X 509 certificate management in NET VAMSI SRI










- Slides: 26

X. 509 certificate management in. NET -VAMSI SRI HARSHA VIDALA

Introduction A public key certificate is digitally signed document that is commonly used for authentication and secure exchange of information on open networks. A certificate securely binds a public key to the entity that holds the corresponding private key. Certificates are digitally signed by the issuing certification authority (CA). They create a trust relationship between two unknown entities.

Overview of X. 509 certificates Entities involved in X. 509 certificate management. o Subjects and Entities. o Certification Authority(CA). o Registration Authority(RA).

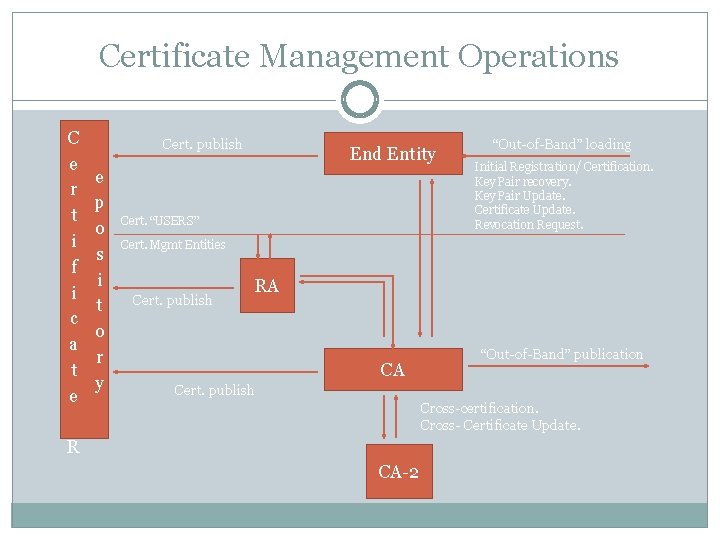
Certificate Management Operations C e r t i f i c a t e Cert. publish e p o s i t o r y End Entity Cert. “USERS” “Out-of-Band” loading Initial Registration/ Certification. Key Pair recovery. Key Pair Update. Certificate Update. Revocation Request. Cert. Mgmt Entities Cert. publish RA CA “Out-of-Band” publication Cert. publish Cross-certification. Cross- Certificate Update. R CA-2

Certificate Management Operations CA establishment. End entity initialization. Certification: Initial registration/Certification. Key pair Update. Certificate Update. CA Key pair update. Cross-certification Request. Cross-certificate Update.

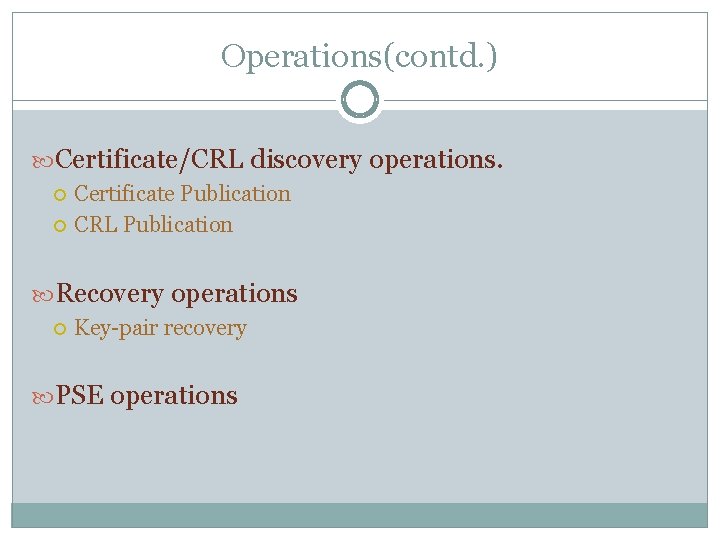
Operations(contd. ) Certificate/CRL discovery operations. Certificate Publication CRL Publication Recovery operations Key-pair recovery PSE operations

