The Importance of Proper Controls Network Controls Developing







- Slides: 12

The Importance of Proper Controls




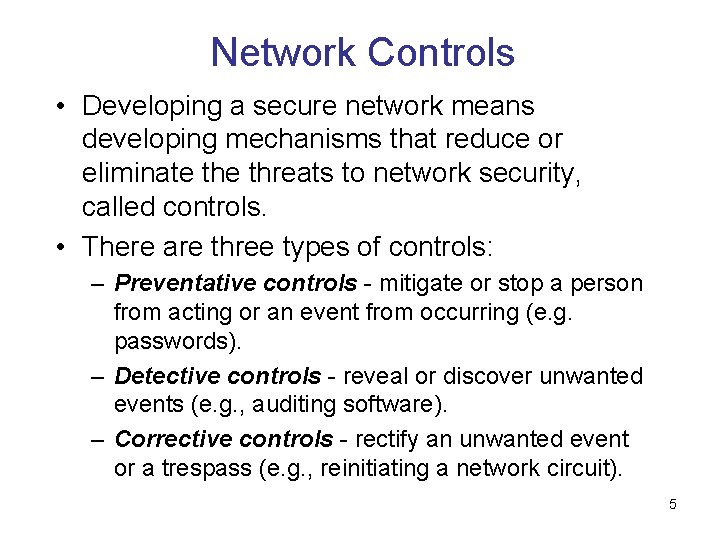
Network Controls • Developing a secure network means developing mechanisms that reduce or eliminate threats to network security, called controls. • There are three types of controls: – Preventative controls - mitigate or stop a person from acting or an event from occurring (e. g. passwords). – Detective controls - reveal or discover unwanted events (e. g. , auditing software). – Corrective controls - rectify an unwanted event or a trespass (e. g. , reinitiating a network circuit). 5

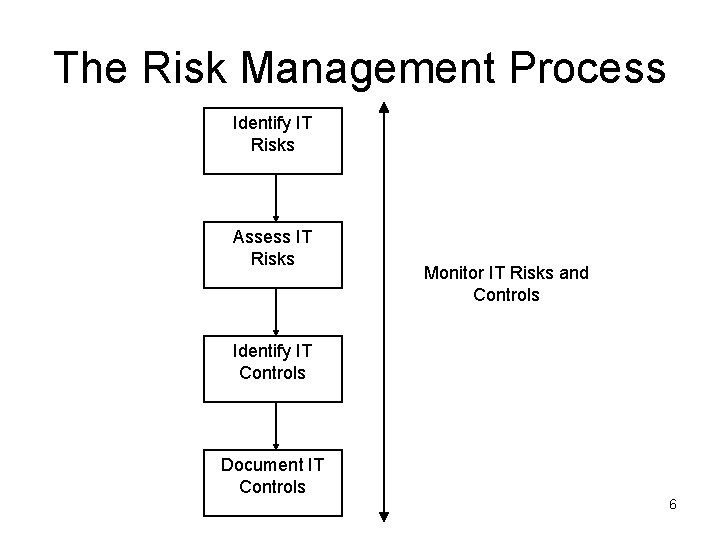
The Risk Management Process Identify IT Risks Assess IT Risks Monitor IT Risks and Controls Identify IT Controls Document IT Controls 6

Risk Assessment • Risk assessment is the process of making a network more secure, by comparing each security threat with the control designed to reduce it (where are controls needed? ). • Cost Benefit Assessment (which controls are appropriate based on cost reward tradeoff? ) • Vulnerability Assessment (how effective are the controls? ; are they working properly? ) 7

