Trusted Federated Identity and Access Management to provide



- Slides: 15

Trusted Federated Identity and Access Management to provide the Cornerstone for Cyber Defense.

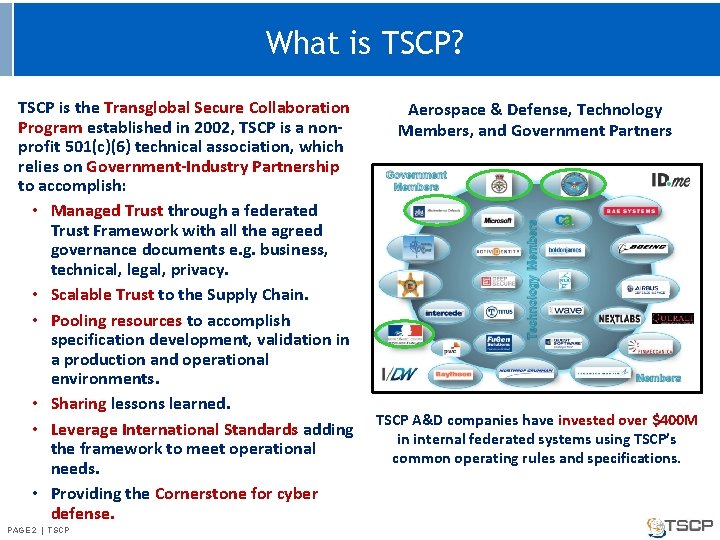
What is TSCP? TSCP is the Transglobal Secure Collaboration Program established in 2002, TSCP is a nonprofit 501(c)(6) technical association, which relies on Government-Industry Partnership to accomplish: • Managed Trust through a federated Trust Framework with all the agreed governance documents e. g. business, technical, legal, privacy. • Scalable Trust to the Supply Chain. • Pooling resources to accomplish specification development, validation in a production and operational environments. • Sharing lessons learned. • Leverage International Standards adding the framework to meet operational needs. • Providing the Cornerstone for cyber defense. PAGE 2 | TSCP Aerospace & Defense, Technology Members, and Government Partners TSCP A&D companies have invested over $400 M in internal federated systems using TSCP’s common operating rules and specifications.

What Does TSCP Do? SPECIFICATIONS DEVELOPMENT. * Develops common specifications for secure collaboration solutions across the TSCP membership that align to government requirements. The specifications fall into these categories: • Secure information exchange • Identity credentials/digital identities and attributes • Federated identity • Information assurance • Data labeling and protection and ITAR/Export VALIDATION THROUGH PRODUCTION REFERENCE LAB. Before TSCP publishes its specifications, the capability is in production with two or more members. GOVERNANCE. Establishes policy and governance for TSCP Solutions. • • Interoperable Identity Federation Trust Framework Common Operating Rules Legal Framework & Allocation of Liabilities Accreditation & Trustmark FEDERATED HUB. Hosts a Federated Hub for TSCP Membership that enables secure collaboration between TSCP membership and government customers. PAGE 3 | TSCP

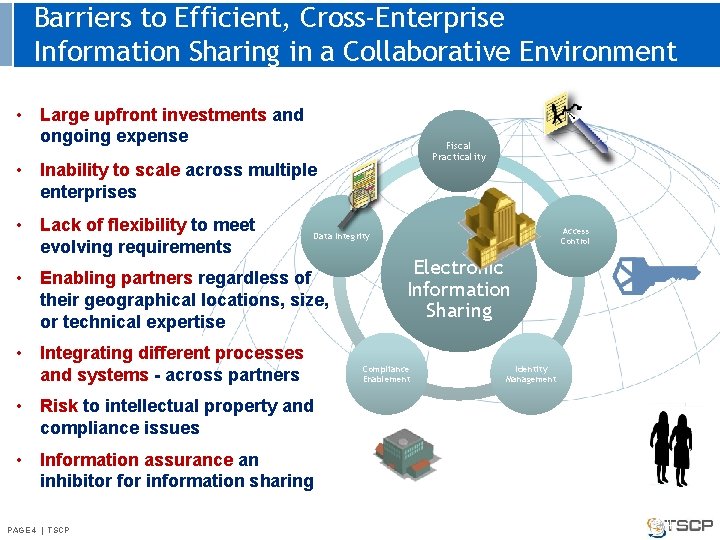
Barriers to Efficient, Cross-Enterprise Information Sharing in a Collaborative Environment • Large upfront investments and ongoing expense Fiscal Practicality • Inability to scale across multiple enterprises • Lack of flexibility to meet evolving requirements Access Control Data Integrity • Enabling partners regardless of their geographical locations, size, or technical expertise • Integrating different processes and systems - across partners Electronic Information Sharing Compliance Enablement Identity Management • Risk to intellectual property and compliance issues • Information assurance an inhibitor for information sharing PAGE 44 || TSCP PAGE TSCP 4