Implementation in ASP. NET

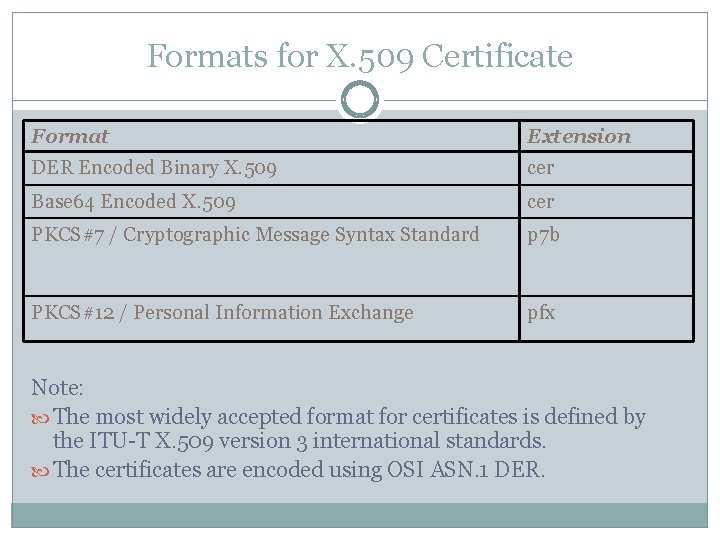
Formats for X. 509 Certificate Format Extension DER Encoded Binary X. 509 cer Base 64 Encoded X. 509 cer PKCS#7 / Cryptographic Message Syntax Standard p 7 b PKCS#12 / Personal Information Exchange pfx Note: The most widely accepted format for certificates is defined by the ITU-T X. 509 version 3 international standards. The certificates are encoded using OSI ASN. 1 DER.

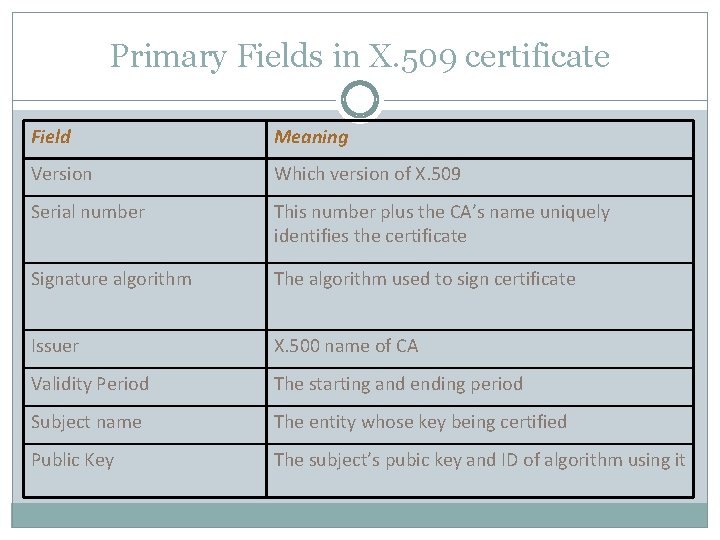
Primary Fields in X. 509 certificate Field Meaning Version Which version of X. 509 Serial number This number plus the CA’s name uniquely identifies the certificate Signature algorithm The algorithm used to sign certificate Issuer X. 500 name of CA Validity Period The starting and ending period Subject name The entity whose key being certified Public Key The subject’s pubic key and ID of algorithm using it

