Azure Information Protection Gregor uster Microsoft Slovenija Agenda
















- Slides: 30

Azure Information Protection Gregor Šuster Microsoft Slovenija

Agenda Reach us with #ntk 17

Providing clarity and consistency for the protection of personal data The General Data Protection Regulation (GDPR) imposes new rules on organizations that offer goods and services to people in the European Union (EU), or that collect and analyze data tied to EU residents, no matter where they are located. Enhanced personal privacy rights Increased duty for protecting data Mandatory breach reporting Significant penalties for non-compliance Reach us with #ntk 17

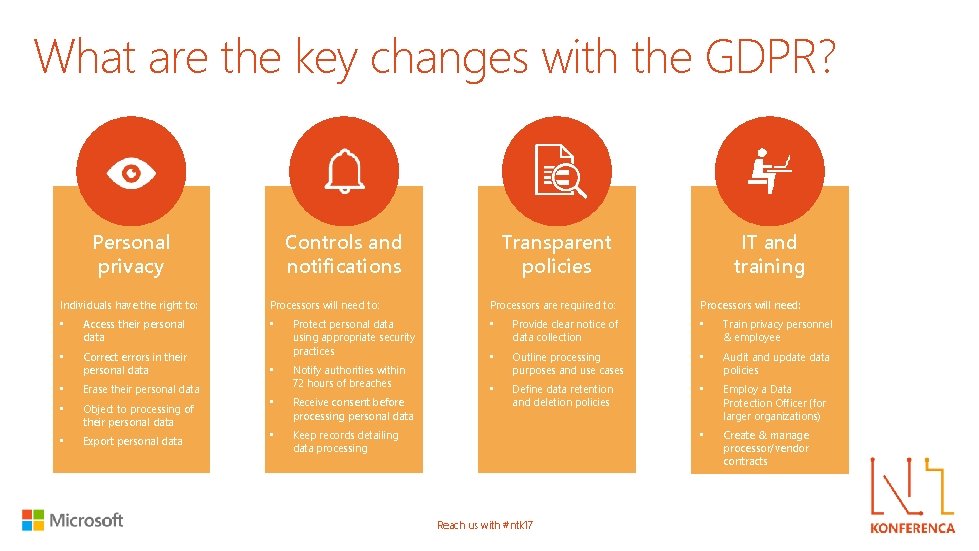
What are the key changes with the GDPR? Controls and notifications Personal privacy Individuals have the right to: • Access their personal data • Correct errors in their personal data • Erase their personal data • Object to processing of their personal data • Export personal data Processors will need to: • Protect personal data using appropriate security practices • Notify authorities within 72 hours of breaches • Receive consent before processing personal data • Keep records detailing data processing Transparent policies Processors are required to: IT and training Processors will need: • Provide clear notice of data collection • Train privacy personnel & employee • Outline processing purposes and use cases • Audit and update data policies • Define data retention and deletion policies • Employ a Data Protection Officer (for larger organizations) • Create & manage processor/vendor contracts Reach us with #ntk 17

What does this mean for my data? Protecting customer privacy with GDPR Reach us with #ntk 17

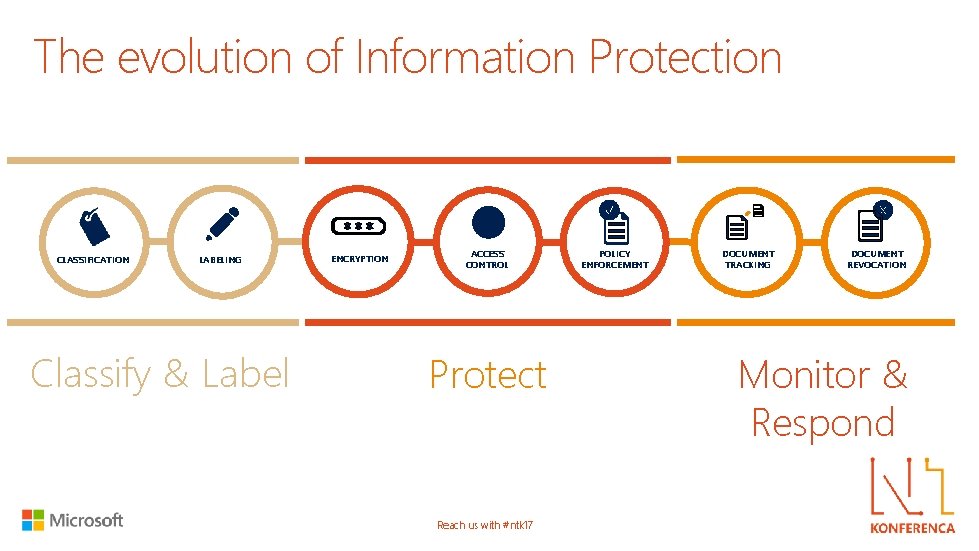
The evolution of Information Protection CLASSIFICATION LABELING Classify & Label ENCRYPTION ACCESS CONTROL Protect Reach us with #ntk 17 POLICY ENFORCEMENT DOCUMENT TRACKING DOCUMENT REVOCATION Monitor & Respond