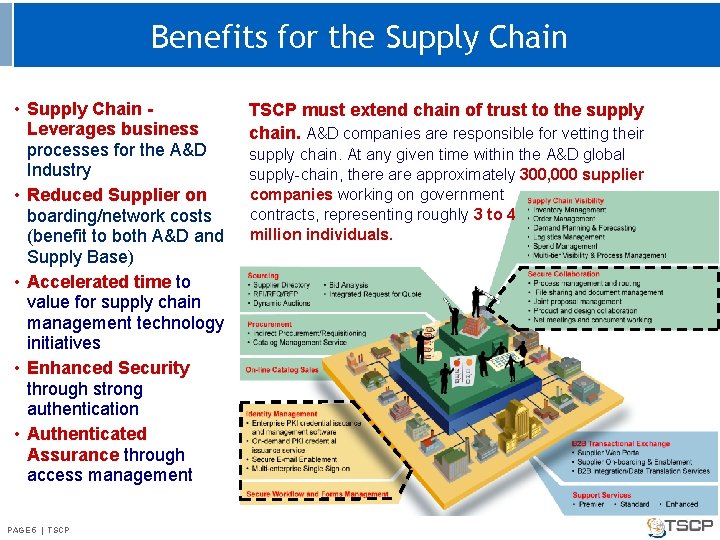
Benefits for the Supply Chain • Supply Chain Leverages business processes for the A&D Industry • Reduced Supplier on boarding/network costs (benefit to both A&D and Supply Base) • Accelerated time to value for supply chain management technology initiatives • Enhanced Security through strong authentication • Authenticated Assurance through access management PAGE 55 || TSCP PAGE TSCP must extend chain of trust to the supply chain. A&D companies are responsible for vetting their supply chain. At any given time within the A&D global supply-chain, there approximately 300, 000 supplier companies working on government contracts, representing roughly 3 to 4 million individuals.

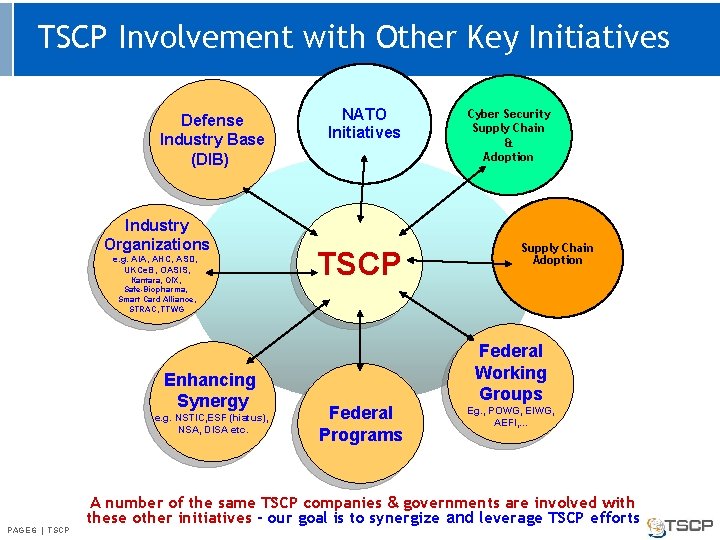
TSCP Involvement with Other Key Initiatives Defense Industry Base (DIB) Industry Organizations e. g. AIA, AHC, ASD, UKCe. B, OASIS, Kantara, OIX, Safe-Biopharma, Smart Card Alliance, STRAC, TTWG Enhancing Synergy e. g. NSTIC, ESF (hiatus), NSA, DISA etc. PAGE 66 || TSCP NATO Initiatives TSCP Federal Programs Cyber Security Supply Chain & Adoption Supply Chain Adoption Federal Working Groups Eg. , POWG, EIWG, AEFI, . . . A number of the same TSCP companies & governments are involved with these other initiatives - our goal is to synergize and leverage TSCP efforts