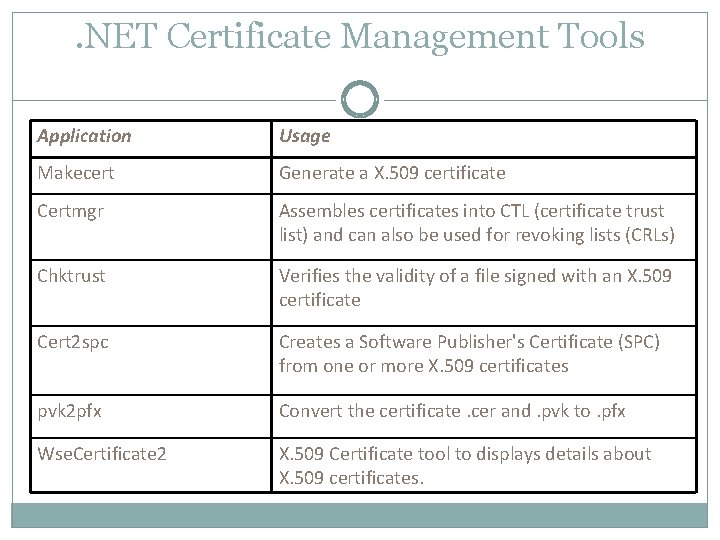
. NET Certificate Management Tools Application Usage Makecert Generate a X. 509 certificate Certmgr Assembles certificates into CTL (certificate trust list) and can also be used for revoking lists (CRLs) Chktrust Verifies the validity of a file signed with an X. 509 certificate Cert 2 spc Creates a Software Publisher's Certificate (SPC) from one or more X. 509 certificates pvk 2 pfx Convert the certificate. cer and. pvk to. pfx Wse. Certificate 2 X. 509 Certificate tool to displays details about X. 509 certificates.

Using X. 509 Certificates in. NET application 1. Create and manage X. 509 Certificate 2. Sign a SOAP Message Using an X. 509 Certificate 3. Verify Digital Signatures of SOAP Messages Signed by an X. 509 Certificate

STEP I Create and manage X. 509 Certificate

Obtain X. 509 Certificate Ø Ø Ø Purchase a certificate from a certificate authority, such as Veri. Sign, Inc Set up our own certificate service and have a certificate authority sign the certificates Set up our own certificate service and do not have the certificates signed Note: Whichever approach we take, the recipient of the SOAP request containing the X. 509 certificate must trust the X. 509 certificate.

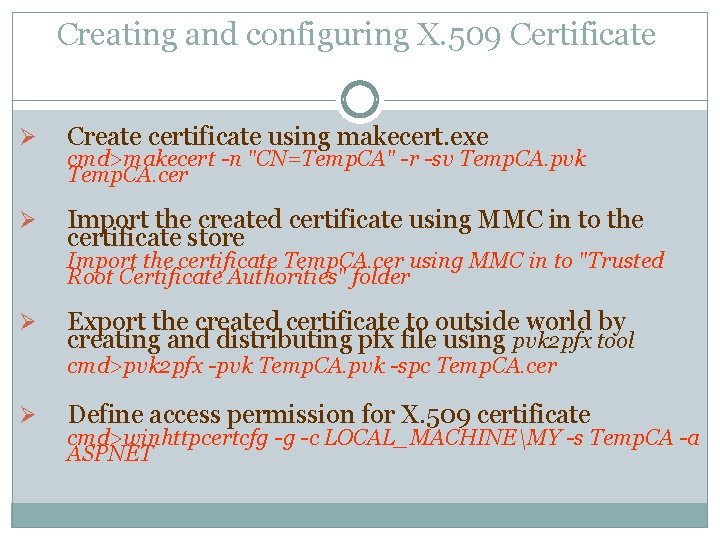
Creating and configuring X. 509 Certificate Ø Create certificate using makecert. exe Ø Import the created certificate using MMC in to the certificate store cmd>makecert -n "CN=Temp. CA" -r -sv Temp. CA. pvk Temp. CA. cer Import the certificate Temp. CA. cer using MMC in to "Trusted Root Certificate Authorities" folder Ø Export the created certificate to outside world by creating and distributing pfx file using pvk 2 pfx tool cmd>pvk 2 pfx -pvk Temp. CA. pvk -spc Temp. CA. cer Ø Define access permission for X. 509 certificate cmd>winhttpcertcfg -g -c LOCAL_MACHINEMY -s Temp. CA -a ASPNET

