Copyright Notice All materials contained within this document


























- Slides: 38

Copyright Notice. All materials contained within this document are protected by United States copyright law and may not be reproduced, distributed, transmitted, displayed, published, or broadcast without the prior, express written permission of Clearwater Compliance LLC. You may not alter or remove any copyright or other notice from copies of this content. For reprint permission and information, please direct your inquiry to bob. chaput@clearwatercompliance. com © Clearwater Compliance LLC | All Rights Reserved 1

Legal Disclaimer. This information does not constitute legal advice and is for educational purposes only. This information is based on current federal law and subject to change based on changes in federal law or subsequent interpretative guidance. Since this information is based on federal law, it must be modified to reflect state law where that state law is more stringent than the federal law or other state law exceptions apply. This information is intended to be a general information resource regarding the matters covered, and may not be tailored to your specific circumstance. YOU SHOULD EVALUATE ALL INFORMATION, OPINIONS AND ADVICE PROVIDED HEREIN IN CONSULTATION WITH YOUR LEGAL OR OTHER ADVISOR, AS APPROPRIATE. The existence of a link or organizational reference in any of the following materials should not be assumed as an endorsement by Clearwater Compliance LLC. © Clearwater Compliance LLC | All Rights Reserved 2

Instructional Module 1: How to Set Up Your Privacy and Security Risk Management & Governance Program © Clearwater Compliance LLC | All Rights Reserved 3

Module 1. Overview 1. “How to Set Up Your Privacy and Security Risk Management & Governance Program” 2. Instructional Module Duration = 45 minutes 3. Learning Objectives Addressed In This Module ‒ Use Clearwater Strategic HIPAA-HITECH Compliance Alignment. Check™ to assess the alignment of your organization’s business strategy with compliance ‒ Learn how to measure Risk using Risk Likelihood and Risk Impact ‒ Learn how to use a process for building a business case for strengthening PHI security ‒ Use Excel template provided to calculate the cost of a breach for your organization ‒ Learn the “tips & tricks” for strengthening your Compliance Risk Management Program ‒ Use Word templates to create a charter and standing agenda for your HIPAA Compliance Council © Clearwater Compliance LLC | All Rights Reserved 4

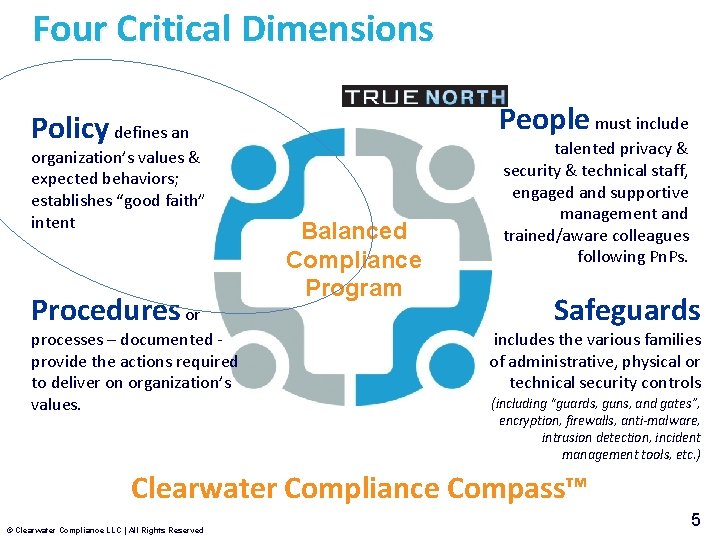
Four Critical Dimensions People must include Policy defines an organization’s values & expected behaviors; establishes “good faith” intent Procedures or processes – documented provide the actions required to deliver on organization’s values. Balanced Compliance Program talented privacy & security & technical staff, engaged and supportive management and trained/aware colleagues following Pn. Ps. Safeguards includes the various families of administrative, physical or technical security controls (including “guards, guns, and gates”, encryption, firewalls, anti-malware, intrusion detection, incident management tools, etc. ) Clearwater Compliance Compass™ © Clearwater Compliance LLC | All Rights Reserved 5

