Cryptography and Network Security Chapter 12 Message Authentication











- Slides: 21

Cryptography and Network Security Chapter 12 Message Authentication Codes Fifth Edition by William Stallings Lecture slides by Lawrie Brown

Message Authentication Ø message authentication is concerned with: l l l protecting the integrity of a message validating identity of originator non-repudiation of origin (dispute resolution) will consider the security requirements Ø then three alternative functions used: Ø l l l hash function (see Ch 11) message encryption message authentication code (MAC)

Message Security Requirements Ø disclosure Ø traffic analysis Ø masquerade Ø content modification Ø sequence modification Ø timing modification Ø source repudiation Ø destination repudiation

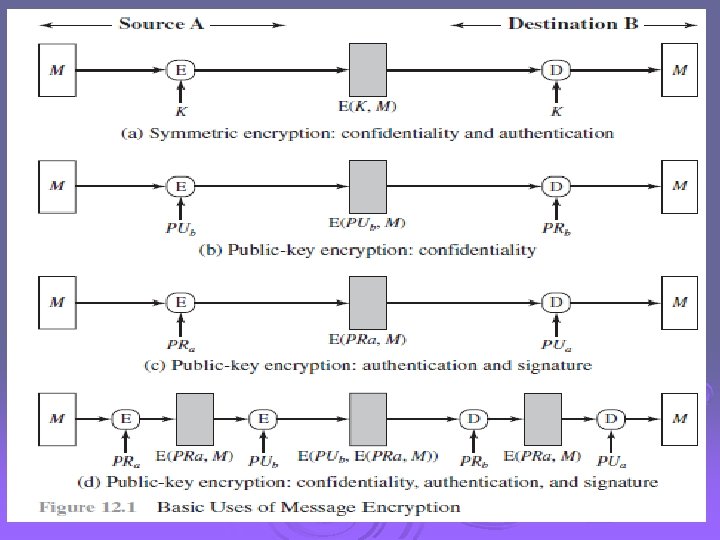
Symmetric Message Encryption Ø encryption can also provides authentication Ø if symmetric encryption is used then: l l receiver know sender must have created it since only sender and receiver now key used know content cannot of been altered if message has suitable structure, redundancy or a checksum to detect any changes

Public-Key Message Encryption Ø if public-key encryption is used: l encryption provides no confidence of sender • since anyone potentially knows public-key l however if • sender signs message using their private-key • then encrypts with recipients public key • have both secrecy and authentication l l again need to recognize corrupted messages but at cost of two public-key uses on message


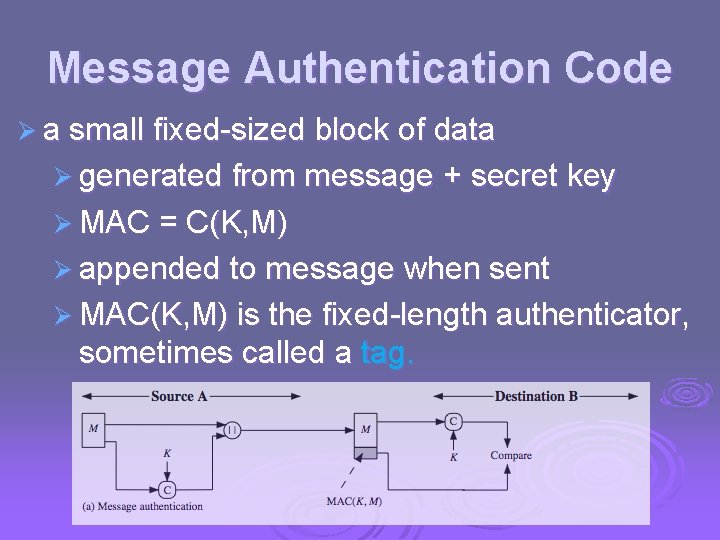
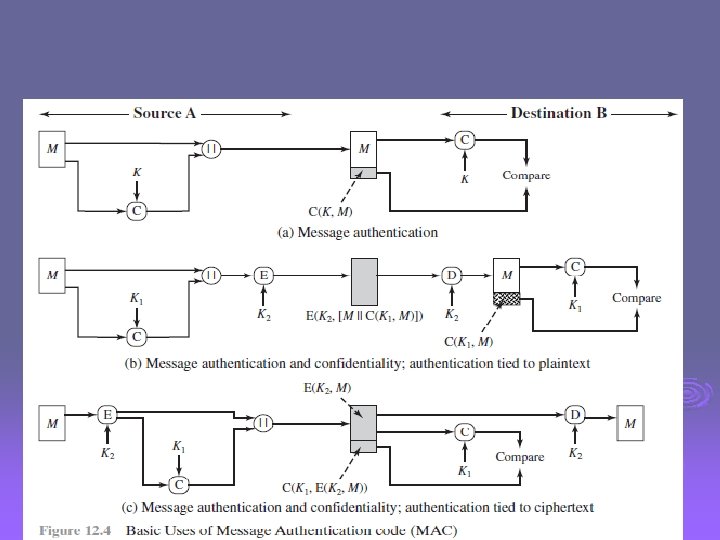
Message Authentication Code (MAC) Ø generated by an algorithm that creates a small fixed-sized block l l depending on both message and some key like encryption though need not be reversible Ø appended to message as a signature Ø receiver performs same computation on message and checks it matches the MAC Ø provides assurance that message is unaltered and comes from sender