Make certificates accessible to application Ø Specify the certificate store that application uses to obtain X. 509 certificates <configuration> <microsoft. web. services 2> <security> <x 509 store. Location="Current. User" /> </security> </microsoft. web. services 2> </configuration> Ø Specify the account under which application is running read access to the file containing the private key associated with the X. 509 certificate. <process. Model enable="true|false" user. Name="username" password="password" />

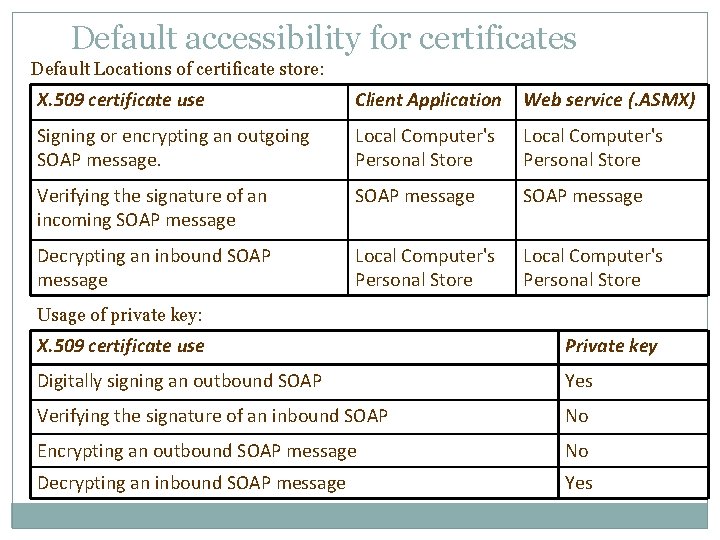
Default accessibility for certificates Default Locations of certificate store: X. 509 certificate use Client Application Web service (. ASMX) Signing or encrypting an outgoing SOAP message. Local Computer's Personal Store Verifying the signature of an incoming SOAP message Decrypting an inbound SOAP message Local Computer's Personal Store Usage of private key: X. 509 certificate use Private key Digitally signing an outbound SOAP Yes Verifying the signature of an inbound SOAP No Encrypting an outbound SOAP message No Decrypting an inbound SOAP message Yes

STEP II Sign a SOAP Message Using an X. 509 Certificate

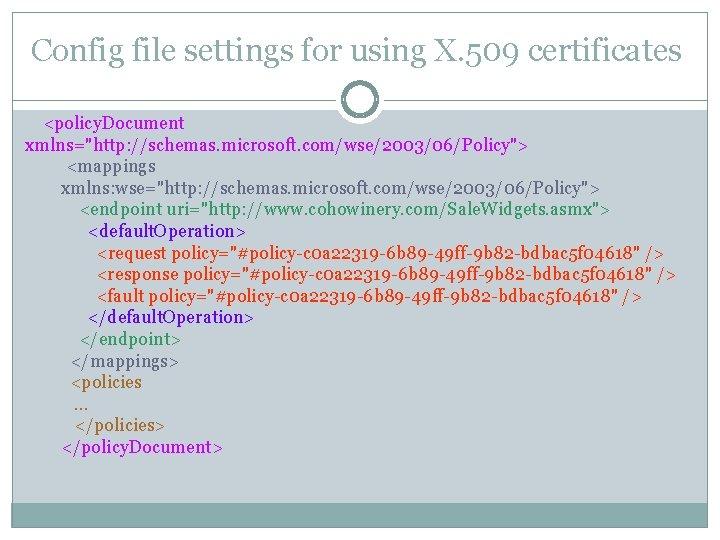
Config file settings for using X. 509 certificates <policy. Document xmlns="http: //schemas. microsoft. com/wse/2003/06/Policy"> <mappings xmlns: wse="http: //schemas. microsoft. com/wse/2003/06/Policy"> <endpoint uri="http: //www. cohowinery. com/Sale. Widgets. asmx"> <default. Operation> <request policy="#policy-c 0 a 22319 -6 b 89 -49 ff-9 b 82 -bdbac 5 f 04618" /> <response policy="#policy-c 0 a 22319 -6 b 89 -49 ff-9 b 82 -bdbac 5 f 04618" /> <fault policy="#policy-c 0 a 22319 -6 b 89 -49 ff-9 b 82 -bdbac 5 f 04618" /> </default. Operation> </endpoint> </mappings> <policies … </policies> </policy. Document>

