An Introduction to ITIL and ITSM and How





































- Slides: 41

An Introduction to ITIL and ITSM and How ITIL supports Information Security 1

The Situation in the 1980’s… 2

Background Since the 1980’s organizations have become ever more reliant on IT and the Services that IT provides. As this reliance grows and as the complexity and sophistication of the IT infrastructure and environment that supports and enables these IT Services increases, there are ever-increasing demands on IT departments to provide robust and predictable levels of IT service provision. This led to the need to effectively manage IT Services. 3

Business Reliance on IT Staff need to know that when they arrive on site that the IT Services they rely on to do their jobs will be available and will stay available throughout the course of the working day. By IT Service we’re talking about: a) the software, programs, applications etc. that staff require to have up and working on their workstation in order to perform their job b) customer-facing applications e. g. company websites and the functionality contained within 4

Growing Expectations Similarly, external customers have high expectations that the IT Services made available to them (via for example corporate websites) will be available when needed. 5

Implications of poor IT service provision The implications of poor IT service provision are non-productive staff, a poor level of service to external customers and the bottom-line implications to the Business that these have. 6

This situation generated requirements… 7

An IT Service mindset IT needed to shift from a technology-driven to a Service-driven approach through the creation of an IT Service mindset and the introduction of a service culture 8

Integrated processes IT also needed to overcome misperceptions and position itself as a true Business partner through the adoption of an integrated process improvement framework that allows for improvements in areas with which Business partners can identify - the provision of IT Services. 9

A Common Language IT also needed to adopt a common language which is easily understood by Business partners. 10

Management Information IT also needed to move towards using complete and accurate Management Information as a basis for decision-making. 11

It was these requirements that lead to the creation of ITIL… 12

ITIL Origins In the mid-80’s, the UK Central Computer and Telecommunications Agency (the CCTA), now called the Office of Government Commerce (OGC), was tasked with developing a framework for efficient and financially responsible use of IT resources within the British government and the private sector. 13

What is the ITIL framework? ITIL was conceived as a set of best-practices (in other words, recommendations related to operational IT processes) developed to provide guidance across the IT Enterprise, including infrastructure, development, operations and support. The goal was to enable an IT organization to provide costeffective, quality services to the organization through alignment of IT to Business needs and the enablement of the highest possible levels of IT Service availability. This process approach allows the implementation of best practices independently from the structure of the organization. 14

ITIL version 1 The goal was to develop an approach that would be vendorindependent and applicable to organizations with differing technical and business needs. This resulted in the creation in 1989 of ITIL - often known now as ITIL version 1. The fact that it was a series of books led to the name IT Infrastructure Library (ITIL). 15

What does it contain? This ‘best practices framework’ is based on the collective experience of commercial and governmental practitioners worldwide. ITIL describes all the tasks, activities, inputs, and outputs of commonly used processes in an organization while at the same time recognizing that each IT organization has a need to implement ITIL processes in a way that meets its unique own requirements. 16

ITIL is also… Therefore, it does not provide any restrictive guidelines for process implementation. This approach is known as non-prescriptive as it explains what organizations need to do to meet the requirements of bestpractice, but does not specifically document how to achieve this. This has been distilled into one reliable, coherent approach, which has become the de facto standard used by many of the world's leading businesses. 17

ITIL version 2 In the mid-90’s the ITIL was updated and then expanded to a series of nine books, each of which covers a core area within IT Management. The ITIL framework encompassed the processes required by an IT department to undertake IT Service Management. These processes include the delivery and support of IT Services, application, infrastructure and security management, and the perspective of the Business. 18

Growth of ITIL While ITIL has its roots in the 1980’s, it was not widely adopted until the mid 1990’s. Although ITIL spread beyond the United Kingdom, it was initially confined to European organizations. Recently North American companies have looked to ITIL to streamline operations and decrease costs. 19

Migration to the US In recent years, the relevance of ITIL in the United States and other countries has come to the forefront because of new regulations passed by governments and other regulatory bodies. For example, an ITIL implementation will help a company meet IT requirements of the Health Insurance Portability and Accountability Act (HIPAA) and the Sarbanes-Oxley Act (SOX). Both of these regulations have provisions regarding data and security, which can be addressed by processes within ITIL. 20

