WWM CRC Annual Information Security Education and Awareness























- Slides: 29

WWM CRC Annual Information Security Education and Awareness Training 2017

Information Security Training 2017 Content Introduction to information security What is Information Security? Why is information security important? Information security at work Physical Information security Digital information security Information protection: How do we? Information security incidents and incident reporting Information Sharing WWM CRC Information Security Resources WWM CRC Information Security Manager contact details Signature Sheet

Introduction to Information Security What is information security? Information security is the protection of our valuable information and our business from information-related risks. It is about safeguarding the confidentiality, integrity and availability of our information to ensure that it is not disclosed to unauthorised individuals or organisations. THINK…. . CIA Confidentiality Integrity Availability

Introduction to Information Security Why is Information Security important? Because WWM CRC wants to avoid causing harm or distress to others. The CRC also wants to avoid the reputational damage and the financial penalties associated with information loss!

Information security at work What is it all about? The WWM CRC is dependent on the information it holds within its information systems The people the WWM CRC works with are concerned about the proper use of their personal data Threats to information systems, by cyber criminals for instance, are on the increase The information we hold and manage is vital to allow the WWM CRC to function and it is valuable to the person it relates to. But remember…. it is also valuable to criminals and, potentially, to terrorists. If we lose, or misuse, personal information it could cause serious harm or distress. Information must be protected when transmitted, stored and during processing.

Information Security at work A few facts about cyber crime… FACT. In the wake of their most serious breach, only 21% of businesses implemented additional staff training and communications to protect against the human risk in cyber security. 20% of businesses took no actions to prevent and protect their organisations from further breaches. FACT. 65% of large firms detected a cyber security breach or attack during 2016. 25% of these experienced a breach at least once a month. FACT. Meanwhile, the average total cost to a small business of its information breaches over 2016 was £ 3, 480. FACT. Only 35% of Britons are following the latest advice from Government to use strong passwords made up of three random words. Further reading available “Just delete” and “How much do you really know about Cyber Space? ” information sheets (issued May 2017) are available on WWM CRC shared drive or on request.

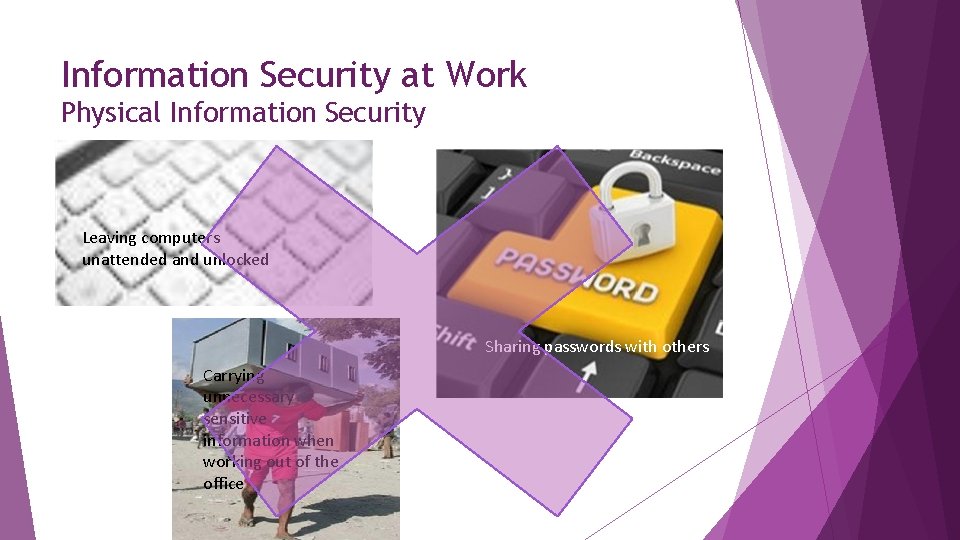
Information Security at Work Physical Information Security is concerned with the protection of tangible, informationrelated assets, such as computer systems and storage media, against real-world, physical, malicious and accidental threats such as unauthorised access, theft, loss, fire and flood. Security controls are put in place to reduce the probability or frequency of occurrence and/or the severity of the impact arising from an incident. WWM CRC Physical Information Security Policy covers topics such as: Further reading available Site security arrangements Site and Building passes, including access for staff, partners/third party contractors, visitors and service users Arrangements for protection of secure operational and working areas, including clear desk requirements Requirement to report all incidents relating to the compromise of physical controls, in line with WWM CRC Incident Management and Reporting Policy and Procedures Handling and Storage of Protectively Marked Paper and Removable Media assets

