Chapter 8 Internet Protocol IP Kyung Hee University



- Slides: 62

Chapter 8 Internet Protocol (IP) Kyung Hee University 1

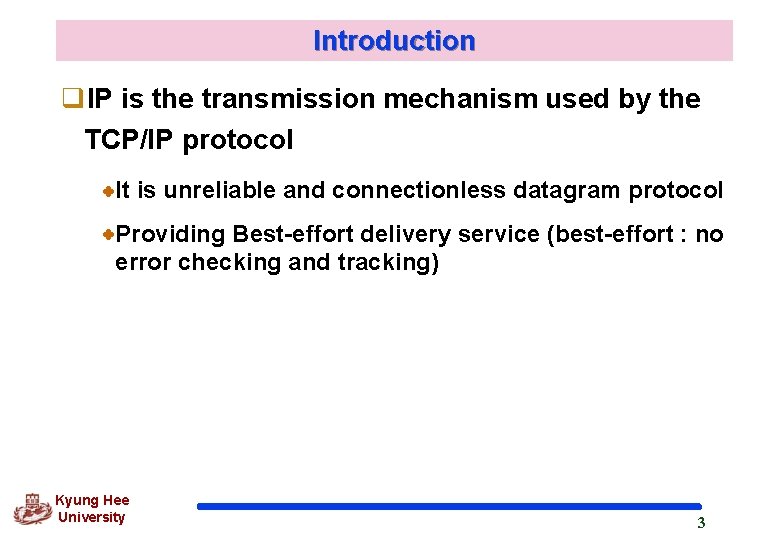
Position of IP in TCP/IP protocol suite Kyung Hee University 2

Introduction q. IP is the transmission mechanism used by the TCP/IP protocol It is unreliable and connectionless datagram protocol Providing Best-effort delivery service (best-effort : no error checking and tracking) Kyung Hee University 3

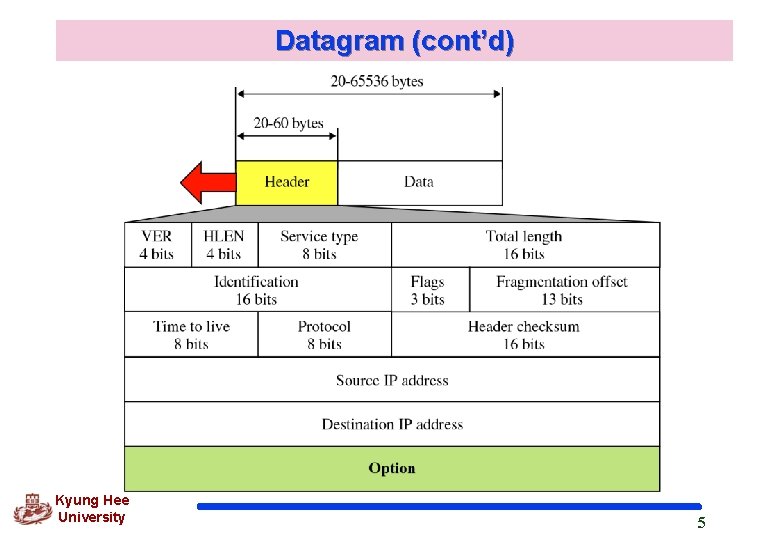
8. 1 Datagram q. Packets in the IP layer : called datagrams q. IP datagram format Variable-length packet consisting of header and data l Header – 20 ~ 60 bytes – Containing information that is essential for routing and delivery q. IP header Version (VER) : Version 4 or 6 (IPng) Header length (HLEN) : represented by in 4 byte words l Kyung Hee University Ex) if HLEN = 5, the real header length is 20 bytes 4

Datagram (cont’d) Kyung Hee University 5

Datagram (cont’d) Service Type l l Defining how the datagram should be handled by the routers Precedence : 3 bits – – – l Kyung Hee University Ex) a datagram for network management vs. optional information to a group of people At present, not used in version 4 service type : 4 bits (TOS bits) – l Defining the priority of the datagram in issues such as congestion With only one bit set at a time Remaining bit : not used 6

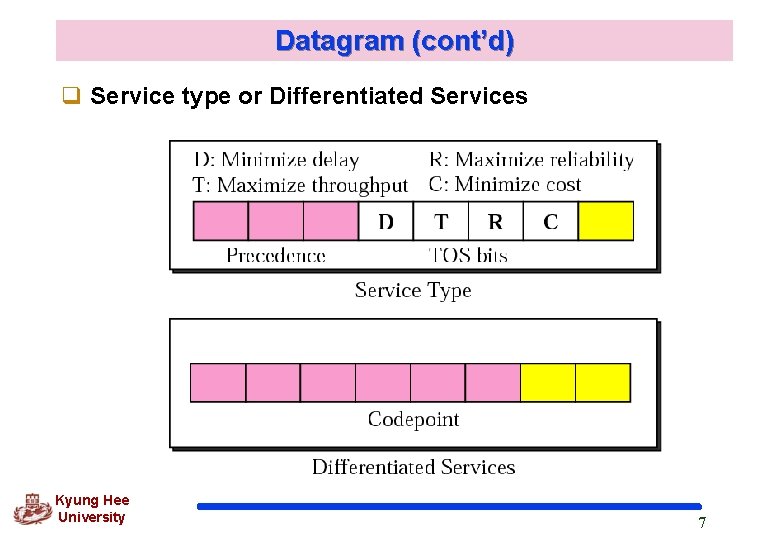
Datagram (cont’d) q Service type or Differentiated Services Kyung Hee University 7

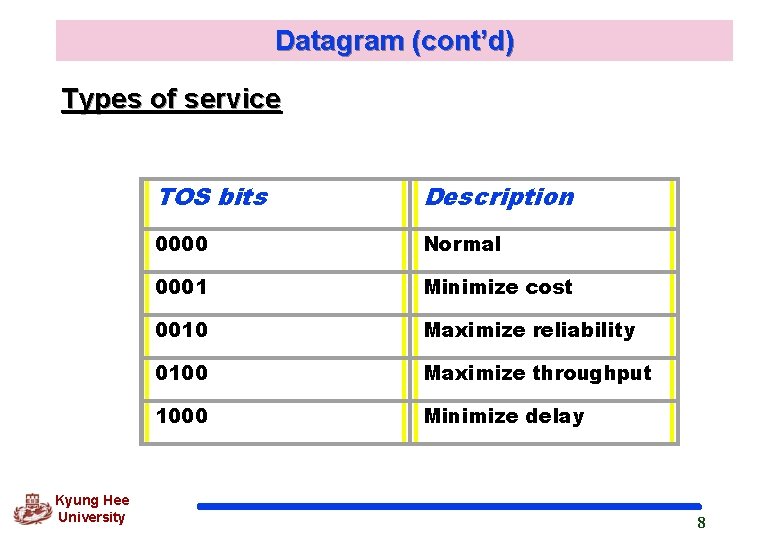
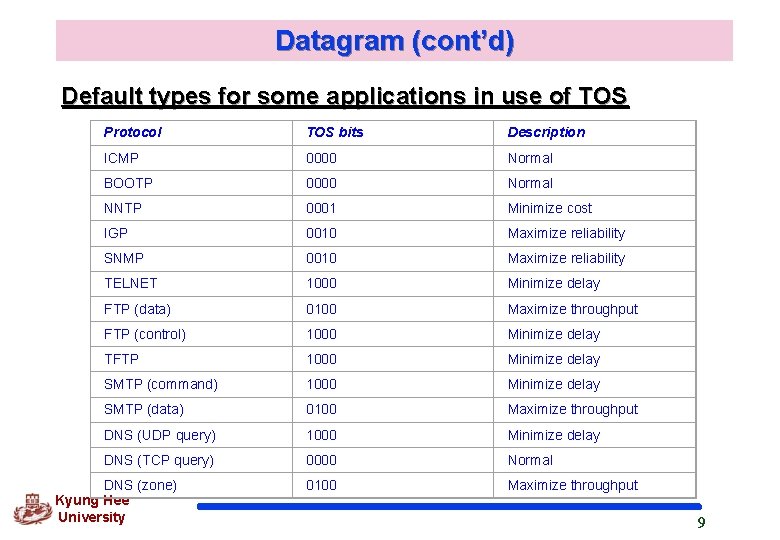
Datagram (cont’d) Types of service Kyung Hee University TOS bits Description 0000 Normal 0001 Minimize cost 0010 Maximize reliability 0100 Maximize throughput 1000 Minimize delay 8