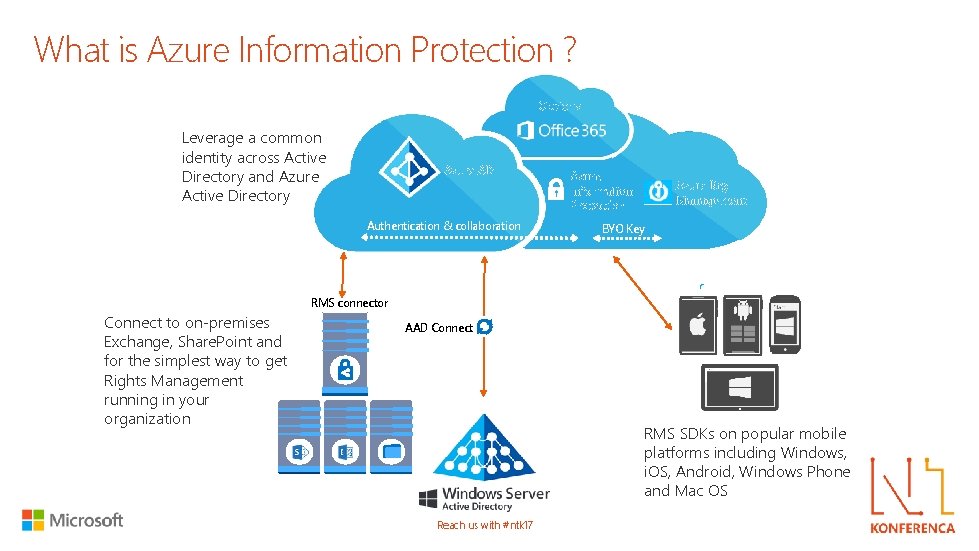
What is Azure Information Protection ? Optional Leverage a common identity across Active Directory and Azure Active Directory Azure AD Authentication & collaboration Azure Information Protection Azure Key Management BYO Key RMS connector Connect to on-premises Exchange, Share. Point and for the simplest way to get Rights Management running in your organization AAD Connect RMS SDKs on popular mobile platforms including Windows, i. OS, Android, Windows Phone and Mac OS Reach us with #ntk 17

