Trusted Computing Systems Definitions and Standards Trusted Computer








































- Slides: 53

Trusted Computing Systems Definitions and Standards

Trusted Computer Systems n IT security is increasingly important n n n Info can have varying degrees of sensitivity Subjects (people or programs) can have varying rights of access to objects (information) IT managers demand increasing confidence in systems to enforce these rights

Information System Security “Information system security is the application of managerial and administrative procedures and technical and physical safeguards to ensure not only the confidentiality, integrity and availability of information which is processed by an information system, but also of the information system itself, together with its environment. Such procedures and safeguards not only need to deter and delay improper access to information systems, they must also ensure that any improper access is detected; that is, individuals have to be made accountable for their actions. [Secman 3 - 103]

Trusted Computer Systems Issues n Need to consider: • system security • physical security • communications security n Most concerned with system security & how to assure its correctness

Rainbow Series—Early 1980’s Orange Book, etc.

TCSEC Trusted Computer System Evaluation Criteria ("Orange Book") n n Standard for single computer systems with terminal access First standard definition of a trusted computer system, how to evaluate and ensure them Original spec Aug 83, revised Dec 85 Has tight coupling between functionality & assurance

Criteria TCSEC defines a number of criteria within broad categories of: n Security Policy must have an explicit, enforced security policy; objects in system need access control labels n Accountability access to information must be controlled by rights of subjects vs. class of information; audit trails must be kept n Assurance system must contain mechanisms which can be independently evaluated to provide sufficient assurance that they enforce the stated requirements

Other "Rainbow Book" Standards n Red Book Trusted Network Interpretation n Yellow Book Methodology for Security Risk Assessment n Lavendar Book Database Security Evaluation

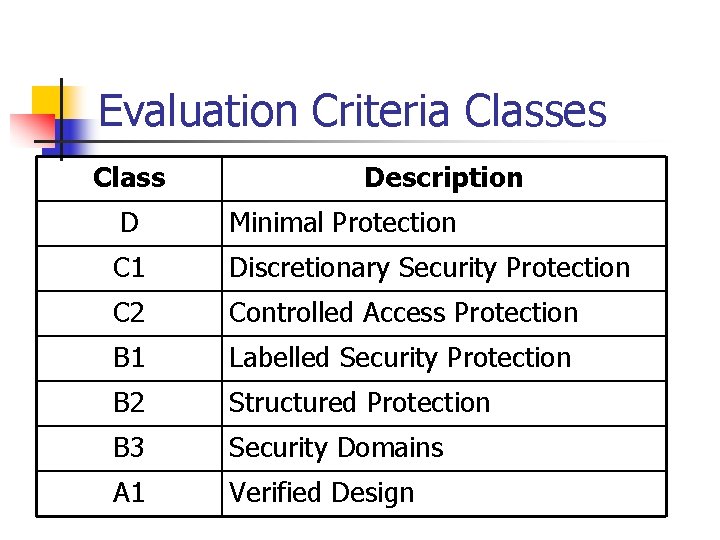
Evaluation Criteria Classes Class Description D Minimal Protection C 1 Discretionary Security Protection C 2 Controlled Access Protection B 1 Labelled Security Protection B 2 Structured Protection B 3 Security Domains A 1 Verified Design

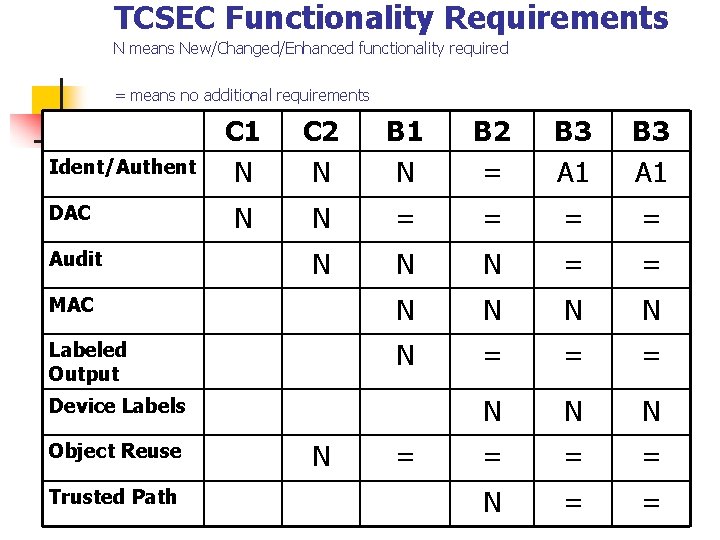
TCSEC Functionality Requirements N means New/Changed/Enhanced functionality required = means no additional requirements C 1 N C 2 N B 1 N B 2 = B 3 A 1 N N = = N N N = = MAC N N Labeled Output N = = = N N N = = = N = = Ident/Authent DAC Audit Device Labels Object Reuse Trusted Path N =