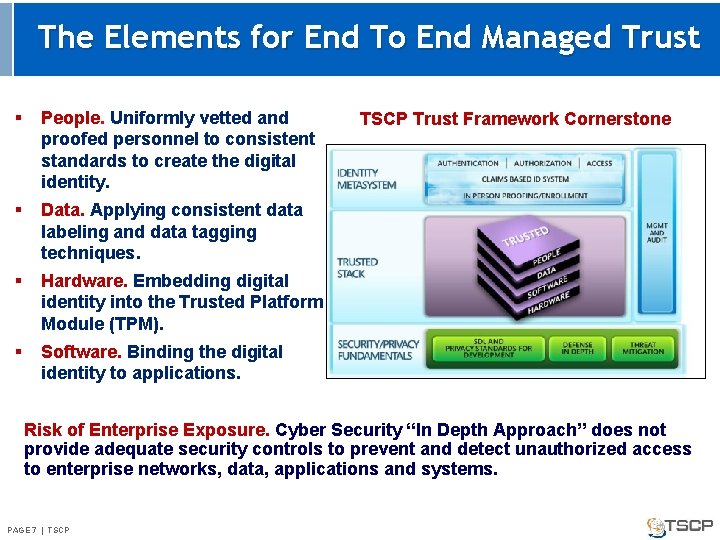
The Elements for End To End Managed Trust § People. Uniformly vetted and proofed personnel to consistent standards to create the digital identity. § Data. Applying consistent data labeling and data tagging techniques. § Hardware. Embedding digital identity into the Trusted Platform Module (TPM). § Software. Binding the digital identity to applications. TSCP Trust Framework Cornerstone Risk of Enterprise Exposure. Cyber Security “In Depth Approach” does not provide adequate security controls to prevent and detect unauthorized access to enterprise networks, data, applications and systems. PAGE 7 | TSCP

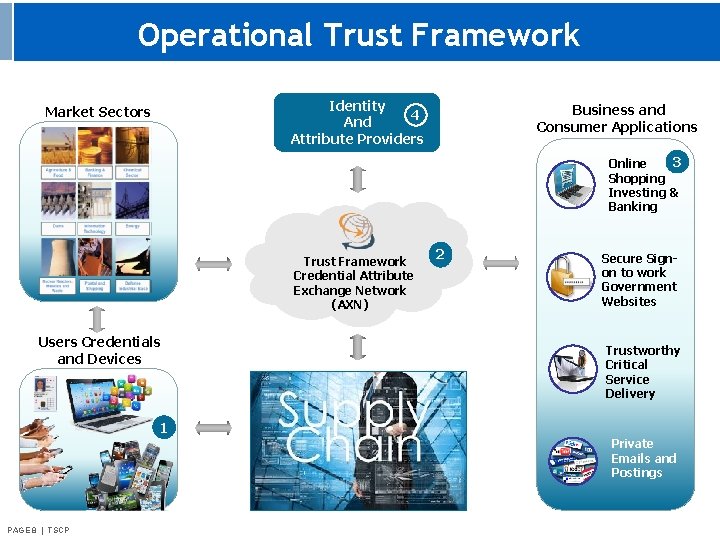
Operational Trust Framework Identity 4 And Attribute Providers Market Sectors Business and Consumer Applications 3 Online Shopping Investing & Banking Trust Framework Credential Attribute Exchange Network (AXN) Users Credentials and Devices 2 Secure Signon to work Government Websites Trustworthy Critical Service Delivery 1 Private Emails and Postings PAGE 88 || TSCP PAGE TSCP

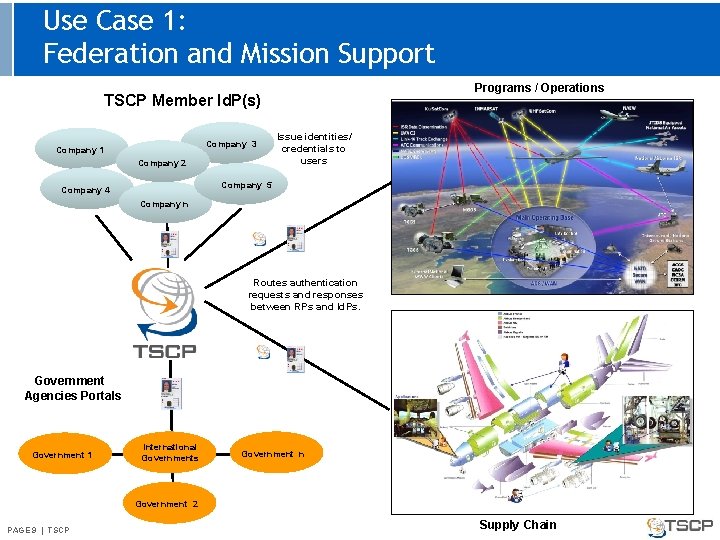
Use Case 1: Federation and Mission Support Programs / Operations TSCP Member Id. P(s) Company 3 Company 1 Company 2 Issue identities/ credentials to users Company 5 Company 4 Company n Routes authentication requests and responses between RPs and Id. Ps. Government Agencies Portals Government 1 International Governments Government n Government 2 PAGE 9 | TSCP Supply Chain

