Analysis of SIP security Ashwini Sanap 006312787 Deepti




- Slides: 16

Analysis of SIP security Ashwini Sanap (006312787) Deepti Agashe (006331234)

Agenda Introduction n SIP Entities and messages n Security Mechanism n Security Attacks n Conclusion n

Introduction n Session Initiation Protocol (SIP) n Application Layer Signaling Protocol n Create, Terminate and Manage Session n Similar to HTTP (Request/Response) n SIP Identity (URI)

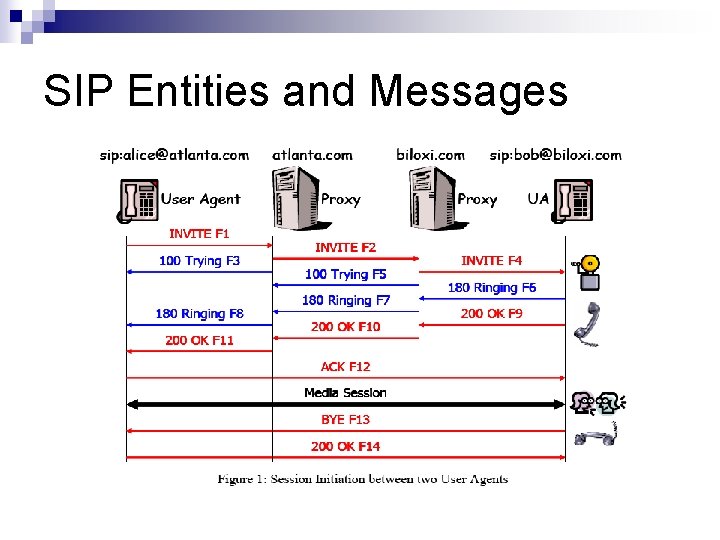
SIP Entities and Messages

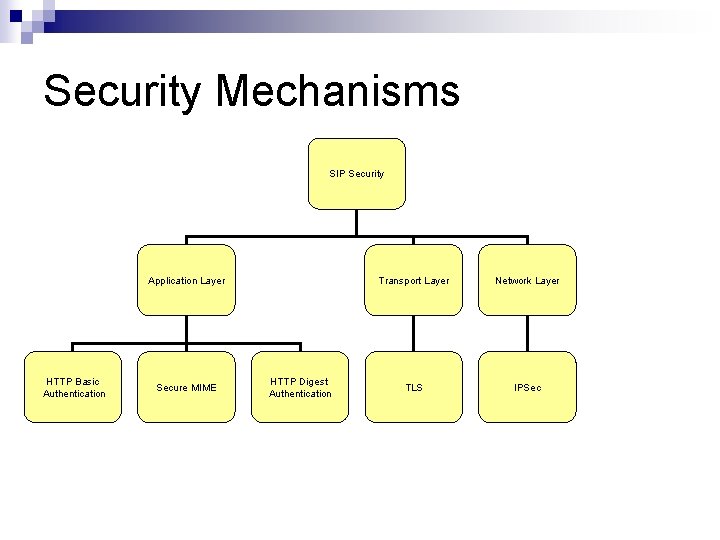
Security Mechanisms SIP Security Application Layer HTTP Basic Authentication Secure MIME HTTP Digest Authentication Transport Layer Network Layer TLS IPSec

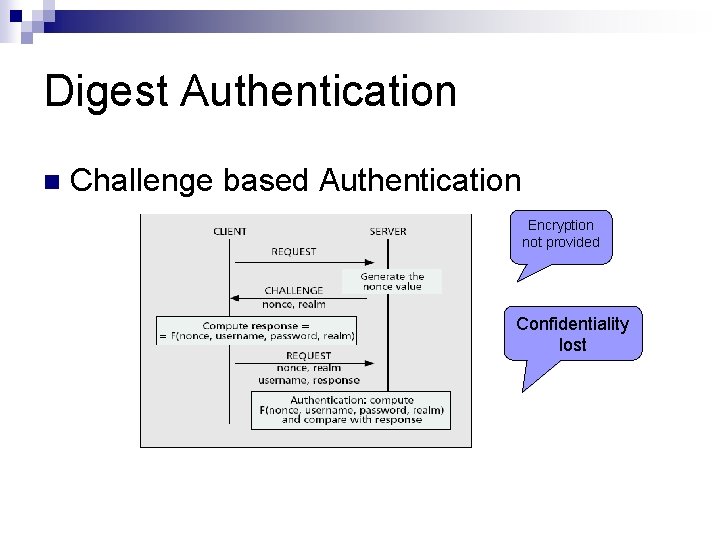
Digest Authentication n Challenge based Authentication Encryption not provided Confidentiality lost