Information Security at Work Physical Information Security

Information Security at Work Physical Information Security Leaving computers unattended and unlocked Sharing passwords with others Carrying unnecessary sensitive information when working out of the office

Information Security at Work Digital Information Security What is Digital Information Security? Digital Security is the protection of digital identity – the network equivalent of the organisation’s physical identity. It includes the tools we use to secure our identity, assets and technology in the online and mobile world. Digital security risks from data theft and hacking are well known but they are an increasing risk to organisations WWM CRC Access Control Policy covers topics such as: Further reading available Security Clearance and Vetting requirements for access to WWM CRC systems and infrastructure User account management, including use of passwords and review of access privileges WWM CRC Network Security Policy covers topics such as Network operations and the responsibilities of authorised administrators, eg ICT staff.

Information Security at work Information Protection: How do we? The WWM Information Security Policy covers topics such as: Further reading available Government Security Classification Scheme (Protective Marking) and Handling of Information Assets Requirements of the Data Protection Act Subject/Data Access Requests Data Retention Information Asset Disposal and Destruction Information Sharing Agreements (ISAs) Secure e-mail. All WWM CRC staff are required to establish and maintain a secure Clear desk sweeps are undertaken at all office sites on a monthly basis to . CJSM. NET account which must be used for the transmission of official information to/from external organisations. monitor compliance with clear desk requirements. A warning and disciplinary process is in place for those who breach information security requirements, including any failure to secure official information in lockable storage.

Information Security at work Information Protection: How do we? Encryption, password protection, protective marking. The risk of compromising or losing information is minimised by the use of these handling requirements. For further information refer to the WWM CRC Information Security Policy. Further reading available The WWM CRC Remote Working Policy. This policy applies to all users who are authorised for remote access to WWM CRC systems, applications and information, and who work from remote working locations. It defines the responsibilities of all involved in the provision, authorisation and use of remote IT access facilities.

Information Security at work Information Protection: How do we? CJSM (Criminal Justice Secure Mail) must be used in ALL circumstances to send and receive e-mails that contain “OFFICIAL” information relating to Service Users. In order for this to work, WWM CRC partner agencies need to have signed up to CJSM themselves. All WWM CRC staff who access the CRC IT infrastructure should have a CJSM account created by IT staff. If you are unsure you need to contact the IT Service Desk. Once your CJSM account has been set up you use your CRC Outlook account to create a new e-mail. You must follow the instructions on the next three slides to make sure you are fully compliant with the requirements for sending and receiving Service User (Official) information securely.

Information Security at work Information Protection: How do we? CJSM (Criminal Justice Secure Mail) To send a secure e-mail. When you type in the recipient’s e-mail address YOU MUST ADD. cjsm. net to the end. EXAMPLES: joe. bloggs@probation. gsi. gov. uk. cjsm. net joe. bloggs@hmps. gsi. gov. uk. cjsm. net joe. bloggs@anywhere. pnn. police. uk. cjsm. net joe. bloggs@anyorganisation. org. uk. cjsm. net Any subsequent e-mails you send to this contact will present the. cjsm. net email address for you to select. Please take care to select the cjsm address rather than the . co. uk address E-mails sent internally within the CRC are already secure and so there is no requirement to insert the. CJSM. NET at the end of the e-mail address.

