Armed Forces Communications Electronics Association AFCEA n AFCEA















- Slides: 23

Armed Forces Communications & Electronics Association (AFCEA) n AFCEA International Non-profit membership association n Serves the military, government, industry, and academia n Advances professional knowledge and relationships in the fields of communications, IT, intelligence, and global security. n n AFCEA Activities n n n SIGNAL Magazine (Monthly) SIGNAL Connections (Online Newsletter) Educational Foundation Professional Development Center AFCEA Sponsored Conferences/Symposia AFCEA Participants 20, 000 individual members n 11, 000 corporate associates n 1, 400 corporate members n

Integrity - Service - Excellence Operationalizing Network Defense (or, “The Awakening of One Comm Guy”) Colonel Mark Kross Commander 26 th Network Operations Group Overall Classification: UNCLASSIFIED

Overview n n n n Importance of the Network Net-D Primer Net-D as a Recognized Operation The Big Evolution People Systems Intel Planning

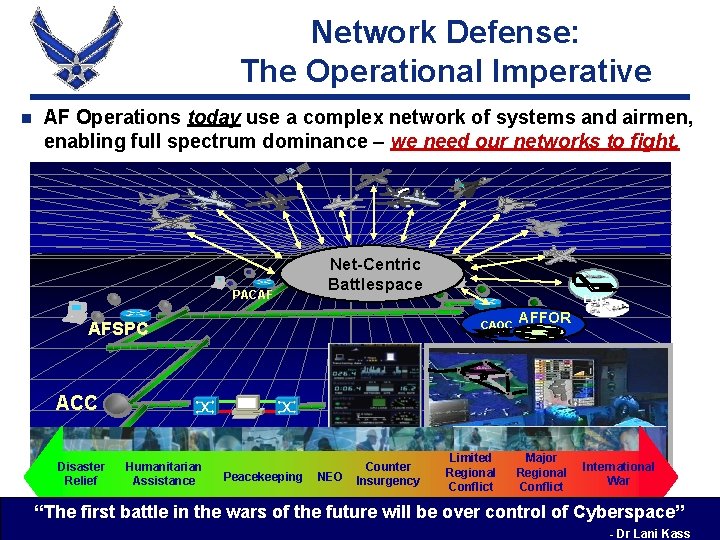
Network Defense: The Operational Imperative n AF Operations today use a complex network of systems and airmen, enabling full spectrum dominance – we need our networks to fight. PACAF Net-Centric Battlespace NCCAFFOR AFSPC EOC CAOC ACC Disaster Humanitarian PENTAGON Relief Assistance Peacekeeping NEO Counter Insurgency Limited Regional Conflict Major Regional Conflict International War “The first battle in the wars of the future will be over control of Cyberspace” - Dr Lani Kass

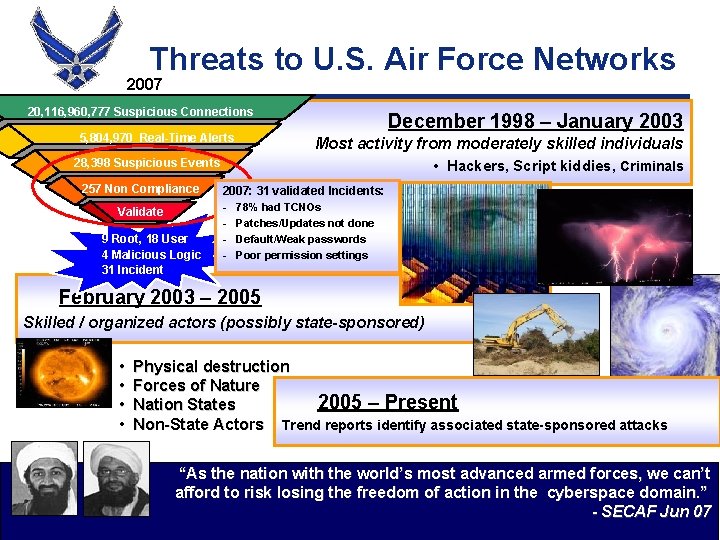
Threats to U. S. Air Force Networks 2007 20, 116, 960, 777 Suspicious Connections 5, 804, 970 Real-Time Alerts 28, 398 Suspicious Events 257 Non Compliance Validate 9 Root, 18 User 4 Malicious Logic 31 Incident December 1998 – January 2003 Most activity from moderately skilled individuals • Hackers, Script kiddies, Criminals 2007: 31 validated Incidents: - 78% had TCNOs - Patches/Updates not done - Default/Weak passwords - Poor permission settings February 2003 – 2005 Skilled / organized actors (possibly state-sponsored) • • Physical destruction Forces of Nature 2005 – Present Nation States Non-State Actors Trend reports identify associated state-sponsored attacks “As the nation with the world’s most advanced armed forces, we can’t afford to risk losing the freedom of action in the cyberspace domain. ” - SECAF Jun 07