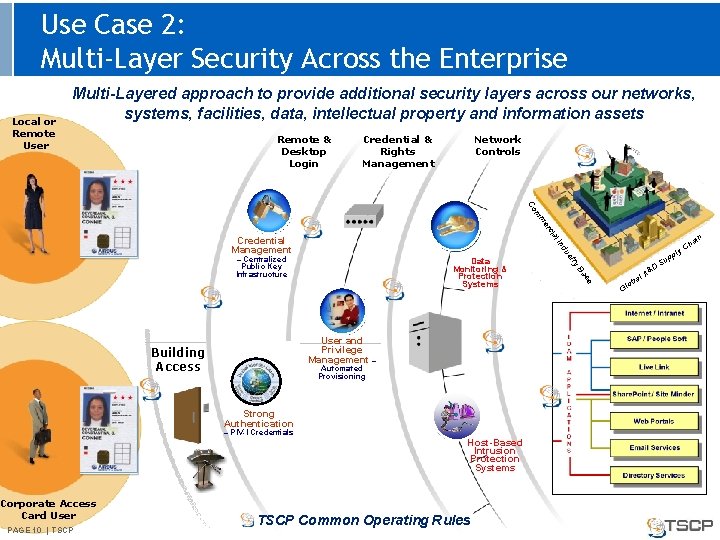
Use Case 2: Multi-Layer Security Across the Enterprise Local or Remote User Multi-Layered approach to provide additional security layers across our networks, systems, facilities, data, intellectual property and information assets Remote & Desktop Login Credential & Rights Management Network Controls ci er m m Co In Corporate Access Card User PAGE 10 | TSCP Host-Based Intrusion Protection Systems TSCP Common Operating Rules se Ba Strong Authentication ry Automated Provisioning st Data Monitoring & Protection Systems User and Privilege Management – – PIV-I Credentials ply up du – Centralized Public Key Infrastructure Building Access in al Credential Management &D Gl ob A al S a Ch

Use Case 3: Information Labeling and Access - ITAR/Export PAGE 11 | TSCP

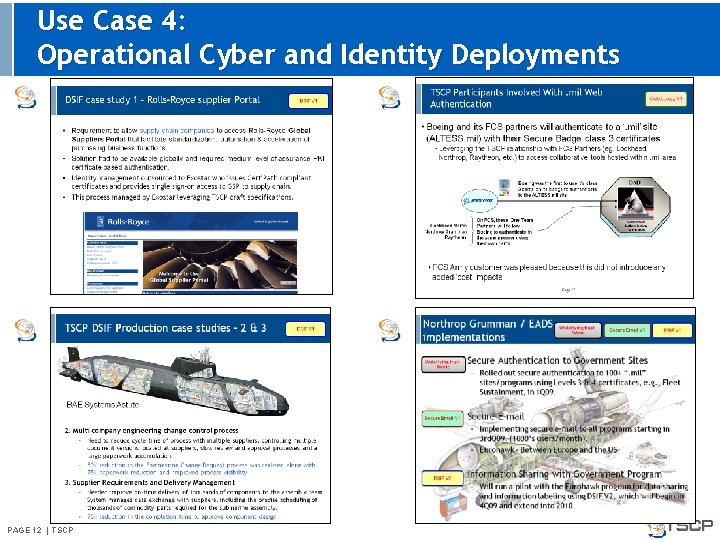
Use Case 4: Operational Cyber and Identity Deployments PAGE 12 | TSCP