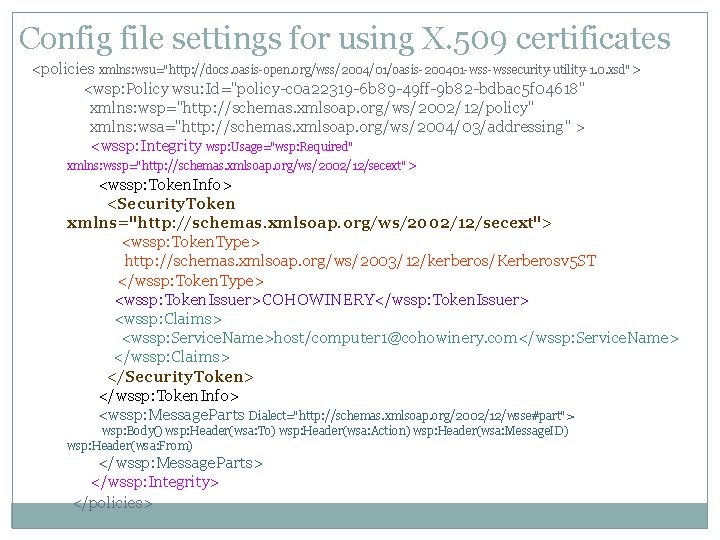
Config file settings for using X. 509 certificates <policies xmlns: wsu="http: //docs. oasis-open. org/wss/2004/01/oasis-200401 -wssecurity-utility-1. 0. xsd"> <wsp: Policy wsu: Id="policy-c 0 a 22319 -6 b 89 -49 ff-9 b 82 -bdbac 5 f 04618" xmlns: wsp="http: //schemas. xmlsoap. org/ws/2002/12/policy" xmlns: wsa="http: //schemas. xmlsoap. org/ws/2004/03/addressing" > <wssp: Integrity wsp: Usage="wsp: Required" xmlns: wssp="http: //schemas. xmlsoap. org/ws/2002/12/secext"> <wssp: Token. Info> <Security. Token xmlns="http: //schemas. xmlsoap. org/ws/2002/12/secext"> <wssp: Token. Type> http: //schemas. xmlsoap. org/ws/2003/12/kerberos/Kerberosv 5 ST </wssp: Token. Type> <wssp: Token. Issuer>COHOWINERY</wssp: Token. Issuer> <wssp: Claims> <wssp: Service. Name>host/computer 1@cohowinery. com</wssp: Service. Name> </wssp: Claims> </Security. Token> </wssp: Token. Info> <wssp: Message. Parts Dialect="http: //schemas. xmlsoap. org/2002/12/wsse#part"> wsp: Body() wsp: Header(wsa: To) wsp: Header(wsa: Action) wsp: Header(wsa: Message. ID) wsp: Header(wsa: From) </wssp: Message. Parts> </wssp: Integrity> </policies>