Datagram (cont’d) Default types for some applications in use of TOS Protocol TOS bits Description ICMP 0000 Normal BOOTP 0000 Normal NNTP 0001 Minimize cost IGP 0010 Maximize reliability SNMP 0010 Maximize reliability TELNET 1000 Minimize delay FTP (data) 0100 Maximize throughput FTP (control) 1000 Minimize delay TFTP 1000 Minimize delay SMTP (command) 1000 Minimize delay SMTP (data) 0100 Maximize throughput DNS (UDP query) 1000 Minimize delay DNS (TCP query) 0000 Normal 0100 Maximize throughput DNS (zone) Kyung Hee University 9

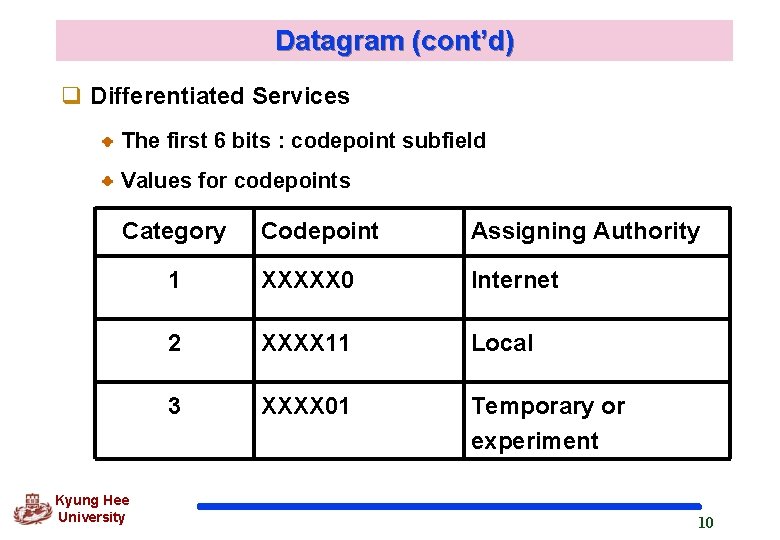
Datagram (cont’d) q Differentiated Services The first 6 bits : codepoint subfield Values for codepoints Category Kyung Hee University Codepoint Assigning Authority 1 XXXXX 0 Internet 2 XXXX 11 Local 3 XXXX 01 Temporary or experiment 10

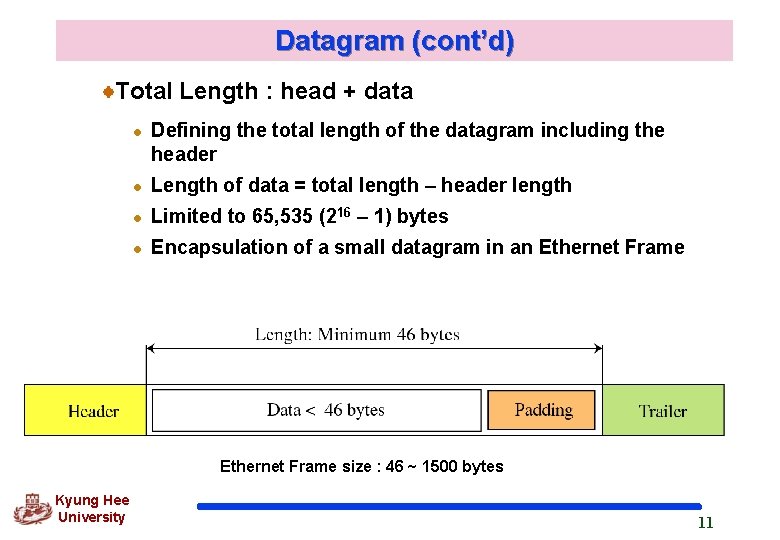
Datagram (cont’d) Total Length : head + data l Defining the total length of the datagram including the header l Length of data = total length – header length l Limited to 65, 535 (216 – 1) bytes l Encapsulation of a small datagram in an Ethernet Frame size : 46 ~ 1500 bytes Kyung Hee University 11

Datagram (cont’d) Flags : used in fragmentation Fragmentation offset : used in fragmentation Time to live l l l Kyung Hee University Used to control the maximum number of hops (routers) visited by the datagram If the value is Zero, the routers discarded If the source wants to confine the packet to the local network, it can store 1 in this field 12

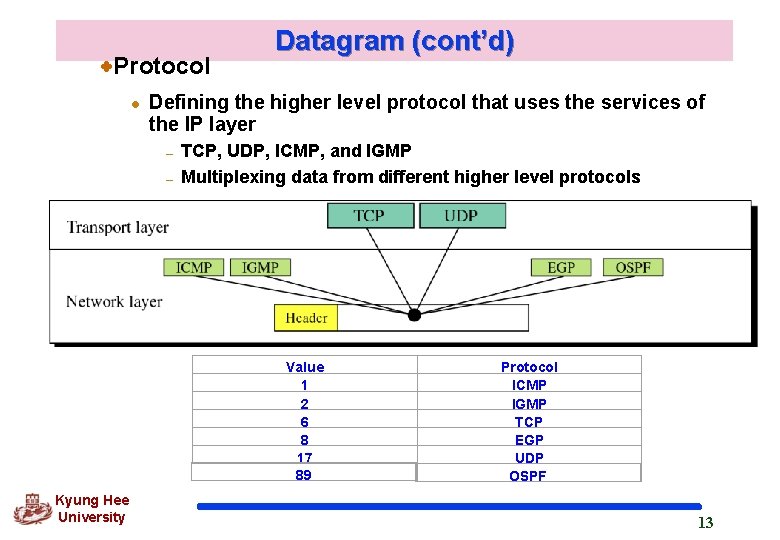
Protocol l Datagram (cont’d) Defining the higher level protocol that uses the services of the IP layer – – TCP, UDP, ICMP, and IGMP Multiplexing data from different higher level protocols Value 1 2 6 8 17 89 Kyung Hee University Protocol ICMP IGMP TCP EGP UDP OSPF 13

Datagram (cont’d) q Example 1 - An arriving IP packet : 01000010 àThe receiver discards the packet, Why ? - 2 x 4 bytes = 8 bytes : Minimum number of bytes in the header must be 20 Kyung Hee University 14

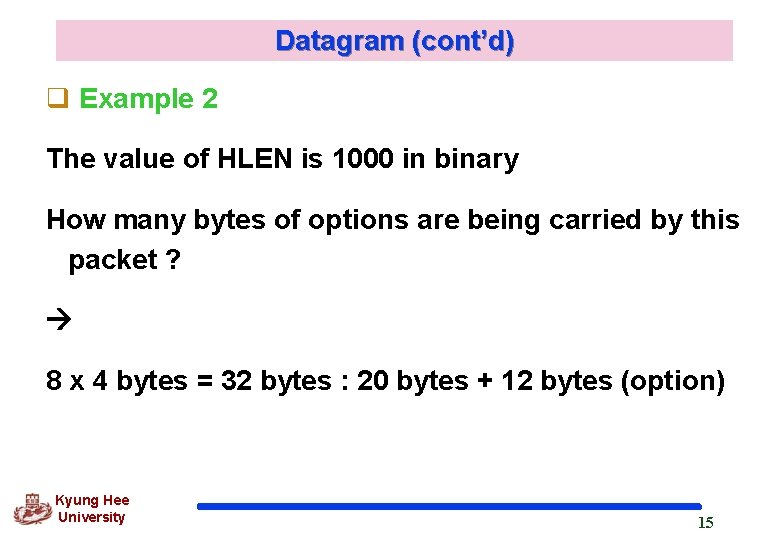
Datagram (cont’d) q Example 2 The value of HLEN is 1000 in binary How many bytes of options are being carried by this packet ? 8 x 4 bytes = 32 bytes : 20 bytes + 12 bytes (option) Kyung Hee University 15