Information Security at work Information Protection: How do we? CJSM (Criminal Justice Secure Mail) To receive a secure e-mail. You will need to notify your contacts that you have a CJSM e-mail account for secure e-mails. Please notify external agencies to send all e-mails to you with the CJSM. net extension. Example: joe. bloggs@wwmcrc-probation. co. uk. cjsm. net. Once again you will need to ensure that they too are signed up to CJSM, otherwise they will be unable to send you any “OFFICIAL” information relating to service users. Received secure emails are accessible from your CRC Outlook e-mail inbox as long as the sender has also signed up to CJSM, eg they are sending from an email address which has. cjsm. net at the end.

Information Security at work Information Protection: How do we? CJSM (Criminal Justice Secure Mail) Managing your CJSM Account Your CJSM Account will automatically expire after 3 months and it is your responsibility to reset and maintain this in order to ensure that all emails containing Service User information continue to be sent and received securely. If you are unsure if your Account is ‘Active’ or not, you can check the status of your CJSM by logging onto your CJSM Account via the Icon on your desktop, finding your Personal Details and at the bottom of the screen your status is displayed (see below). User Role: Has Hosted Mailbox: Status: Ex Directory: Login name: Last Login: Date Added: Organisation Administrator No Active No Joe. bloggs@wwmcrc-probation. co. uk Fri May 19 13: 07: 29 BST 2017 Wed Mar 16 12: 08: 47 GMT 2016

Information security at work Government Security Classification Scheme: Protective Marking OFFICIAL The majority of information that is created / processed by WWM CRC. Includes routine business operations, including offender and staff personal information, and services, some of which could have damaging consequences if lost, stolen or published in the media, but are not subject to a heightened threat profile. SECRET Official information does not require a protective marking Very sensitive information that justifies heightened protective measures to defend against determined / highly capability threats. Where compromise may seriously damage military capabilities, international relations or the investigation of serious organised crime. TOP SECRET HMG’s most sensitive information requiring the highest levels of protection from the most serious threats. Where compromise could cause widespread loss of life or else threaten the security or economic wellbeing of the country or friendly nations. A limited amount of information will be particularly sensitive but will still come within OFFICIAL if it is not subject to the threat sources for which SECRET is designed, even if its loss or compromise could have severely damaging consequences. This information can be described as OFFICIAL SENSITIVE and the need to know principle must be rigorously enforced, particularly where it may be being shared outside of a routine or well understood business process. This more sensitive information must be identified by being marked ‘OFFICIAL SENSITIVE’. This marking alerts users to the enhanced level of risk and that additional controls are required.

Information Security at work Information Security Incidents and Incident Reporting Further reading available WWM CRC Security Incident Management Policy defines an incident as “the occurrence of any event or action that results from: an actual and/or potential compromise (breach) of WWM CRC information, WWM CRC information assets (information assets have recognisable and manageable value, risk, content and lifecycle and can be stored in any manner e. g. assets in physical format such a paper files (operational and financial); assets in electronic format, such as electronic files and computer media such as CD-ROMs which contain information assets) and/or the WWM CRC communications infrastructure or a failure of information security controls which have a significant probability of compromising business operations. ”

