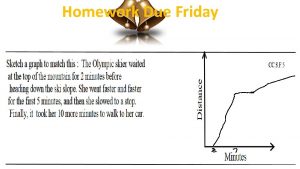
Announcement r Homework 3 due tomorrow midnight r


















- Slides: 39

Announcement r Homework #3 due tomorrow midnight r Project #3 is out 1

Last class r Routing in the Internet m Hierarchical routing m RIP m OSPF m BGP 2

Hierarchical Routing: Intra- and Inter-AS Routing 3 c 3 a 3 b AS 3 1 a 2 a 1 c 1 d 1 b Intra-AS Routing algorithm 2 c AS 2 AS 1 Inter-AS Routing algorithm Forwarding table 2 b r Forwarding table is configured by both intra- and inter-AS routing algorithm m m Intra-AS sets entries for internal dests Inter-AS & Intra-As sets entries for external dests 3

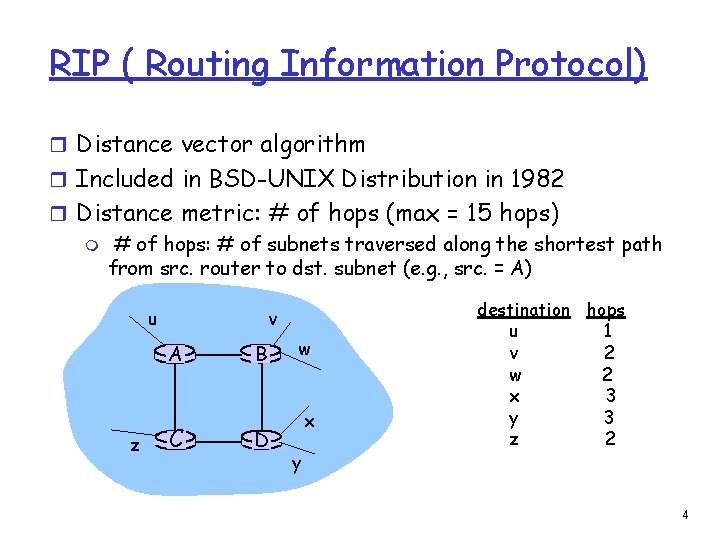
RIP ( Routing Information Protocol) r Distance vector algorithm r Included in BSD-UNIX Distribution in 1982 r Distance metric: # of hops (max = 15 hops) m # of hops: # of subnets traversed along the shortest path from src. router to dst. subnet (e. g. , src. = A) u v A z C B D w x y destination hops u 1 v 2 w 2 x 3 y 3 z 2 4

OSPF (Open Shortest Path First) r “open”: publicly available r Uses Link State algorithm m LS packet dissemination m Topology map at each node m Route computation using Dijkstra’s algorithm m Link costs configured by the network administrator r OSPF advertisement carries one entry per neighbor router r Advertisements disseminated to entire AS (via flooding) m Carried in OSPF messages directly over IP (rather than TCP or UDP 5

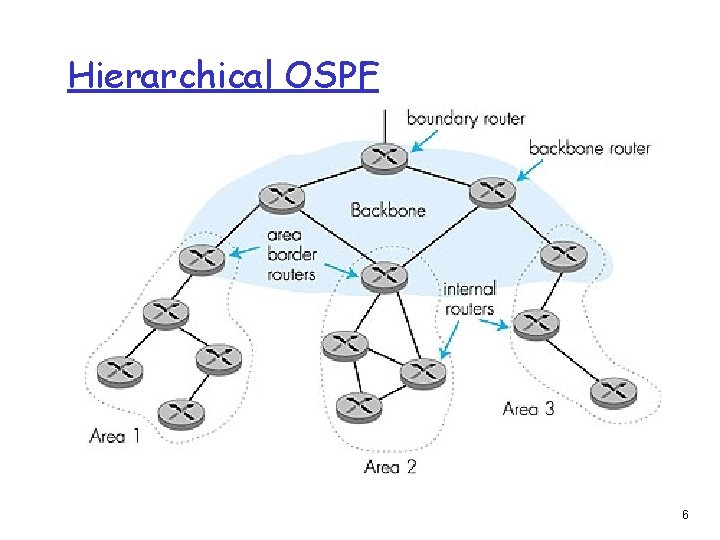
Hierarchical OSPF 6

Overview m BGP r Data link layer m Introduction and services m Error detection and correction m Multiple access protocols 7

