SECURITY AWARENESS ANNUAL TRAINING Texas Hospital Association Annual














- Slides: 20

SECURITY AWARENESS ANNUAL TRAINING Texas Hospital Association Annual Security Awareness Training previou s next

SECURITY AWARENESS ANNUAL TRAINING previou s next Who Must Complete This Training? As part of our Security Awareness Program all employees of Texas Hospital Association must complete this training on an annual basis. In addition, contractors with facility or system access must also complete this training. All new employees must complete this training within 30 days of employment and annually thereafter. (effective 8 -1 -2014) After you have reviewed the training slides, read and print the certificate found on the last page. Sign and date the certificate, then give it to your immediate supervisor and keep a copy for your own records. 2

SECURITY AWARENESS ANNUAL TRAINING previou s next Why You Need This Training This training will help you to: 1. Understand your security responsibilities before being permitted access to the THA Network. 2. Understand privacy and sensitive data. 3. Understand the security vulnerabilities and threats that could impact you and THA. 4. Protect your personal information at work and at home. 3

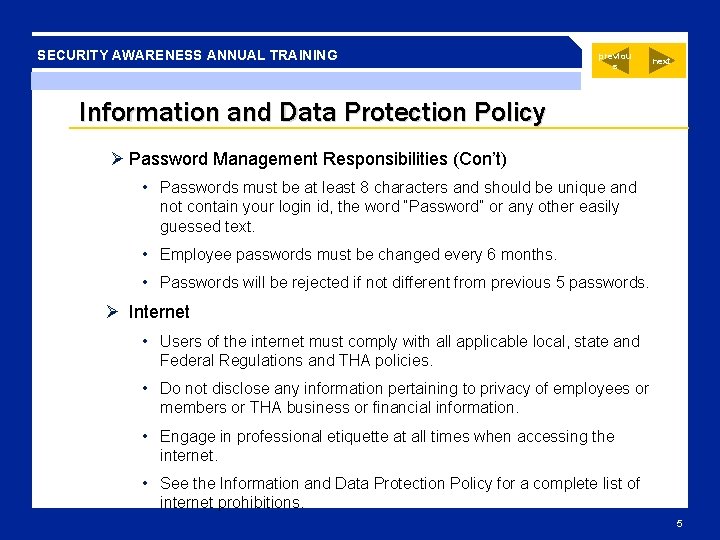
SECURITY AWARENESS ANNUAL TRAINING previou s next Information and Data Protection Policy Information and Data Protection Polices are comprised of many sub policies focusing on specific areas (mobile, data retention, data integrity etc. ). All these policy's combined are called the Information and Data Protection Policy. These policy’s in the THA handbook and on T-net should be read and understood by all employees, and the signature page from the Employee Handbook serve as notice of receipt. The policies address several areas: Ø Understanding that all users are monitored and there should be no expectation of privacy rights for any information created, received and/or stored on any THA computer or mobile device. Ø Password Management Responsibilities – • Under no circumstances should a password be shared or delegated to others. • You are accountable for all work and other activities that occur using your password. • An effective password will have a mix of lower and upper case letters, numerals and special characters. 4

SECURITY AWARENESS ANNUAL TRAINING previou s next Information and Data Protection Policy Ø Password Management Responsibilities (Con’t) • Passwords must be at least 8 characters and should be unique and not contain your login id, the word “Password” or any other easily guessed text. • Employee passwords must be changed every 6 months. • Passwords will be rejected if not different from previous 5 passwords. Ø Internet • Users of the internet must comply with all applicable local, state and Federal Regulations and THA policies. • Do not disclose any information pertaining to privacy of employees or members or THA business or financial information. • Engage in professional etiquette at all times when accessing the internet. • See the Information and Data Protection Policy for a complete list of internet prohibitions. 5

SECURITY AWARENESS ANNUAL TRAINING previou s next Information and Data Protection Policy Ø Email • THA prohibits the use of the email system in ways that are discriminatory, harassing, derogatory, obscene or offensive to others. Users encountering or receiving this type of email should report it to their manager or the Human Resources Department. • Your email is not private and anything in your email is subject to review. • Do not engage in email chain letters or respond to any that you receive. • Do not open attachments or click on any links embedded in an email unless you know the source. • Do not provide any privacy information using email. Vendors never ask for account numbers or SSNs via email. Always call the source when in doubt. • Do not forward emails to co-workers unless you know the source and they are work related. If you receive spam (junk email) from a fellow employee, notify both the employee and IT that the employee’s email 6