ITSEC—Followed TCSEC n European Version

ITSEC n Information Technology Security Evaluation Criteria (ITSEC) n European trusted evaluation standard harmonized with TCSEC - Unlike TCSEC, designed for both single & multiple networked systems - Target Of Evaluation (TOE) = evaluated system - Structured around - assurance and functionality n n Details evaluation process by independent evaluators working with developer and sponsor Evaluator: - Checks test & analysis results supplied by sponsor and - Performs additional tests to audit and supplement these

Assurance n Correctness is addressed both from: - development process & environment in building TOE - operation of the TOE n TOE must also be assessed for: - suitability and binding of functionality - consequences of known and discovered vulnerabilities - strength of security mechanisms against direct attack

Assurance – 7 evaluation levels n n n E 0 - inadequate E 1 - statement of security objects, informal description of security architecture E 2 - +informal description of detailed design, testing, configuration control and controlled distribution n n E 3 E 4 - +detailed design and source code evaluated +formal security policy model, rigorous architectural and detailed design, vulnerability analysis n E 5 - +close correspondence between detailed design and source code, vulnerability analysis on source code n E 6 - +formal description of TOE consistent with formal security model, evaluation of object code against source

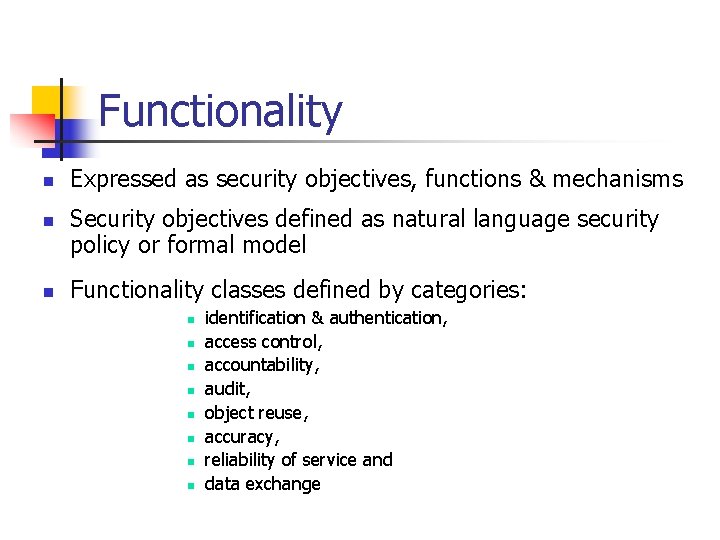
Functionality n n n Expressed as security objectives, functions & mechanisms Security objectives defined as natural language security policy or formal model Functionality classes defined by categories: n n n n identification & authentication, access control, accountability, audit, object reuse, accuracy, reliability of service and data exchange