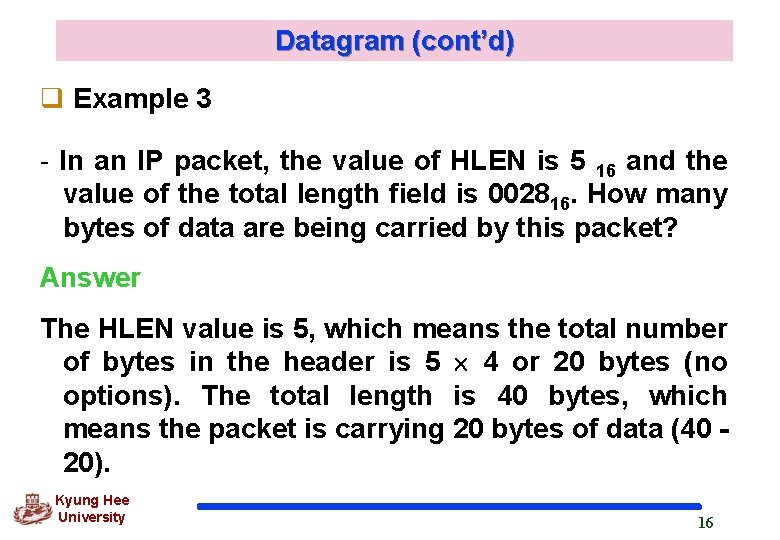
Datagram (cont’d) q Example 3 - In an IP packet, the value of HLEN is 5 16 and the value of the total length field is 002816. How many bytes of data are being carried by this packet? Answer The HLEN value is 5, which means the total number of bytes in the header is 5 4 or 20 bytes (no options). The total length is 40 bytes, which means the packet is carrying 20 bytes of data (40 20). Kyung Hee University 16

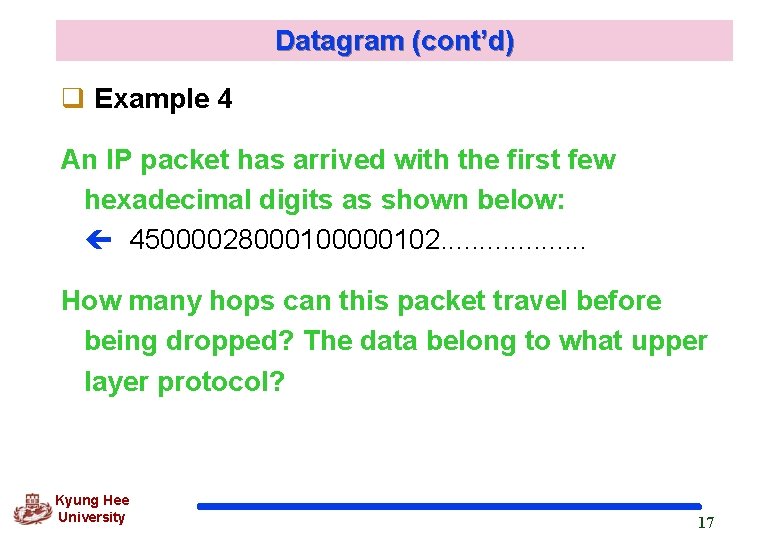
Datagram (cont’d) q Example 4 An IP packet has arrived with the first few hexadecimal digits as shown below: 45000028000100000102. . . . . How many hops can this packet travel before being dropped? The data belong to what upper layer protocol? Kyung Hee University 17

Datagram (cont’d) q Answer To find the time-to-live field, we should skip 8 bytes (16 hexadecimal digits). The time-to-live field is the ninth byte, which is 01. This means the packet can travel only one hop. The protocol field is the next byte (02), which means that the upper layer protocol is IGMP. Kyung Hee University 18

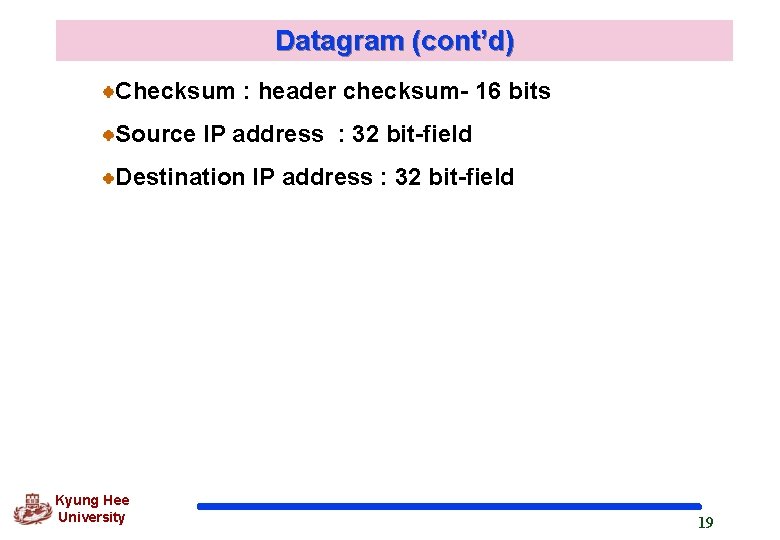
Datagram (cont’d) Checksum : header checksum- 16 bits Source IP address : 32 bit-field Destination IP address : 32 bit-field Kyung Hee University 19

8. 2 Fragmentation q. The format and size of the received frame depend on the protocol used by the physical network q. Ex) A router connecting Ethernet to token ring Kyung Hee University 20

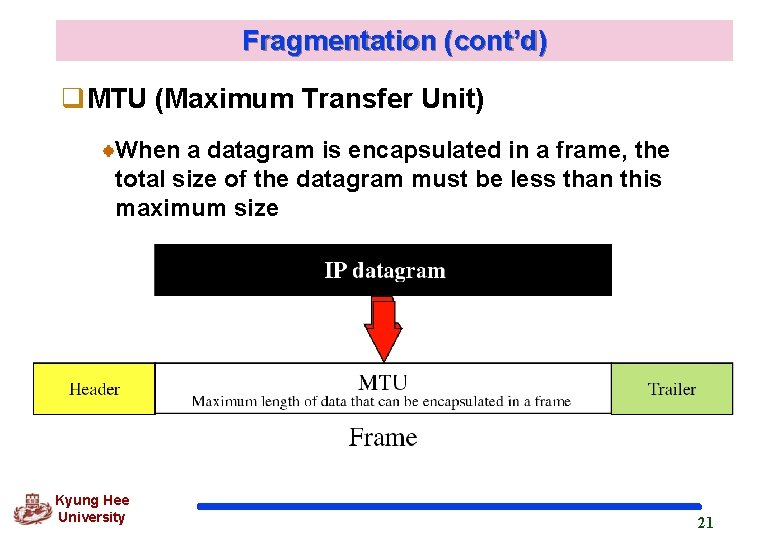
Fragmentation (cont’d) q. MTU (Maximum Transfer Unit) When a datagram is encapsulated in a frame, the total size of the datagram must be less than this maximum size Kyung Hee University 21

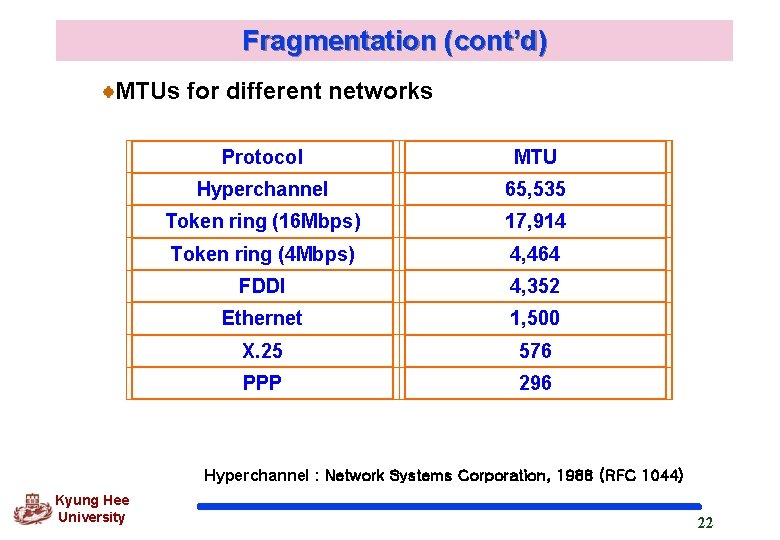
Fragmentation (cont’d) MTUs for different networks Protocol MTU Hyperchannel 65, 535 Token ring (16 Mbps) 17, 914 Token ring (4 Mbps) 4, 464 FDDI 4, 352 Ethernet 1, 500 X. 25 576 PPP 296 Hyperchannel : Network Systems Corporation, 1988 (RFC 1044) Kyung Hee University 22

