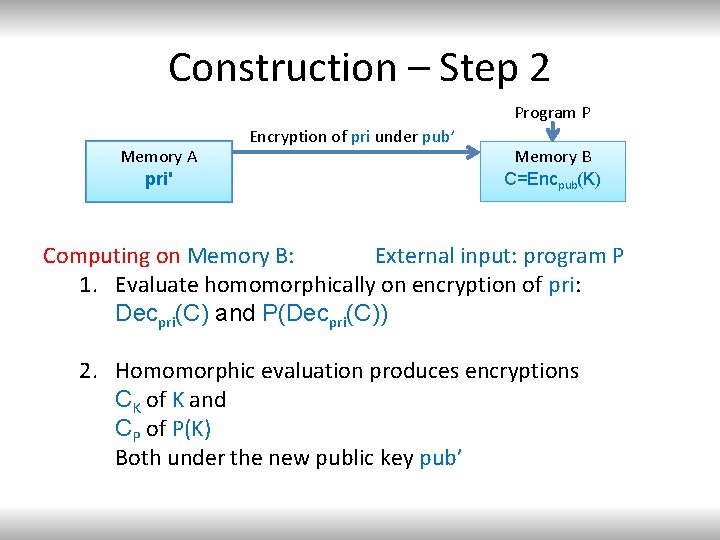
Construction – Step 2 Program P Memory A pri' pri Encryption of pri under pub’ Memory B C=Encpub(K) Computing on Memory B: External input: program P 1. Evaluate homomorphically on encryption of pri: Decpri(C) and P(Decpri(C)) 2. Homomorphic evaluation produces encryptions CK of K and CP of P(K) Both under the new public key pub’

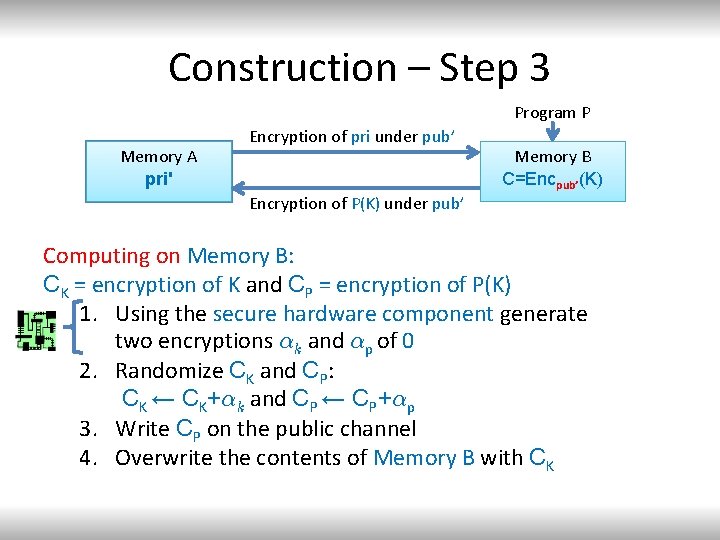
Construction – Step 3 Program P Memory A pri' pri Encryption of pri under pub’ Encryption of P(K) under pub’ Memory B C=Encpub’ (K) pub(K) Computing on Memory B: CK = encryption of K and CP = encryption of P(K) 1. Using the secure hardware component generate two encryptions ®k and ®p of 0 2. Randomize CK and CP: CK ← CK+®k and CP ← CP+®p 3. Write CP on the public channel 4. Overwrite the contents of Memory B with CK