Ø MACs are used between two parties that share a secret key to authenticate information exchanged between those parties. Ø A MAC function takes as input a secret key and a data block and produces a hash value, referred to as the MAC. Ø two categories: Ø those built from cryptographic hash functions and those built using a block cipher

Message Authentication Code Ø a small fixed-sized block of data Ø generated from message + secret key Ø MAC = C(K, M) Ø appended to message when sent Ø MAC(K, M) is the fixed-length authenticator, sometimes called a tag.

Message Authentication Codes as shown the MAC provides authentication Ø can also use encryption for secrecy Ø l l l Ø why use a MAC? l l Ø generally use separate keys for each can compute MAC either before or after encryption is generally regarded as better done before sometimes only authentication is needed sometimes need authentication to persist longer than the encryption (eg. archival use) note that a MAC is not a digital signature


MAC Properties Ø a MAC is a cryptographic checksum l l l MAC = CK(M) condenses a variable-length message M using a secret key K to a fixed-sized authenticator Ø is a many-to-one function l l potentially many messages have same MAC but finding these needs to be very difficult

Requirements for MACs taking into account the types of attacks Ø need the MAC to satisfy the following: Ø 1. 2. 3. knowing a message and MAC, is infeasible to find another message with same MACs should be uniformly distributed MAC should depend equally on all bits of the message

Keyed Hash Functions as MACs Ø want a MAC based on a hash function l l because hash functions are generally faster crypto hash function code is widely available Ø hash includes a key along with message Ø original proposal: Keyed. Hash = Hash(Key|Message) l some weaknesses were found with this Ø eventually led to development of HMAC

HMAC Design Objectives Ø use, without modifications, hash functions Ø allow for easy replaceability of embedded hash function Ø preserve original performance of hash function without significant degradation Ø use and handle keys in a simple way. Ø have well understood cryptographic analysis of authentication mechanism strength