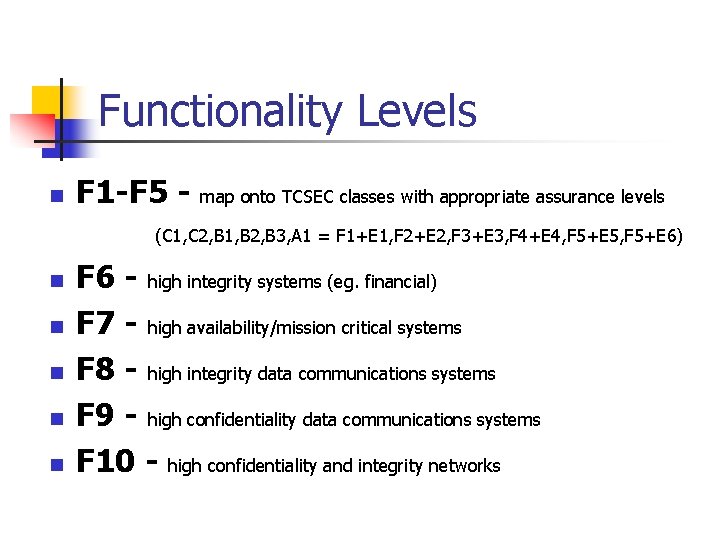
Functionality Levels n F 1 -F 5 - map onto TCSEC classes with appropriate assurance levels (C 1, C 2, B 1, B 2, B 3, A 1 = F 1+E 1, F 2+E 2, F 3+E 3, F 4+E 4, F 5+E 5, F 5+E 6) n n n F 6 - high integrity systems (eg. financial) F 7 - high availability/mission critical systems F 8 - high integrity data communications systems F 9 - high confidentiality data communications systems F 10 - high confidentiality and integrity networks

Common Criteria—Today n ISO standard

Common Criteria n n n Common Criteria being developed as an ISO standard (JTC 1. SC 27) Based on existing TCSEC, ITSEC, CTCPEC (Canadian), Federal (US) standards Concerned with standards for: - evaluation criteria - methodology for application of criteria - administrative procedures for evaluation, certification & accreditation schemes

Common Criteria CC Part 1 covers: n IT Security n n Threat Analysis n n "reduction of risks associated with threats to the information arising directly or indirectly from human error or deliberate subversion“ to discover conceivable threats Risk Analysis n to determine countermeasures

Common Criteria Key Concepts n Protection Profile n n Security Target n n set of generic security requirements for some applications sector a particular instance of a PP Target of Evaluation n actual system evaluated

Functional Class Set n n n n n identification & authentication trusted path security audit TOE entry user data protection resource utilization & availability protection of TOE security functions physical protection privacy communications

Assurance Levels n n n n AL 0 AL 1 AL 2 AL 3 AL 4 AL 5 AL 6 AL 7 - unassured tested structurally tested methodically tested & checked methodically tested & reviewed semiformal design semiformal verified design formally verified design

DSD Publications n Australian Version

DSD Publications n Defense Signals Directorate (DSD) Australia's national authority - signals intelligence and - information security n DSD's Infosec role not classified n Infosec products and services available: http: //www. dsd. gov. au/infosec/

ACSI 33 n n n Australian Communications-Electronic Security Instruction 33 (ACSI 33) Developed by DSD Provides guidance to Australian Government agencies

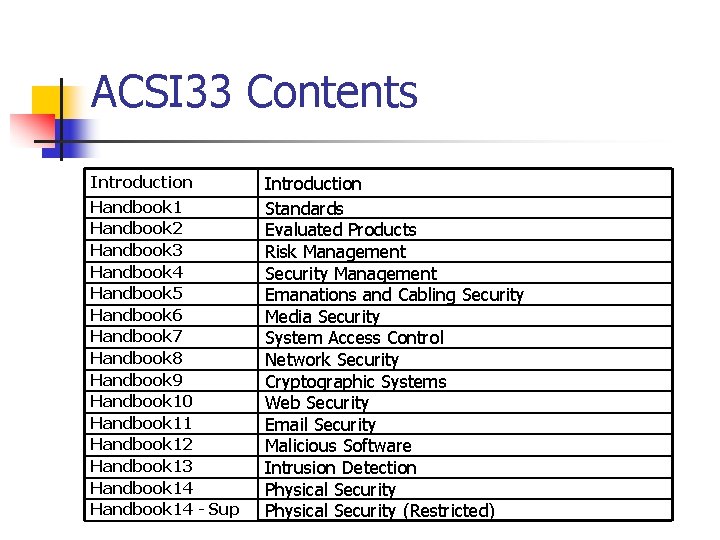
ACSI 33 Contents Introduction Handbook 1 Handbook 2 Handbook 3 Handbook 4 Handbook 5 Handbook 6 Handbook 7 Handbook 8 Handbook 9 Handbook 10 Handbook 11 Handbook 12 Handbook 13 Handbook 14 - Sup Introduction Standards Evaluated Products Risk Management Security Management Emanations and Cabling Security Media Security System Access Control Network Security Cryptographic Systems Web Security Email Security Malicious Software Intrusion Detection Physical Security (Restricted)