Deployment phases for AIP Reach us with #ntk 17

Phase 1: Basic Classification Reach us with #ntk 17

Basic Classification - Considerations Reach us with #ntk 17


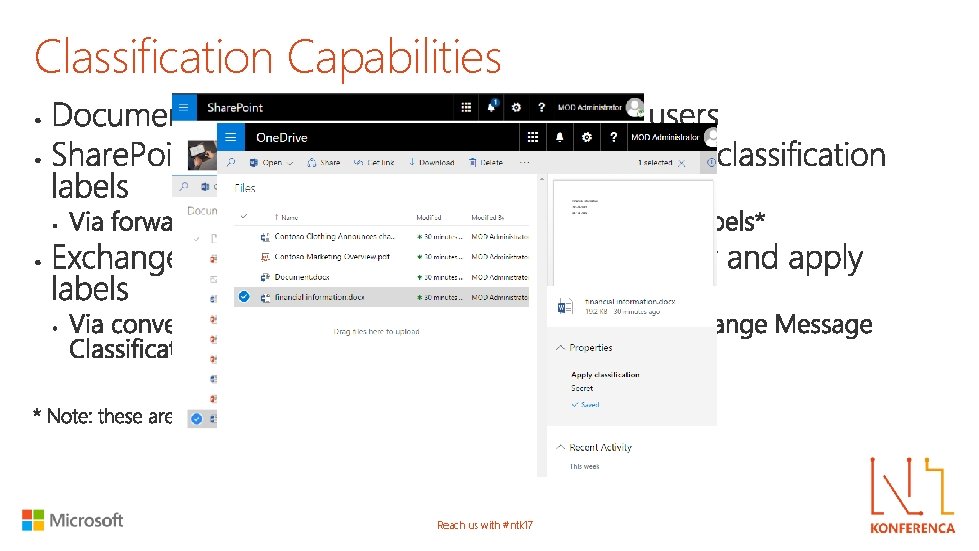
Classification Capabilities Reach us with #ntk 17

Designing a classification taxonomy Reach us with #ntk 17

Classification Best Practices Reach us with #ntk 17

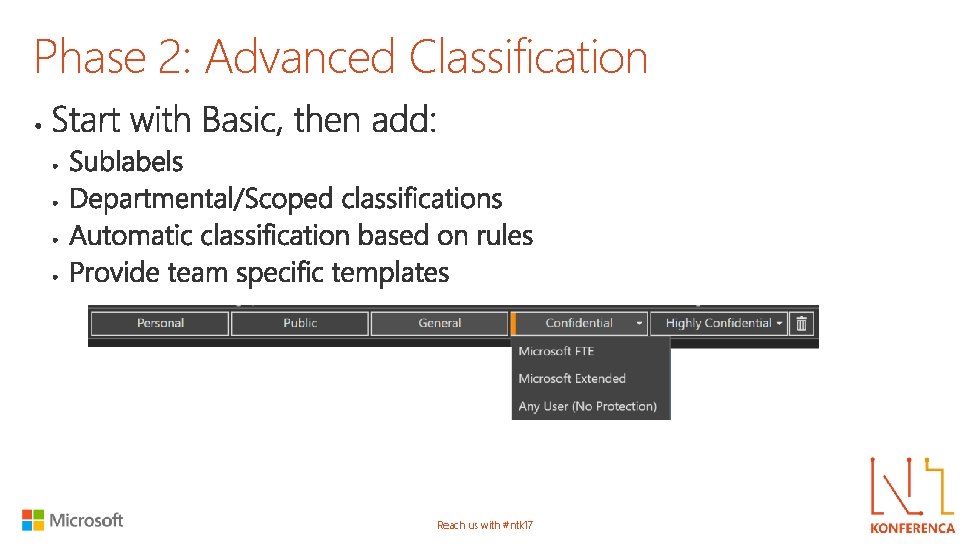
Phase 2: Advanced Classification Reach us with #ntk 17

Scoped labels Reach us with #ntk 17

+Automation Reach us with #ntk 17

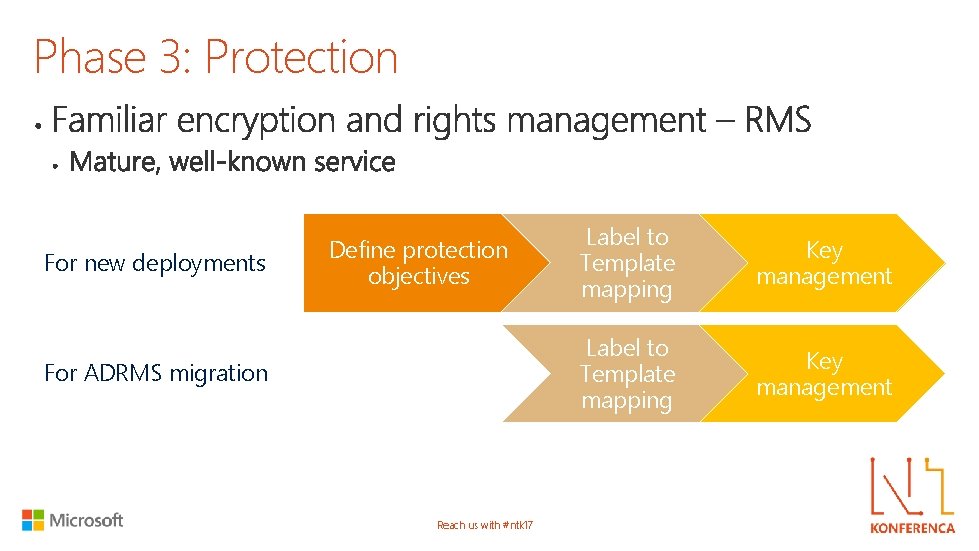
Phase 3: Protection For new deployments Define protection objectives For ADRMS migration Reach us with #ntk 17 Label to Template mapping Key management

