Controlling Processes Chapter 4 Controlling Processes Introduction n
















- Slides: 24

Controlling Processes Chapter 4 - Controlling Processes

Introduction n A process is the abstraction used by UNIX to represent a running process. n It is the object through which a program’s use of n n n memory, processor time, and I/O resources can be managed and monitored Chapter 4 - Controlling Processes

Introduction n It is part of the UNIX philosophy that as much work as possible be done within the context of processes, rather than be handled specially by the kernel. n Although portions of the kernel cannot be made to fit this model, it is used by most system software. n System and user processes all follow the same rules, so you can use a single set of tools to control them both. Chapter 4 - Controlling Processes

1. Components of a Process n Introduction: n A process consists of an address space and a set of data structures within the kernel. n The address space is a set of memory pages that the kernel has marked for the process’s use. n It contains the code and libraries that the process is executing, the process’s variables, its stacks, and various extra information needed by the kernel while the process is running. Chapter 4 - Controlling Processes

1. Components of a Process n The kernel’s internal data structures record various pieces of information about each process. n Some of the more important of these are: n n n The process’s address space map The current status of the process (sleeping, stopped, runnable, . . ) The execution priority of the process Information about the resources the process has used (for accounting purposes) The process’s signal mask (which signals are blocked) The owner of the process. n Now let’s look at the meaning and significance of the parameters that are interesting from the system 4 - Controlling Processes administrator’s. Chapter point of view.

1. Components of a Process n PID: process ID number n The kernel assigns a unique ID number to every process. n Most commands and system calls that manipulate processes require you to specify a PID to identify the target of the operation n PIDs are assigned in order as processes are created. n When the kernel runs out of PIDs, it starts again at 1, skipping over PIDs that are still in use. Chapter 4 - Controlling Processes

1. Components of a Process n PPID: parent PID An existing program must clone itself to create a new process. n The clone can then exchange the program it is running for a different one. n When a process is cloned the original is called the parent, and the copy is called the child. n The PPID of a process is the PID of the parent from which it was cloned. n n while that parent is alive. Chapter 4 - Controlling Processes

1. Components of a Process n UID and EUID: real and effective user ID n The process’s UID is the user identification number of the person who created it, n more accurately it is a copy of the EUID of the parent process. n The EUID is the “effective” user ID n used to determine what resources and files a process has permission to access n Why have both? n It is useful to maintain a distinction between identity and permission Chapter 4 - Controlling Processes

1. Components of a Process n GID and EGID: real and effective group ID The GID is the group identification number of a process. n The EGID is related to the GID in the same was that the EUID is related to the UID. n If a process tries to access a file for which it does not have owner permissions, the kernel will automatically check to see if permission may be granted on the basis of the EGID n n On some systems, a process can be in more than one group at a time. Chapter 4 - Controlling Processes

1. Components of a Process n Niceness n A process’s scheduling priority determines how much CPU time it receives. n The kernel uses a dynamic algorithm to compute priorities n n n taking into account the amount of CPU time that a process has recently consumed and the length of time it has been waiting to run. It also takes into consideration an administratively set value that’s usually called the “nice value” or “niceness” We will come back to niceness in Section 6. Chapter 4 - Controlling Processes

1. Components of a Process n Control terminal The control terminal determines the linkages for stdin, stdout, and stderr. n The concept of a control terminal also affects the distribution of signals n n We will discuss signals more in Section 3. Chapter 4 - Controlling Processes

2. The Life Cycle of a Process n To create a new process, a process copies itself with the fork system call. n fork creates a copy of the original process. n The copy has a distinct PID and has its own accounting information. n fork returns two different values n from the child’s point of view it returns 0 n the parent, on the other hand is returned the PID of the child Chapter 4 - Controlling Processes

2. The Life Cycle of a Process After fork, the child will often use one of the exec family of system calls to begin executing a new program. n Before a process can be allowed to disappear completely, UNIX requires that its death be acknowledged by the process’s parent n n They do this with a call to n wait. If the parent dies first, the orphan is adopted by init Chapter 4 - Controlling Processes