Internet inter-AS routing: BGP r BGP (Border Gateway Protocol): the de facto standard r BGP provides each AS a means to: 1. 2. 3. Obtain subnet reachability information from neighboring ASs. Propagate the reachability information to all routers internal to the AS. Determine “good” routes to subnets based on reachability information and policy. r Allows a subnet to advertise its existence to rest of the Internet: “I am here” 8

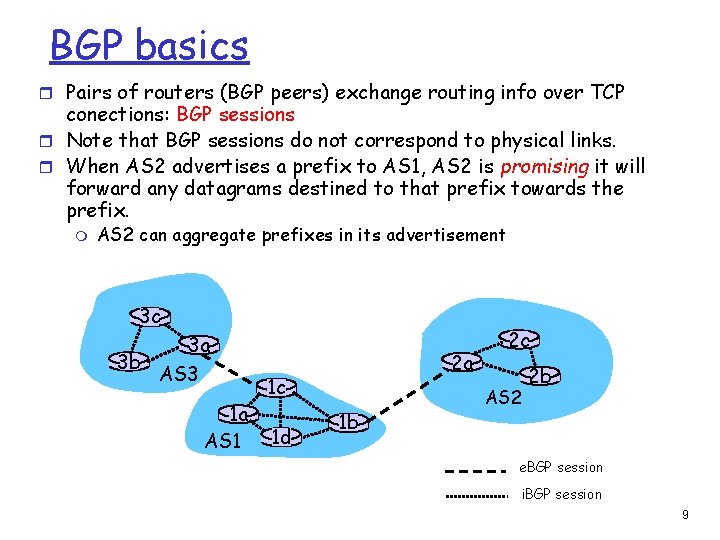
BGP basics r Pairs of routers (BGP peers) exchange routing info over TCP conections: BGP sessions r Note that BGP sessions do not correspond to physical links. r When AS 2 advertises a prefix to AS 1, AS 2 is promising it will forward any datagrams destined to that prefix towards the prefix. m AS 2 can aggregate prefixes in its advertisement 3 c 3 a 3 b AS 3 1 a AS 1 2 a 1 c 1 d 1 b 2 c AS 2 2 b e. BGP session i. BGP session 9

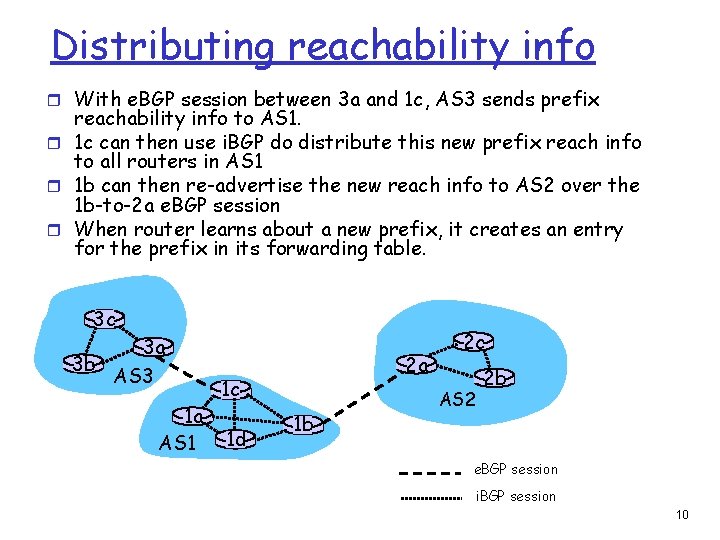
Distributing reachability info r With e. BGP session between 3 a and 1 c, AS 3 sends prefix reachability info to AS 1. r 1 c can then use i. BGP do distribute this new prefix reach info to all routers in AS 1 r 1 b can then re-advertise the new reach info to AS 2 over the 1 b-to-2 a e. BGP session r When router learns about a new prefix, it creates an entry for the prefix in its forwarding table. 3 c 3 a 3 b AS 3 1 a AS 1 2 a 1 c 1 d 1 b 2 c AS 2 2 b e. BGP session i. BGP session 10

Path attributes & BGP routes r When advertising a prefix, advert includes BGP attributes. m prefix + attributes = “route” r Two important attributes: m AS-PATH: contains the ASs through which the advert for the prefix passed: AS 67 AS 17 m NEXT-HOP: Indicates the specific internal-AS router to next-hop AS. (There may be multiple links from current AS to next-hop-AS. ) r When gateway router receives route advert, uses import policy to accept/decline. 11