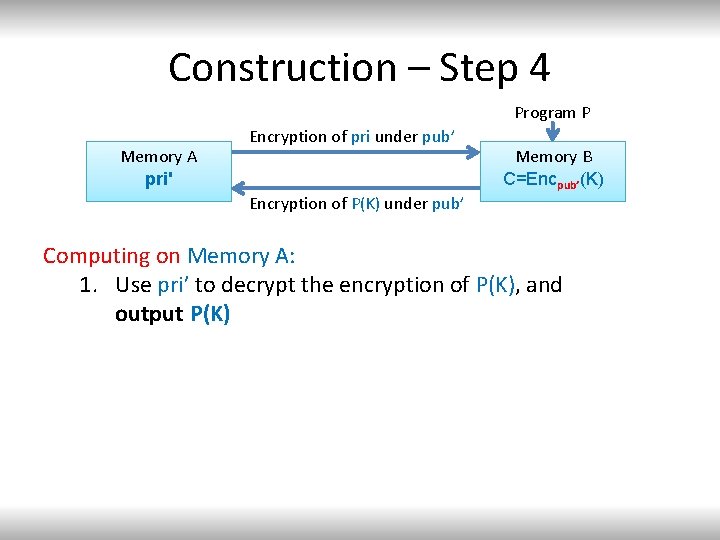
Construction – Step 4 Program P Memory A pri' pri Encryption of pri under pub’ Encryption of P(K) under pub’ Memory B C=Encpub’ (K) pub(K) Computing on Memory A: 1. Use pri’ to decrypt the encryption of P(K), and output P(K)

Construction Everything together: Encryption of K under previous public key Previous private key pri Generate new key pair pub’, pri’ Encryption of previous private key under pub’ New private key pri' Decrypt using pri’ and output P(K) Private key pri' Compute encryptions of K, P(K) under pub’ Encryption of P(K) under pub’ Randomize encryptions of K, P(K) Encryption of K under pub’

Secure Hardware Components Can we rely on secure hardware to achieve leakage resilience? Yes, but it would be nice if it is 1. Independent from protected functionality: amount and function of hardware should be same for all applications 2. Memory-less: secure against adversaries with a drill 3. Testable: operates on inputs from a known distribution

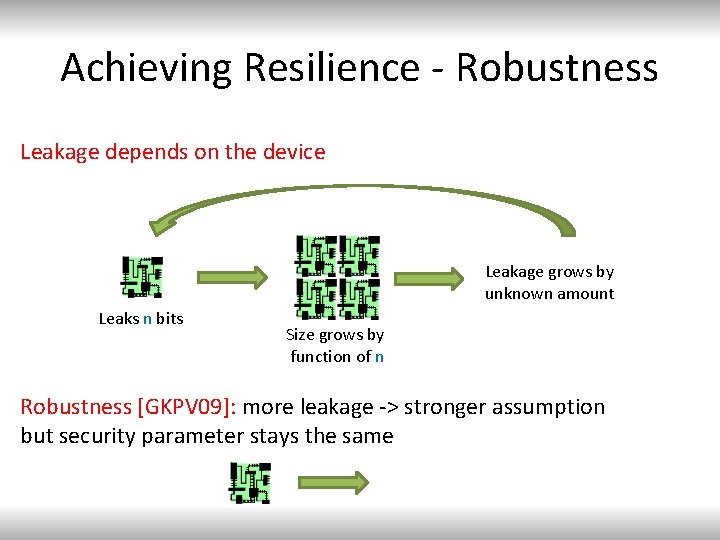
Achieving Resilience - Robustness Leakage depends on the device Leakage grows by unknown amount Leaks n bits Size grows by function of n Robustness [GKPV 09]: more leakage -> stronger assumption but security parameter stays the same

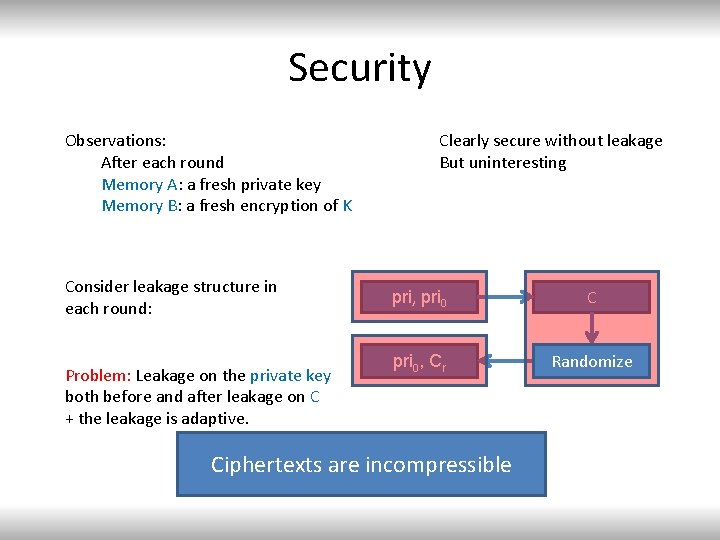
Security Observations: After each round Memory A: a fresh private key Memory B: a fresh encryption of K Consider leakage structure in each round: Problem: Leakage on the private key both before and after leakage on C + the leakage is adaptive. Clearly secure without leakage But uninteresting pri, pri 0 C pri 0, Cr Randomize Ciphertexts are incompressible