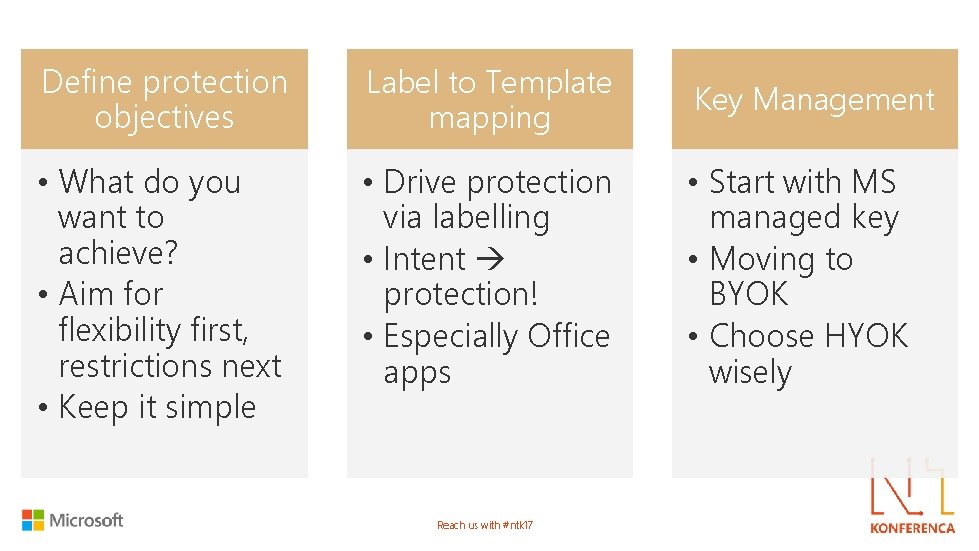
Define protection objectives Label to Template mapping Key Management • What do you want to achieve? • Aim for flexibility first, restrictions next • Keep it simple • Drive protection via labelling • Intent protection! • Especially Office apps • Start with MS managed key • Moving to BYOK • Choose HYOK wisely Reach us with #ntk 17

Key Management Reach us with #ntk 17

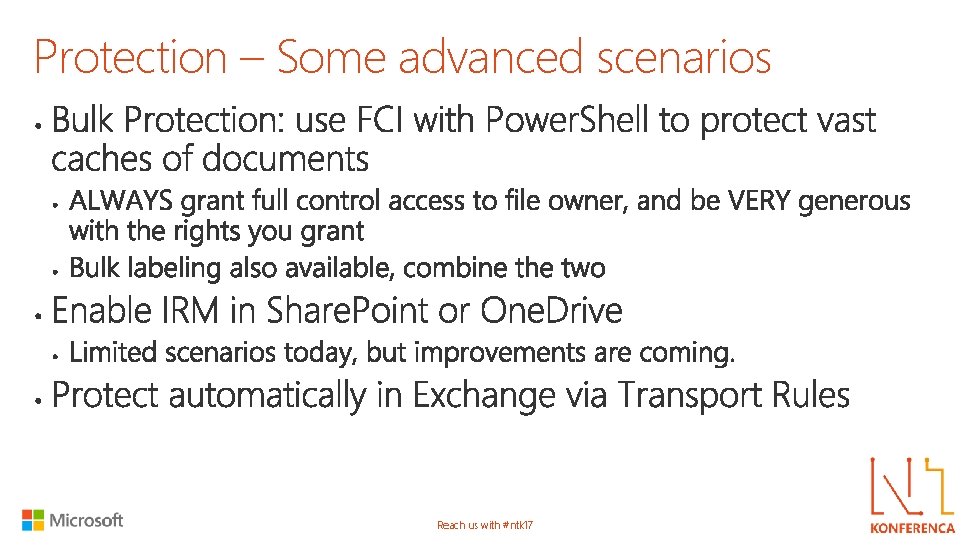
Protection – Some advanced scenarios Reach us with #ntk 17