BGP route selection r Router may learn about more than 1 route to some prefix. Router must select route. r Elimination rules: 1. 2. 3. 4. Local preference value attribute: policy decision Shortest AS-PATH Closest NEXT-HOP router: hot potato routing Additional criteria 12

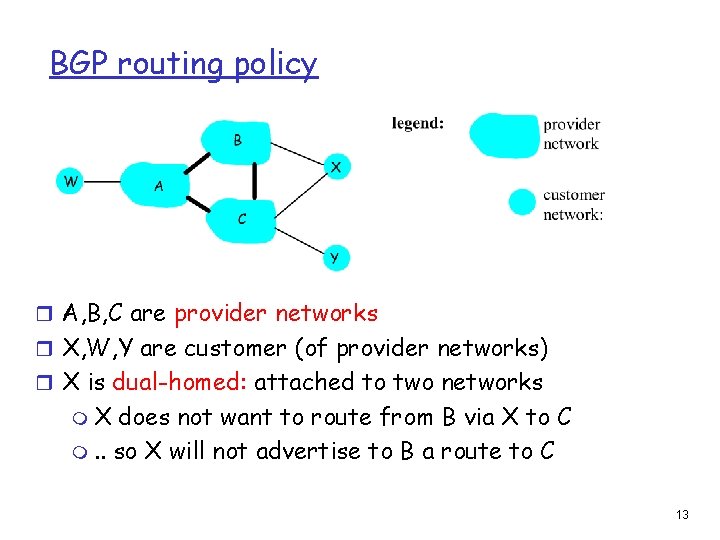
BGP routing policy r A, B, C are provider networks r X, W, Y are customer (of provider networks) r X is dual-homed: attached to two networks m. X does not want to route from B via X to C m. . so X will not advertise to B a route to C 13

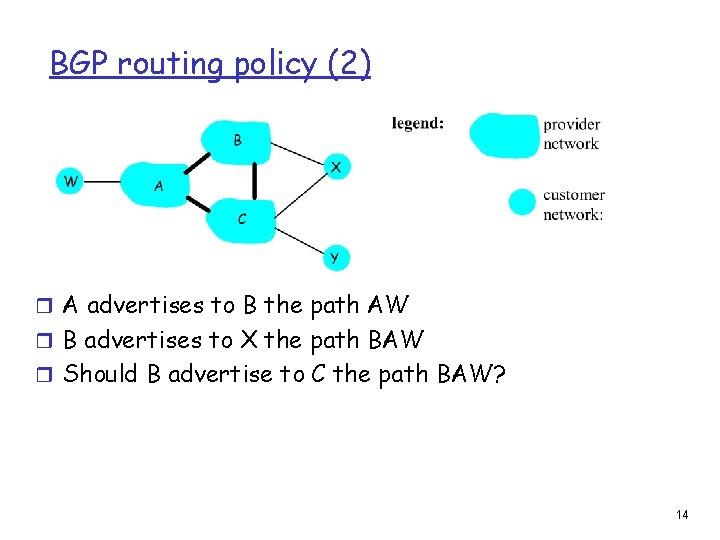
BGP routing policy (2) r A advertises to B the path AW r B advertises to X the path BAW r Should B advertise to C the path BAW? 14

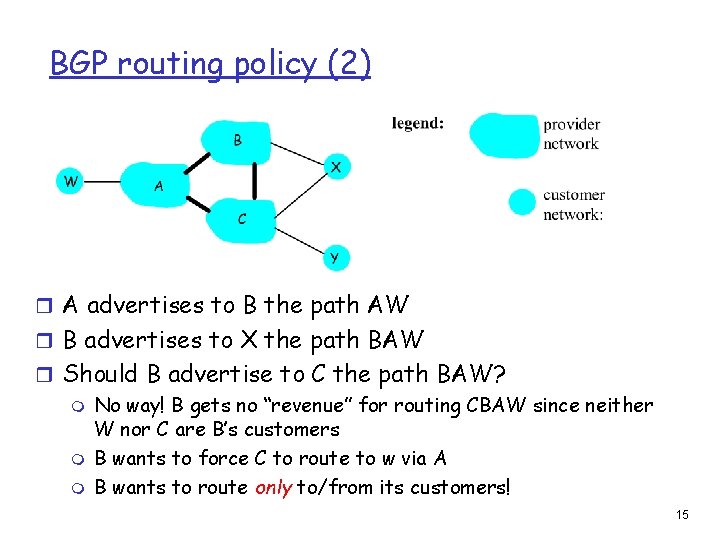
BGP routing policy (2) r A advertises to B the path AW r B advertises to X the path BAW r Should B advertise to C the path BAW? m No way! B gets no “revenue” for routing CBAW since neither W nor C are B’s customers m B wants to force C to route to w via A m B wants to route only to/from its customers! 15