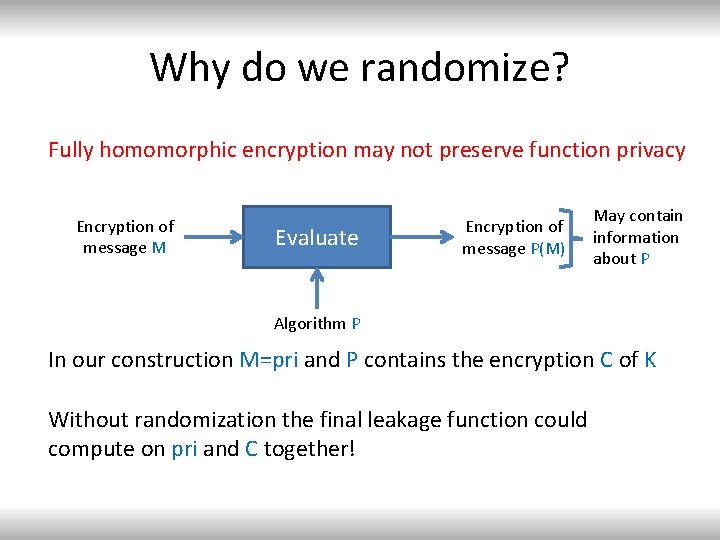
Why do we randomize? Fully homomorphic encryption may not preserve function privacy Encryption of message M Evaluate Encryption of message P(M) May contain information about P Algorithm P In our construction M=pri and P contains the encryption C of K Without randomization the final leakage function could compute on pri and C together!

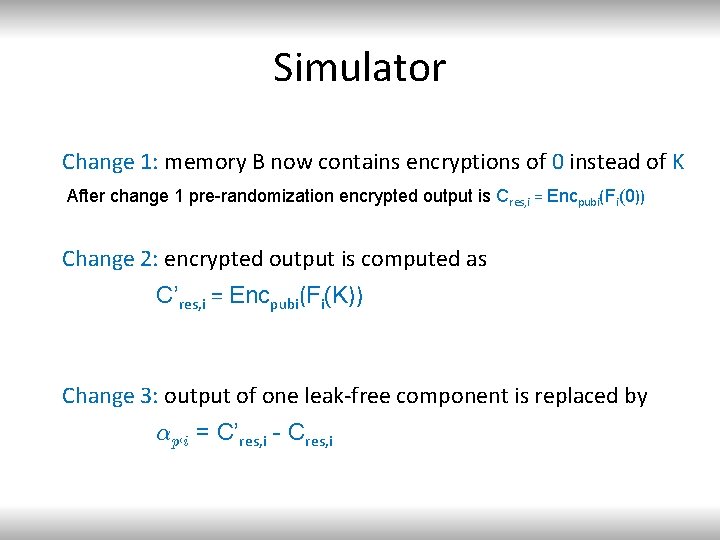
Simulator Change 1: memory B now contains encryptions of 0 instead of K After change 1 pre-randomization encrypted output is Cres, i = Encpubi(Fi(0)) Change 2: encrypted output is computed as C’res, i = Encpubi(Fi(K)) Change 3: output of one leak-free component is replaced by ®p, i = C’res, i - Cres, i

