Federated Authentication Who am I Aaron Anderson Federated










- Slides: 13

Federated Authentication

Who am I? Aaron Anderson Federated Identity and Privileged Identity Management practice lead at IDMWORKS 12 years in the Id. M space 10 years provisioning projects 2 years doing federated authentication using Ping. Federate

Fed Auth Use Case The primary security benefit for federated authentication is to eliminate credential stores and allow users to authenticate to applications using their primary identity (IDP). If a user’s primary account is disabled, they can no longer access applications No need for complex Id. M product that disables all the user’s accounts The enterprise generally uses SAML 2. 0 Consumer services (eg Facebook, etc) use Open. ID Connect/OAUTH

WEB SSO - SAML 2. 0

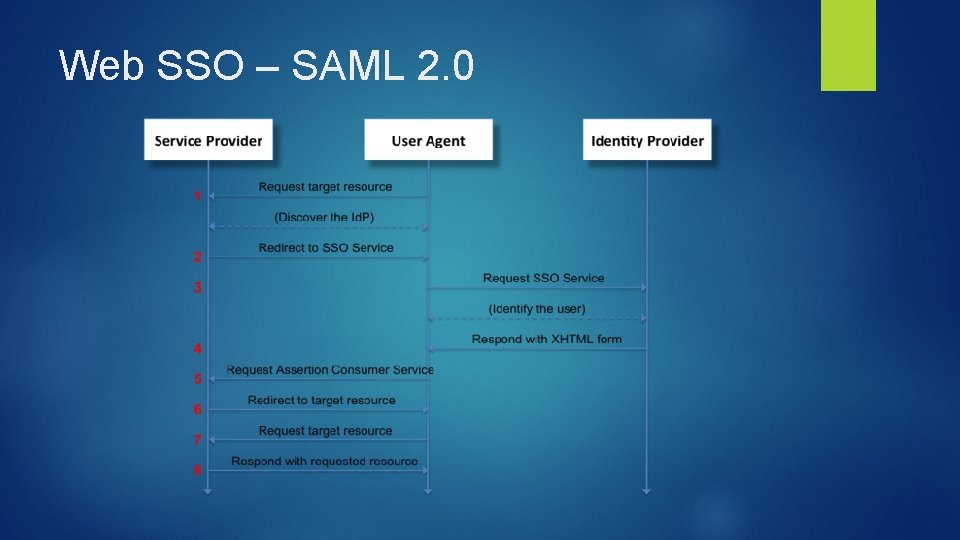
Web SSO - SAML 2. 0 2 main components: IDP – Identity Provider SP – Service Provider SAML – Security Assertion Markup Language. Version 2 is the current standard. A SAML message is a XML document that contains a response and an assertion. The SAML message is secured using PKI. A hash of the SAML message is produced and digitally signed by the IDP using a private key. The SP creates the same digest (hash) and verifies the signature using the IDPs public key, which is distributed during the setup of a connection. The user’s browser is the transport mechanism.

Web SSO – SAML 2. 0

Web SSO – SAML 2. 0 <saml: Response ID=“_50 k 4 fj 4 f 4” In. Response. To=“_5 kgrlr” Version=“ 2. 0”> <saml: Assertion Version="2. 0“ ID=“_34234 se 72” Issue. Instant="2005 -04 -01 T 16: 58: 33. 173 Z"> <saml: Issuer>http: //authority. example. com/</saml: Issuer> <ds: Signature>. . . </ds: Signature> <saml: Subject><saml: Name. ID format="urn: oasis: names: tc: SAML: 2. 0: nameid-format: persistent">aaron. Anderson@mydomain. com</saml: Name. ID> </saml: Subject> <saml: Authn. Context. Class. Ref> urn: oasis: names: tc: SAML: 2. 0: ac: classes: Password. Protected. Transport </saml: Authn. Context. Class. Ref> <saml: Attribute. Statement> <saml: Attribute Name. Format="urn: oasis: names: tc: SAML: 2. 0: attrname-format: basic Name=“groups" <saml: Attribute. Value xsi: type="xs: string">member</saml: Attribute. Value> <saml: Attribute. Value xsi: type="xs: string">staff</saml: Attribute. Value> </saml: Attribute. Statement> </saml: Assertion>

OAUTH and Open. ID Connect (OIDC)

Open. ID Connect Built on top of OAuth 2. 0. Adds a schema to OAuth 2. 0. 2 Flows: Code Flow – Delegated Access - Issues an access token that can be used to access resources ID Token Flow – Federation - Issues a JWT token to assert a user’s identity Scopes: Defines the attributes that being requested Examples: email, address, phone

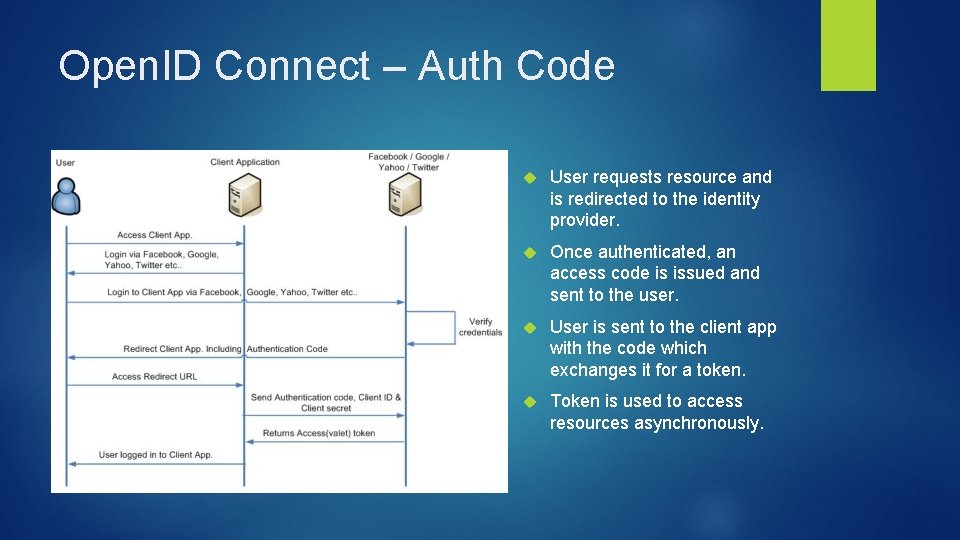
Open. ID Connect – Auth Code User requests resource and is redirected to the identity provider. Once authenticated, an access code is issued and sent to the user. User is sent to the client app with the code which exchanges it for a token. Token is used to access resources asynchronously.

Open. ID Connect – ID Token User requests resource and is redirected to the identity provider. Once authenticated, a JWT is generated and sent to the user. User is sent to the client app with the JWT. Client application validates JWT and extracts user’s identity. JWT can be used to obtain an access token.

Nike use case

Nike Use Case Use Ping. Federate Presently used for workforce federation to external and internal applications Extended use cases are use Open. ID Connect to allow retail users to leverage their identity to access APIs from mobile devices
 What is peer entity authentication
What is peer entity authentication Iff
Iff Federated search vs discovery
Federated search vs discovery Federated database vs distributed database
Federated database vs distributed database Federated esb
Federated esb Federated search examples
Federated search examples Unified search vs federated search
Unified search vs federated search Federated enterprise architecture
Federated enterprise architecture Confidential machine learning
Confidential machine learning Federated discovery
Federated discovery Types of avionics architecture
Types of avionics architecture Federated database architecture
Federated database architecture Federated data mart
Federated data mart Federated search vs distributed search
Federated search vs distributed search