Why different Intra- and Inter-AS routing ? Policy: r Inter-AS: admin wants control over how its traffic routed, who routes through its net. r Intra-AS: single admin, so no policy decisions needed Scale: r hierarchical routing saves table size, reduced update traffic Performance: r Intra-AS: can focus on performance r Inter-AS: policy may dominate over performance 16

Overview m BGP r Data link layer m Introduction and services m Error detection and correction m Multiple access protocols 17

The Data Link Layer Our goals: r understand principles behind data link layer services: m m error detection, correction sharing a broadcast channel: multiple access link layer addressing reliable data transfer, flow control: done! r instantiation and implementation of various link layer technologies 18

Overview m BGP r Data link layer m Introduction and services m Error detection and correction m Multiple access protocols 19

Link Layer: Introduction Some terminology: “link” r hosts and routers are nodes r communication channels that connect adjacent nodes along communication path are links m m m wired links wireless links LANs r layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 20

Link layer: context r Datagram transferred by different link protocols over different links: m e. g. , Ethernet on first link, frame relay on intermediate links, 802. 11 on last link r Each link protocol provides different services m e. g. , may or may not provide rdt over link transportation analogy r trip from Princeton to Lausanne m limo: Princeton to JFK m plane: JFK to Geneva m train: Geneva to Lausanne r tourist = datagram r transport segment = communication link r transportation mode = link layer protocol r travel agent = routing algorithm 21

Link Layer Services r Framing, link access: m encapsulate datagram into frame, adding header, trailer m channel access if shared medium m “MAC” addresses used in frame headers to identify source, dest • different from IP address! r Reliable delivery between adjacent nodes m we learned how to do this already (chapter 3)! m seldom used on low bit error link (fiber, some twisted pair) m wireless links: high error rates • Q: why both link-level and end-end reliability? 22

Link Layer Services (more) r Flow Control: m pacing between adjacent sending and receiving nodes r Error Detection: m errors caused by signal attenuation, noise. m receiver detects presence of errors: • signals sender for retransmission or drops frame r Error Correction: m receiver identifies and corrects bit error(s) without resorting to retransmission r Half-duplex and full-duplex m with half duplex, nodes at both ends of link can transmit, but not at same time 23

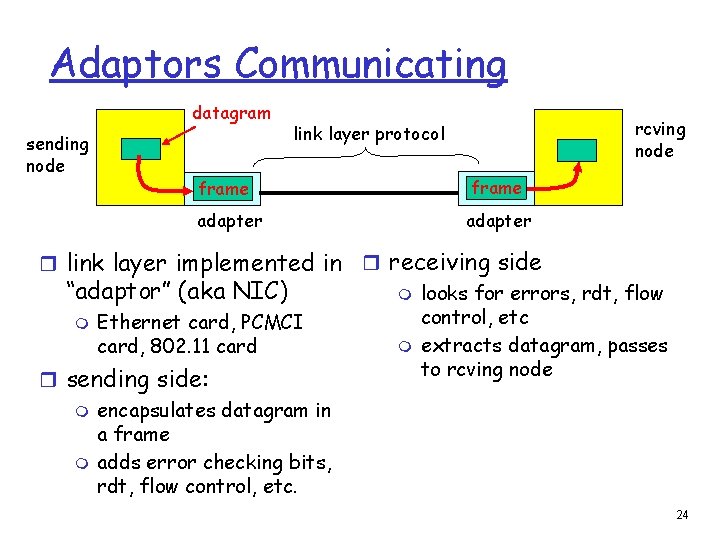
Adaptors Communicating datagram sending node rcving node link layer protocol frame adapter r link layer implemented in r receiving side “adaptor” (aka NIC) m looks for errors, rdt, flow control, etc m Ethernet card, PCMCI m extracts datagram, passes card, 802. 11 card to rcving node r sending side: m m encapsulates datagram in a frame adds error checking bits, rdt, flow control, etc. 24

Overview m BGP r Data link layer m Introduction and services m Error detection and correction m Multiple access protocols 25