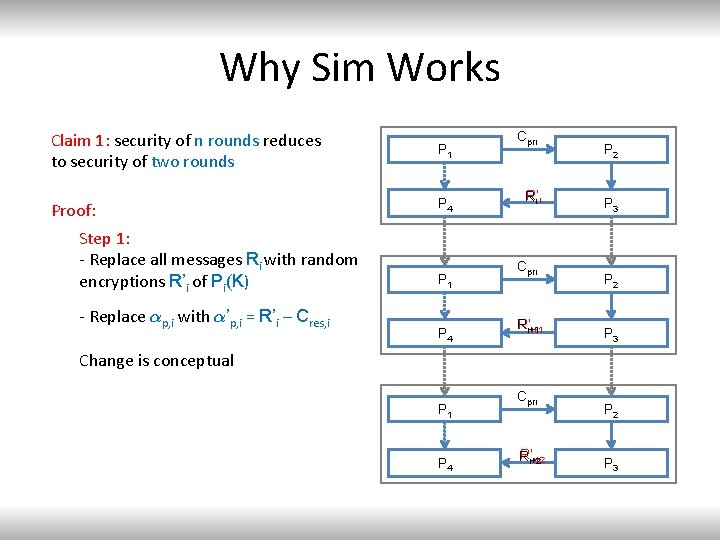
Why Sim Works Claim 1: security of n rounds reduces to security of two rounds P 1 Proof: P 4 Step 1: - Replace all messages Ri with random encryptions R’i of Pi(K) - Replace ®p, i with ®’p, i = R’i – Cres, i P 1 P 4 Cpri R’i i R Cpri R’i+1 R i+1 P 2 P 3 Change is conceptual P 1 P 4 Cpri R’i+2 R i+2 P 3

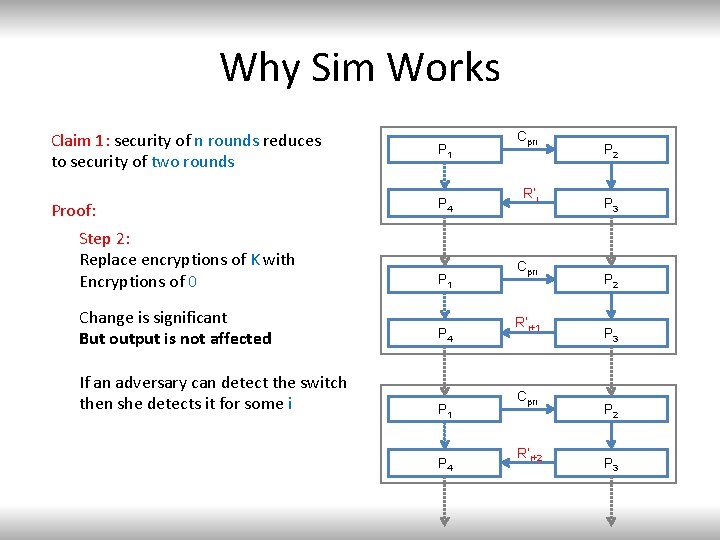
Why Sim Works Claim 1: security of n rounds reduces to security of two rounds P 1 Proof: P 4 Step 2: Replace encryptions of K with Encryptions of 0 P 1 Change is significant But output is not affected P 4 If an adversary can detect the switch then she detects it for some i P 1 P 4 Cpri R’i+1 Cpri R’i+2 P 3 P 2 P 3

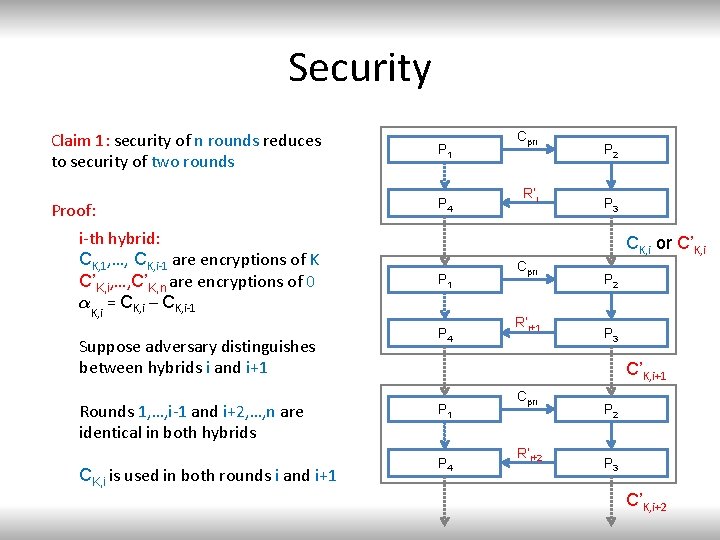
Security Claim 1: security of n rounds reduces to security of two rounds P 1 Proof: P 4 i-th hybrid: CK, 1, …, CK, i-1 are encryptions of K C’K, i, …, C’K, n are encryptions of 0 ®K, i = CK, i – CK, i-1 Suppose adversary distinguishes between hybrids i and i+1 Rounds 1, …, i-1 and i+2, …, n are identical in both hybrids CK, i is used in both rounds i and i+1 Cpri R’i P 2 P 3 CK, i or C’K, i P 1 P 4 Cpri R’i+1 P 2 P 3 C’K, i+1 P 4 Cpri R’i+2 P 3 C’K, i+2