Cyberspace is a Battlespace… We’re at WAR! Hundreds of Jihadi Web Sites and Internet Hosts, Thousands of Individual email Accounts PENTAGON, 11 Sep 2001: Adversary Used: Internet for Recruitment International & Cell Comms for Coord; Training on Simulators

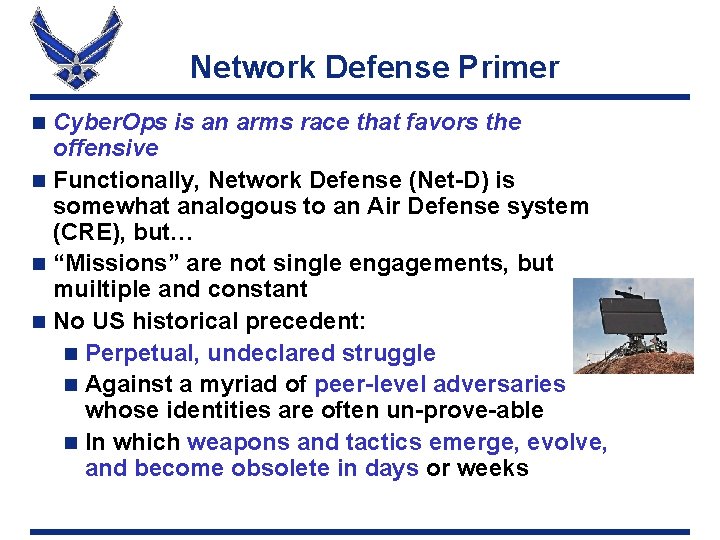
Network Defense Primer Cyber. Ops is an arms race that favors the offensive n Functionally, Network Defense (Net-D) is somewhat analogous to an Air Defense system (CRE), but… n “Missions” are not single engagements, but muiltiple and constant n No US historical precedent: n Perpetual, undeclared struggle n Against a myriad of peer-level adversaries whose identities are often un-prove-able n In which weapons and tactics emerge, evolve, and become obsolete in days or weeks n

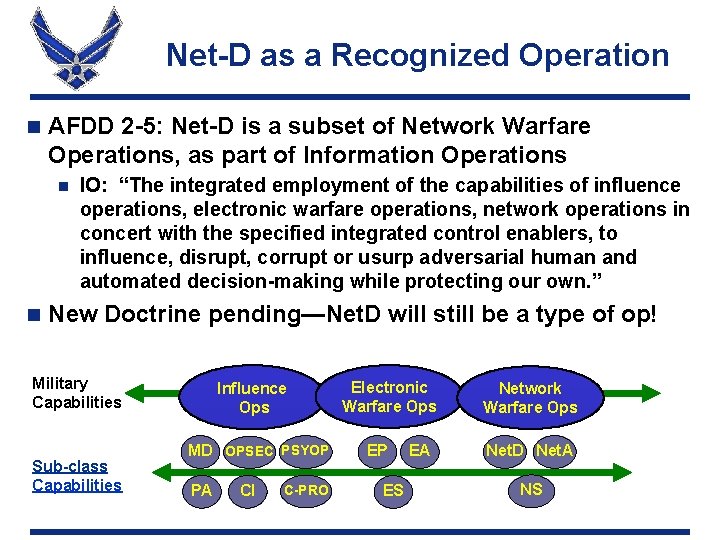
Net-D as a Recognized Operation n AFDD 2 -5: Net-D is a subset of Network Warfare Operations, as part of Information Operations n n IO: “The integrated employment of the capabilities of influence operations, electronic warfare operations, network operations in concert with the specified integrated control enablers, to influence, disrupt, corrupt or usurp adversarial human and automated decision-making while protecting our own. ” New Doctrine pending—Net. D will still be a type of op! Military Capabilities Sub-class Capabilities Influence Ops MD OPSEC PSYOP PA CI C-PRO Electronic Warfare Ops EP ES EA Network Warfare Ops Net. D Net. A NS