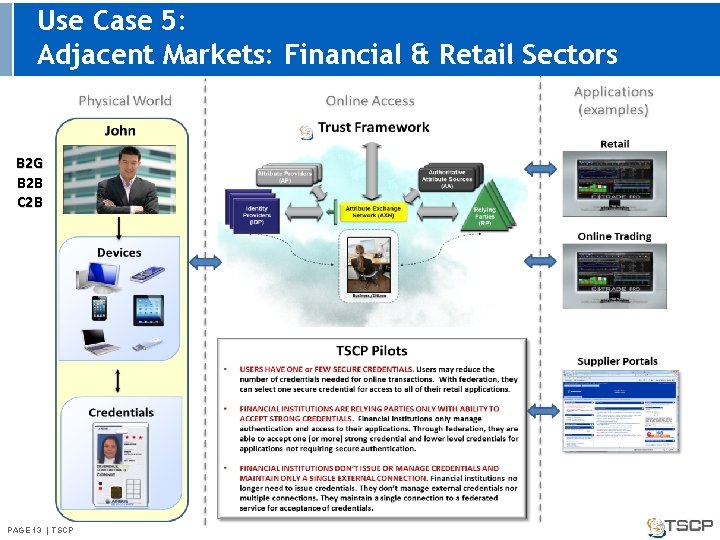
Use Case 5: Adjacent Markets: Financial & Retail Sectors B 2 G B 2 B C 2 B PAGE 13 | TSCP

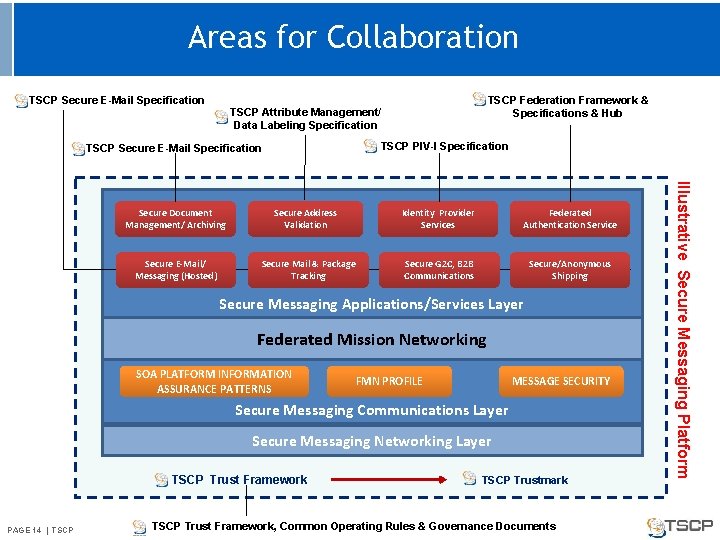
Areas for Collaboration TSCP Secure E-Mail Specification TSCP Federation Framework & Specifications & Hub TSCP Attribute Management/ Data Labeling Specification TSCP PIV-I Specification TSCP Secure E-Mail Specification Secure Address Validation Identity Provider Services Federated Authentication Service Secure E-Mail/ Messaging (Hosted) Secure Mail & Package Tracking Secure G 2 C, B 2 B Communications Secure/Anonymous Shipping Secure Messaging Applications/Services Layer Federated Mission Networking SOA PLATFORM INFORMATION ASSURANCE PATTERNS FMN PROFILE MESSAGE SECURITY Secure Messaging Communications Layer Secure Messaging Networking Layer TSCP Trust Framework PAGE 14 | TSCP Trustmark TSCP Trust Framework, Common Operating Rules & Governance Documents Illustrative Secure Messaging Platform Secure Document Management/ Archiving

Benefits to the TSCP Community • Managed Trust through a global federated Trust Framework with agreed common governance documents e. g. business, technical, legal, privacy. • Scalable Trust for Collaborative Endeavors. • Pooling resources to accomplish specification development, validation in a production and operational environments. • Sharing lessons learned. • Leverage International Standards adding the framework to meet operational needs. • Using Trusted Federated Identity and Access Management to provide the Cornerstone for Cyber Defense. PAGE 15 | TSCP
 Tivoli iam
Tivoli iam Ucf plc application
Ucf plc application Gartner iam maturity model
Gartner iam maturity model Identity and access management roadmap
Identity and access management roadmap Aws identity and access management
Aws identity and access management Oracle esso
Oracle esso Identity and access management assessment questionnaire
Identity and access management assessment questionnaire Hp identity access management
Hp identity access management Hp identity management
Hp identity management Identity management für versicherungen
Identity management für versicherungen Federated metadata management
Federated metadata management Personal identity map
Personal identity map Federated search ui
Federated search ui Federated discovery
Federated discovery Federated search vs distributed search
Federated search vs distributed search Centralized vs distributed database
Centralized vs distributed database