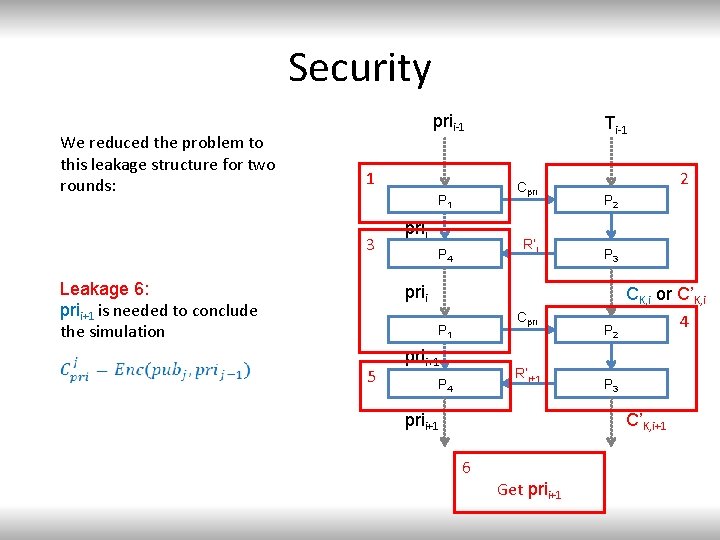
Security We reduced the problem to this leakage structure for two rounds: prii-1 1 Cpri P 1 3 Leakage 6: prii+1 is needed to conclude the simulation Ti-1 prii R’i P 4 2 P 3 prii CK, i or C’K, i Cpri P 1 5 prii+1 R’i+1 P 4 prii+1 4 P 2 P 3 C’K, i+1 6 Get prii+1