Fragmentation (cont’d) The maximum length of the IP datagram equals to the largest MTU defined so far (65, 535 bytes) Therefore, for the other physical networks we must divide the datagram : fragmentation datagram that can be fragmented by the source host or any router in the path, but the reassembly of datagram is done by the destination When a datagram is fragmented, required parts of the header must be copied by all fragments. l Changing the values of the three fields : flags, fragmentation offset, and total length l The rest of fields must be copied l Checksum must be recalculated Kyung Hee University 23

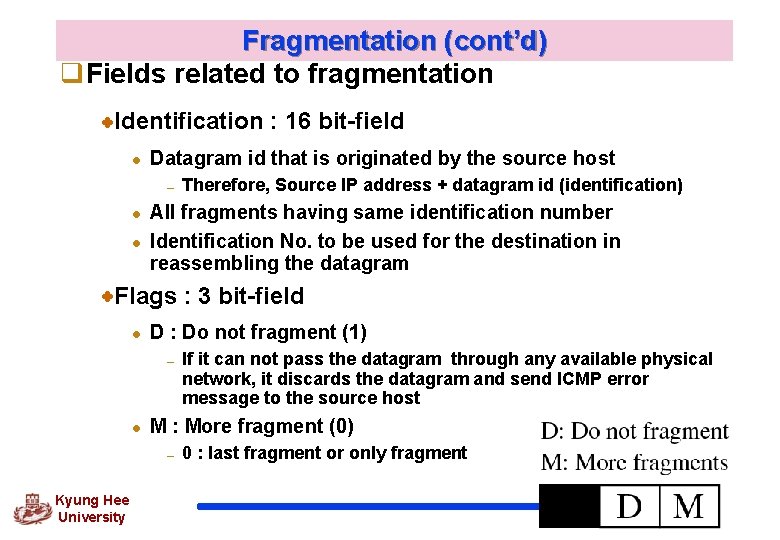
Fragmentation (cont’d) q. Fields related to fragmentation Identification : 16 bit-field l Datagram id that is originated by the source host – l l Therefore, Source IP address + datagram id (identification) All fragments having same identification number Identification No. to be used for the destination in reassembling the datagram Flags : 3 bit-field l D : Do not fragment (1) – l M : More fragment (0) – Kyung Hee University If it can not pass the datagram through any available physical network, it discards the datagram and send ICMP error message to the source host 0 : last fragment or only fragment 24

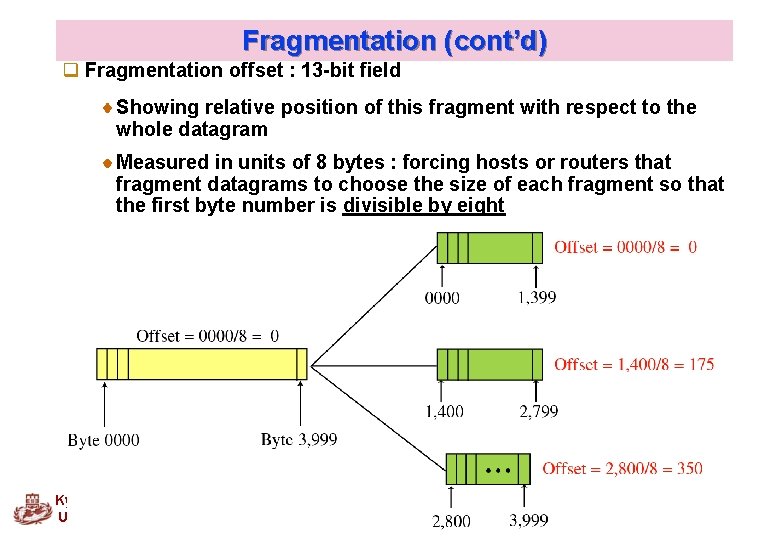
Fragmentation (cont’d) q Fragmentation offset : 13 -bit field Showing relative position of this fragment with respect to the whole datagram Measured in units of 8 bytes : forcing hosts or routers that fragment datagrams to choose the size of each fragment so that the first byte number is divisible by eight Kyung Hee University 25

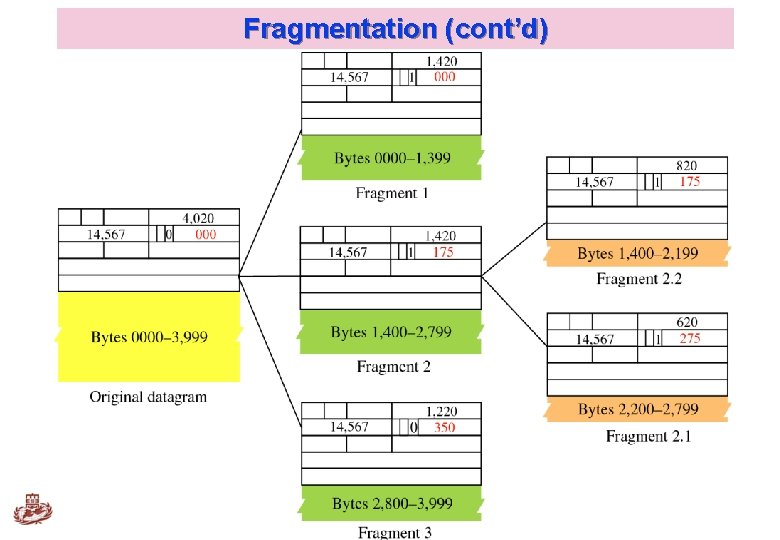
Fragmentation (cont’d) Kyung Hee University 26

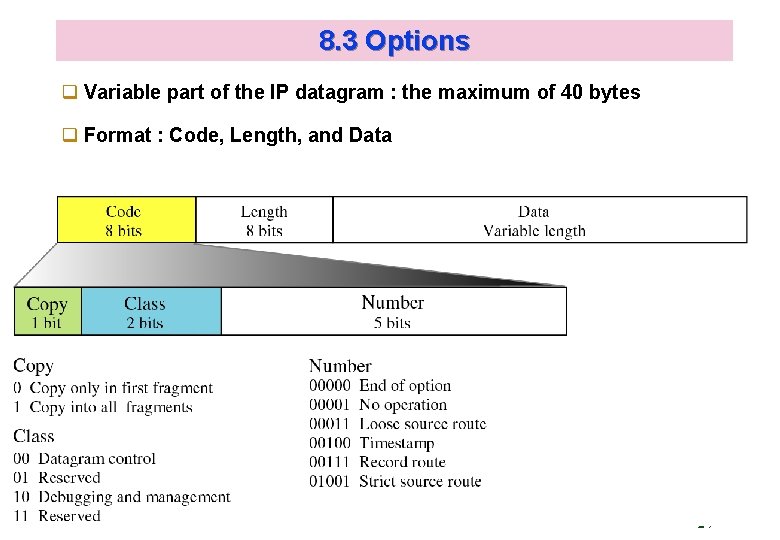
8. 3 Options q Variable part of the IP datagram : the maximum of 40 bytes q Format : Code, Length, and Data Kyung Hee University 27