Gateway Certification Guide · Developed by DSD · Provides independent assessment of an agency's gateway (firewall): · - configured and managed appropriately That - suitable safeguards have been effectively implemented Introduction Chapter 1 Security Risk Assessment Chapter 2 Gateway Policy Chapter 3 Gateway Design Chapter 4 Gateway Security Management Chapter 5 DSD Certification Procedures

Evaluated Products List n DSD maintains "Evaluated Products List" products/systems evaluated to a particular class n Australia formerly used ITSEC, now Common Criteria accept some O/S evaluations also note it’s a slow, costly process to have a system evaluated n examples: n B 1 n n C 2 n n SCO CMW+, BEST-X/B 1, Sun Trusted Solaris SCO Unix. Ware, BEST-X/C 2, Sun Solaris, HP-UX, Novell Netware 4. 11 Server< AIX see EPL - Products at a Glance (Jan 2001)

Evaluation Certifying Systems vs. Standards

Evaluation Concepts and Relationships n n n evaluation -> assurance so that owners -> have confidence -> that countermeasures -> minimize risk -> to assets Evaluation of "trusted computer systems" is the ultimate goal of implementing standards Systems evaluated against evaluation standard

Two Key Aspects Evaluated n Functionality functions in system which enforce security n Assurance effectiveness and correctness of system’s construction and implementation

Trusted Computing Base “Trusted Computing Base” concept is central to IA n n n Includes security-relevant hardware/software Mediates all access between subjects & objects is tamperproof is validated

Types of Secure Computing Systems n n Categories of secure computing systems Based on classification range of supported subjects and objects Dedicated (Single-Level) Systems System-High Compartmented Multi-Level Systems

Dedicated (Single-Level) Systems n n Handles subjects & objects with same classification Relies on other security procedures (eg. physical) n Almost any system can operate at this level

System-High n n Only provides need-to-know protection between users Entire system operates at highest classification level All users must be cleared for that level of information Have basic access controls to provide some protection of data

Compartmented n n n Variation of System-High: can process 2 or more types of compartmented information Not all users are cleared for all compartments, but all must be cleared to the highest level of information processed Basic access controls provide some protection of data

Multi-Level Systems n n Validated for handling subjects & objects with different rights and levels of security simultaneously Major features include: n n user identification and authentication resource access control and object labeling audit trails of all security relevant events external validation of system’s security

Parties to an Evaluation n Sponsor of system (TOE) being developed n Developer of system (may be sponsor) n Evaluation facility performing evaluation n Certification body

Security Evaluation Phases n Pre-evaluation defines security target & deliverables n Evaluation fulfills required evaluation tasks n Re-evaluation corrects faults or changes n Certification confirms & accepts evaluation

Approaching Security Evaluation Tasks n Defining Security Requirements n n Risk Assessment n n of code checking both normal/erroneous usage Examination of the Source Code n n of functionality required to assurance level needed Practical Testing n n based on standards/criteria based on experience Theoretical Evaluation n n use system specification use standards/criteria use experience for potential bugs Penetration n attempting to hack system using knowledge of it