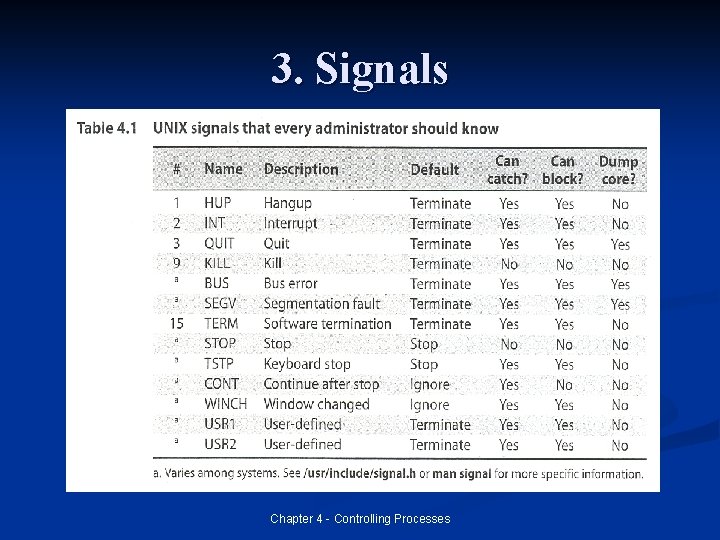
3. Signals n Signals are process-level interrupt requests. About 30 different kinds are defined and they are used in a variety of ways. n They can be sent among processes as a means of communication n They can be sent by the terminal driver to kill, interrupt, or suspend a process n <CTRL-C> and <CTRL-Z> n They can be sent by the administrator to achieve various results. n They can be sent by the kernel when a process commits an infraction (division by 0) Chapter 4 - Controlling Processes

3. Signals n When a signal is received, one of two things can happen. n If the receiving process has designated a handler routine for that particular signal, the handler is called with information about the context in which the signal was delivered. n Otherwise the kernel takes some default action n n many terminate the process some also generate a core dump Chapter 4 - Controlling Processes

3. Signals n Specifying a handler routine is often referred to as “catching the signal” n When the handler completes, execution restarts from the point at which the signal was received n n just like an interrupt To prevent signals from arriving, programs can request that they be either ignored or blocked. n Ignored are thrown away n Blocked are queued until they are unblocked (and only handled once) Chapter 4 - Controlling Processes

3. Signals Chapter 4 - Controlling Processes

4. KILL: Send Signals n The kill program is most often used to terminate a process. It can also send any signal. n kill [-signal] pid n signal is the number or symbolic name of the signal to be sent. n pid is the process id number of the target process n kill -9 pid n will “guarantee” that the process will die because signal 9 (kill) cannot be caught. n You have to reboot to eliminate those that will not die this way (they are stuck) Chapter 4 - Controlling Processes

5. Process States n A process is not automatically eligible to receive CPU time just because it exists. n There are essentially four execution states that you need to be aware of n Runnable - the process can be executed n Sleeping - the process is waiting for some resource n Zombie - the process is trying to die n Stopped - the process is suspended (not allowed to execute) Chapter 4 - Controlling Processes

6. Nice and Renice: Influence Scheduling Priority n The “niceness” of a process is a numeric hint to the kernel about how the process should be treated in relationship to other processes contending for the CPU. This determines how nice you are going to be to other users of the system. n High nice means low priority, Low or negative value means high priority. n Chapter 4 - Controlling Processes

7. PS: Monitor Processes ps is the system administrator’s main tool for monitoring processes. n Understanding ps output is an important administrative skill n n Looking at the ps listing you can determine (among other things) n n n What processes are running. How much CPU and memory they are using Who owns them Chapter 4 - Controlling Processes

8. Top: Monitor Processes Even Better Since the commands like ps offer only a one-time snapshot of your system, it is often difficult to grasp the big picture of what’s really happening. n top is a free utility that runs on many systems that provides a regularly updated summary of active processes and their use of resources n Chapter 4 - Controlling Processes

9. Runaway Processes n Runaway processes come in two flavors n User processes that use up excessive amounts of system resources n sometimes you have to investigate to see if they are legit (doing real computation) or malicious. n System processes that suddenly go berserk and exhibit wild behavior. Chapter 4 - Controlling Processes

Chapter 4 - Controlling Processes