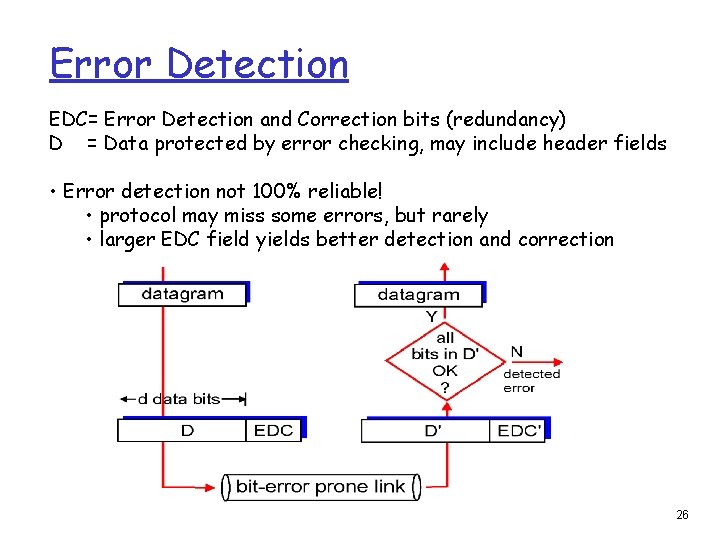
Error Detection EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction 26

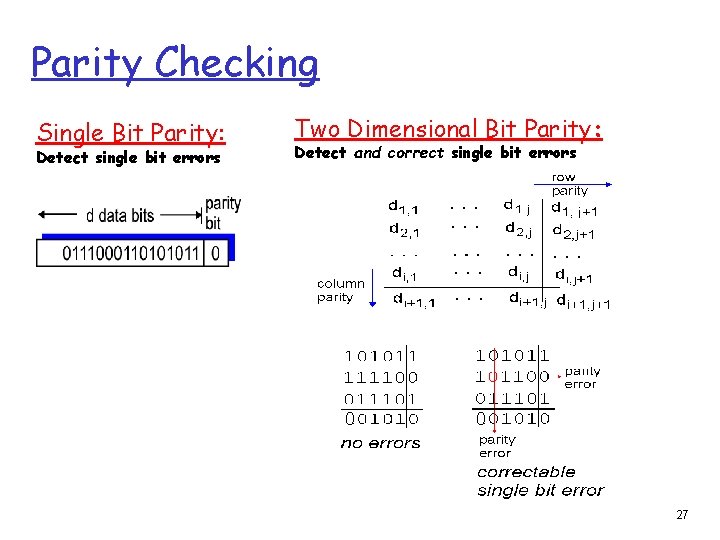
Parity Checking Single Bit Parity: Detect single bit errors Two Dimensional Bit Parity: Detect and correct single bit errors 0 0 27

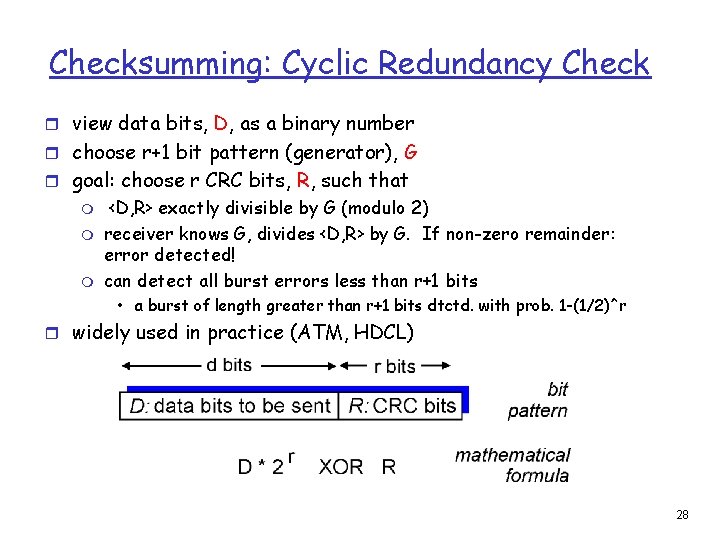
Checksumming: Cyclic Redundancy Check r view data bits, D, as a binary number r choose r+1 bit pattern (generator), G r goal: choose r CRC bits, R, such that m m m <D, R> exactly divisible by G (modulo 2) receiver knows G, divides <D, R> by G. If non-zero remainder: error detected! can detect all burst errors less than r+1 bits • a burst of length greater than r+1 bits dtctd. with prob. 1 -(1/2)^r r widely used in practice (ATM, HDCL) 28