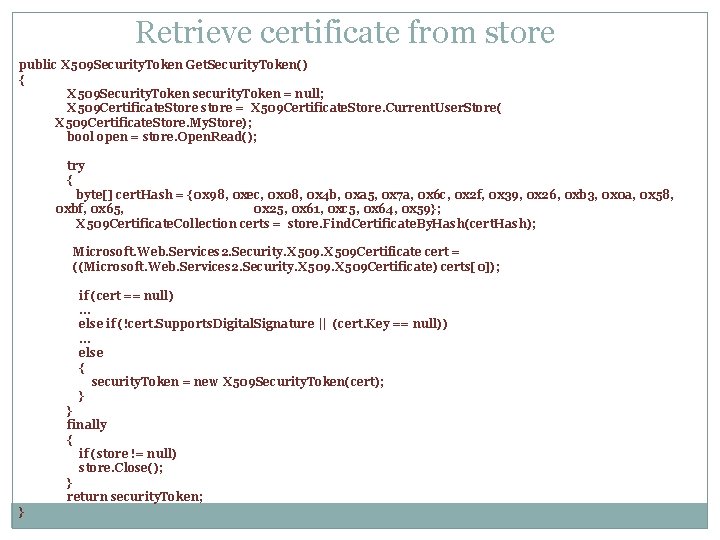
Retrieve certificate from store public X 509 Security. Token Get. Security. Token() { X 509 Security. Token security. Token = null; X 509 Certificate. Store store = X 509 Certificate. Store. Current. User. Store( X 509 Certificate. Store. My. Store); bool open = store. Open. Read(); try { byte[] cert. Hash = {0 x 98, 0 xec, 0 x 08, 0 x 4 b, 0 xa 5, 0 x 7 a, 0 x 6 c, 0 x 2 f, 0 x 39, 0 x 26, 0 xb 3, 0 x 0 a, 0 x 58, 0 xbf, 0 x 65, 0 x 25, 0 x 61, 0 xc 5, 0 x 64, 0 x 59}; X 509 Certificate. Collection certs = store. Find. Certificate. By. Hash(cert. Hash); Microsoft. Web. Services 2. Security. X 509 Certificate cert = ((Microsoft. Web. Services 2. Security. X 509 Certificate) certs[0]); if (cert == null) … else if (!cert. Supports. Digital. Signature || (cert. Key == null)) … else { security. Token = new X 509 Security. Token(cert); } } finally { if (store != null) store. Close(); } return security. Token; }

Code for signing SOAP messages q Call Get. Security. Token() to retrieve certificate X 509 Security. Token signature. Token = Get. Security. Token(); q Get the Soap. Context method for the SOAP request made to the Web service. Service 1 svc = new Service 1(); Soap. Context request. Context = svc. Request. Soap. Context; q Add the client's X. 509 certificate to the SOAP header. request. Context. Security. Tokens. Add(signature. Token); q Create a new instance of the Message. Signature class by using the X. 509 certificate just added to the SOAP header. Message. Signature sig = new Message. Signature(signature. Token); q Add the digital signature to the SOAP header. Request. Context. Security. Elements. Add(sig); q Specify the TTL for the SOAP message request. Context. Security. Timestamp. Ttl. In. Seconds = 60; q Call the Web service. svc. say. Hello();

STEP III Verify Digital Signatures of SOAP Messages Signed by an X. 509 Certificate