Secure MIME Multipurpose Internet Mail Extension n End to End security n Encrypts MIME body using public key of receiver n PK Exchanged thru Certificates n Entity Authentication n

Transport Layer Security (TLS) TCP->TLS n SIPS (Similar to HTTPS) n SIPS ensures parameters passed securely n SRTP ensures media is also secured n SIPS+SRTP = Protection n

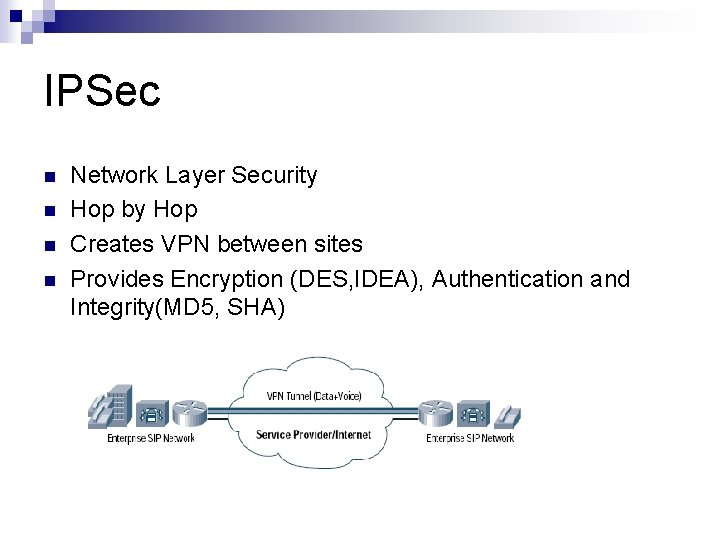
IPSec n n Network Layer Security Hop by Hop Creates VPN between sites Provides Encryption (DES, IDEA), Authentication and Integrity(MD 5, SHA)

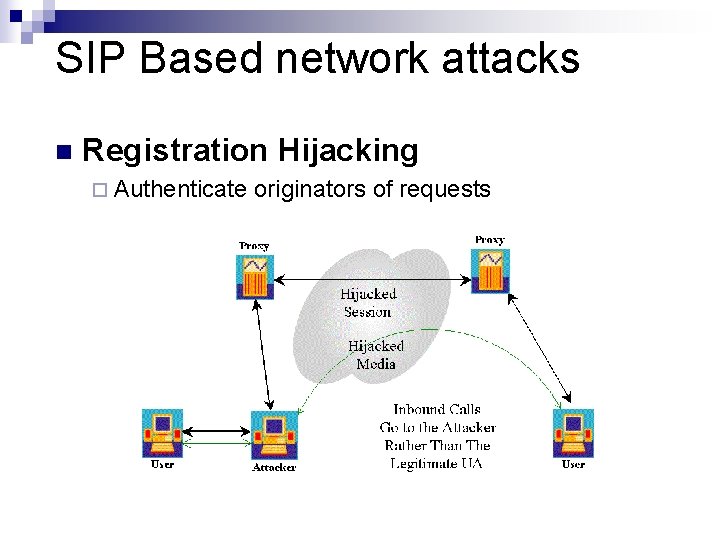
SIP Based network attacks n Registration Hijacking ¨ Authenticate originators of requests

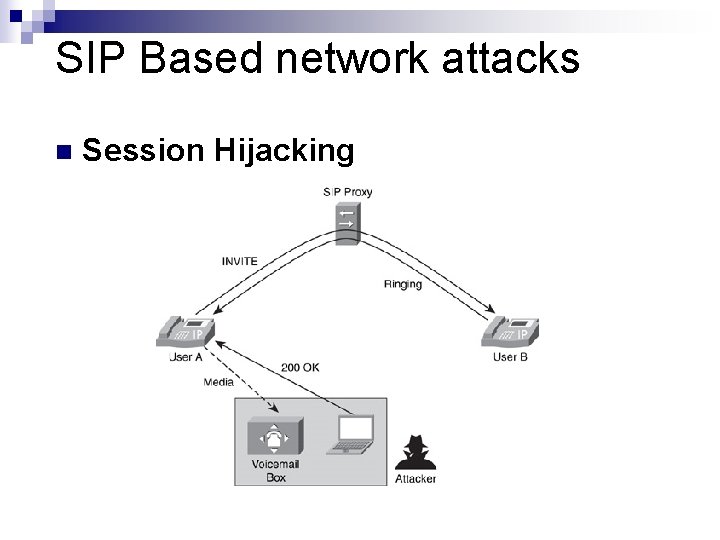
SIP Based network attacks n Session Hijacking