SECURITY AWARENESS ANNUAL TRAINING previou s next Information and Data Protection Policy Ø Computer and Software Use • Computers issued by THA (desktops, laptops, mobile devices) are the property of THA and THA prohibits the removal, relocation or alteration of equipment without notification and approval of the IT Department. • Employees must take reasonable measures to secure mobile devices; e. g. , do not leave visible in car, do not check with luggage, and ensure password protection. • Do not duplicate software or related documentation. • Do not put personal or non-standard software on devices without approval from IT and your department manager. • Keep your virus protection current and never disable it. 7

SECURITY AWARENESS ANNUAL TRAINING previou s next Personal Mobile Devices The e-mail system and all communication and information initiated, received or transmitted by the e-mail systems is a THA asset and is to be protected and used for the purpose of conducting THA business. In exchange for allowing you to use your personal mobile device (PMD) in our corporate environment; you agree as follows: You agree to abide by the Mobile Device Policy. If your device is lost or stolen, you must notify the Vice President of Information Technology immediately to report the loss. Personal (HR) and financial information should not be stored on personal mobile devices, even if that data is contained within normally allowed channels e. g. e-mail. IT has the authority to disable network access capabilities and remotely wipe data on personal devices (and personal data if necessary) should the need arise, including for security reasons or if employment is terminated by either party. 8

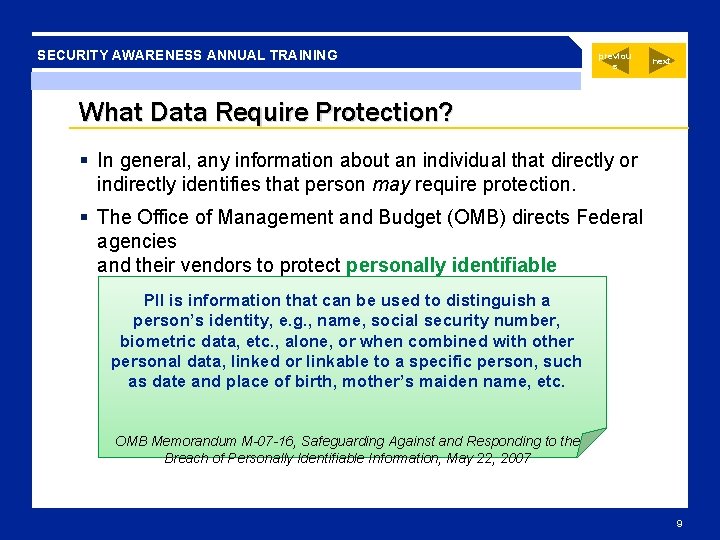
SECURITY AWARENESS ANNUAL TRAINING previou s next What Data Require Protection? In general, any information about an individual that directly or indirectly identifies that person may require protection. The Office of Management and Budget (OMB) directs Federal agencies and their vendors to protect personally identifiable information (PII). PII is information that can be used to distinguish a person’s identity, e. g. , name, social security number, biometric data, etc. , alone, or when combined with other personal data, linked or linkable to a specific person, such as date and place of birth, mother’s maiden name, etc. OMB Memorandum M-07 -16, Safeguarding Against and Responding to the Breach of Personally Identifiable Information, May 22, 2007 9

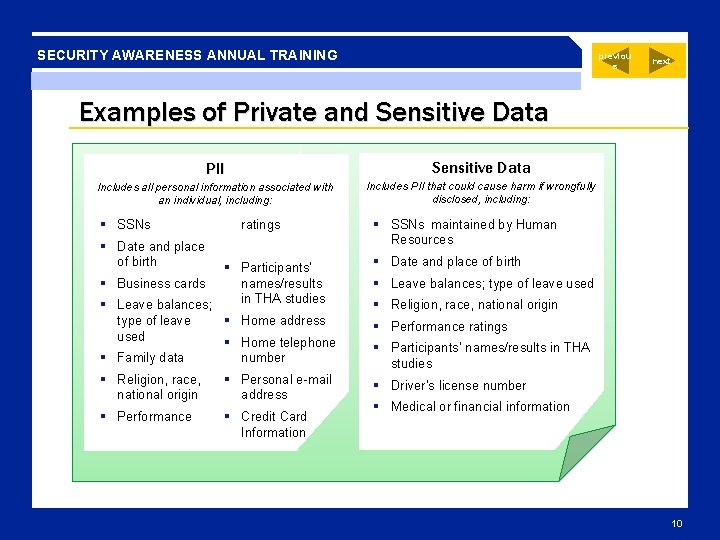
SECURITY AWARENESS ANNUAL TRAINING previou s next Examples of Private and Sensitive Data PII Sensitive Data Includes all personal information associated with an individual, including: Includes PII that could cause harm if wrongfully disclosed, including: SSNs ratings Date and place of birth Participants’ names/results Business cards in THA studies Leave balances; Home address type of leave used Home telephone Family data number Religion, race, national origin Personal e-mail address Performance Credit Card Information SSNs maintained by Human Resources Date and place of birth Leave balances; type of leave used Religion, race, national origin Performance ratings Participants’ names/results in THA studies Driver’s license number Medical or financial information 10