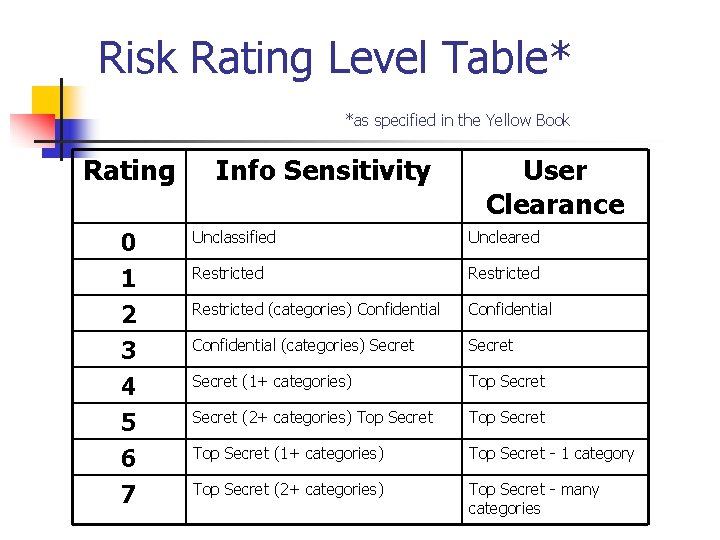
Risk Assessment 1. 2. 3. 4. 5. 2. determine what you are protecting against determine how much the protection is worth to you goal: "provide some assurance that cost of security countermeasures is commensurate with risk“ without it could spend too little or too much Risk Assessment - Yellow Book 1. 2. 3. original risk assessment from "rainbow book" series guiding principle is that recommended rating of a system depends on differential between user & info levels Risk Index (defined in Yellow book) is given by: 1. Risk Index = Max Info Sensitivity -

Risk Rating Level Table* *as specified in the Yellow Book Rating Info Sensitivity User Clearance 0 1 2 3 4 5 Unclassified Uncleared Restricted (categories) Confidential (categories) Secret (1+ categories) Top Secret (2+ categories) Top Secret 6 7 Top Secret (1+ categories) Top Secret - 1 category Top Secret (2+ categories) Top Secret - many categories

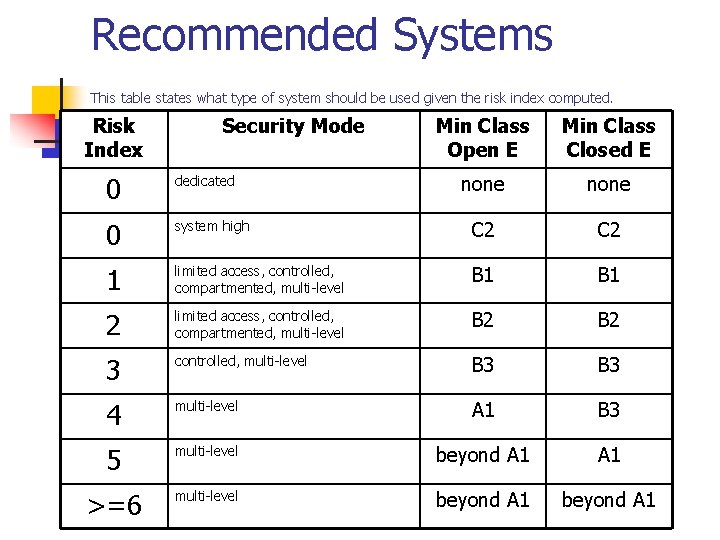
Recommended Systems This table states what type of system should be used given the risk index computed. Risk Index Security Mode Min Class Open E Min Class Closed E none 0 dedicated 0 system high C 2 1 limited access, controlled, compartmented, multi-level B 1 2 limited access, controlled, compartmented, multi-level B 2 3 controlled, multi-level B 3 4 multi-level A 1 B 3 5 multi-level beyond A 1 >=6 multi-level beyond A 1

Risk Analysis - DSD Gateway Certification Guide n n n Yellow book approach is very narrow and prescriptive In practice consider many factors DSD includes risk analysis section in Gateway Certification Guide

Process n Asset identification n Threat & threat likelihood estimation n Harm estimation n Risk assessment n Required risk & countermeasure rating

Asset Identification n ID Asset: tangible thing, suitable level of service, staff, information n Who is responsible for each n Determined in conjunction with owners

Threat & Threat Likelihood Estimation n n Focus on threats to identified assets May be multiple threats per asset Focus on likely and/or disastrous threats ID likely external threats from CERT reports, news, previous experience, legal requirements, etc. Internal threats harder to evaluate: use organization experience n Assign likelihood (probability) per threat (negligible - extreme) n Document threat sources & likelihood estimation

Harm Estimation n Estimate harm caused if threats realized n from insignificant – grave n If threat low/harm high, there is a risk n Harm estimation done with asset owner n Threat likelihood done by security specialist