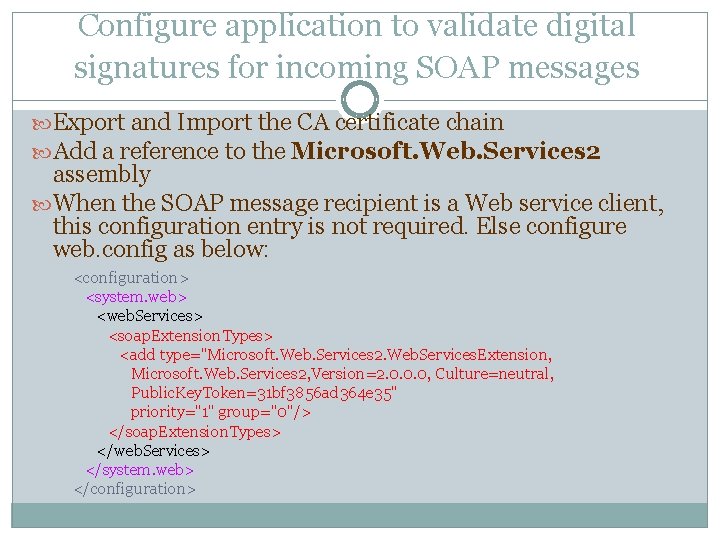
Configure application to validate digital signatures for incoming SOAP messages Export and Import the CA certificate chain Add a reference to the Microsoft. Web. Services 2 assembly When the SOAP message recipient is a Web service client, this configuration entry is not required. Else configure web. config as below: <configuration> <system. web> <web. Services> <soap. Extension. Types> <add type="Microsoft. Web. Services 2. Web. Services. Extension, Microsoft. Web. Services 2, Version=2. 0. 0. 0, Culture=neutral, Public. Key. Token=31 bf 3856 ad 364 e 35" priority="1" group="0"/> </soap. Extension. Types> </web. Services> </system. web> </configuration>

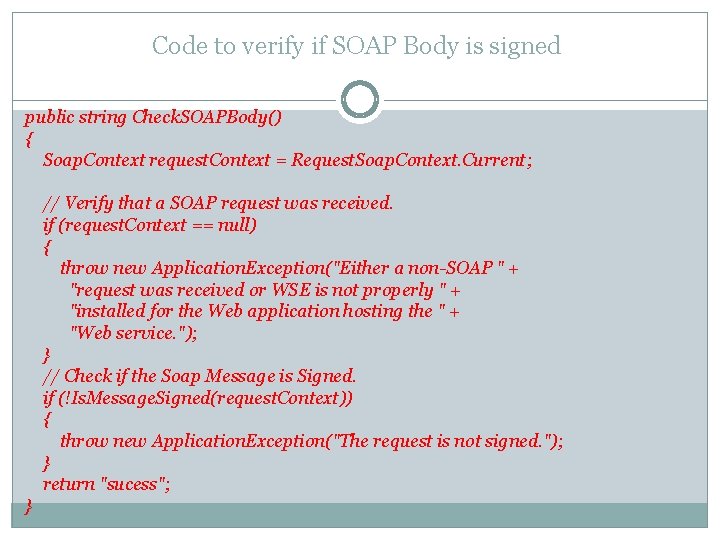
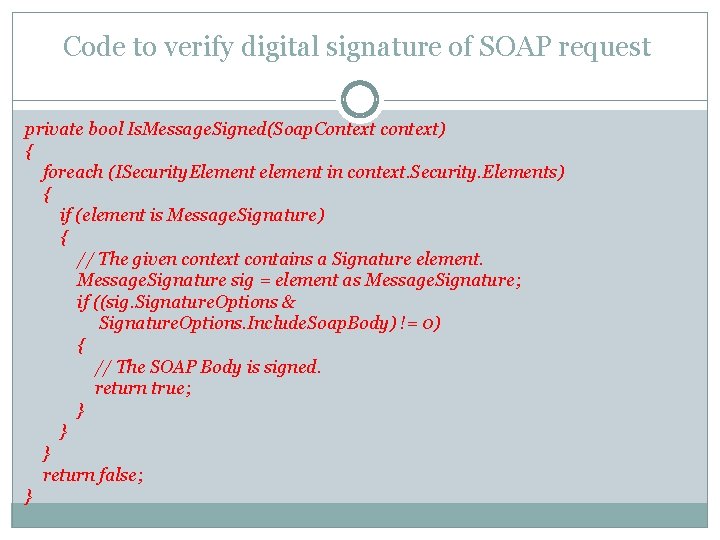
Code to verify if SOAP Body is signed public string Check. SOAPBody() { Soap. Context request. Context = Request. Soap. Context. Current; // Verify that a SOAP request was received. if (request. Context == null) { throw new Application. Exception("Either a non-SOAP " + "request was received or WSE is not properly " + "installed for the Web application hosting the " + "Web service. "); } // Check if the Soap Message is Signed. if (!Is. Message. Signed(request. Context)) { throw new Application. Exception("The request is not signed. "); } return "sucess"; }