SECURITY AWARENESS ANNUAL TRAINING previou s next Safeguarding Privacy Data Minimize Privacy Data Use Collect only data that you are authorized to collect, and at the minimum level necessary to accomplish a required purpose. Limit number of copies containing privacy data to the minimum needed. Secure Privacy Data When not in use, store data in an appropriate access-controlled environment. Use fictional personal data for presentations or training. Review documents for privacy and appropriateness prior to posting on THA web site. Safeguard the Transfer of Privacy Data Do not e-mail privacy data unless it is encrypted or in a password protected attachment. Use services that provide tracking and confirmation of delivery when mailing or shipping PII offsite. Dispose of Privacy Data Properly Delete/dispose of data at the end of its retention period and place in bins for shredding. Safeguard data in any format around your work area. Disclose privacy data to only to those authorized to see it. 11

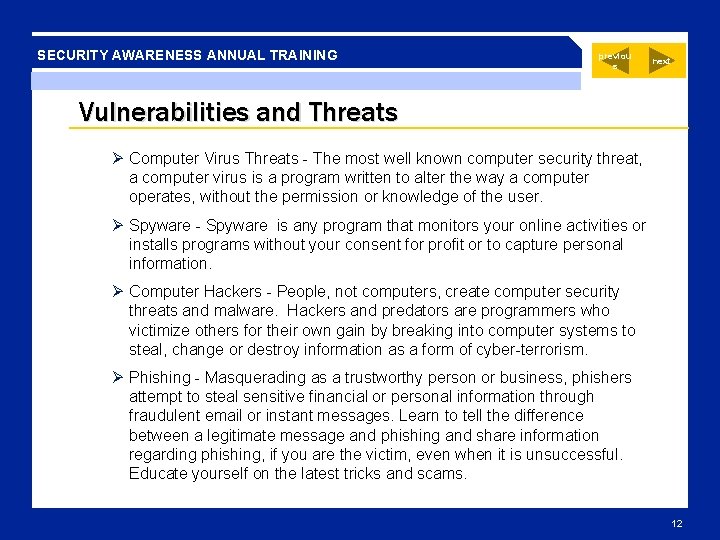
SECURITY AWARENESS ANNUAL TRAINING previou s next Vulnerabilities and Threats Ø Computer Virus Threats - The most well known computer security threat, a computer virus is a program written to alter the way a computer operates, without the permission or knowledge of the user. Ø Spyware - Spyware is any program that monitors your online activities or installs programs without your consent for profit or to capture personal information. Ø Computer Hackers - People, not computers, create computer security threats and malware. Hackers and predators are programmers who victimize others for their own gain by breaking into computer systems to steal, change or destroy information as a form of cyber-terrorism. Ø Phishing - Masquerading as a trustworthy person or business, phishers attempt to steal sensitive financial or personal information through fraudulent email or instant messages. Learn to tell the difference between a legitimate message and phishing and share information regarding phishing, if you are the victim, even when it is unsuccessful. Educate yourself on the latest tricks and scams. 12

SECURITY AWARENESS ANNUAL TRAINING previou s next Security Precautions we all should take Creating Secure Passwords Combine upper and lower case letters, numbers, special characters. Do not use personal information. Do not use common phrases or words. Do not write down your password; memorize it. Do not share your password with anyone, ever! Following Physical Security Procedures Use your own security key. Never grant access for someone else. Report suspicious activity. 13

SECURITY AWARENESS ANNUAL TRAINING previou s Security Precautions Avoiding Social Engineering Attempts Avoiding Phishing Attempts Delete any suspicious email. Give out computer or network information. When in doubt, always contact the emailing organization via telephone or call IT rather than responding to the email. Follow instructions from unverified personnel. Do not respond to emails that claim you will receive money. Do not: Participate in unapproved telephone surveys. Give out personal information. Give out your password to anyone, except IT staff. Reveal any personal information in an email. . Open suspicious email. Access the web by selecting links in emails or pop-up messages. Enter sensitive or financial information into pop-up windows next