The Big Evolution n Steps on the Evolutionary Trail of Network Defense: n Nothing n Information Assurance plus Network Defense n Info Assurance plus Operationalized Net-D n Operationized Net-D—the process to get there is a set of concurrent evolutions in many areas— including people, systems, intelligence, and planning!

The Evolution in People n Steps on the Evolutionary Trail of Building a Network Defender: n Nothing n Technical Training plus Operational Training in an IQT/MQT Construct n Certified Training Under a Stan/Eval Process

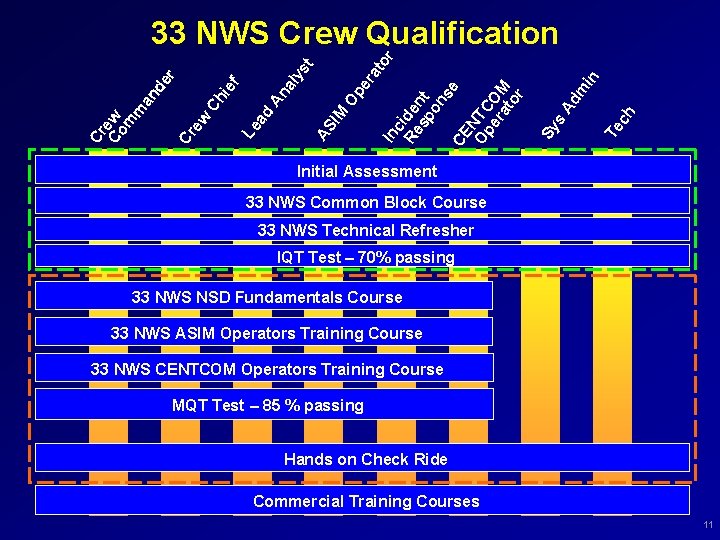
or in Te ch m Ad s Sy In c Re ide sp nt on se CE N Op TC er OM at or er at Op AS IM An al ys t d Le a Ch ew Cr Cr Coew m m an ie f de r 33 NWS Crew Qualification Initial Assessment 33 NWS Common Block Course 33 NWS Technical Refresher IQT Test – 70% passing 33 NWS NSD Fundamentals Course Unix 33 NWS ASIM Operators Training Course Routing/Networking 33 NWS CENTCOM Operators Training Course MQT Test – 85 % passing ASIM Tech CENTCOM Tech Hands on Check Ride Commercial Training Courses 11

