Identity Management In A Federated Environment Identity Protection










- Slides: 13

Identity Management In A Federated Environment Identity Protection and Management Conference Presented by Samuel P. Jenkins, Director Defense Privacy and Civil Liberties Office April 2010

Presentation Outline n n Success factors for identity federation and relation to privacy Fair Information Practice Principles for Identity Management Systems Core Information Privacy Concerns Privacy Design Considerations 2

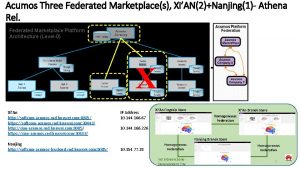
Identity Federation n Goal q Enable users to securely access data, systems, or applications of another domain seamlessly and without the need for completely redundant user administration 3

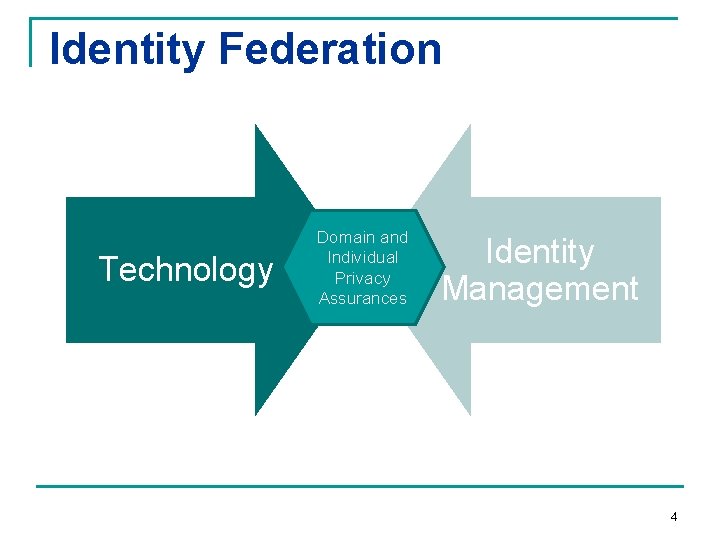
Identity Federation Technology Domain and Individual Privacy Assurances Identity Management 4

Identity Federation n Basis for Success q Agreement on root identities q Trust n n Between domains Between domain and individual 5

Root Identity Agreement Identity theft risk q Authentication q Social Security Number q Access control q 6

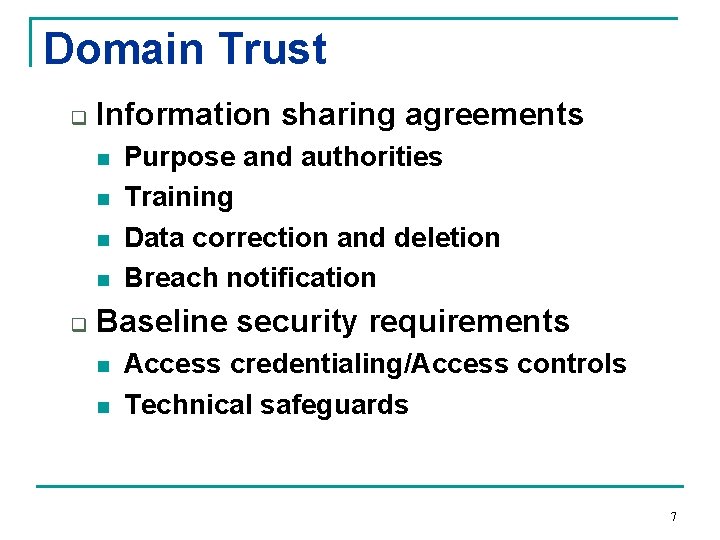
Domain Trust q Information sharing agreements n n q Purpose and authorities Training Data correction and deletion Breach notification Baseline security requirements n n Access credentialing/Access controls Technical safeguards 7

Individual Trust One person, one identity q Accuracy and timeliness q Controlled information sharing q IT Security q 8

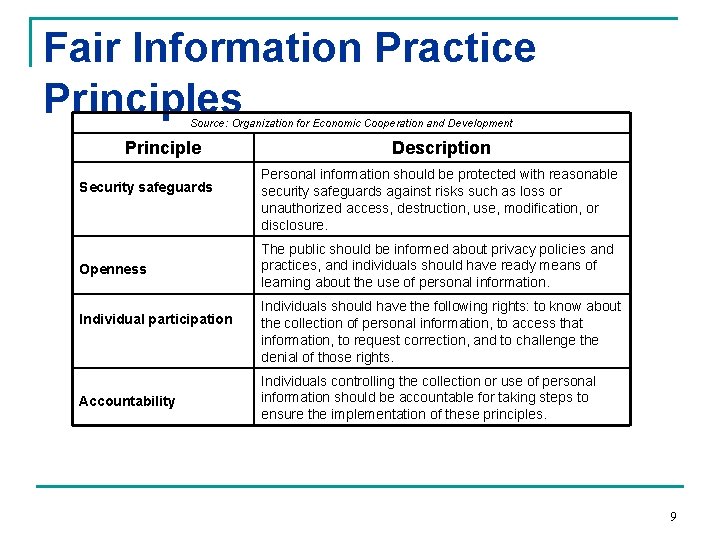
Fair Information Practice Principles Source: Organization for Economic Cooperation and Development Principle Security safeguards Openness Individual participation Accountability Description Personal information should be protected with reasonable security safeguards against risks such as loss or unauthorized access, destruction, use, modification, or disclosure. The public should be informed about privacy policies and practices, and individuals should have ready means of learning about the use of personal information. Individuals should have the following rights: to know about the collection of personal information, to access that information, to request correction, and to challenge the denial of those rights. Individuals controlling the collection or use of personal information should be accountable for taking steps to ensure the implementation of these principles. 9

Fair Information Practice Principles for Identity Management Systems Principle Description Diversity and decentralization Resist centralizing identity information or using a single credential for multiple purposes. Proportionality The amount, type, and sensitivity of identity information collected and stored by an identity management system should be consistent with and proportional to the system’s purpose. Privacy by design Privacy considerations should be incorporated into the identity management system from the outset of the design process. 10

Core Informational Privacy Concerns q Observability n q The possibility that others (potential observers) will gain information. Linkability n The potential to link between data and an individual as well as potential links between different data sets that can be tied together for further analysis. 11

Privacy Design Considerations Determine whether identity is necessary q Identify risks q Discourage unnecessary linkages q Implement security during design q Adopt trust-enhancing measures q 12

Thank you! Questions? 13
 Tivoli federated identity manager infocenter
Tivoli federated identity manager infocenter Ucf machine lab
Ucf machine lab Federated metadata management
Federated metadata management Careful protection and preservation of environment
Careful protection and preservation of environment Environment of business finance
Environment of business finance Federated search ui
Federated search ui Federated search vs discovery
Federated search vs discovery Federated search vs distributed search
Federated search vs distributed search Centralized vs distributed database
Centralized vs distributed database Common avionics architecture system
Common avionics architecture system Dbms definition
Dbms definition Benefits of federated search
Benefits of federated search Federated search examples
Federated search examples Federated data mart
Federated data mart