9 Actions to Take Now 1. Set Privacy and Security Risk Management & Governance Program in place (45 CFR § 164. 308(a)(1)) 2. Develop & Implement comprehensive HIPAA Privacy and Security and Breach Notification Policies & Procedures (45 CFR § 164. 530 and 45 CFR § 164. 316) 3. Train all Members of Your Workforce (45 CFR § 164. 530(b) and 45 CFR § 164. 308(a)(5)) 4. Complete a HIPAA Security Risk Analysis (45 CFR § 164. 308(a)(1)(ii)(A)) 5. Complete a HIPAA Security Evaluation (= compliance assessment) (45 CFR § 164. 308(a)(8)) 6. Complete Technical Testing of Your Environment (45 CFR § 164. 308(a)(8)) 7. Implement a Strong, Proactive Business Associate / Management Program (45 CFR § 164. 502(e) and 45 CFR § 164. 308(b)) 8. Complete Privacy Rule and Breach Rule compliance assessments (45 CFR § 164. 530 and 45 CFR § 164. 400) 9. Document and act upon a remediation plan Demonstrate Good Faith Effort! © Clearwater Compliance LLC | All Rights Reserved 6

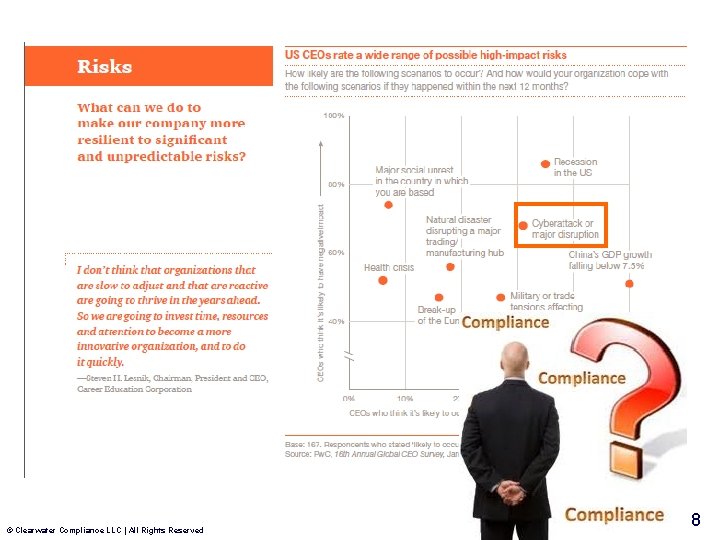
http: //www. pwc. com/us/en/ceo-survey-us/downloads. jhtml © Clearwater Compliance LLC | All Rights Reserved 7

© Clearwater Compliance LLC | All Rights Reserved 8

Some Definitions…. • Risk is the potential of losing something of value, weighed against the potential to gain something of value. • Risk management is the continuing process to identify, analyze, evaluate, prioritize and treat loss exposures and to monitor risk controls and financial resources to mitigate the adverse effects of loss. • Risk treatment is the decision to avoid, mitigate, transfer, or accept certain risks © Clearwater Compliance LLC | All Rights Reserved 9

Measuring Risk What …. • Bad Thing Could Happen • Vulnerabilities Exist • What Offsetting Controls or Safeguards Exist • Is the Likelihood of that Bad Thing Happening • Is the Potential Impact if the Bad Thing Happens Result: Risk Rating © Clearwater Compliance LLC | All Rights Reserved 10

Likelihood Chance that a bad thing will happen? © Clearwater Compliance LLC | All Rights Reserved 11

Impact Harm or loss if bad thing happens? © Clearwater Compliance LLC | All Rights Reserved 12