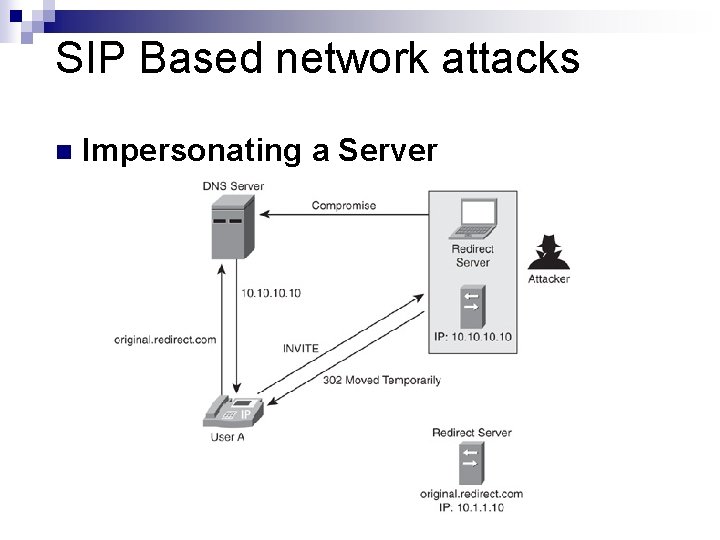
SIP Based network attacks n Impersonating a Server

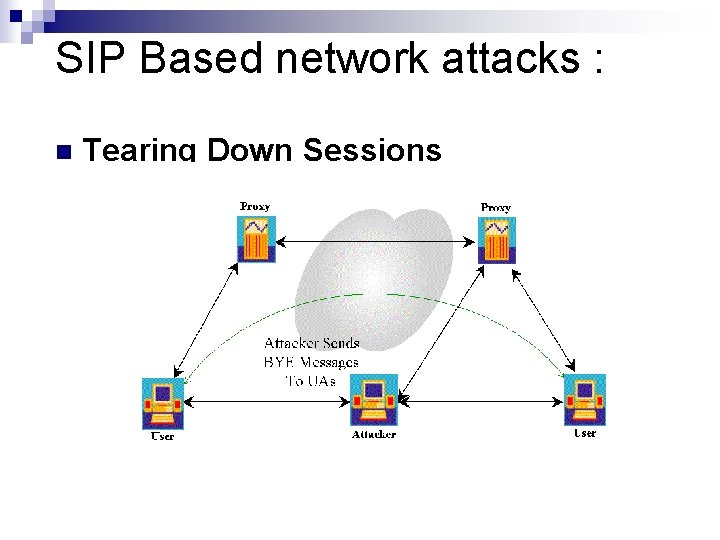
SIP Based network attacks : n Tearing Down Sessions

SIP Based network attacks : n Other attacks include : ¨ Tampering ¨ Denial ¨ Bots with Message Bodies of Service and Amplification and DDOS Attacks

Conclusion SIP is expected to be the future Vo. IP protocol of choice. n Use SIP-optimized firewalls, which both support use of standards-based security and provide the best possible protection where system-wide standards-based security is not possible. n

 Ashwini jarral
Ashwini jarral Private securit
Private securit Sip security vulnerabilities
Sip security vulnerabilities Sip security issues
Sip security issues Sip security best practice
Sip security best practice What is osi security architecture
What is osi security architecture Guide to network security
Guide to network security Wireless security in cryptography and network security
Wireless security in cryptography and network security Visa international security model in information security
Visa international security model in information security Electronic mail security in network security
Electronic mail security in network security Explain about cnss security model
Explain about cnss security model Electronic commerce security
Electronic commerce security Software security building security in
Software security building security in Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals Berikut format alamat sip yang benar adalah
Berikut format alamat sip yang benar adalah Verizon business solutions consultant
Verizon business solutions consultant