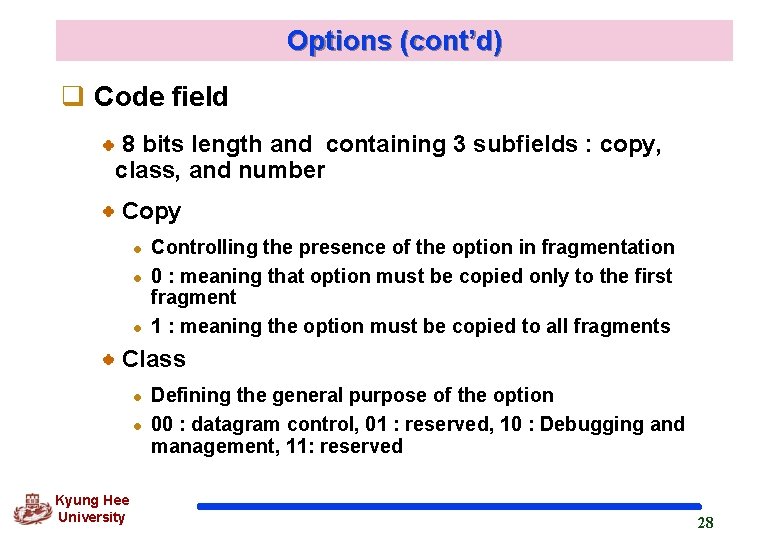
Options (cont’d) q Code field 8 bits length and containing 3 subfields : copy, class, and number Copy l l l Controlling the presence of the option in fragmentation 0 : meaning that option must be copied only to the first fragment 1 : meaning the option must be copied to all fragments Class l l Kyung Hee University Defining the general purpose of the option 00 : datagram control, 01 : reserved, 10 : Debugging and management, 11: reserved 28

Options (cont’d) Number l Defining the type of the option : only 6 options that are currently being used q Length defining the total length of the option including the code field and length field itself q Data containing the data that specific options require Kyung Hee University 29

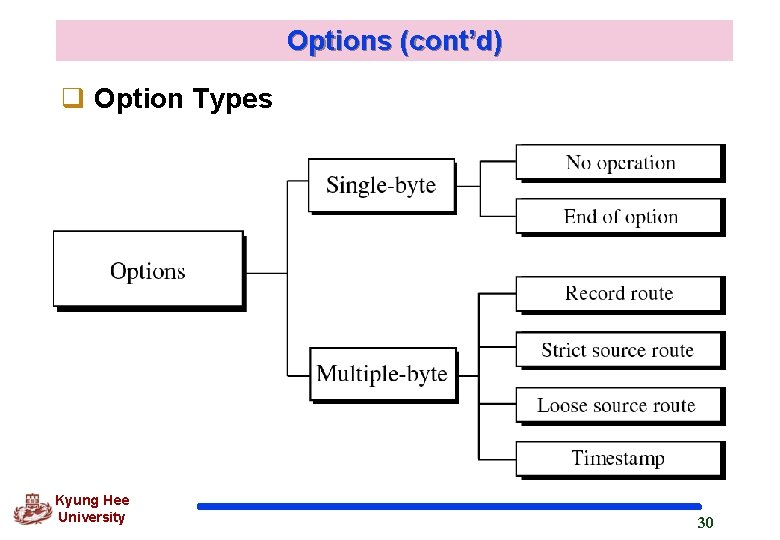
Options (cont’d) q Option Types Kyung Hee University 30

Options (cont’d) No Operation l Kyung Hee University one byte option used as a filler between options 31

Options (cont’d) q. End of Option one-byte option used for padding at the end of the option field used as the last option Kyung Hee University 32

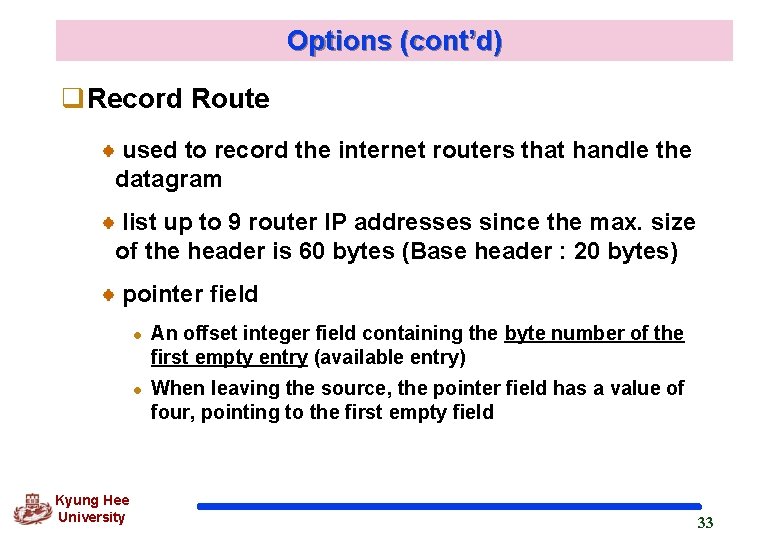
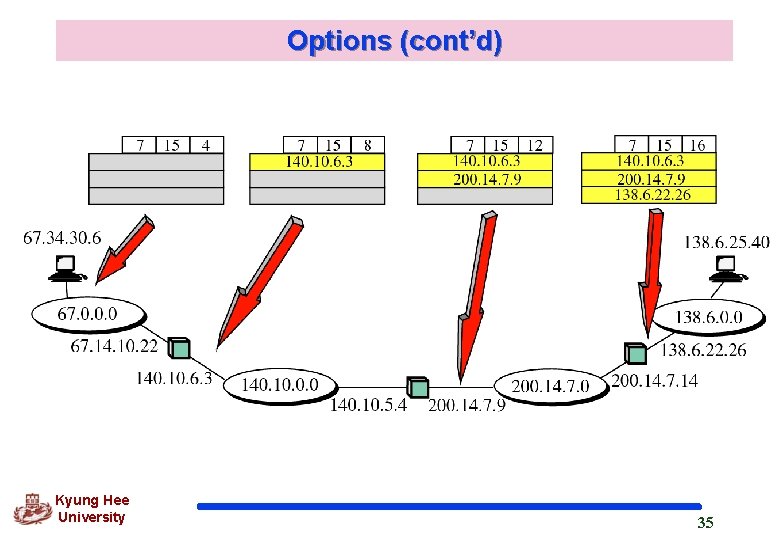
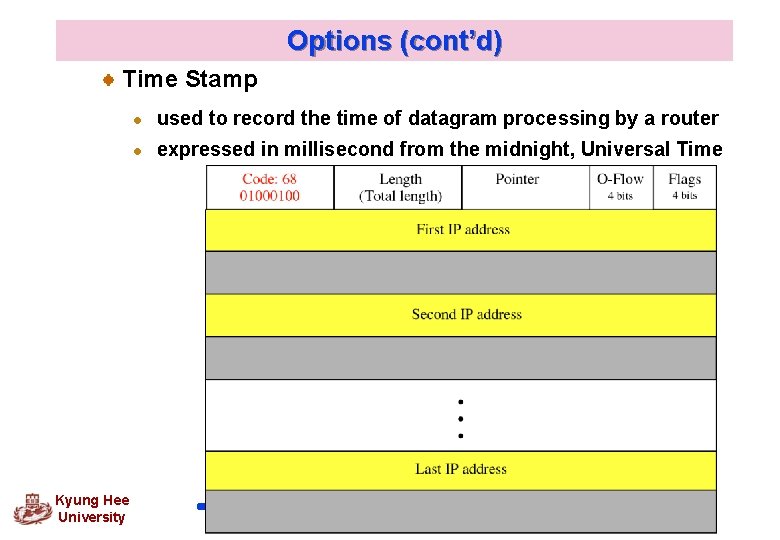
Options (cont’d) q. Record Route used to record the internet routers that handle the datagram list up to 9 router IP addresses since the max. size of the header is 60 bytes (Base header : 20 bytes) pointer field l l Kyung Hee University An offset integer field containing the byte number of the first empty entry (available entry) When leaving the source, the pointer field has a value of four, pointing to the first empty field 33