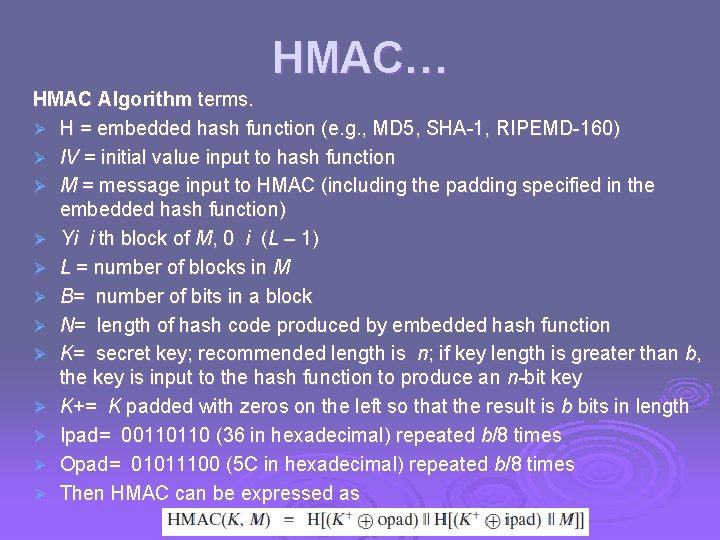
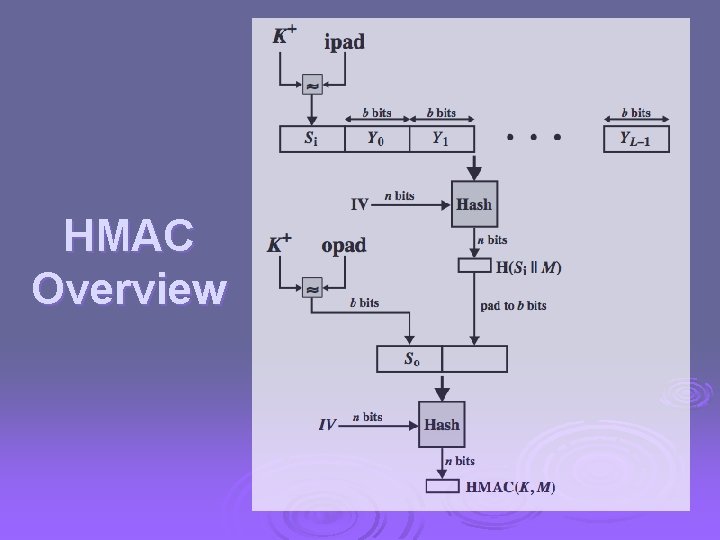
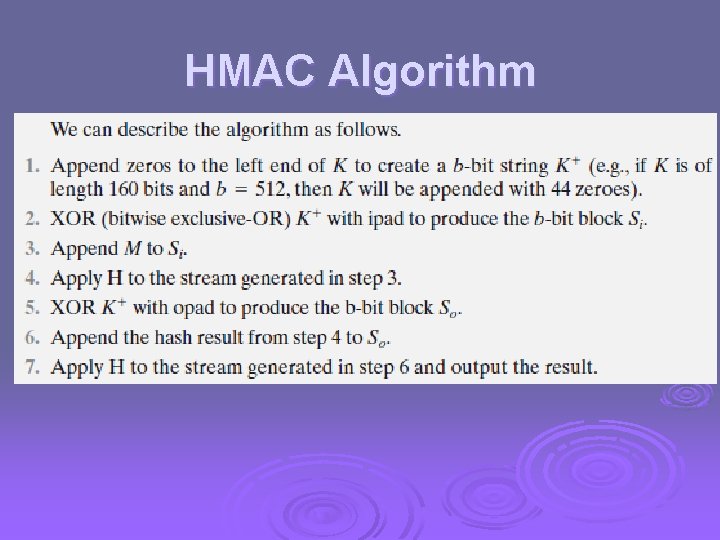
HMAC specified as Internet standard RFC 2104 Ø uses hash function on the message: Ø HMACK(M)= Hash[(K+ XOR opad) || Hash[(K+ XOR ipad) || M)] ] + is the key padded out to size l where K l opad, ipad are specified padding constants overhead is just 3 more hash calculations than the message needs alone Ø any hash function can be used Ø l eg. MD 5, SHA-1, RIPEMD-160, Whirlpool

HMAC… HMAC Algorithm terms. Ø H = embedded hash function (e. g. , MD 5, SHA-1, RIPEMD-160) Ø IV = initial value input to hash function Ø M = message input to HMAC (including the padding specified in the embedded hash function) Ø Yi i th block of M, 0 i (L – 1) Ø L = number of blocks in M Ø B= number of bits in a block Ø N= length of hash code produced by embedded hash function Ø K= secret key; recommended length is n; if key length is greater than b, the key is input to the hash function to produce an n-bit key Ø K+= K padded with zeros on the left so that the result is b bits in length Ø Ipad= 00110110 (36 in hexadecimal) repeated b/8 times Ø Opad= 01011100 (5 C in hexadecimal) repeated b/8 times Ø Then HMAC can be expressed as

HMAC Overview

HMAC Algorithm

Using Symmetric Ciphers for MACs Ø can use any block cipher chaining mode and use final block as a MAC Ø Data Authentication Algorithm (DAA) is a widely used MAC based on DES-CBC l l l using IV=0 and zero-pad of final block encrypt message using DES in CBC mode and send just the final block as the MAC • or the leftmost M bits (16≤M≤ 64) of final block Ø but final MAC is now too small for security

Summary Ø have considered: l l l message authentication requirements message authentication using encryption MACs HMAC authentication using a hash function CMAC authentication using a block cipher Pseudorandom Number Generation (PRNG) using Hash Functions and MACs