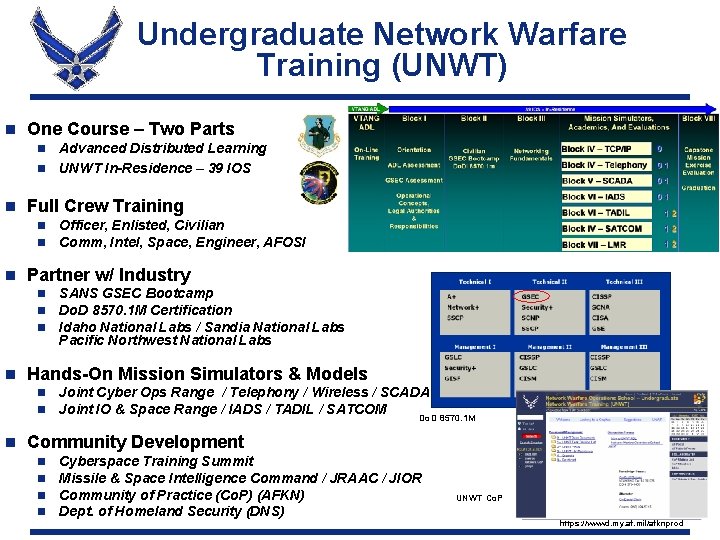
Undergraduate Network Warfare Training (UNWT) n One Course – Two Parts Advanced Distributed Learning n UNWT In-Residence – 39 IOS n n Full Crew Training n n n Partner w/ Industry n n SANS GSEC Bootcamp Do. D 8570. 1 M Certification Idaho National Labs / Sandia National Labs Pacific Northwest National Labs Hands-On Mission Simulators & Models n n n Officer, Enlisted, Civilian Comm, Intel, Space, Engineer, AFOSI Joint Cyber Ops Range / Telephony / Wireless / SCADA Joint IO & Space Range / IADS / TADIL / SATCOM Do. D 8570. 1 M Community Development n n Cyberspace Training Summit Missile & Space Intelligence Command / JRAAC / JIOR Community of Practice (Co. P) (AFKN) Dept. of Homeland Security (DNS) UNWT Co. P https: //wwwd. my. af. mil/afknprod

Standardization and Evaluation Stan/Eval – Professionalizes Stan/Eval Operations n Methodical mission planning n Synchronized Ops execution n Rigor/discipline/control Career long evaluations Weapons & Tactics n How? n Standard ROEs and TTPs n Mission Training n Mandatory Simulator time – Mission critical thinking Training Operations n Rigorous Evaluation n Elite Network Warriors – ready to affect the battle space n

The Evolution in Systems n Steps on the Evolutionary Trail of a Net-D Weapon: n “Some IT Gear” bought and deployed n A System, tested prior to deployment n A System, obtained to achieve a specific Net-D effect, tested, certified, and weaponized prior to deployment

AF Info Ops Center (AFIOC) § Weapons Ø Net. Warfare Tools OT&E Ø Countermeasure Development/Support Ø Network Warfare Systems Capability Integration Ø Wireless Signature support Ø New Technologies § Tactics Development Ø Architecture analysis support (incident response) Ø TTP Development Ø System/ Software Vulnerability Assessments Ø Modeling/Simulation

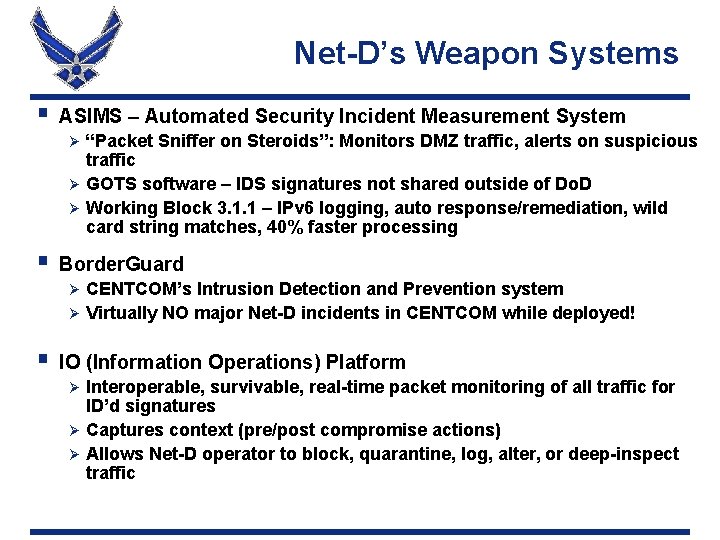
Net-D’s Weapon Systems § ASIMS – Automated Security Incident Measurement System “Packet Sniffer on Steroids”: Monitors DMZ traffic, alerts on suspicious traffic Ø GOTS software – IDS signatures not shared outside of Do. D Ø Working Block 3. 1. 1 – IPv 6 logging, auto response/remediation, wild card string matches, 40% faster processing Ø § Border. Guard CENTCOM’s Intrusion Detection and Prevention system Ø Virtually NO major Net-D incidents in CENTCOM while deployed! Ø § IO (Information Operations) Platform Interoperable, survivable, real-time packet monitoring of all traffic for ID’d signatures Ø Captures context (pre/post compromise actions) Ø Allows Net-D operator to block, quarantine, log, alter, or deep-inspect traffic Ø