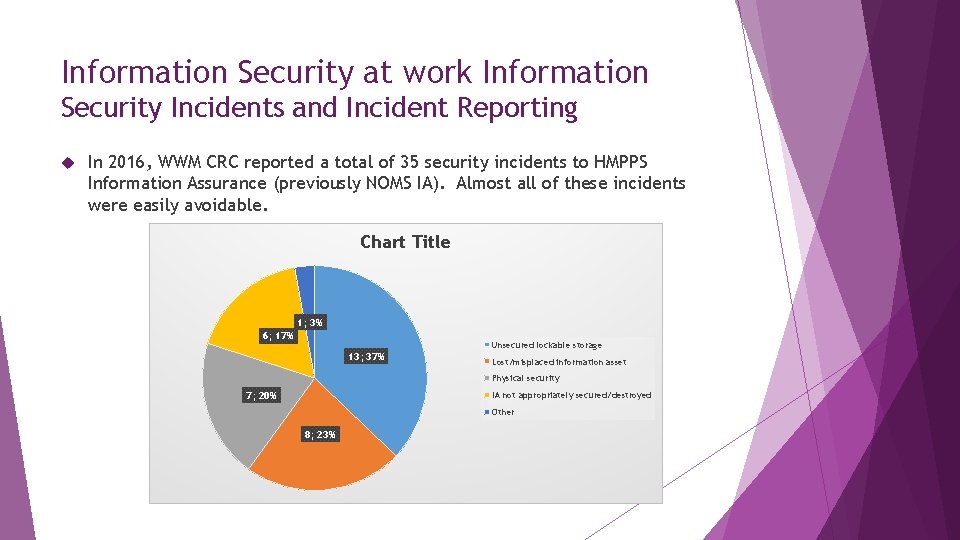
Information Security at work Information Security Incidents and Incident Reporting In 2016, WWM CRC reported a total of 35 security incidents to HMPPS Information Assurance (previously NOMS IA). Almost all of these incidents were easily avoidable. Chart Title 1; 3% 6; 17% Unsecured lockable storage 13; 37% Lost/misplaced information asset Physical security IA not appropriately secured/destroyed 7; 20% Other 8; 23%

Information Security at work Information Security Incidents and Incident Reporting Four MUSTS about incident reporting: Further reading available Information Security Incidents MUST be reported IMMEDIATELY UPON DETECTION. The WWM CRC is required to notify Information Assurance in HMPPS WITHIN 1 HOUR OF DETECTION. Incidents MUST be responded to in a quick, effective and orderly manner in order to reduce the negative effect of incidents, to repair damage and to inform policy and mitigate future risks. All WWM CRC staff, partners and visitors, including contractors and third parties MUST be aware of the process for reporting Information Security incidents and their responsibility to report such incidents. All information Security Incidents MUST be reported promptly in line with the WWM CRC Incident Reporting and Management Process.

Information Security at work Information Security Incidents and Incident Reporting The Process IF YOU IDENTIFY AN ACTUAL OR “NEAR MISS” SECURITY BREACH YOU MUST: 1. Discuss it with a WWM CRC Manager or Information Security Manager IMMEDIATELY. They will decide whether or not the incident is a security breach. 2. If the incident is a security breach THE MANAGER YOU DISCUSSED IT WITH must report it to HMPPS Information Assurance Team WITHIN ONE HOUR, either by telephone or by secure e-mail. 3. YOU must then complete the WWM CRC Security Incident Notification Form and follow the instructions on the form which tell you who to send it to. Further 4. reading available If you identify a security breach “out of hours” and do not have access to a manager, you must report it to HMPPS Information Assurance Team yourself by telephone or by secure e-mail. You will then need to follow this up by completing the WWM CRC Security Incident Notification Form on the next working day. Full information and further guidance is available in the WWM CRC Incident Reporting and Management Process document.

Information Security at work Information Security Incidents and Incident Reporting Is this a security breach? A few examples to think about. “I’ve lost/misplaced my RSA token (or building access fob); it might be at home. Do I need to report it? YES. Even if it is subsequently found, you must report it. “I’ve found a diary/notebook/papers in the kitchen/meeting room. Do I need to report it? ” YES. Even if you know who it belongs to, it is still a security breach as it could have been picked up or the content seen by an unauthorised person. “There’s someone just followed me through a secure door but I don’t know who they are and I didn’t like to ask. Do I need to report it? ” YES. OK, so you made a mistake…but you recognised it. It still needs to be reported because it was an incident. “I’ve just received a text message from my manager who is on leave and there is some service user information (names) in it. I’ve deleted it now but do I need to report it? ” YES. Speak to another Manager to get it reported within the hour; don’t wait for your own manager to return to work

Information Security at work Information Sharing information is an important part of our work but we must keep information security in mind. The WWM CRC has a number of information sharing agreements in place with key partners. The CRC is also bound by the Probation Instruction PI 15/2016: Information Sharing Policy. The Information Commissioner’s Office website www. ico. org. uk provides a data sharing checklist. Always ask: 1. Is the sharing justified? 2. Do you have the power to share? 3. If you decide to share: What information do you need to share? How should the information be shared? REMEMBER: DATA PROTECTION LEGISLATION IS NOT A BARRIER TO APPROPRIATE INFORMATION SHARING.