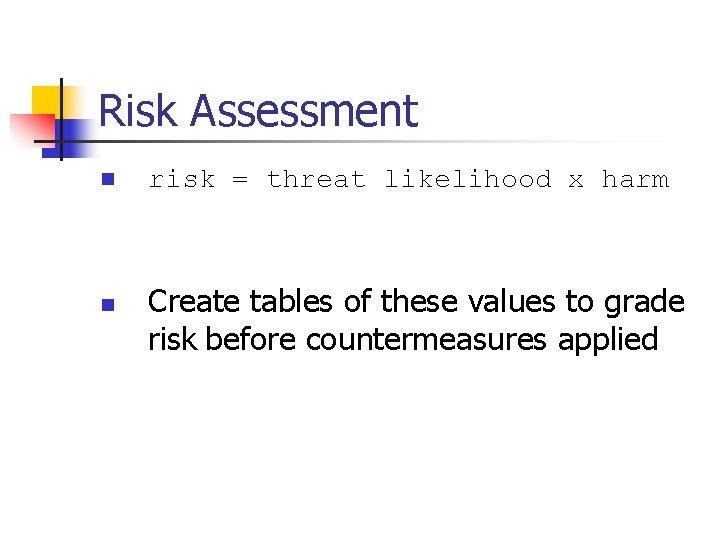
Risk Assessment n n risk = threat likelihood x harm Create tables of these values to grade risk before countermeasures applied

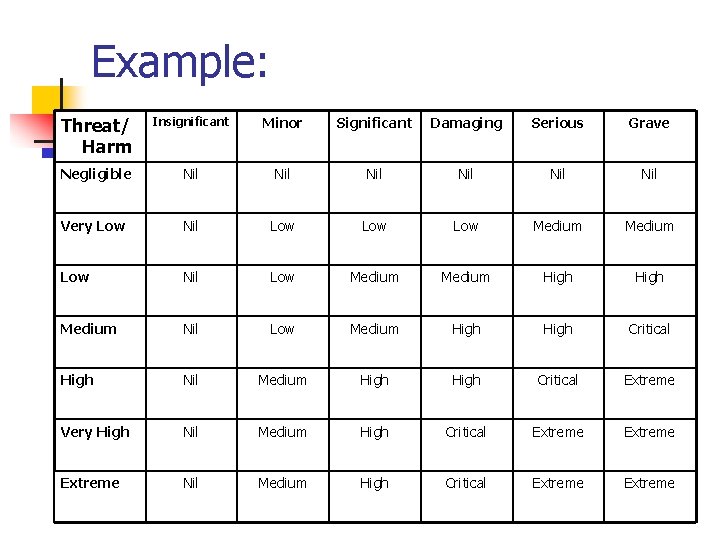
Example: Threat/ Harm Insignificant Minor Significant Damaging Serious Grave Negligible Nil Nil Nil Very Low Nil Low Low Medium Low Nil Low Medium High Medium Nil Low Medium High Critical High Nil Medium High Critical Extreme Very High Nil Medium High Critical Extreme Nil Medium High Critical Extreme

Required Risk & Countermeasure Rating n Required risk = risk level management will accept n Vs. particular risk assessed for a threat n Remember: reducing risk comes at a cost n n Countermeasure rating = required risk - assessed risk Provides guidance on importance of security countermeasures vs. each threat

Sample Problem 1: As part of a risk assessment of desktop systems, consider the following: you have identified the following asset "integrity of data files on system"; you have identified the following threat "corruption of data files due to import of a virus onto the system". As part of the risk assessment process you must now: n n n estimate the likelihood of the threat specify the harm caused if the threat is realized assess the resultant risk specify the risk management are willing to accept hence identify the scale of countermeasures required, and suggest what they might be Justify your choices.

Sample Problem 2: Your advice is requested on the appropriate level of security evaluation to be requested in an RFP for a computer system to be used by engineers writing maintenance documentation for a new weapons system. The documents are classified as either Confidential or Secret, while some of the staff using the system are cleared for Confidential, others are cleared for Secret. Identify the evaluation level nominally required using the Yellow Book assessment procedure.