ITIL version 3 2007 -2011 - ITIL Version 3 - the “ITIL refresh” 5 core books encompassing the IT Service lifecycle: • Service Strategy • Service Design • Service Transition • Service Operation • Continual Service Improvement 21

Other than being a process framework, what else should I know about ITIL? • • • Customizable Framework Non-Prescriptive Applicable to any industry type, any organization size, any organizational culture Integrates IT with the Business and focuses IT on corporate objectives. The provision of IT Services becomes customer-focused and service quality agreements help further develop the relationship Shifts IT from a technology-driven approach through the creation of an IT Service mindset and allows for the introduction of a service culture Introduces a common language which allows for improved communications with internal customers and external suppliers Improves efficiency, increases effectiveness, and reduces risk Typical organizational benefits of implementing ITIL fall into the categories of Service, Quality, and Performance An integrated process improvement framework that allows for improvements in areas with which Business partners can identify - the provision of IT Services Complete and accurate Management Information as a basis for decision-making 22

ITIL Adoption ITIL is the most widely adopted approach to IT Service Management (ITSM) in the world and provides a comprehensive and consistent set of best practices for ITSM, promoting a quality approach to achieving business effectiveness and efficiency in the use of information systems. 23

ITIL Adoption More than 10, 000 organizations have adopted ITIL worldwide and ITIL is becoming increasingly integrated with other quality standards such as the Information Services Procurement Library, the Application Services Library, Dynamic Systems Development Method, and the Capability Maturity Model. ITIL is also linked with IT governance through Control Objectives for Information and related Technology (COBIT). 24

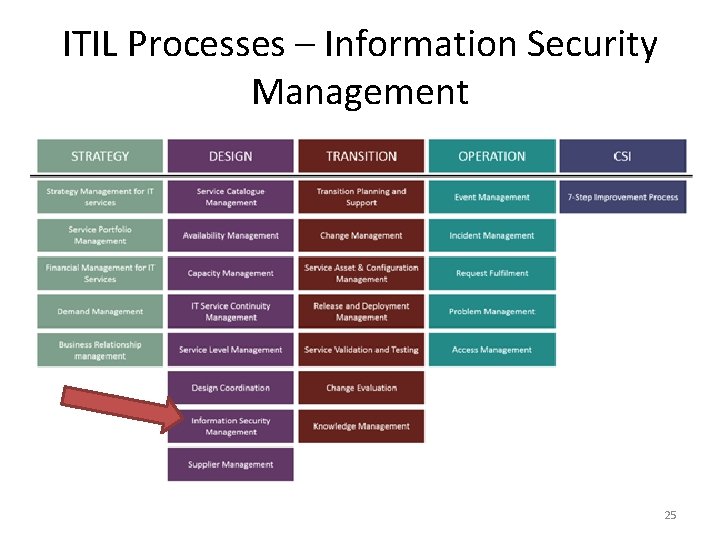
ITIL Processes – Information Security Management 25

ISO 27001 and ITIL (ISO 20000) ISO 27001 describes the model for establishing, implementing, operating, monitoring, reviewing, maintaining and improving an Information Security Management System (ISMS). The ISMS identifies the organization’s strategic direction for security and ensures that the objectives are achieved. The ISMS ensures that information security risks are appropriately managed and that information resources are used responsibly. ITIL does not provide detail on all aspects of Information Security Management, instead deferring to ISO 27001 for that. Instaed, as with all other ITSM processes ITIL documents crucial activities and enables integration with other ITSM processes. From an ITIL perspective, the ISMS addresses: • Information Security policies • Information Security plan • Information Security organizational structure • Management of Information Security risks • Communication strategy It also provides guidance on creating the following Sub-Processes 26

ITIL Information Security process activities Design of Security Controls The design of appropriate technical and organizational solutions to ensure the confidentiality, integrity, security and availability of an organization's assets, information, data and services through the establishment a management framework which will initiate and manage information security in the organization, establish an organization structure to prepare, approve and implement the Information Security Policy, define roles and responsibilities, allocate resources, and establish and control documentation Security Testing Regularly tests all information security mechanisms to ensure that appropriate procedures, tools and controls are in place to underpin the Information Security Policy Management of Security Incidents Detect and fight attacks and intrusions, and minimize the impact of security breaches Security Review Ensure that security measures and procedures remain in line with risk through regular maintenance and testing. Monitor compliance with Information Security policy. Conduct regular audits of the technical security of IT systems. Improve security agreements as defined in e. g. SLAs, OLAs, and Vendor Contracts. Conduct continual improvement of 27 Information Security measures and controls