Information Security at work Information Sharing What can I share/tell them? A few examples to think about. I have a Social Worker on the ‘phone asking me about one of the service users on my caseload. What can I tell them? I have the mother of a service user on the ‘phone asking me for information. What can I tell her? I have a police detective on the phone asking me for a current address and contact details of a service user on my caseload. What can I tell them? A service user is on the phone asking me when his mate is being released from custody? Can I tell him?

Information Security at work Information Sharing What can I share/tell them? ANSWERS 1. Is there a clear and legitimate purpose for sharing? If yes, go to question 2. If no, DON’T SHARE. 2. Does the information enable an individual to be identified? If yes, go to question 3. If no, you can share but need to think about how. 3. Is the information confidential? If yes, go to question 4. If no, you can share but need to think about how. 4. Do you have consent to share? If yes – you can share but need to think about how. If no, go to question 5. Is there another reason to share the information such as to fulfil a public function or to protect the vital interests of the information subject? If yes, you can share but need to think about how. If no, DON’T SHARE. ALWAYS consider the impact of disclosing information on the information subject and any third parties.

Information Security at work Resources There a number of documents referred to in this presentation which can all be accessed electronically on the WWM CRC file share. Hard or e-mail copies are available on request from the WWM CRC Information Security Manager, Karen Simmonds. WWM CRC Information Security Policies and Procedures: . . All_UsersPolicies_&_ProceduresWWM CRC PoliciesInformation Security Policies Probation Instructions: . . All_UsersProbation_Instructions WWM CRC Information Security advice and Guidance: . . All_UsersInformation_Security Information Commissioner’s Office: https: //ico. org. uk

Information Security at work

Information Security at work WWM CRC Information Security Manager: Karen Simmonds Direct line: 01905 677149 Email: karen. simmonds@wwmcrc-probation. co. uk

Information Security at work Information Security Awareness and Education Training 2017 Please now e. mail learninganddevelopment@wwmcrc-probation. co. uk and your line manager to confirm that you have completed this training. Alternatively, print this page, sign and date it, and scan/return it to the e. mail address above. I confirm that I have read and understood the 2017 Information Security Awareness and Education Training Power. Point presentation. Name: Date: Job Title: Office Base: Line Manager:
 Security annual refresher training
Security annual refresher training Security education training and awareness seta program
Security education training and awareness seta program Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Cyber security crc
Cyber security crc Private security
Private security Visa international security model in information security
Visa international security model in information security Cnss model
Cnss model Suspicious mail training
Suspicious mail training Cjis training
Cjis training Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Refresher briefing
Refresher briefing Security awareness nulmeting
Security awareness nulmeting Security awareness game
Security awareness game Security awareness screensavers
Security awareness screensavers Chemical sensitivity symptoms
Chemical sensitivity symptoms Information technology workshop
Information technology workshop Webroot security awareness training pricing
Webroot security awareness training pricing Security awareness program
Security awareness program Stanford university cio
Stanford university cio Opsec awareness
Opsec awareness Cyber awareness voorbeeld
Cyber awareness voorbeeld Uc cyber security awareness training answers
Uc cyber security awareness training answers Security awareness ciampa
Security awareness ciampa Quid pro quo cyber security
Quid pro quo cyber security Cda security awareness training
Cda security awareness training Annual status of education report
Annual status of education report For p = 110011 and m = 11100011, find the crc
For p = 110011 and m = 11100011, find the crc Crc roles and responsibilities
Crc roles and responsibilities Wireless security in cryptography
Wireless security in cryptography E commerce security meaning
E commerce security meaning