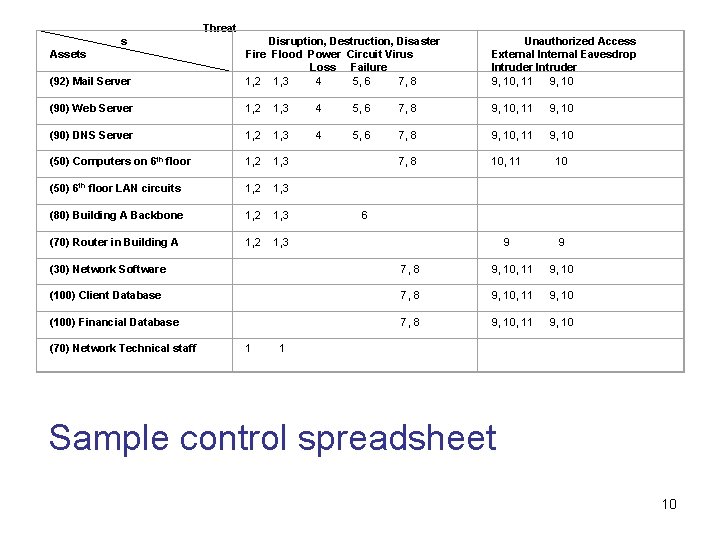
Risk Assessment • One way to do this is by developing a control spreadsheet • Network assets are listed down the side. • Threats are listed across the top of the spreadsheet. • The cells of the spreadsheet list the controls that are currently in use to address each threat. 8

Valuation of Asset • Assets: People, Data, Hardware, Software, Facilities, (Procedures) • Valuation Methods – Criticallity to the organization’s success – Revenue generated – Profitability – Cost to replace – Cost to protect – Embarrassment/Liability 9

Threat Disruption, Destruction, Disaster s Assets Fire Flood Power Circuit Virus Loss Failure (92) Mail Server 1, 2 1, 3 4 5, 6 7, 8 Unauthorized Access External Internal Eavesdrop Intruder 9, 10, 11 9, 10 (90) Web Server 1, 2 1, 3 4 5, 6 7, 8 9, 10, 11 9, 10 (90) DNS Server 1, 2 1, 3 4 5, 6 7, 8 9, 10, 11 9, 10 (50) Computers on 6 th floor 1, 2 1, 3 7, 8 10, 11 10 (50) 6 th floor LAN circuits 1, 2 1, 3 (80) Building A Backbone 1, 2 1, 3 6 (70) Router in Building A 1, 2 1, 3 9 (30) Network Software 7, 8 9, 10, 11 9, 10 (100) Client Database 7, 8 9, 10, 11 9, 10 (100) Financial Database 7, 8 9, 10, 11 9, 10 (70) Network Technical staff 1 1 Sample control spreadsheet 10

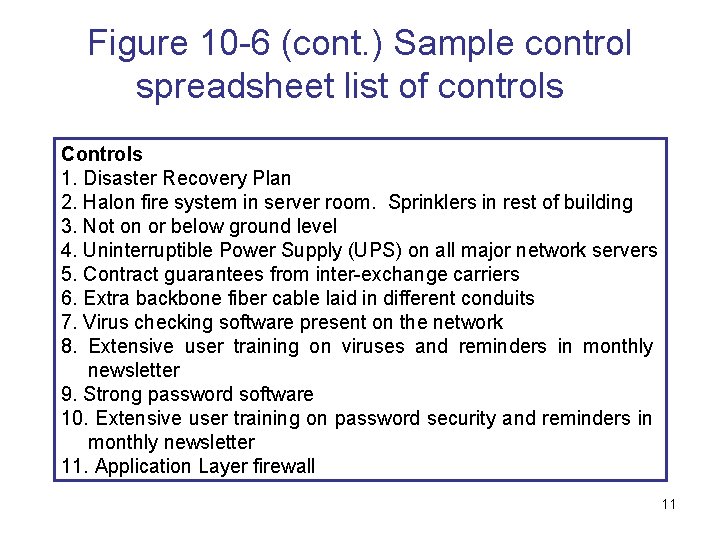
Figure 10 -6 (cont. ) Sample control spreadsheet list of controls Controls 1. Disaster Recovery Plan 2. Halon fire system in server room. Sprinklers in rest of building 3. Not on or below ground level 4. Uninterruptible Power Supply (UPS) on all major network servers 5. Contract guarantees from inter-exchange carriers 6. Extra backbone fiber cable laid in different conduits 7. Virus checking software present on the network 8. Extensive user training on viruses and reminders in monthly newsletter 9. Strong password software 10. Extensive user training on password security and reminders in monthly newsletter 11. Application Layer firewall 11

Evaluate the Network’s Security • The last step in designing a control spreadsheet is evaluating the adequacy of the controls and the degree of risk associated with each threat. • Based on this, priorities can be decided on for dealing with threats to network security. • The assessment can be done by the network manager, but it is better done by a team of experts chosen for their in-depth knowledge about the network and environment being reviewed. 12