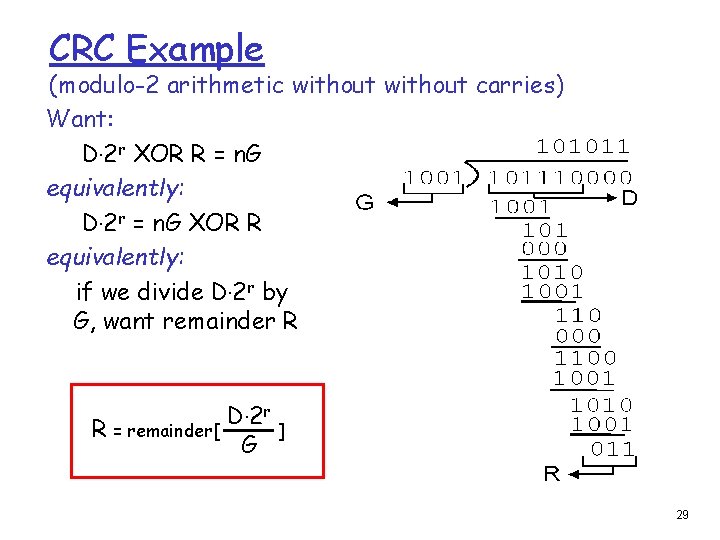
CRC Example (modulo-2 arithmetic without carries) Want: D. 2 r XOR R = n. G equivalently: D. 2 r = n. G XOR R equivalently: if we divide D. 2 r by G, want remainder R R = remainder[ D. 2 r G ] 29

Overview m BGP r Data link layer m Introduction and services m Error detection and correction m Multiple access protocols 30

Multiple Access Links and Protocols Two types of “links”: r point-to-point m PPP for dial-up access m point-to-point link between Ethernet switch and host r broadcast (shared wire or medium) m traditional Ethernet m upstream cable m 802. 11 wireless LAN 31

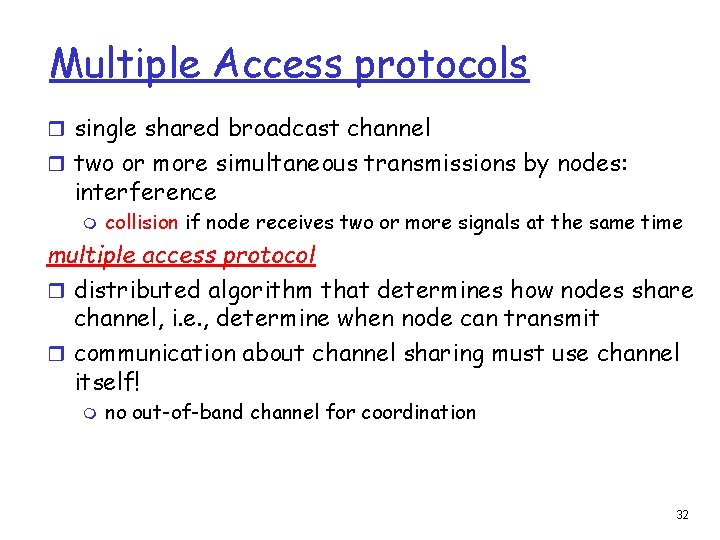
Multiple Access protocols r single shared broadcast channel r two or more simultaneous transmissions by nodes: interference m collision if node receives two or more signals at the same time multiple access protocol r distributed algorithm that determines how nodes share channel, i. e. , determine when node can transmit r communication about channel sharing must use channel itself! m no out-of-band channel for coordination 32

Ideal Multiple Access Protocol Broadcast channel of rate R bps 1. When one node wants to transmit, it can send at rate R. 2. When M nodes want to transmit, each can send at average rate R/M 3. Fully decentralized: m m no special node to coordinate transmissions no synchronization of clocks, slots 4. Simple 33

MAC Protocols: a taxonomy Three broad classes: r Channel Partitioning m m divide channel into smaller “pieces” (time slots, frequency, code) allocate piece to node for exclusive use r Random Access m channel not divided, allow collisions m “recover” from collisions r “Taking turns” m Nodes take turns, but nodes with more to send can take longer turns 34