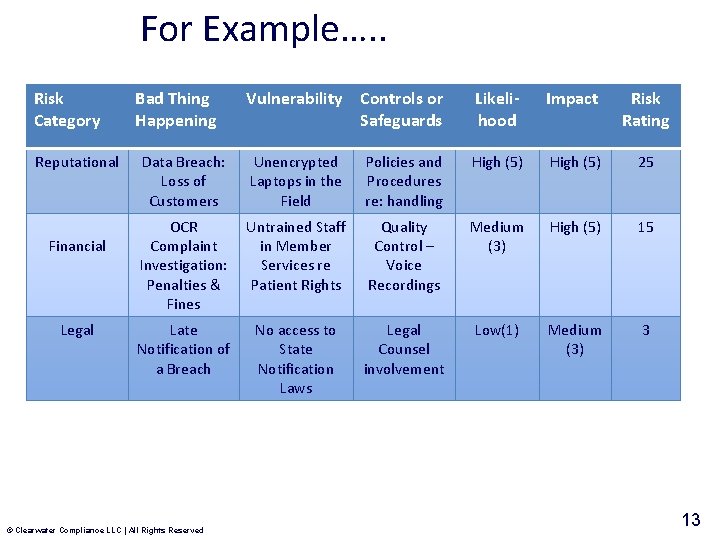
For Example…. . Risk Category Reputational Financial Legal Bad Thing Happening Vulnerability Controls or Safeguards Likelihood Impact Risk Rating Data Breach: Loss of Customers Unencrypted Laptops in the Field Policies and Procedures re: handling High (5) 25 OCR Complaint Investigation: Penalties & Fines Untrained Staff in Member Services re Patient Rights Quality Control – Voice Recordings Medium (3) High (5) 15 Late Notification of a Breach No access to State Notification Laws Legal Counsel involvement Low(1) Medium (3) 3 © Clearwater Compliance LLC | All Rights Reserved 13

Measuring Risk What …. • Bad Thing Could Happen • Vulnerabilities Exist • What Offsetting Controls or Safeguards) Exist • Is the Likelihood of that Bad Thing Happening • Is the Potential Impact if the Bad Thing Happens Result: Risk Rating Where do the arguments lie? For Privacy, Security and Compliance – the Likelihood and the Impact © Clearwater Compliance LLC | All Rights Reserved 14

Calculating the Likelihood and Impact of a Bad Thing Happening © Clearwater Compliance LLC | All Rights Reserved 15

Industry/Expert Collaboration Table of Contents 1. The Progression of the Health Care Ecosystem 2. The Evolution of Laws, Rules, and Regulations 3. PHI Data Breach Landscape 4. Threats and Vulnerabilities 5. Safeguards and Controls 6. Survey Findings: Current Practices and Attitudes 7. Data Breach Costing Framework 8. Calculating the Cost of a PHI Breach 9. Finale 10. Appendices © Clearwater Compliance LLC | All Rights Reserved

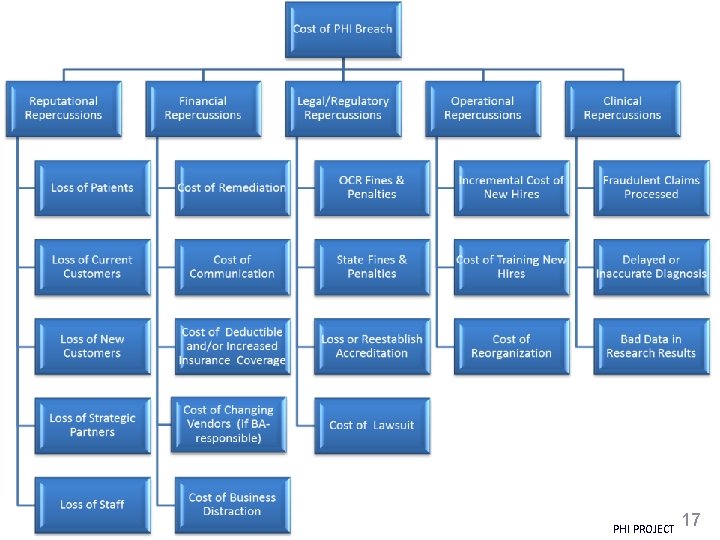
© Clearwater Compliance LLC | All Rights Reserved PHI PROJECT 17