Code to verify digital signature of SOAP request private bool Is. Message. Signed(Soap. Context context) { foreach (ISecurity. Element element in context. Security. Elements) { if (element is Message. Signature) { // The given context contains a Signature element. Message. Signature sig = element as Message. Signature; if ((sig. Signature. Options & Signature. Options. Include. Soap. Body) != 0) { // The SOAP Body is signed. return true; } } return false; }

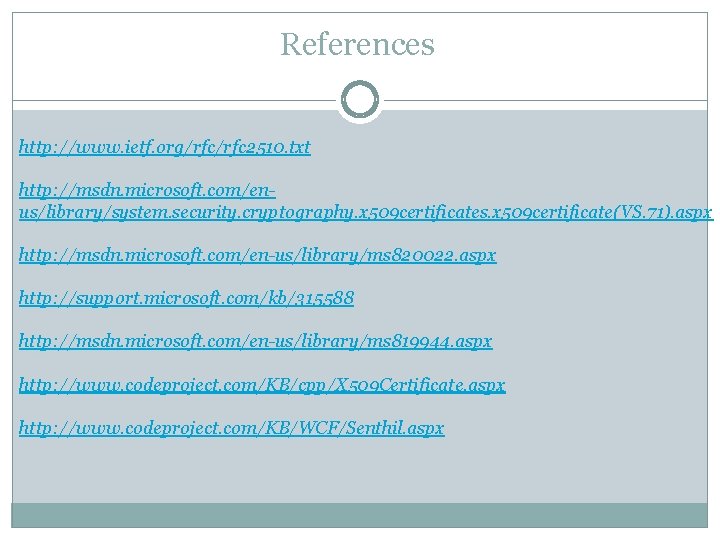
References http: //www. ietf. org/rfc 2510. txt http: //msdn. microsoft. com/enus/library/system. security. cryptography. x 509 certificates. x 509 certificate(VS. 71). aspx http: //msdn. microsoft. com/en-us/library/ms 820022. aspx http: //support. microsoft. com/kb/315588 http: //msdn. microsoft. com/en-us/library/ms 819944. aspx http: //www. codeproject. com/KB/cpp/X 509 Certificate. aspx http: //www. codeproject. com/KB/WCF/Senthil. aspx
 Sri rama sri rama sri manoharama
Sri rama sri rama sri manoharama X.509
X.509 X.509 certificate
X.509 certificate Phytosanitary certificate sample
Phytosanitary certificate sample Methyl bromide banned countries list
Methyl bromide banned countries list Sr 509 extension
Sr 509 extension X.509 attributes
X.509 attributes 753-509
753-509 Sr 509 extension
Sr 509 extension Sr 509 extension
Sr 509 extension 509 sports
509 sports Jux-509
Jux-509 Kerberos x.509 authentication service
Kerberos x.509 authentication service Kerberos x.509
Kerberos x.509 Republica romana 509 a 27 a.c
Republica romana 509 a 27 a.c X.509
X.509 B7 nach din 509
B7 nach din 509 Donkey protocol
Donkey protocol Kerberos motivation
Kerberos motivation Roma devleti
Roma devleti 509
509 Trimuvirate
Trimuvirate X 509
X 509 Entertainment in rome
Entertainment in rome Roma 509
Roma 509 Pki itu
Pki itu X.509 vs pgp
X.509 vs pgp