Phase 4: Reporting/Monitoring Reach us with #ntk 17

End-user doc tracking Reach us with #ntk 17

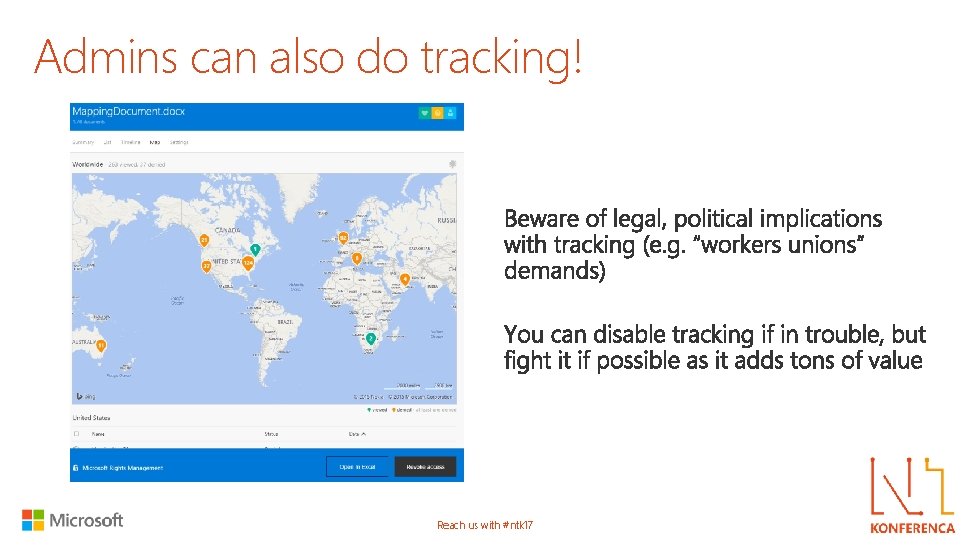
Admins can also do tracking! Reach us with #ntk 17

Log-based reporting Reach us with #ntk 17

Phase 5: Secure Collaboration Reach us with #ntk 17

Phase 6: Integration with other systems Reach us with #ntk 17

Demo in 15 minutes… https: //www. microsoft. com/en-us/cloudplatform/enterprise-mobility-security-trial Reach us with #ntk 17

Additional questions? Reach us with #ntk 17

 Think quality
Think quality Ks uster
Ks uster Azure erdrich
Azure erdrich Azure secure enclave
Azure secure enclave Data retention
Data retention Agenda sistemica y agenda institucional
Agenda sistemica y agenda institucional Program zedinjene slovenije
Program zedinjene slovenije Slovenske dežele v okviru sosednjih držav
Slovenske dežele v okviru sosednjih držav Rokodelstvo art & craft slovenija
Rokodelstvo art & craft slovenija Full members
Full members Budicool slovenija
Budicool slovenija Dsv kranj
Dsv kranj Uniforme medicinske sestre
Uniforme medicinske sestre Sava trelleborg
Sava trelleborg Radio slovenija
Radio slovenija Brp slovenija
Brp slovenija Cobiss slovenija
Cobiss slovenija Slovenija
Slovenija Slovenija
Slovenija Geton slovenija
Geton slovenija Republika slovenija ministrstvo za finance
Republika slovenija ministrstvo za finance Ibclc slovenija
Ibclc slovenija Digitalna slovenija
Digitalna slovenija Slovenija turizam
Slovenija turizam Sava osiguranje slovenija
Sava osiguranje slovenija Veeam cloud connect for enterprise
Veeam cloud connect for enterprise Practical threat analysis
Practical threat analysis Private cloud microsoft
Private cloud microsoft Case study on microsoft azure in cloud computing
Case study on microsoft azure in cloud computing Microsoft azure olap
Microsoft azure olap Azure support plan
Azure support plan