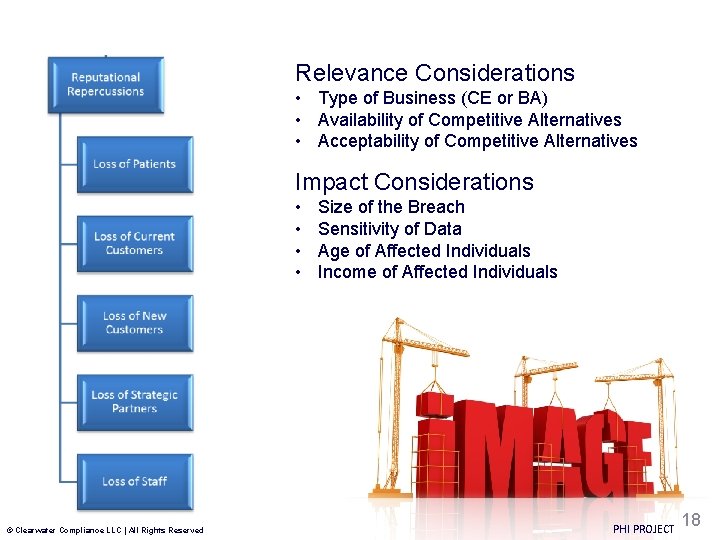
Relevance Considerations • Type of Business (CE or BA) • Availability of Competitive Alternatives • Acceptability of Competitive Alternatives Impact Considerations • • © Clearwater Compliance LLC | All Rights Reserved Size of the Breach Sensitivity of Data Age of Affected Individuals Income of Affected Individuals PHI PROJECT 18

Time to get to work…. © Clearwater Compliance LLC | All Rights Reserved 19

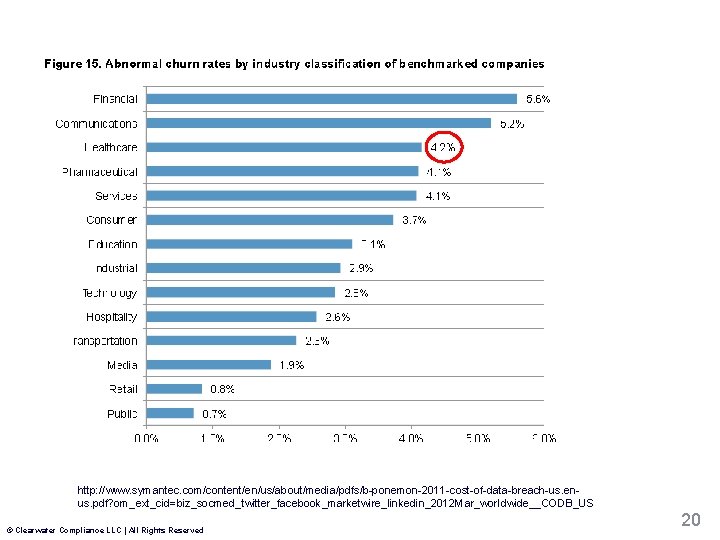
http: //www. symantec. com/content/en/us/about/media/pdfs/b-ponemon-2011 -cost-of-data-breach-us. enus. pdf? om_ext_cid=biz_socmed_twitter_facebook_marketwire_linkedin_2012 Mar_worldwide__CODB_US © Clearwater Compliance LLC | All Rights Reserved 20

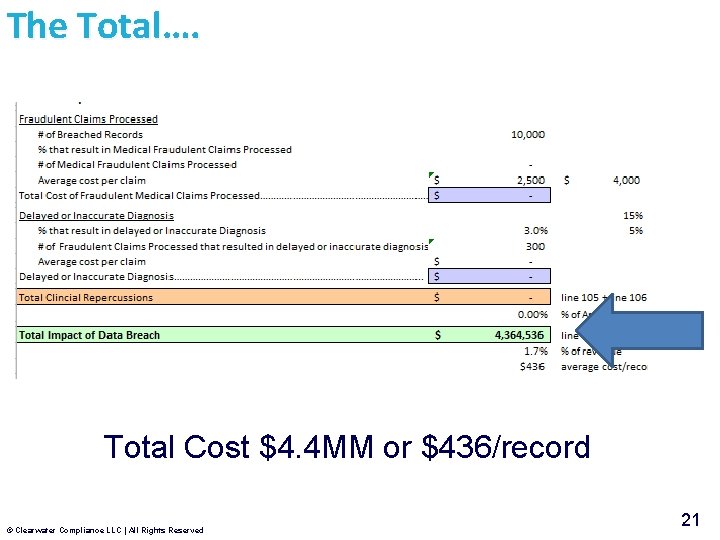
The Total…. Total Cost $4. 4 MM or $436/record © Clearwater Compliance LLC | All Rights Reserved 21