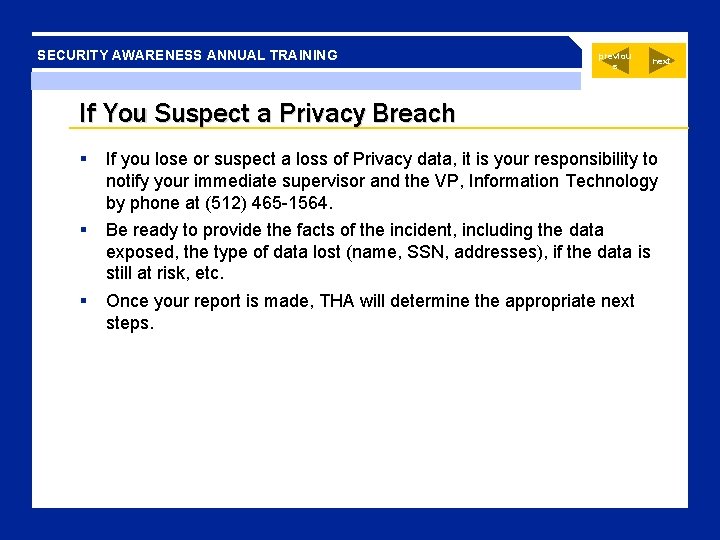
SECURITY AWARENESS ANNUAL TRAINING previou s next If You Suspect a Privacy Breach If you lose or suspect a loss of Privacy data, it is your responsibility to notify your immediate supervisor and the VP, Information Technology by phone at (512) 465 -1564. Be ready to provide the facts of the incident, including the data exposed, the type of data lost (name, SSN, addresses), if the data is still at risk, etc. Once your report is made, THA will determine the appropriate next steps.

SECURITY AWARENESS ANNUAL TRAINING previou s next There are Risks if Data is Lost or Stolen Risks to the Victim Identity theft, including financial loss and impact on job, credit, and reputation; Embarrassment; Emotional distress. Risks to the THA Employee Disciplinary action or loss of employment; Penalties under the Privacy Act; and Diminished reputation. Risks to THA Diminished reputation; Costs of mitigation; Litigation and associated costs; Impact on member and client processes; and Loss of member trust.

SECURITY AWARENESS ANNUAL TRAINING previou s next Nine things you should be destroying if outdated Old Credit Cards ID Badges/Fobs Computer Hard Disk Drives Thumb Drives / Flash Drives / Memory Cards Outdated or unused Cell/Smart Phones Optical Media – CDs/DVDs Other Mag Media – Floppy & Zip Disks, Computer Backup Tapes, Audio or Video Tapes Old versions of sensitive documentation From “Nine Things You’re Not Destroying, But Should Be!” Security Magazine, January 2007 http: //www. securitymagazine. com

SECURITY AWARENESS ANNUAL TRAINING Home Security Tips Install system and application security updates and patches. Keep anti-virus software up-to-date. Regularly scan files for viruses. Install spyware protection software. Turn on firewall protection. Require confirmation before installing mobile code. Back up your files!!! previou s next

SECURITY AWARENESS ANNUAL TRAINING previou s Questions about Security? Contact the VP of Information Technology or Human Resources For more information regarding security: Password Policy Access Control Policy Employee Handbook Information and Data Integrity Policy Mobile Device Policy Physical and Environmental Protection Policy next

SECURITY AWARENESS ANNUAL TRAINING Certificate of Completion I certify that I have completed Texas Hospital Association’s Security Awareness Annual Training as Required for Employees and Contractors. I have been informed and understand that any security violations must be reported to my supervisor or IT as soon as possible. PRINT NAME SIGNATURE DATE 20
 Annual security refresher training
Annual security refresher training Cvs privacy awareness and hipaa privacy training
Cvs privacy awareness and hipaa privacy training Ncic restricted files
Ncic restricted files Seta program 5 steps
Seta program 5 steps Chemical security awareness training
Chemical security awareness training Webroot security awareness training
Webroot security awareness training Security training and threat awareness
Security training and threat awareness Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Good computing practices
Good computing practices Cda security awareness training
Cda security awareness training Private secuirty
Private secuirty Average annual rainfall in south texas brush country
Average annual rainfall in south texas brush country What are the ecoregions of texas
What are the ecoregions of texas Cyber awareness onderzoek
Cyber awareness onderzoek Security awareness game
Security awareness game Security awareness screensavers
Security awareness screensavers Workshop security awareness
Workshop security awareness Security awareness program
Security awareness program Stanford university cio
Stanford university cio Printer security awareness
Printer security awareness Security awareness voorbeeld
Security awareness voorbeeld