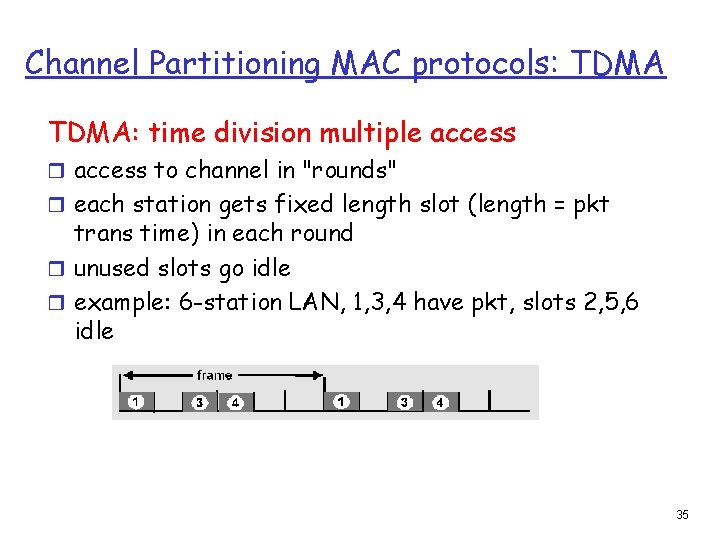
Channel Partitioning MAC protocols: TDMA: time division multiple access r access to channel in "rounds" r each station gets fixed length slot (length = pkt trans time) in each round r unused slots go idle r example: 6 -station LAN, 1, 3, 4 have pkt, slots 2, 5, 6 idle 35

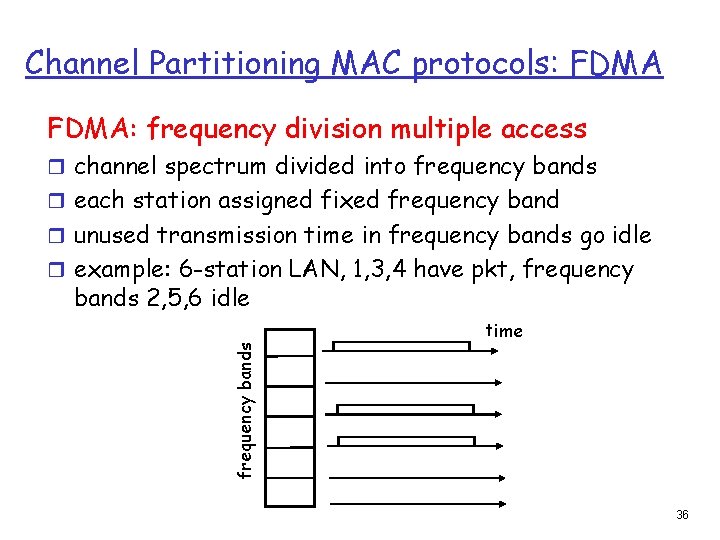
Channel Partitioning MAC protocols: FDMA: frequency division multiple access r channel spectrum divided into frequency bands r each station assigned fixed frequency band r unused transmission time in frequency bands go idle r example: 6 -station LAN, 1, 3, 4 have pkt, frequency bands 2, 5, 6 idle frequency bands time 36

Random Access Protocols r When node has packet to send m transmit at full channel data rate R. m no a priori coordination among nodes r two or more transmitting nodes ➜ “collision”, r random access MAC protocol specifies: m how to detect collisions m how to recover from collisions (e. g. , via delayed retransmissions) r Examples of random access MAC protocols: m slotted ALOHA m CSMA, CSMA/CD, CSMA/CA 37

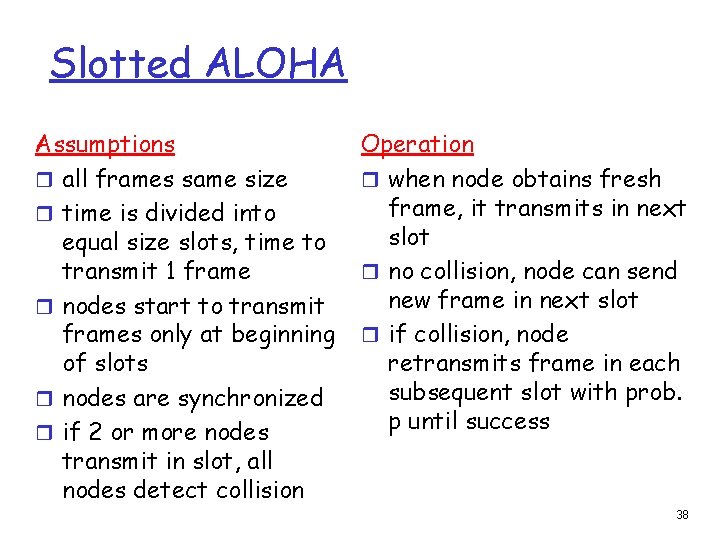
Slotted ALOHA Assumptions r all frames same size r time is divided into equal size slots, time to transmit 1 frame r nodes start to transmit frames only at beginning of slots r nodes are synchronized r if 2 or more nodes transmit in slot, all nodes detect collision Operation r when node obtains fresh frame, it transmits in next slot r no collision, node can send new frame in next slot r if collision, node retransmits frame in each subsequent slot with prob. p until success 38