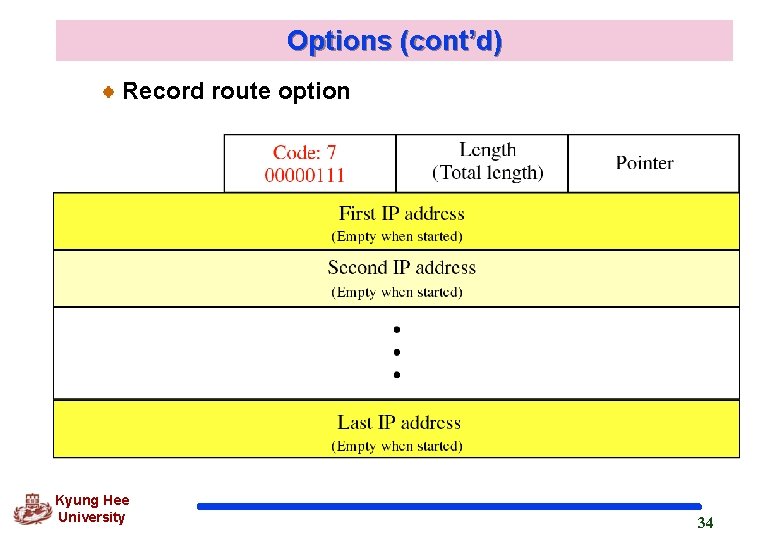
Options (cont’d) Record route option Kyung Hee University 34

Options (cont’d) Kyung Hee University 35

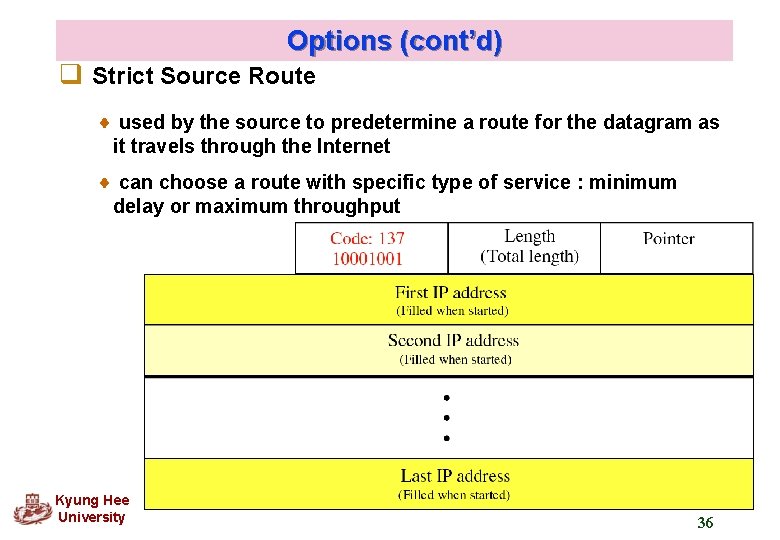
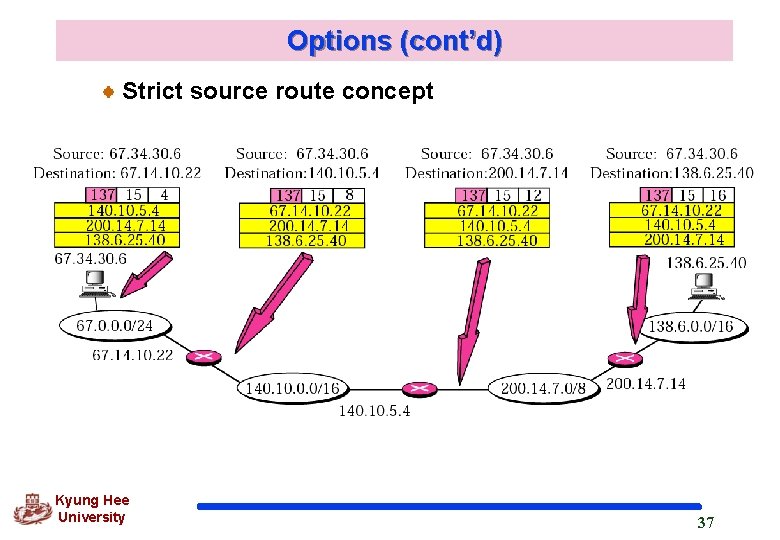
Options (cont’d) q Strict Source Route used by the source to predetermine a route for the datagram as it travels through the Internet can choose a route with specific type of service : minimum delay or maximum throughput Kyung Hee University 36

Options (cont’d) Strict source route concept Kyung Hee University 37

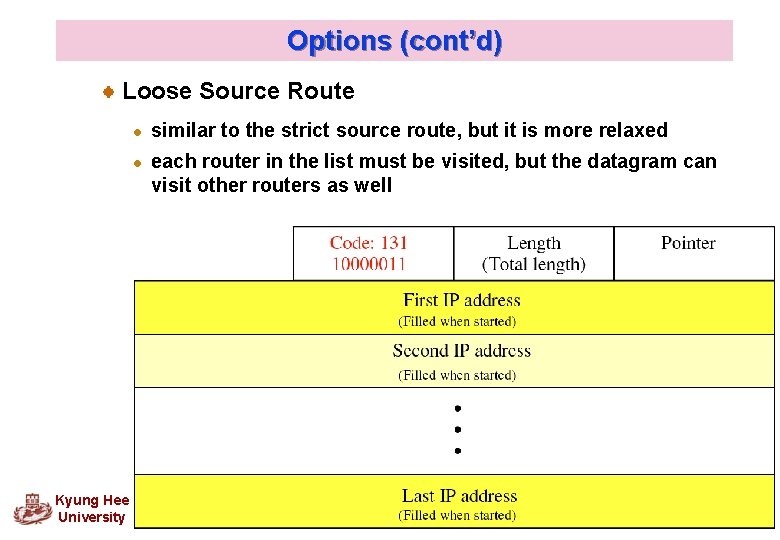
Options (cont’d) Loose Source Route l l Kyung Hee University similar to the strict source route, but it is more relaxed each router in the list must be visited, but the datagram can visit other routers as well 38

Options (cont’d) Time Stamp Kyung Hee University l used to record the time of datagram processing by a router l expressed in millisecond from the midnight, Universal Time 39

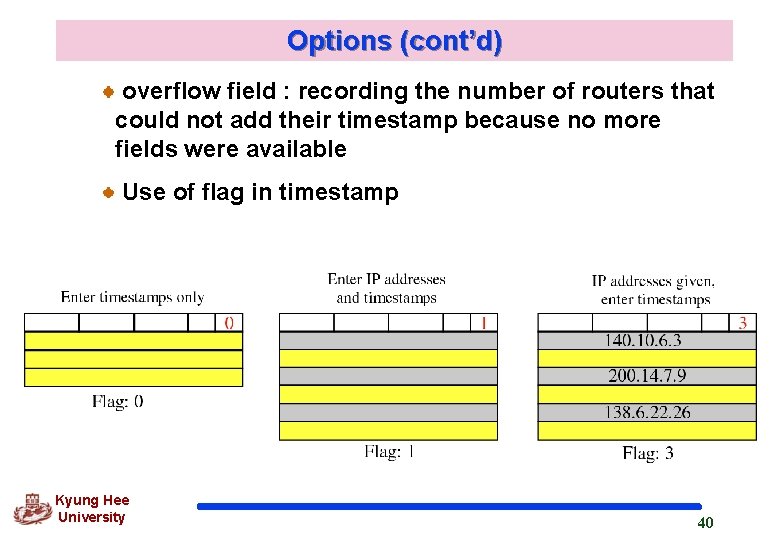
Options (cont’d) overflow field : recording the number of routers that could not add their timestamp because no more fields were available Use of flag in timestamp Kyung Hee University 40

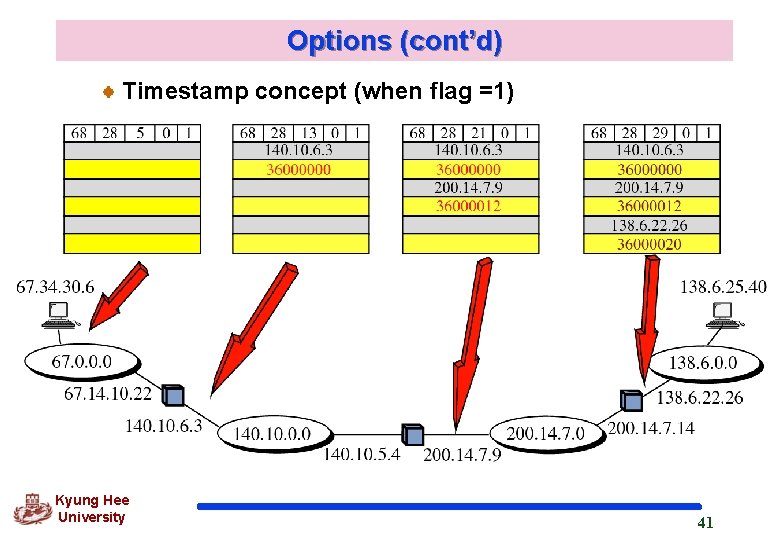
Options (cont’d) Timestamp concept (when flag =1) Kyung Hee University 41