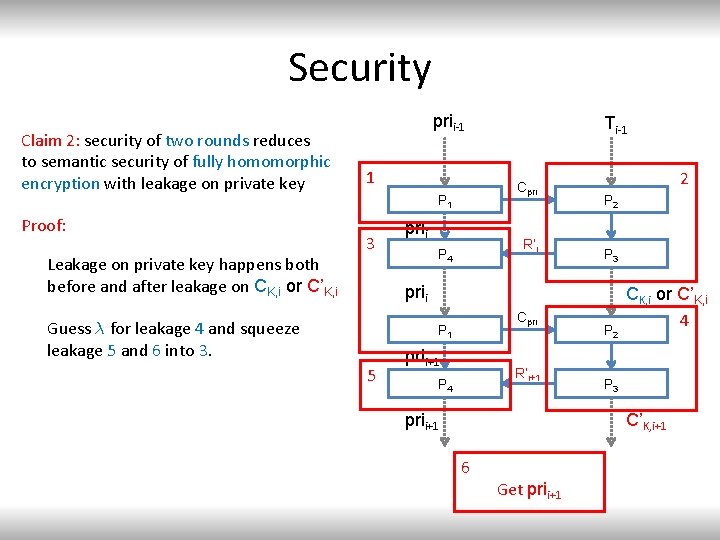
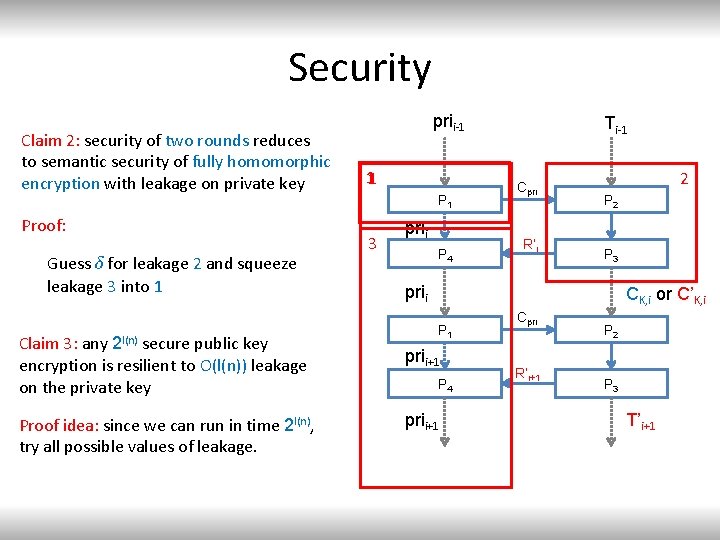
Security Claim 2: security of two rounds reduces to semantic security of fully homomorphic encryption with leakage on private key Proof: Leakage on private key happens both before and after leakage on CK, i or C’K, i prii-1 1 Cpri P 1 3 Ti-1 prii R’i P 4 2 P 3 prii Guess ¸ for leakage 4 and squeeze leakage 5 and 6 into 3. Cpri P 1 5 prii+1 R’i+1 P 4 prii+1 P 2 CK, i or C’K, i 4 P 3 C’K, i+1 6 Get prii+1

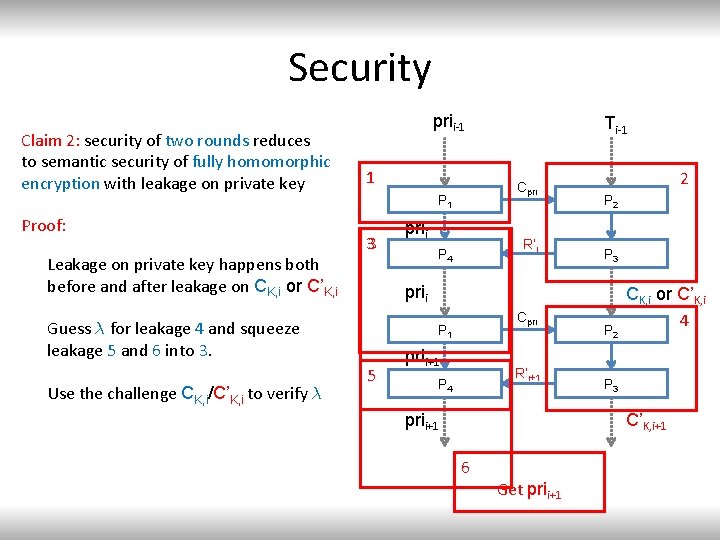
Security Claim 2: security of two rounds reduces to semantic security of fully homomorphic encryption with leakage on private key Proof: Leakage on private key happens both before and after leakage on CK, i or C’K, i prii-1 1 prii R’i P 4 2 P 3 prii Guess ¸ for leakage 4 and squeeze leakage 5 and 6 into 3. Use the challenge CK, i/C’K, i to verify ¸ Cpri P 1 3 Ti-1 Cpri P 1 5 prii+1 R’i+1 P 4 prii+1 P 2 CK, i or C’K, i 4 P 3 C’K, i+1 6 Get prii+1

Security Claim 2: security of two rounds reduces to semantic security of fully homomorphic encryption with leakage on private key Proof: Guess ± for leakage 2 and squeeze leakage 3 into 1 Claim 3: any secure public key encryption is resilient to O(l(n)) leakage on the private key 2 l(n) Proof idea: since we can run in time 2 l(n), try all possible values of leakage. prii-1 1 P 1 3 prii P 4 Ti-1 Cpri R’i 2 P 3 prii CK, i or C’K, i P 1 prii+1 P 4 prii+1 Cpri R’i+1 P 2 P 3 T’i+1