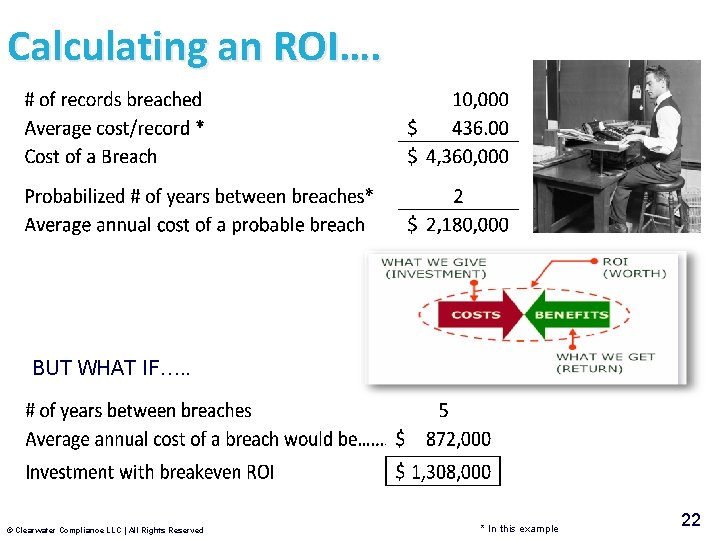
Calculating an ROI…. BUT WHAT IF…. . © Clearwater Compliance LLC | All Rights Reserved * In this example 22

Tips & Tricks for Establishing or Strengthening Your Privacy & Security Risk Management Program © Clearwater Compliance LLC | All Rights Reserved 23

1. Secure a Sponsor on the Executive Team © Clearwater Compliance LLC | All Rights Reserved 24

de co nfi rity eg int nti ali ty 2. Change the Conversation availability © Clearwater Compliance LLC | All Rights Reserved 25

Pause & Quick Poll • Has your organization established a formal Privacy & Security Risk Management Oversight Council? YES NO DON’T KNOW Formal HIPAAHITECH Oversight Council © Clearwater Compliance LLC | All Rights Reserved 26

3. Establish or Strengthen your Privacy & Security Risk Management Oversight Council • Provide strategic direction relative to risk philosophy • Establish authority, responsibility and accountability • Understand the level of risk and the impact of the consequences • Approve initiatives to reduce or mitigate risk • Ensure adequate resources to achieve initiatives • Provide high level support for initiatives • Be aware of compliance issues and remediation • Ascertain that risks are managed appropriately © Clearwater Compliance LLC | All Rights Reserved 27

4. Establish or Strengthen your Privacy & Security Working Group • Develop and implement an effective compliance program • Educate the Compliance Oversight Council on Risks: Likelihood and Impact • Make recommendations and implement approved initiatives to reduce or eliminate risks • Provide frequent and effective updates to the Oversight Council on: – – – Regulatory Changes Trends in Incidents/Breaches Compliance Audits Remediation Progress Training Updates Non-compliance issues and resolutions © Clearwater Compliance LLC | All Rights Reserved 28

Working Group Membership? Privacy Officer Security Officer Clinical Operations Patient/Member Services Provider Services Claims Administration Grievances & Complaints Processing IT Quality Improvement HR Audit Legal Data Analysis Project Management …. (just to name a few) Approximately 10 -15 senior managers who are responsible for PHI © Clearwater Compliance LLC | All Rights Reserved 29