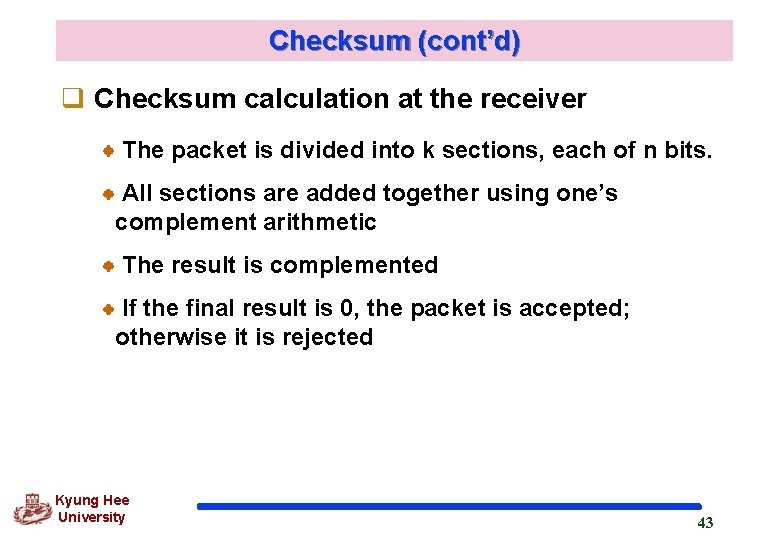
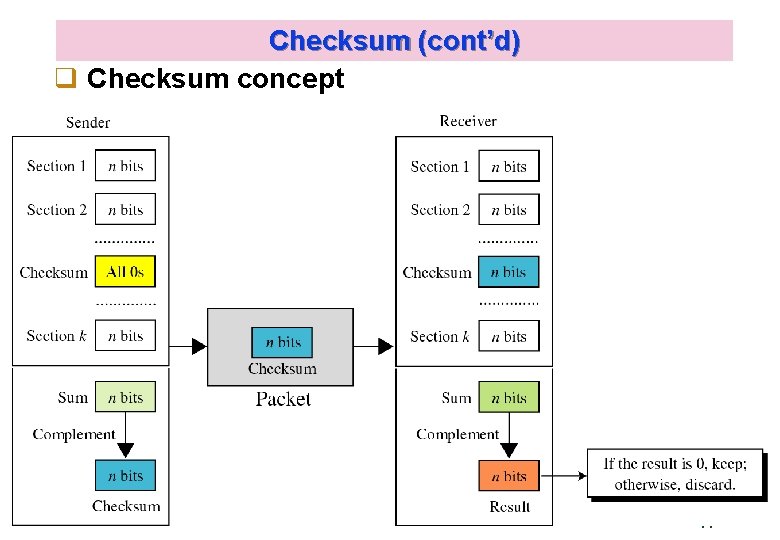
8. 4 Checksum q Error detection method used by most TCP/IP protocols q Checksum calculation at the sender The packet is divided into k sections, each of n bits ( n is usually 16) All sections are added together using one’s complement arithmetic The final result is complemented to make the checksum Kyung Hee University 42

Checksum (cont’d) q Checksum calculation at the receiver The packet is divided into k sections, each of n bits. All sections are added together using one’s complement arithmetic The result is complemented If the final result is 0, the packet is accepted; otherwise it is rejected Kyung Hee University 43

Checksum (cont’d) q Checksum concept Kyung Hee University 44

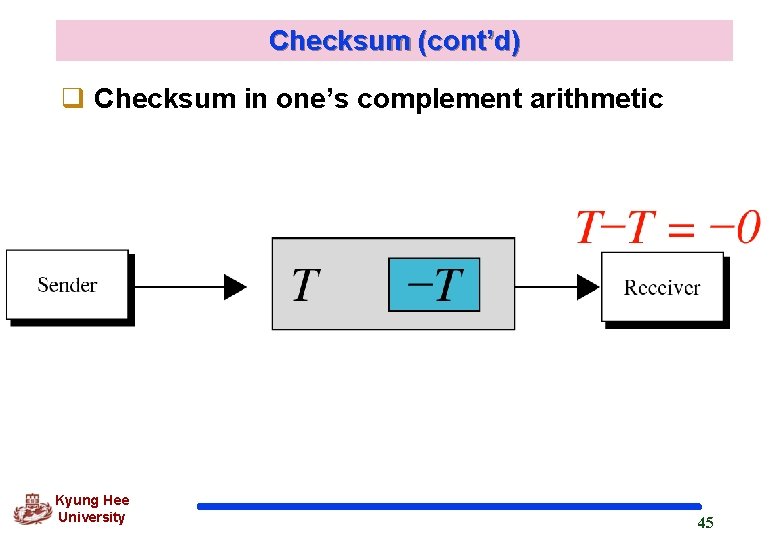
Checksum (cont’d) q Checksum in one’s complement arithmetic Kyung Hee University 45

Checksum (cont’d) q Checksum in the IP Packet covering only the header, not the data l l l Kyung Hee University all higher level protocols that encapsulate data in the IP datagram have a checksum field that covers the whole packet the header changes with each visited router, but data does not. So the checksum includes only the part which has changed if each router must recalculates the checksum, it is needed to have the more processing time for each router 46

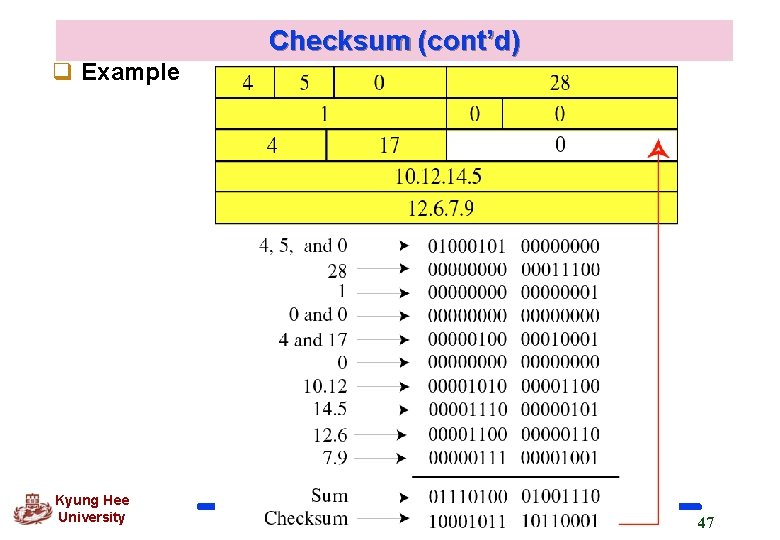
Checksum (cont’d) q Example Kyung Hee University 47

8. 5 IP Package q IP package : 8 components Header-adding module Processing module Routing module fragmentation module reassembly module routing table MTU table reassembly table Kyung Hee University 48