AF Net-D Weapon Systems AF Sensors: 215 USCENTCOM Sensors: 111 79% Cisco Enlisted: 117 33 NWS Officer: 51 Civilian: 10 Contractors: 107 21% ASIM + AFIOC + Do. D + OSI + Joint + NOSCs + Civilian

The Evolution in Intelligence n Steps on the Evolutionary Trail of Net-D Intelligence: n Nothing n “Headline vignette” –quality Intel n “Headline vignette”, plus implications n Predictive, actionable Intel, through standard processes (PIRs, etc. )

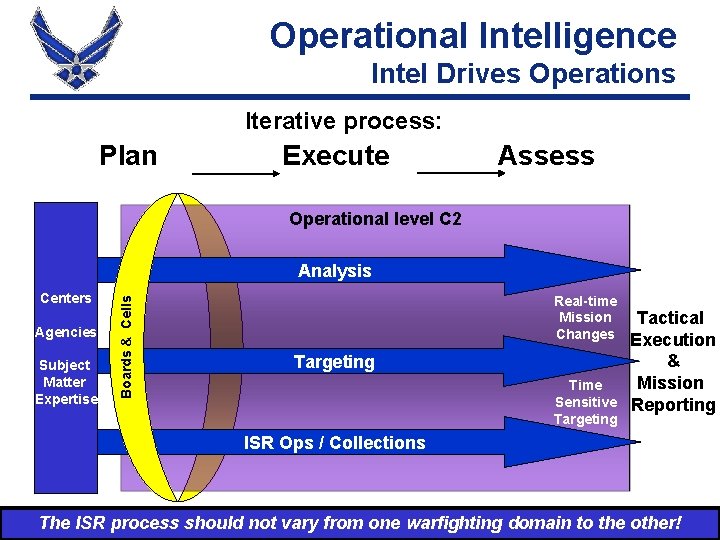
Operational Intelligence Intel Drives Operations Iterative process: Plan Execute Assess Operational level C 2 Centers Agencies Subject Matter Expertise Boards & Cells Analysis Real-time Mission Changes Targeting Time Sensitive Targeting Tactical Execution & Mission Reporting ISR Ops / Collections The ISR process should not vary from one warfighting domain to the other!

Cyberspace Intel Requirements n n n Provide predictive, timely and actionable intelligence to Commanders conducting operations in and through cyberspace (physical, digital, social, wireless networks) Collaborate with USGov, public, private and allied/coalition partners on cyberspace intelligence Perform operational assessments to improve cyber incident response Support operational assessment process with tailored analysis of cyberspace effectiveness in support of ongoing missions Develop and implement annual intel training requirements for all cyberspace operators Not much difference from ISR support to other forms of warfare…

The Evolution in Planning n Steps on the Evolutionary Trail of Net-D Mission Planning: n None—just “do what the systems force you to do” n Minimal—put context around “what the systems force you to do” n Plan in advance for what might happen—includes deliberate planning process n Self-initiated, aggressive Net-D Operations— ”named” operations—Mission Planning n Campaign Planning

Mission Planning, Campaign Planning Address specific adversaries and provide operational planning capability on the 2 week-to-1 year window n Focused on known adversaries n Focused on probable scenarios—develop mission concept from I&W to employment n Future capabilities will allow for more active defense, including ROE-based immediate response actions n

Questions?