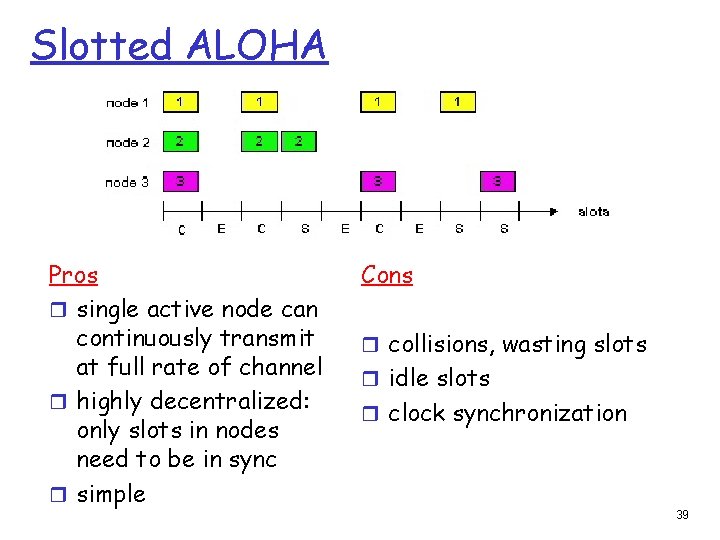
Slotted ALOHA Pros r single active node can continuously transmit at full rate of channel r highly decentralized: only slots in nodes need to be in sync r simple Cons r collisions, wasting slots r idle slots r clock synchronization 39
 Tomorrow and tomorrow and tomorrow kurt vonnegut
Tomorrow and tomorrow and tomorrow kurt vonnegut Tomorrow and tomorrow and tomorrow kurt vonnegut analysis
Tomorrow and tomorrow and tomorrow kurt vonnegut analysis Due tomorrow do tomorrow
Due tomorrow do tomorrow Due tomorrow do tomorrow
Due tomorrow do tomorrow Ilegalism
Ilegalism If you finish your homework before school
If you finish your homework before school Unsullied definition to kill a mockingbird
Unsullied definition to kill a mockingbird Jack prelutsky homework oh homework
Jack prelutsky homework oh homework Homework oh homework poem
Homework oh homework poem Jack prelutsky homework oh homework
Jack prelutsky homework oh homework Alitteration definition
Alitteration definition Homework oh homework i hate you you stink
Homework oh homework i hate you you stink Consonance
Consonance Homework due today
Homework due today Astr
Astr Folk culture and popular culture venn diagram
Folk culture and popular culture venn diagram Homework
Homework Homework due today
Homework due today Homework is due on friday
Homework is due on friday Homework is due on friday
Homework is due on friday Homework is due
Homework is due Black cat analogy
Black cat analogy Homework due today
Homework due today Grande rhetra
Grande rhetra Conservazione del moto
Conservazione del moto Famiglia dei parallelogrammi
Famiglia dei parallelogrammi Procedural due process vs substantive due process
Procedural due process vs substantive due process Pvu background
Pvu background Draft a circular letter announcing change in premises
Draft a circular letter announcing change in premises Presidential elections exploration and announcement
Presidential elections exploration and announcement Please turn off your cell phone announcement
Please turn off your cell phone announcement Bert van bruchem
Bert van bruchem Willard scott birthday announcement form
Willard scott birthday announcement form Hear ye, hear ye announcement examples
Hear ye, hear ye announcement examples He and she ___ not pay attention of teachers announcement
He and she ___ not pay attention of teachers announcement Announcement flag ceremony
Announcement flag ceremony Lecture announcement sample
Lecture announcement sample Midterm exam announcement
Midterm exam announcement Example of thesis statement and topic sentence
Example of thesis statement and topic sentence Which of the following is true about functional text?
Which of the following is true about functional text?