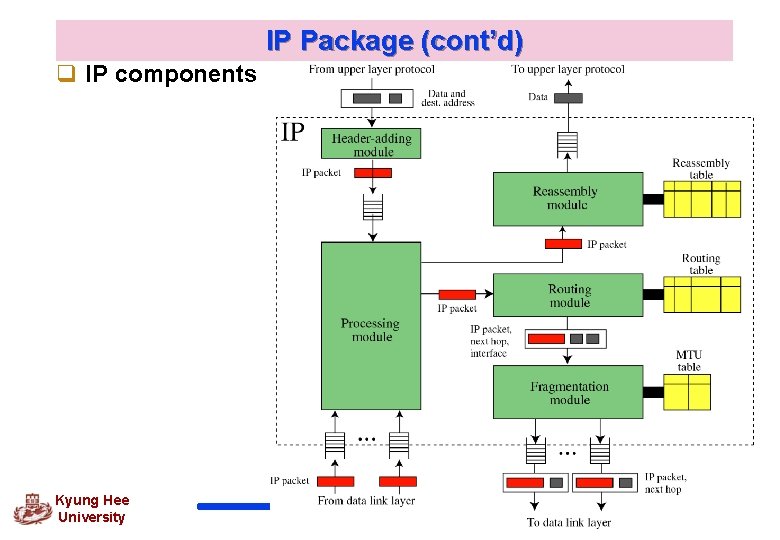
IP Package (cont’d) q IP components Kyung Hee University 49

IP Package(cont’d) q The operation of IP package receiving an IP packet, either from the data link layer or a higher level protocol if the packet comes from a upper layer protocol, it should be delivered to the data link layer if the packet comes from the data link layer, forwarding to data link or a upper layer ( the destination is same as the station address) Kyung Hee University 50

IP Package (cont’d) q Header-adding Module Receive : data, destination address 1. Encapsulate the data in an IP datagram 2. Calculate the checksum and insert it in the checksum field 3. Send the data to the corresponding input queue 4. Return Kyung Hee University 51

IP Package (cont’d) q Processing Module 1. Remove one datagram from one of the input queues 2. if (destination address is 127. X. Y. Z or matches one of the local addresses) 1. Send datagram to the reassembly module. 2. Return 3. if (machine is a router) 1. Decrement TTL 4. if (TTL less than or equal to zero) 1. Discard the datagram 2. Send an ICMP error message 3. Return 5. Send the datagram to the routing module 6. Return Kyung Hee University 52

IP Package (cont’d) q Queues Input queues and output queues q Routing table used by the routing module to determine the nexthop address of the packet q Routing module receiving an IP packet from the processing module sending the packet with the information to the fragmentation module Kyung Hee University 53

IP Package (cont’d) q MTU Table to find the maximum transfer unit of a particular interface. Kyung Hee University 54

IP Package (cont’d) q Fragmentation Module Receive : an IP packet from routing module 1. Extract the size of the datagram 2. if (size > MTU of the corresponding network) 1. If (D (do not fragment) bit is set 1. 2. 3. 2. Discard the datagram Send an ICMP error message Return Else 1. 2. 3. 4. 5. 6. Calculate the maximum size Divide the datagram into fragments Add header to each fragment Add required options to each fragment Send the datagram Return 3. Else Kyung Hee University 1. Send the datagram 4. Return 55

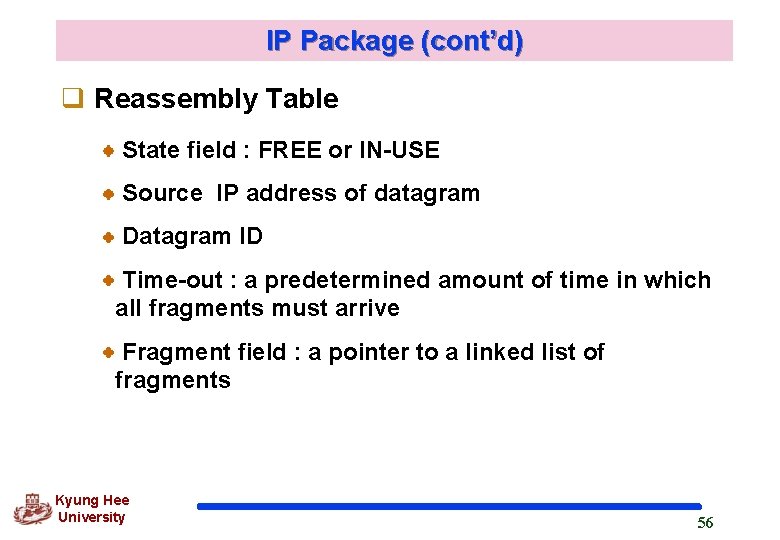
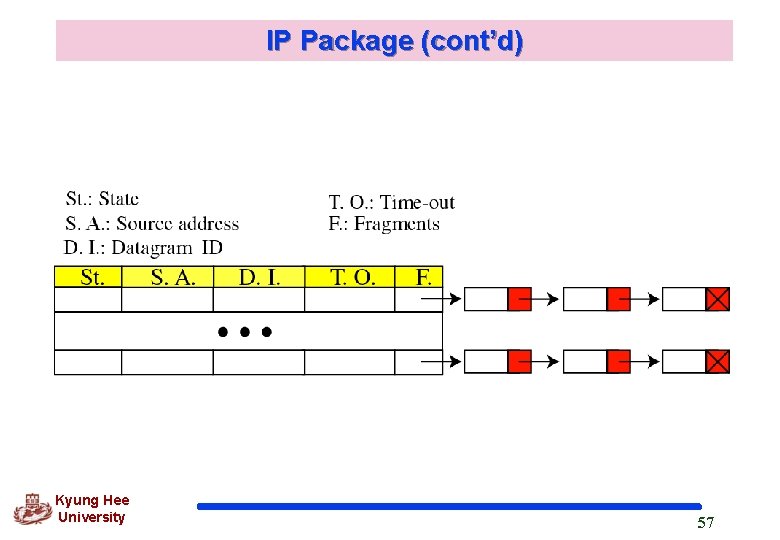
IP Package (cont’d) q Reassembly Table State field : FREE or IN-USE Source IP address of datagram Datagram ID Time-out : a predetermined amount of time in which all fragments must arrive Fragment field : a pointer to a linked list of fragments Kyung Hee University 56

IP Package (cont’d) Kyung Hee University 57

IP Package (cont’d) q Reassembly Module Receive : an IP packet from the processing module 1. If (offset value is zero and the M bit is 0) 1. Send the datagram to the appropriate queue 2. Return 2. Search the reassembly table for the corresponding entry 3. If (not found) 1. Create a new entry Kyung Hee University 58

IP Package (cont’d) 4. Insert list 1. if (all fragments have arrived) 1. 2. 3. 2. the fragment at the appropriate place in the linked Reassemble the fragments Deliver the datagram to the corresponding upper layer protocol Return Else 1. 2. Check the time-out if (time-out expired) 1. 2. Discard all fragment Send an ICMP error message 5. Return Kyung Hee University 59

Summary (1) q IP is an unreliable connectionless protocol responsible for sourceto-destination delivery. q Packets in the IP layer are called datagrams q A datagram consists of a header (20 to 60 bytes) and data. q The IP header contains the following information: version number, header length, differentiated services, datagram length, identification number, fragmentation flags, fragmentation offset, time to live, protocol, checksum, source address, destination address, and options. q The maximum length of a datagram is 65, 535 bytes. q The MTU is the maximum number of bytes that a data link protocol can encapsulate. MTUs vary from protocol to protocol. Kyung Hee University 60

Summary (2) q. Fragmentation is the division of a datagram into smaller units to accommodate the MTU of a data link protocol. q. The fields in the IP header that relate to fragmentation are the identification number, the fragmentation flags, and the fragmentation offset. q. The IP datagram header consists of a fixed, 20 -byte section and a variable options section with a maximum of 40 bytes. q. The options section of the IP header is used for network testing and debugging. q. The options header contains the following information: a code field that identifies the option, option length, and the specific data. Kyung Hee University 61

Summary (3) q The six IP options each have a specific function. They are as follows: filler between options for alignment purposes, padding, recording the route the datagram takes, selection of a mandatory route by the sender, selection of certain routers that must be visited, and recording of processing times at routers. q The ping and traceroute utilities in UNIX can be used to implement some of the IP options. q The error detection method used by IP is the checksum. q The checksum uses one's complement arithmetic to add equal-size sections of the IP header. The complemented result is stored in the checksum field. The receiver also uses one's complement arithmetic to check the header. q An IP package can consist of the following: a header-adding module, a processing module, a forwarding module, a fragmentation module, a reassembly module, a routing table, an MTU table, and a reassembly table. Kyung Hee University 62