ITIL Information Security - Goals and Benefits The goals of the Information Security Management process are to: • Align Information Security with Business security • Ensure that Information Security is effectively undertaken for all IT Services and within all related IT Service Management activities The benefits of implementing an Information Security process utilizing the ITIL framework are that: • It encourages the creation and operation of the process using a structured approach based on proven industry-standard best practices • Defined roles and responsibilities are documented and operationalized • The process is integrated with other complementary processes within the overall ITIL framework • Once operationalized, the process is subject to continuous review and improvement and is therefore optimized over time. This also allows for required updates based on the discovery of new threats ITIL v 3 has the Information Security Management process contained within the Service Design phase of the Service lifecycle which means that Information Security requirements can be documented and built into IT solutions rather than considered ‘after the fact’ 28

How does ITIL enable Information Security? The ITIL framework enables Information Security both Directly and Indirectly: • Directly through the implementation and operation of the Information Security process itself as we have just seen • Indirectly, as multiple other ITIL processes also support Information Security either through Resolution (reactive) or Prevention (proactive) 29

The processes that support Information Security through Resolution The Help Desk/Service Desk and Incident Management IT Service Continuity Management/Business Continuity/Disaster Recovery 30

The Service Desk • Through its adherence to best practices and its initiation and driving of key aspects of the Incident Management process, the Service Desk ensures minimal downtime to IT Services when Information Security-related Incidents occur and minimal impact through a constant cycle of obtaining and communicating updates 31

Incident Management • Incident Management ensures the fastest possible return to service when service interruptions occur, by concentrating limited resources on the highest priority Incidents at any given time (which by default should always be any Information Security-related Incidents) 32

IT Service Continuity Management/BC/DR • ITSCM/BC/DR ensuring the fastest possible return to service when service interruptions occur, by returning Services to normal operation in the order defined in the ITSCM/BC/DR Plan which has itself been written in conjunction with the Business 33

The processes that support Information Security through Prevention Event Management Access Management Problem Management Change Management Requirements Validation and Testing Configuration Management 34

Event Management • Event Management allows for Event prediction, and the preemption and prevention of IT Service interruptions, through ensuring effective monitoring of the most Business-critical Services. The intent is to spot e. g. a hacking attempt or an intrusion and resolve it before any impact to the IT operational environment 35

Access Management • Access Management ensures that only staff members with a Business need to do so, have access to Systems. This minimizes the risk of deliberate or accidental damage to IT systems 36

Problem Management • Problem Management provisions of Known Error and Workaround information which means that when symptoms of e. g. a hacking attempt or an intrusion are discovered, the remedial actions required are already known, documented and staff trained to immediately undertake the necessary actions to minimize any impact • Problem Management also minimizes the possibility of repeat occurrences through permanent resolution after the first instance 37

Change Management • Change Management minimizes the possibility of Change activity adversely impacting the IT environment by ensuring the highest possible number of successful (non-Serviceimpacting) Changes • Change Management also allows a greater ability to handle a large volume of change (including those to permanently resolve e. g. the cause(s) of Information Security-related Incidents) 38

Requirements Validation and Testing • Non-functional requirements, including Information Security requirements, are included in Change solution design rather than being considered ‘after the fact’ 39

Asset/Configuration Management • Improves the accuracy of CI status throughout lifecycle • Enables the identification and removal of discovered unauthorized IT components • Provisions a tool (the Configuration Management System – CMS) which provides a virtual representation of the IT environment which enables all other processes in the ITIL framework • Helps identify poorly performing/poor quality assets • Enables the reduction of Audit findings over time • Facilitates IT Service restoration for ITSCM/DR/BC • Enables legal and Regulatory Compliance requirements to be met through adherence to standards 40

Conclusions ITIL (ISO 20000) and Information Security (ISO 27001) are complementary And ITIL can be used to most effectively implement ISO 27001 recommendations 41