© Clearwater Compliance LLC | All Rights Reserved 30

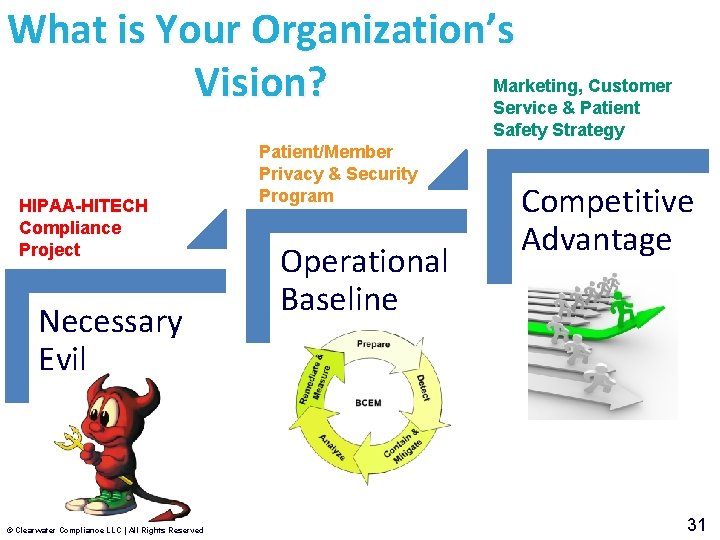
What is Your Organization’s Marketing, Customer Vision? Service & Patient Safety Strategy HIPAA-HITECH Compliance Project Necessary Evil © Clearwater Compliance LLC | All Rights Reserved Patient/Member Privacy & Security Program Operational Baseline Competitive Advantage 31

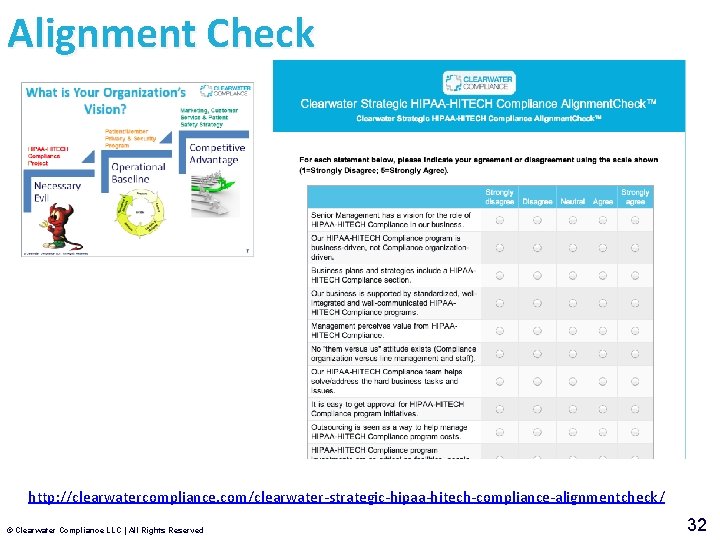
Alignment Check http: //clearwatercompliance. com/clearwater-strategic-hipaa-hitech-compliance-alignmentcheck/ © Clearwater Compliance LLC | All Rights Reserved 32

5. Align your recommendations with the business strategy… © Clearwater Compliance LLC | All Rights Reserved 33

6. Calculate a (believable) ROI on investments in PHI privacy, security and compliance © Clearwater Compliance LLC | All Rights Reserved 34

The Challenges • Alignment with Business Strategy Is Dynamic • Constant Change Occurring in Strategic Context --Market, Customers, Products, Etc. • Constant Change Occurring in Environment --Technology, Competition, Regulation, Etc. • Takes Time and Energy of Executive Staff • Takes Commitment of your Working Group Goal Is To Keep Compliance Investments And Program Heading In The Right Direction… The Direction That Supports Your Growth Plans © Clearwater Compliance LLC | All Rights Reserved 35

In Summary… 1. Secure a Sponsor on the Executive Team 2. “Change the conversation” 3. Establish an HIPAA Compliance Oversight Council 4. Establish a HIPAA Working Group 5. Align your recommendations with the business strategy 6. Calculate an ROI on PHI Security Investment 7. Ensure On-Going Efforts and Accomplishments © Clearwater Compliance LLC | All Rights Reserved 36

Supplemental Materials 1 -1. HIPAA Compliance Program Charter template (Word) 1 -2. HIPAA_Compliance_Program 1 st Agenda_ template (Word) 1 -3. Clearwater Strategic HIPAA-HITECH Compliance Alignment. Check™ 1 -4. Clearwater Business Associate Omnibus Readiness. Check™ 1 -5. Clearwater Covered Entity Omnibus Readiness. Check™ 1 -6. The Financial Impact of a Data Breach - ANSI Project Paper 1 -7. Costing of a Data Breach for Your Organization (Excel) © Clearwater Compliance LLC | All Rights Reserved 37

© Clearwater Compliance LLC | All Rights Reserved 38